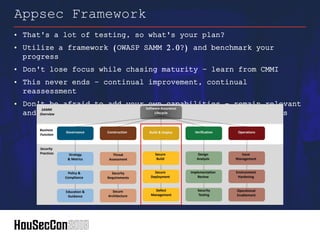
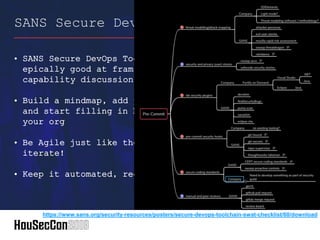
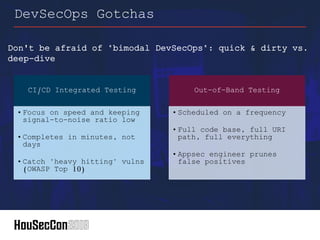
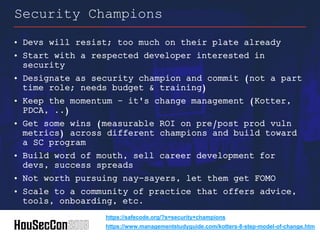
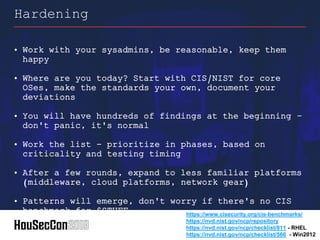
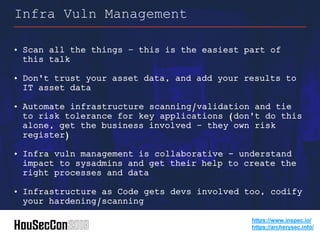
This document outlines strategies for establishing an offensive security posture within organizations, directed towards security leaders seeking to improve their capabilities. It discusses a structured approach to integrate application security, DevSecOps, and vulnerability management, while emphasizing the importance of collaboration between development and security teams. Additionally, it highlights the significance of continuous improvement, agile methodologies, and the role of security champions in fostering a culture of security awareness and readiness.