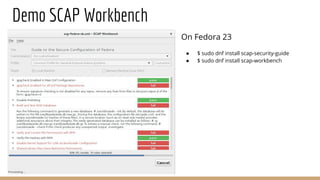
The document discusses atomic scan with OpenSCAP, focusing on identifying software vulnerabilities and configuration flaws in containers. It explains how atomic scan operates by detecting operating systems, fetching CVE feeds, and parsing results using OpenSCAP, along with references to notable vulnerabilities like Heartbleed and Shellshock. It also highlights the role of SCAP in compliance and security management, including tools and resources for scanning and maintaining secure systems.