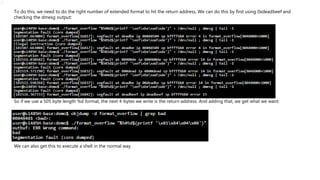
The document discusses format string attacks, which exploit vulnerabilities in C functions that use unchecked user input as the format string parameter. A malicious user can use special format string tokens like %s and %x to print data from the call stack or write to arbitrary memory locations using %n. This allows attackers to execute arbitrary code, read sensitive data, or crash applications. The document provides examples of how format strings work and how buffer overflows can be caused when more data is written than the buffer can hold, overwriting adjacent memory.








![Using formats in an exploit
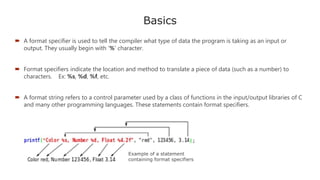
Now that we've had a whirl-wind tour of formats you've never heard of nor ever really wanted to use, how
can we use them in an exploit. Here's the program we are going to exploit.
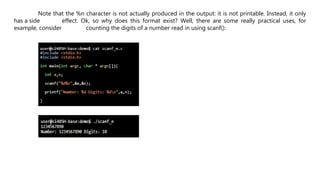
This is a rather contrived example of using sprintf() to do a copy. One may think because
in the first sprintf() the %.400s format is used, this would not enable a overflow of buffer or
outbuff. For example, this does not cause a segmentation fault:
True, we can't overflow buffer, but we can overflow outbuff because buffer is treated as
the format character. For example, what if the input was like:
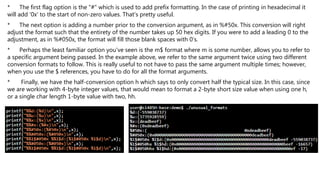
And if we look at the dmesg output: [dmesg is a command on most Unix-like operating systems that prints
the message buffer of the kernel]
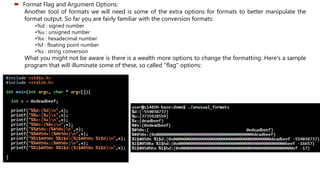
We see that we overwrote the instruction pointer with a bunch of 0x20 bytes, or spaces!
Now, the goal is to overwrite the return address with something useful, like the address of
bad().](https://image.slidesharecdn.com/formatstringattack-190116113154/85/Format-String-Attack-13-320.jpg)