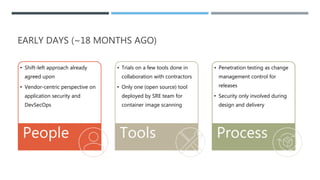
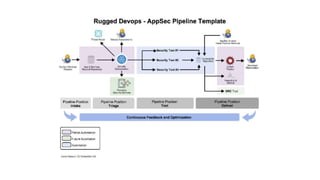
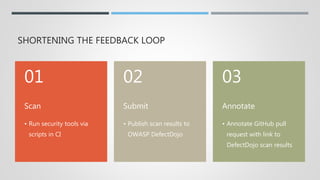
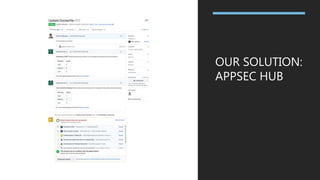
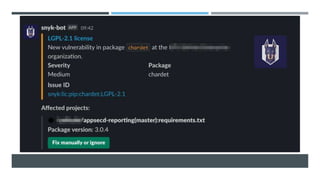
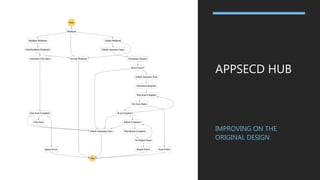
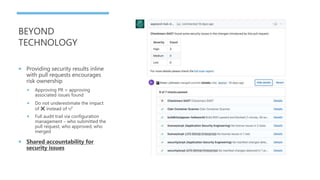
This document discusses the journey of an application security engineer in implementing an effective application security program within a large organization. It describes early challenges around tool selection, process definition, and gaining developer buy-in. It outlines the creation of an "AppSec Hub" to automate security scans and feedback, but limitations led to building tools aligned with how development teams work. Lessons learned include the importance of relationships, compromise, and embedding security seamlessly into development flows and tools. The conclusions emphasize that tools should focus on alignment, scanning profiles should have optimal signal-to-noise, and removing ambiguity to make development easier.