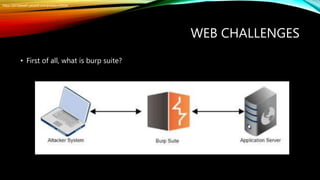
The document is a presentation by Heba Hamdy Farahat on various aspects of cybersecurity, including data breaches, capture the flag (CTF) competitions, and how to get started in the field. It highlights famous incidents, necessary skills, and resources for learning and practicing cybersecurity techniques through various CTF platforms. Additionally, it provides insights into penetration testing, incident response, and the importance of hands-on experience in the cybersecurity industry.






![FACEBOOK ADMITS CYBER ATTACK MAY
HAVE EXPOSED INFO FROM 50 MILLION
ACCOUNTS
A vulnerability in Facebook’s code that impacted “View As”.
This allowed attackers to steal Facebook access tokens which they could then use to take over
people’s accounts![*]
[*] Reference:
https://newsroom.fb.com/news/2018/09/security-update/](https://image.slidesharecdn.com/playlearnandhack-191207220332/85/Play-Learn-and-Hack-CTF-Training-7-320.jpg)
![TWITTER CEO AND CO-FOUNDER JACK DORSEY
HAS ACCOUNT HACKED[*]
[*]Reference: https://www.wired.com/story/jack-dorsey-twitter-hacked/](https://image.slidesharecdn.com/playlearnandhack-191207220332/85/Play-Learn-and-Hack-CTF-Training-8-320.jpg)