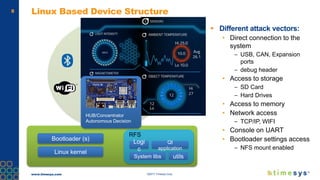
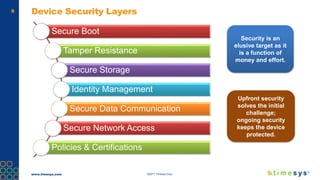
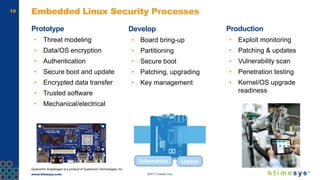
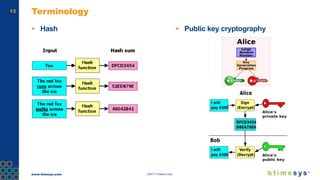
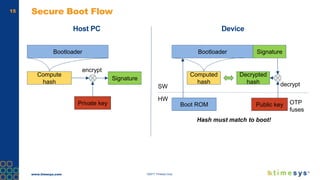
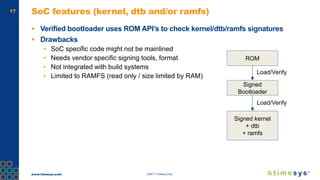
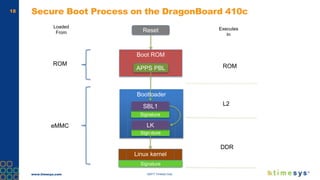
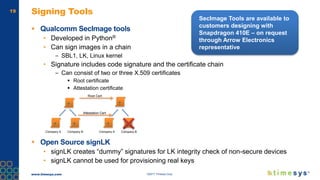
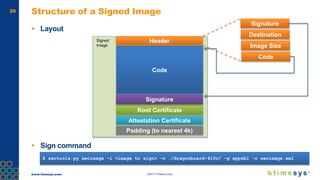
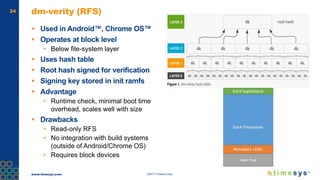
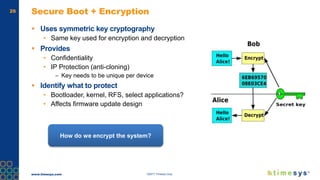
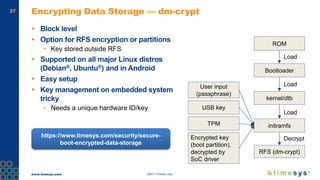
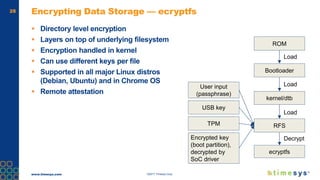
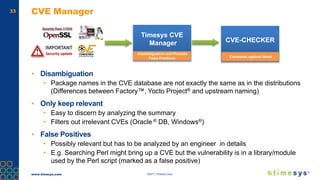
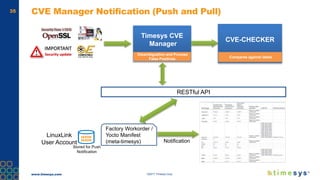
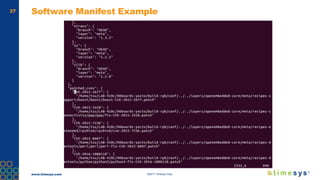
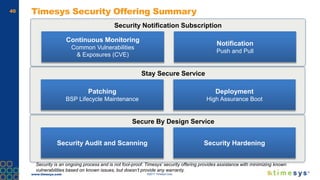
This document discusses ongoing security for embedded Linux devices. It describes Timesys' security notification service which monitors Common Vulnerabilities and Exposures (CVEs) and notifies customers of relevant issues. The service filters CVE data, disambiguates package names, and flags false positives. Notifications are sent via a RESTful API or through a LinuxLink user account. The meta-timesys layer integrates these security features into builds using OpenEmbedded RPB BSP. Ongoing security helps minimize known vulnerabilities over the product lifecycle.