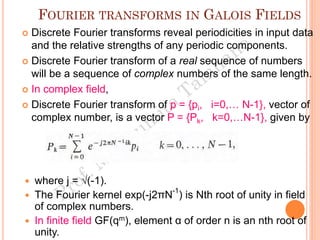
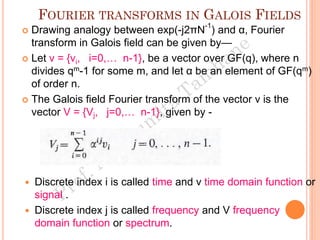
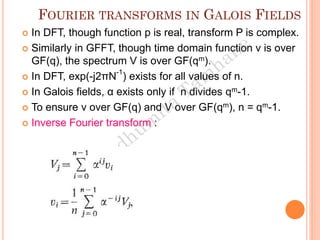
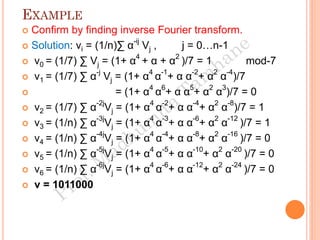
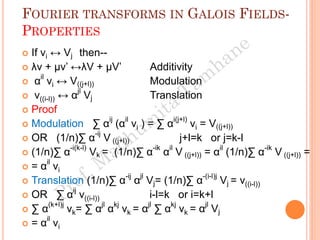
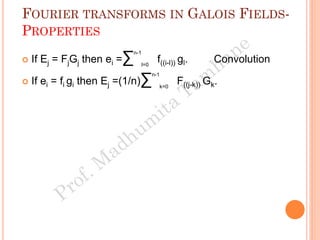
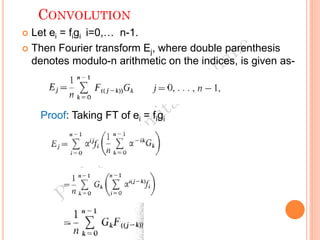
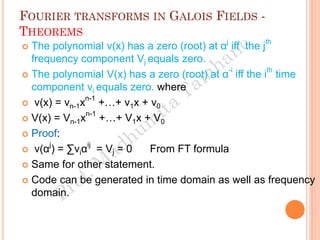
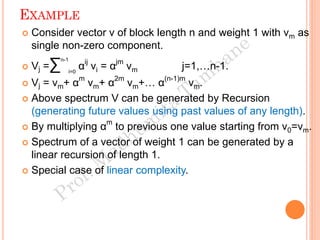
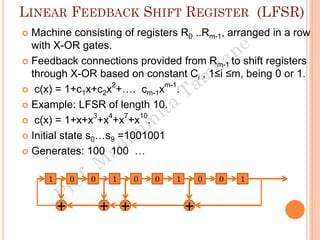
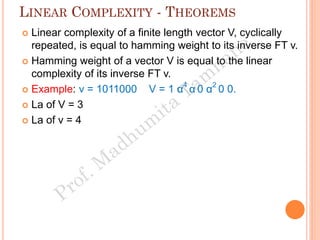
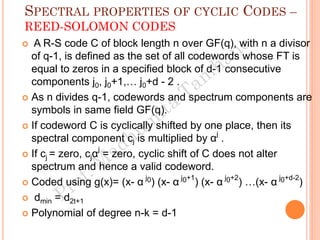
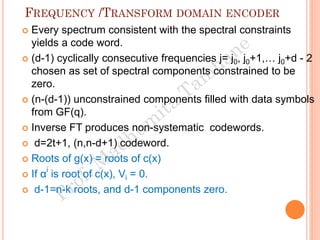
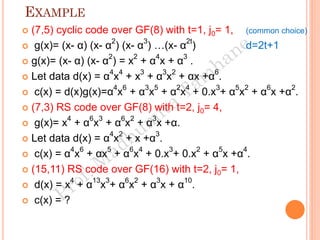
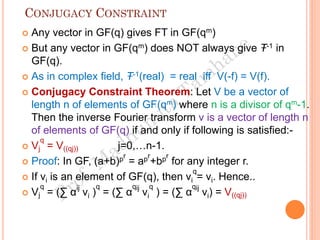
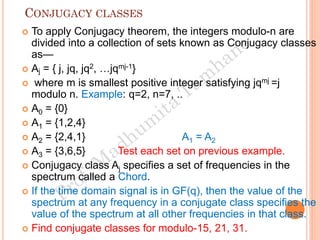
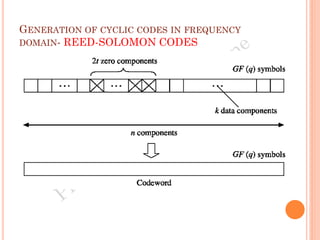
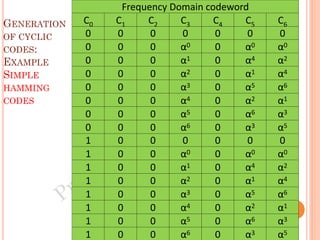
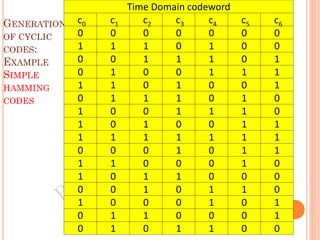
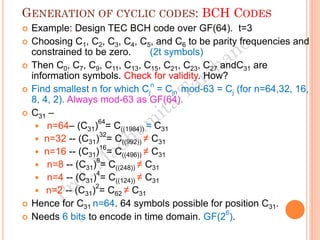
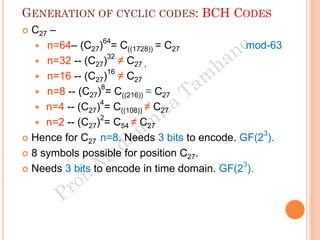
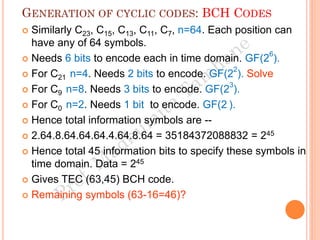
The document discusses the generation of error control codes, particularly BCH and Reed-Solomon codes, through Fourier transforms in Galois fields. It explains the relationship between discrete Fourier transforms in real and complex fields, and how similar principles apply in finite fields, emphasizing properties, theorems, and examples related to linear feedback shift registers and the significance of these codes in error correction. Key concepts include transformations, inverses, spectrum, and code generation with constraints on cyclic shifts and polynomial roots.