Vishwas Narayan discusses application security and the need to shift security left in the software development lifecycle. Some key points discussed include:
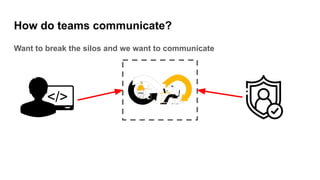
- Application security professionals deal with vulnerabilities in connections, users, content, files and more. Firewalls, authentication, authorization, and other tools are used to address security.
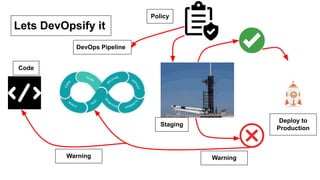
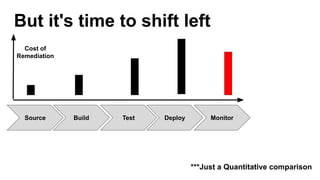
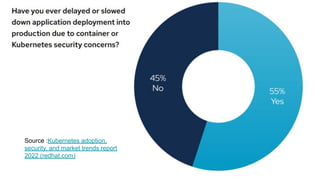
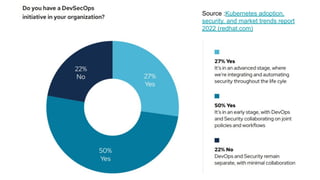
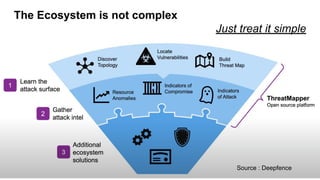
- As software grows, security becomes more difficult as new vulnerabilities are found daily. Shifting security left to earlier stages makes remediation less costly than fixing issues after deployment.
- However, shifting left is not a perfect strategy as some vulnerabilities may remain, third party components are harder to control, and unknown issues can still be found post-deployment. The ultimate strategy is to both shift left