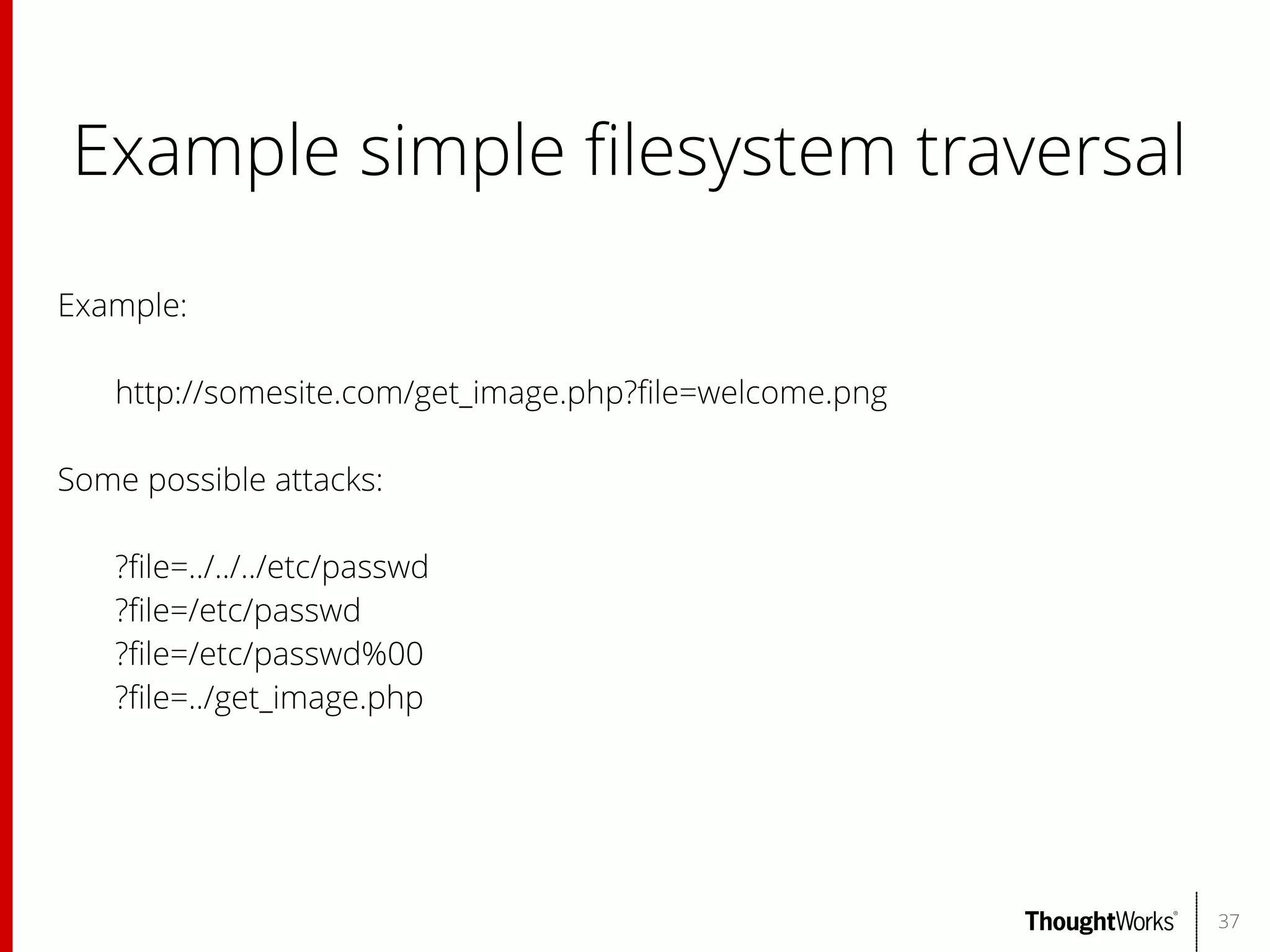
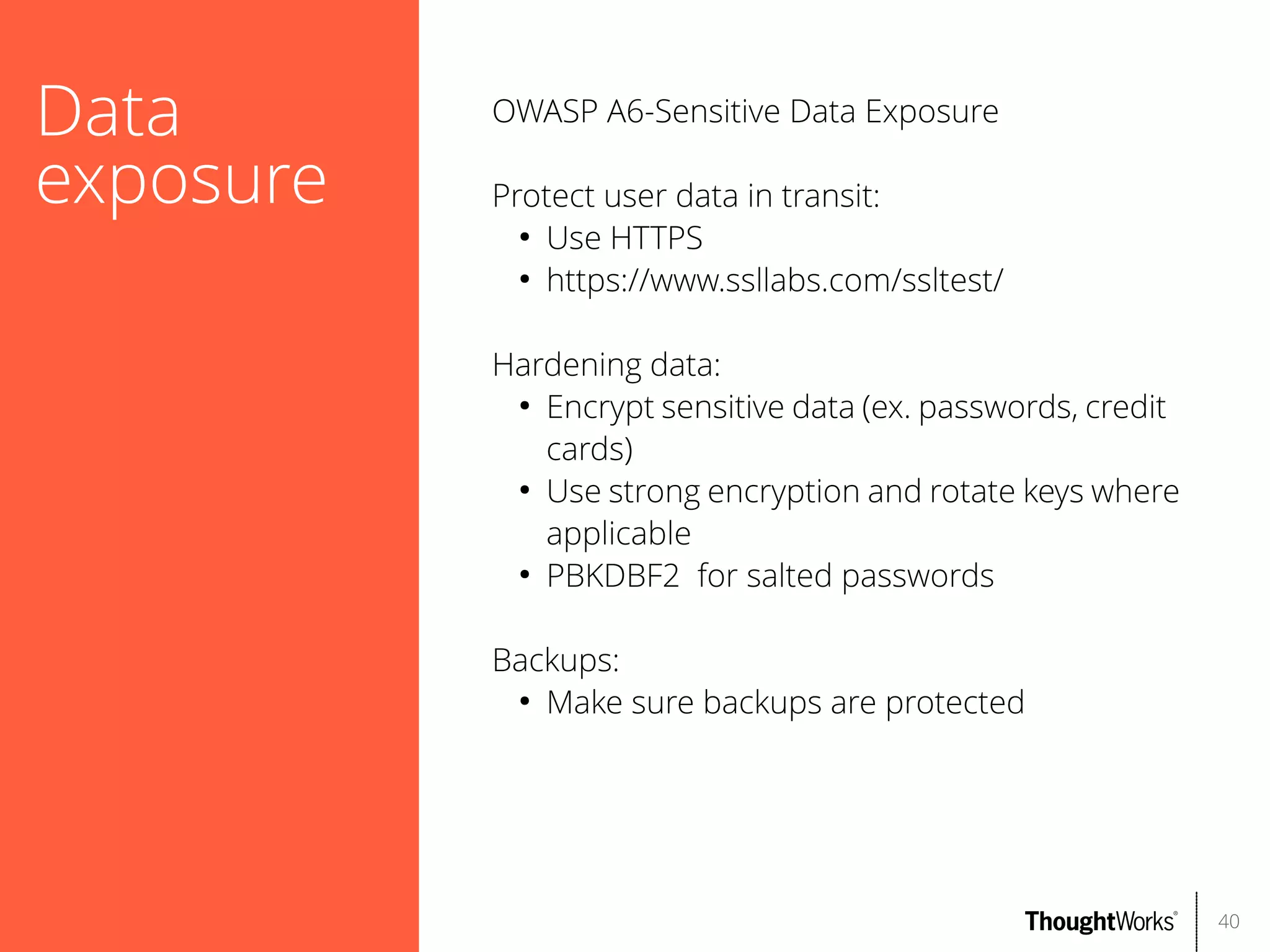
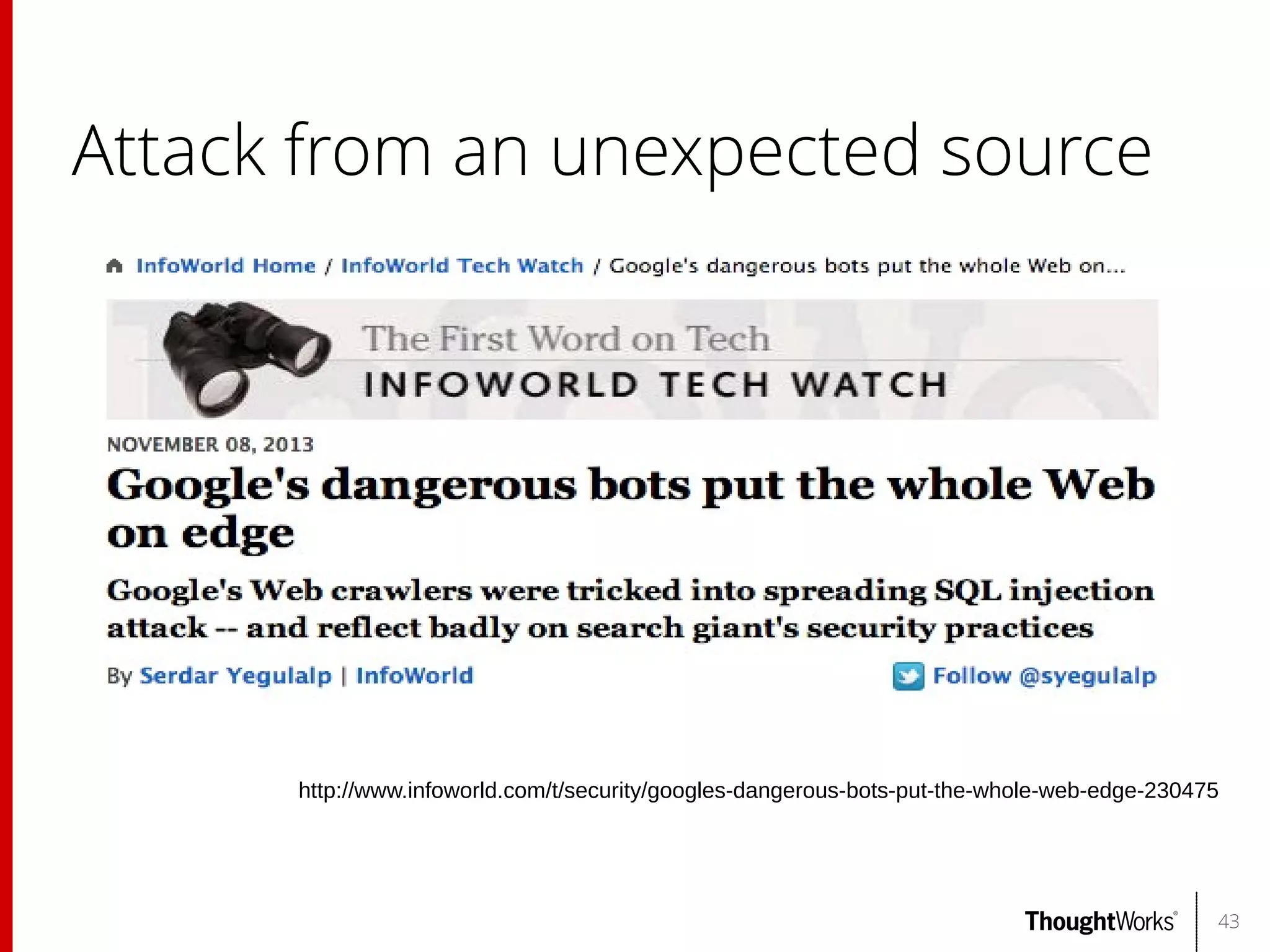
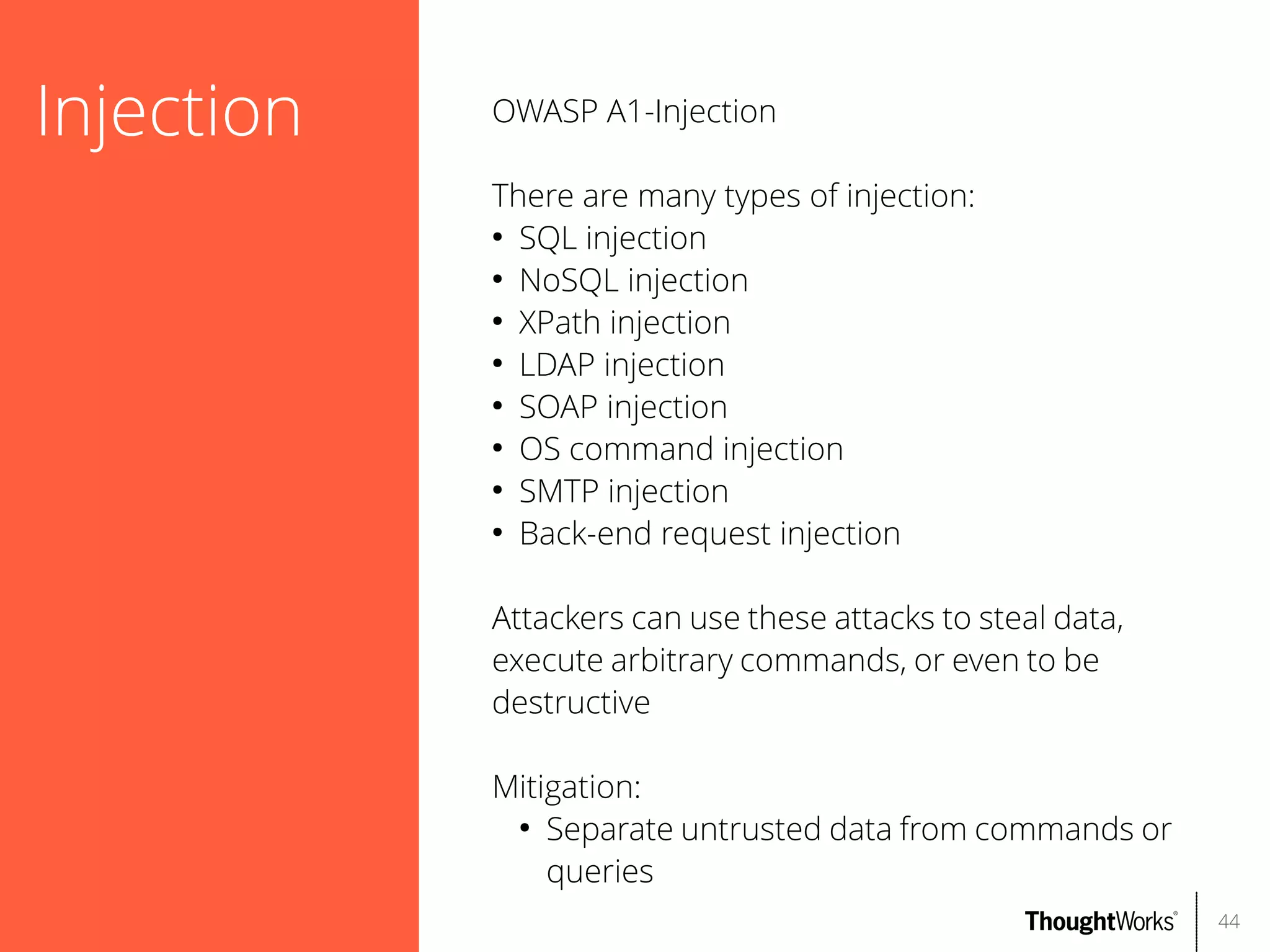
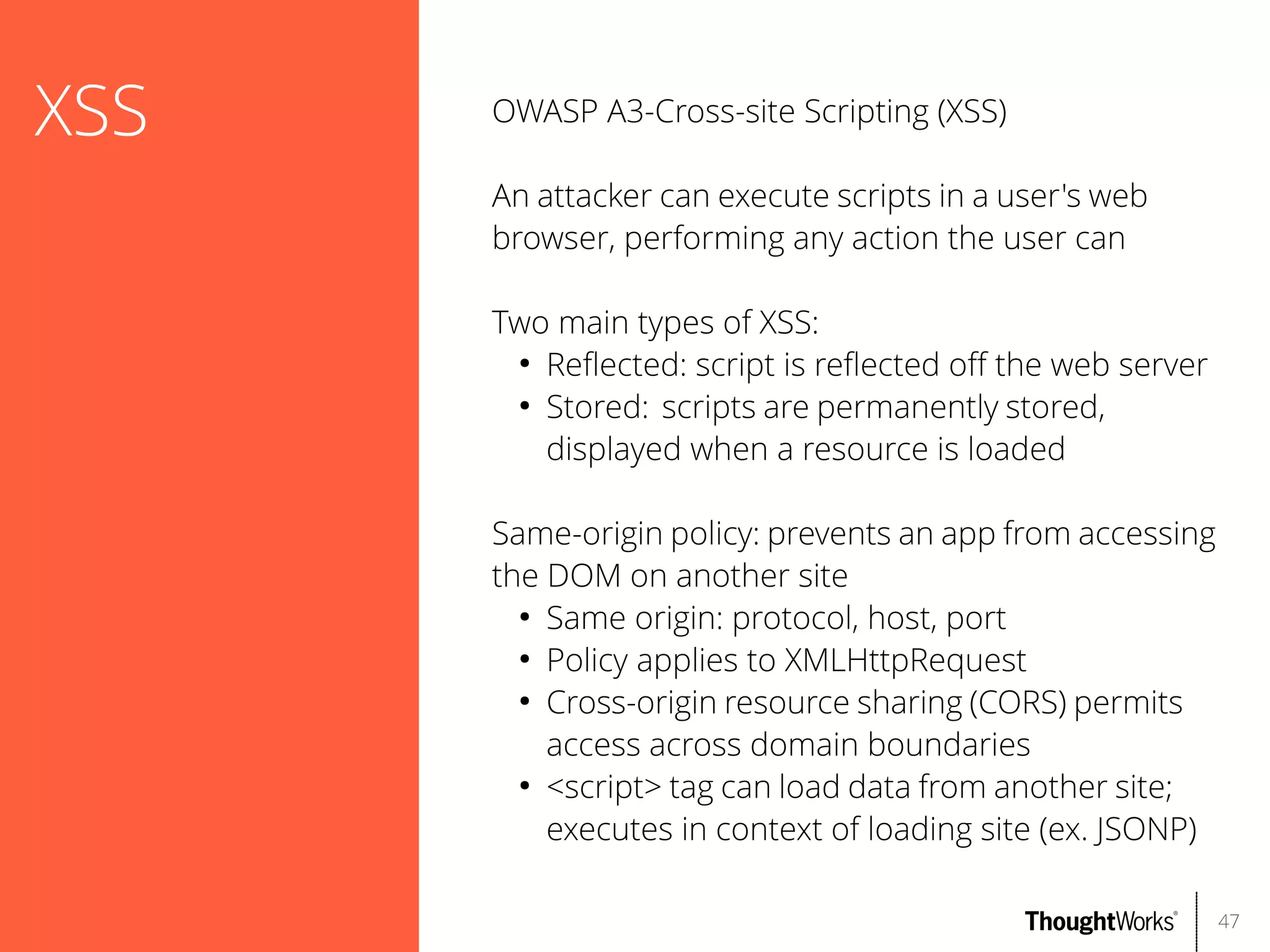
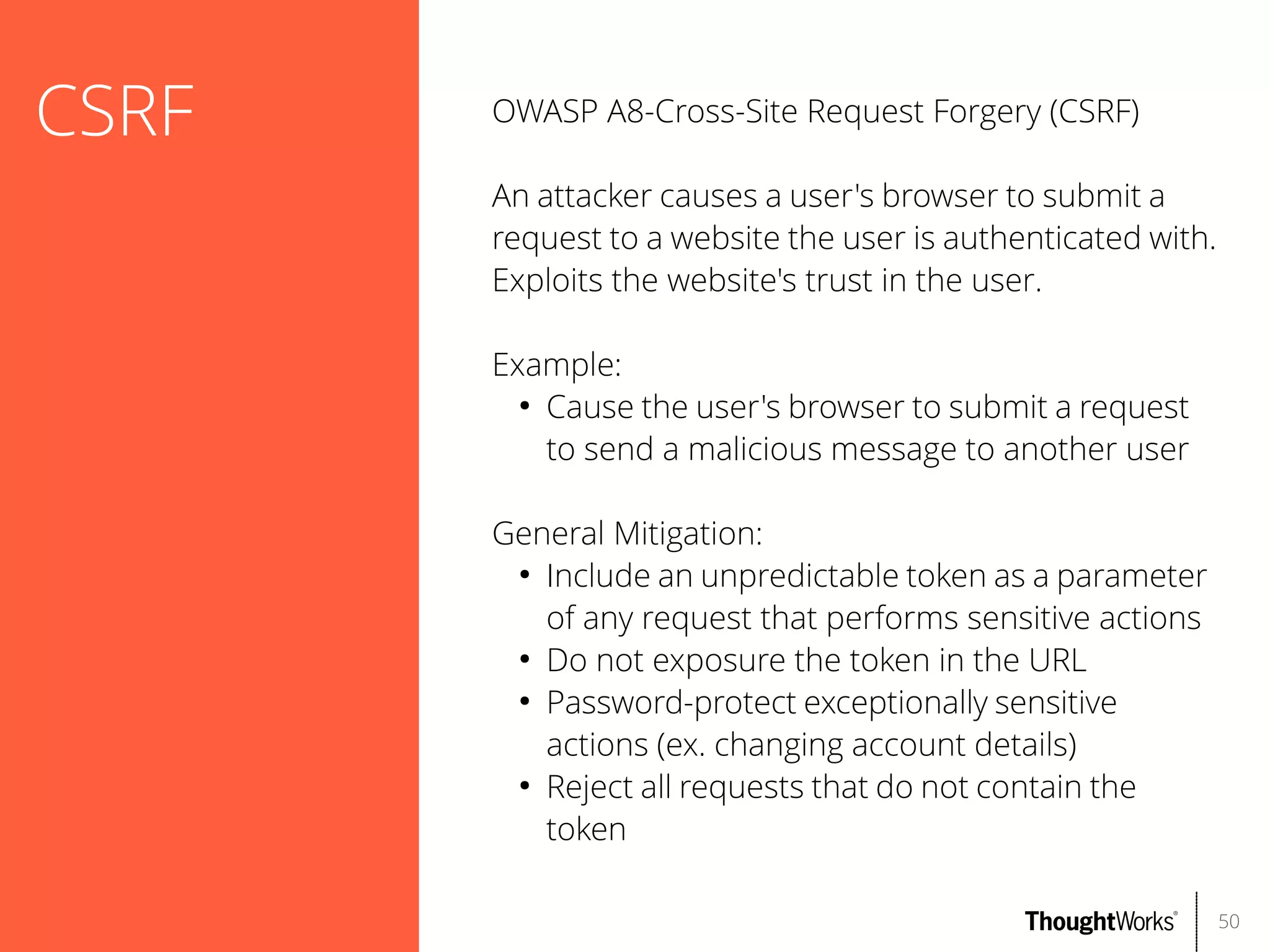
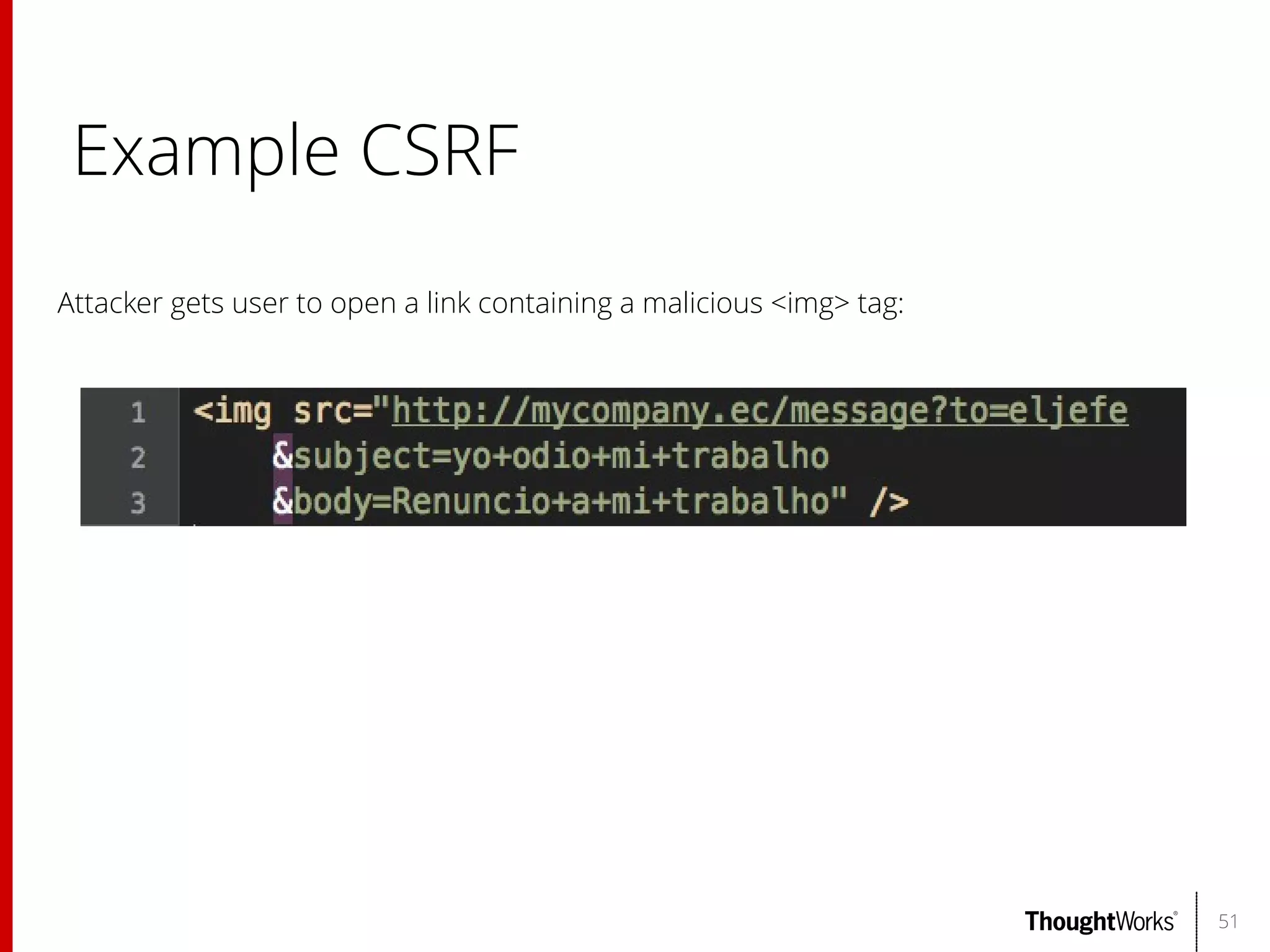
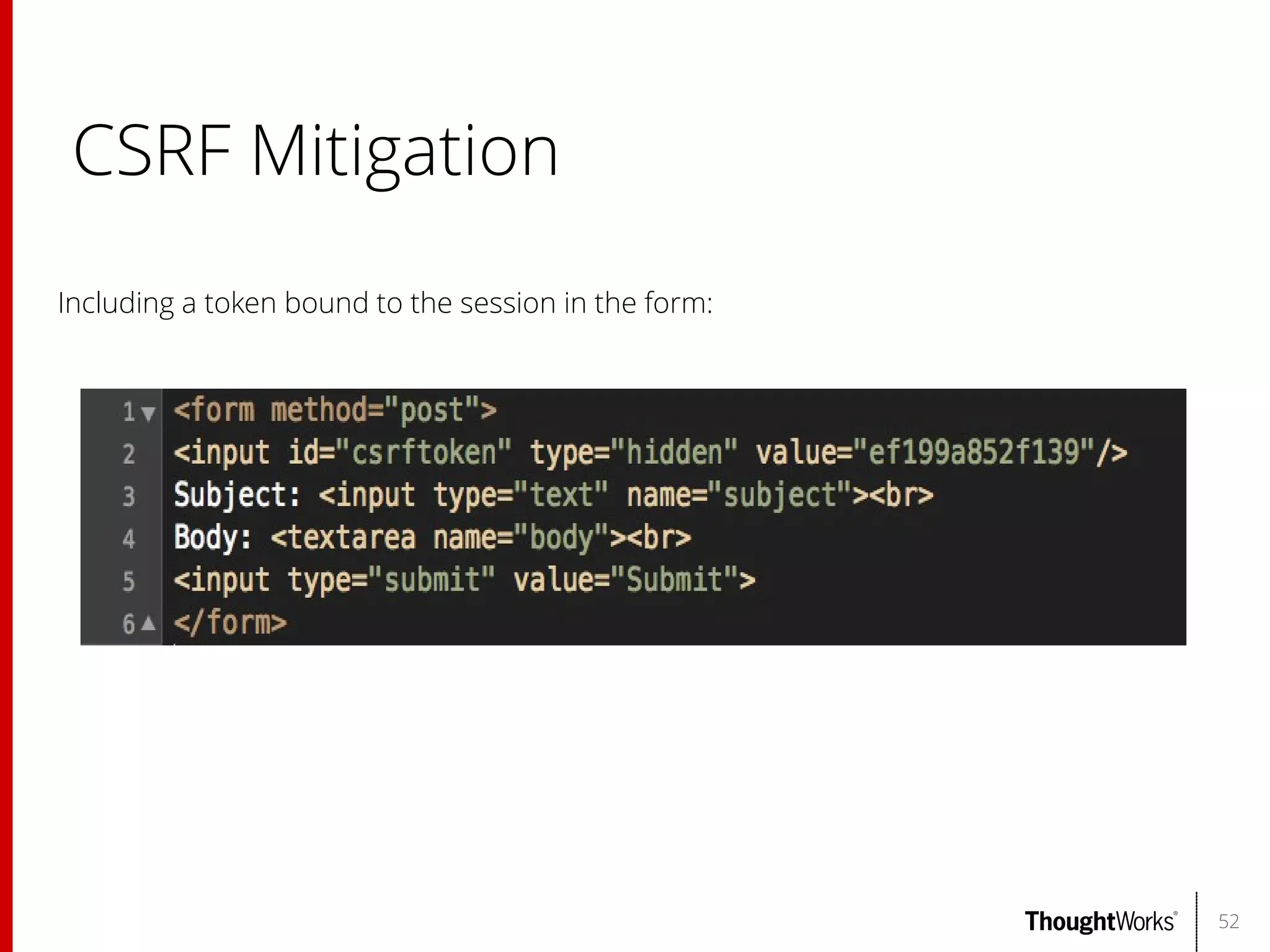
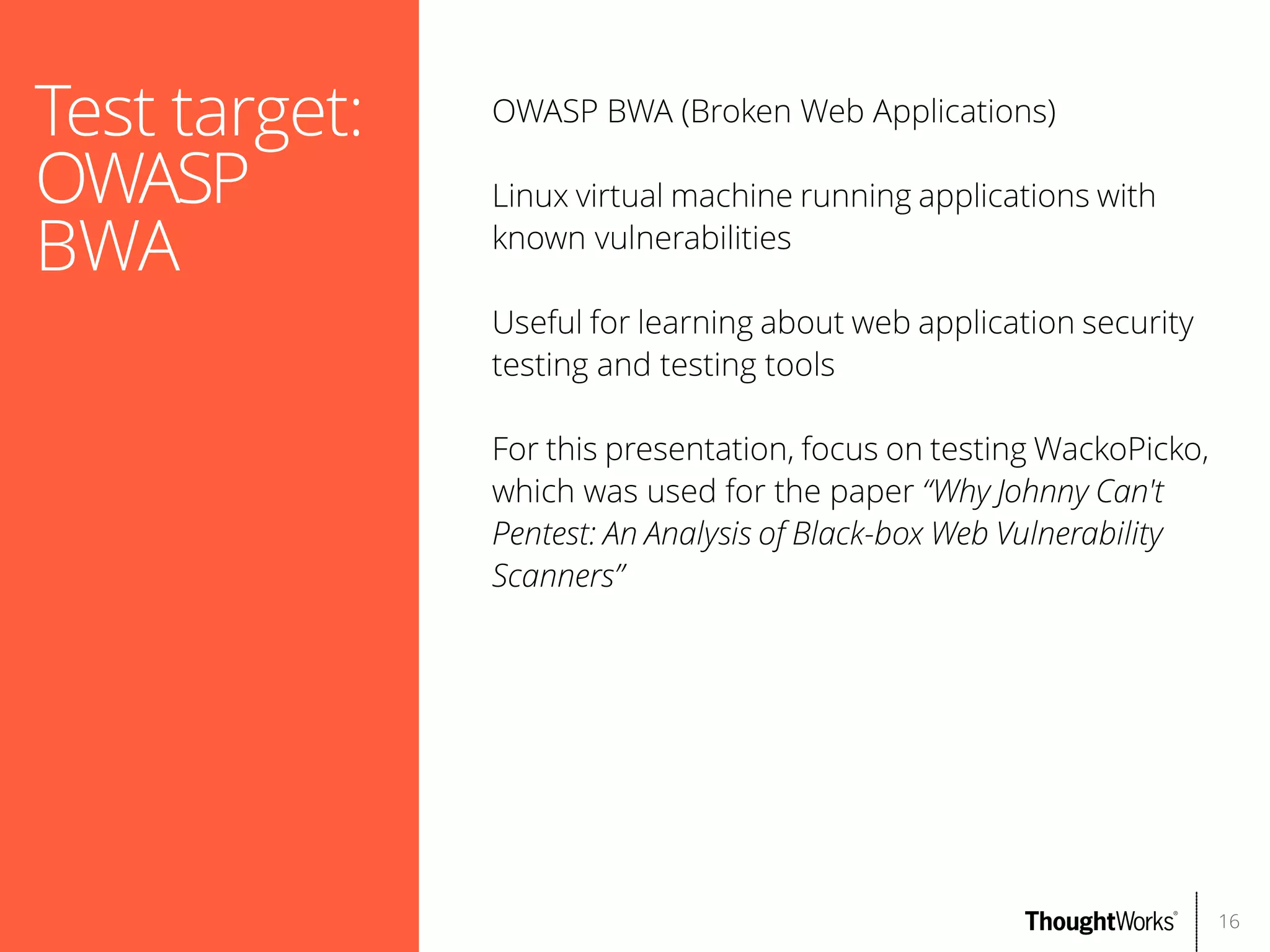
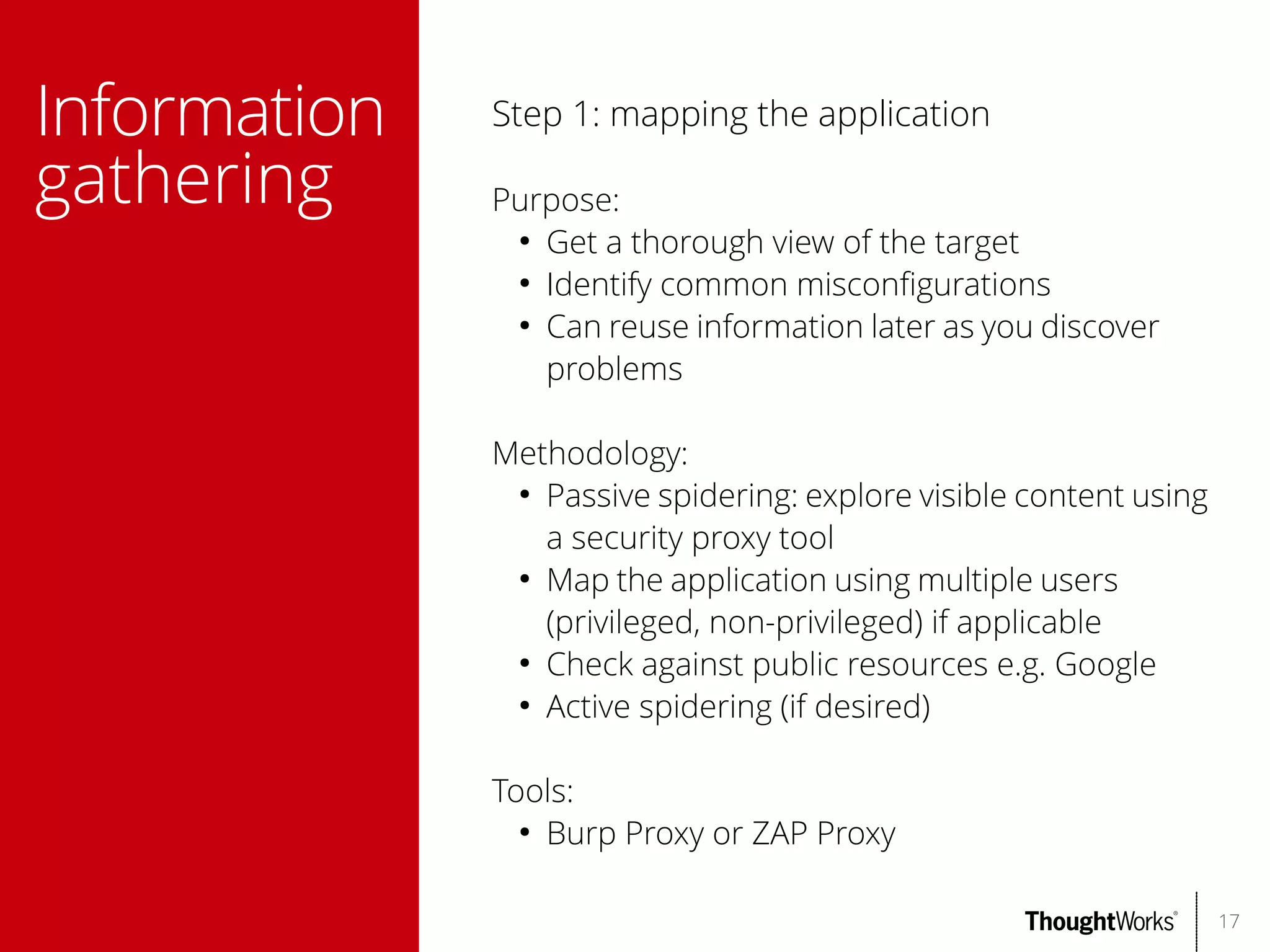
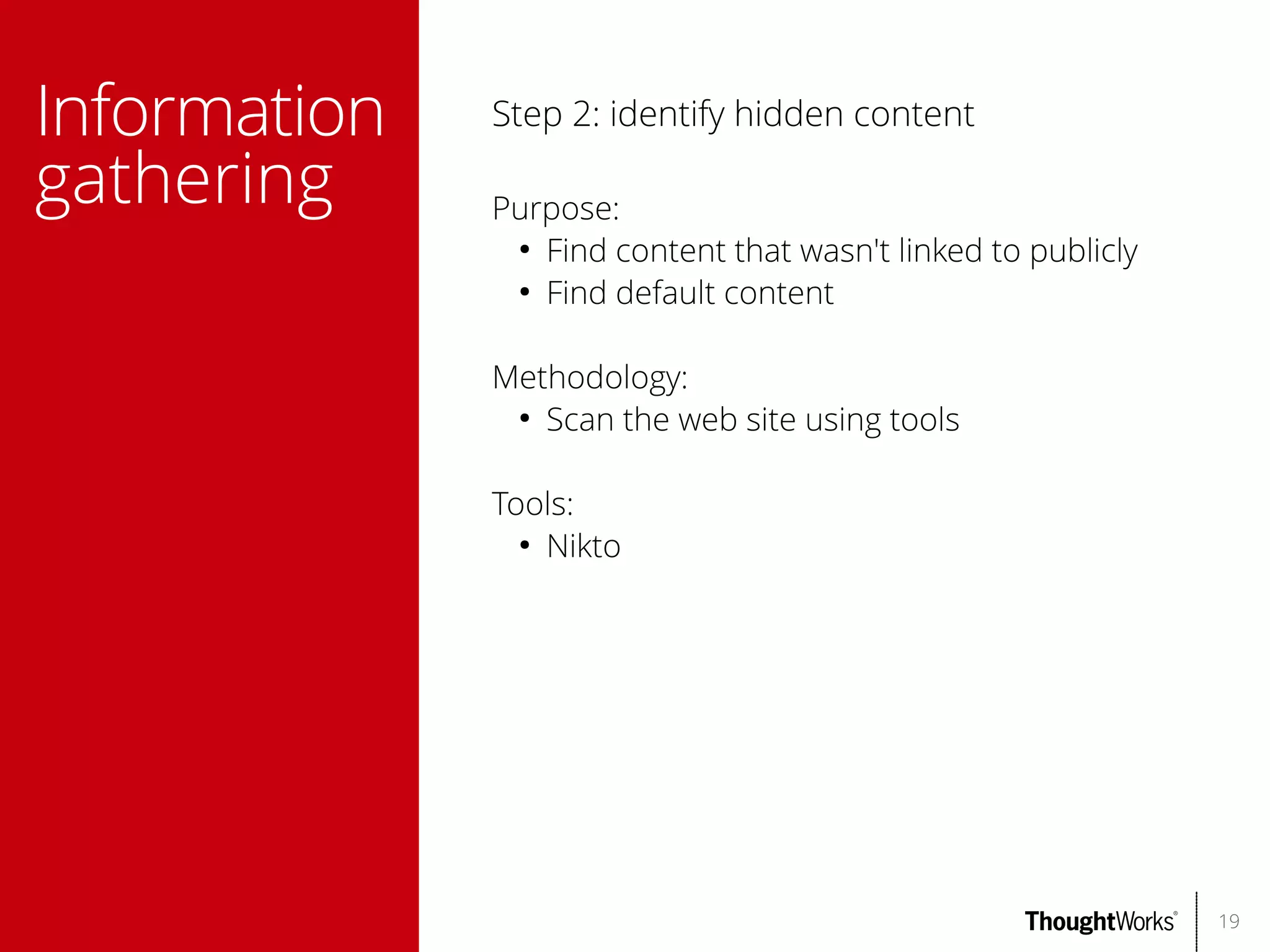
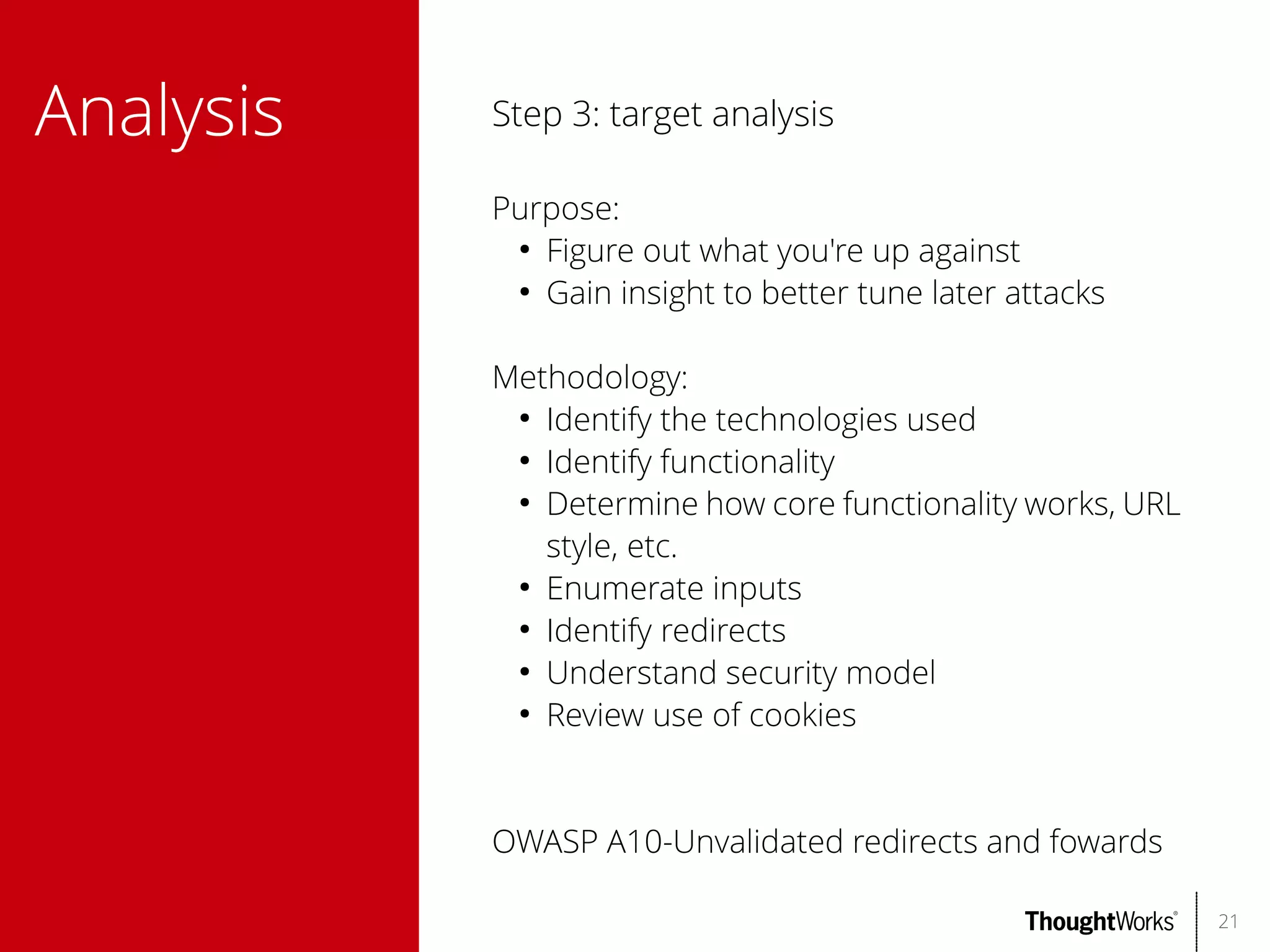
The document outlines web application security, discussing common classes of vulnerabilities, testing methodologies, and tools for developers and testers to enhance security. It includes a guide on the threat evolution, testing plans, and specific tools like Burp Suite and OWASP ZAP. Additionally, it details best practices for authentication, access control, and input validation to mitigate risks and protect sensitive data.





![OWASP Zed
Attack
Proxy (ZAP)
Highly-rated security tool [1]
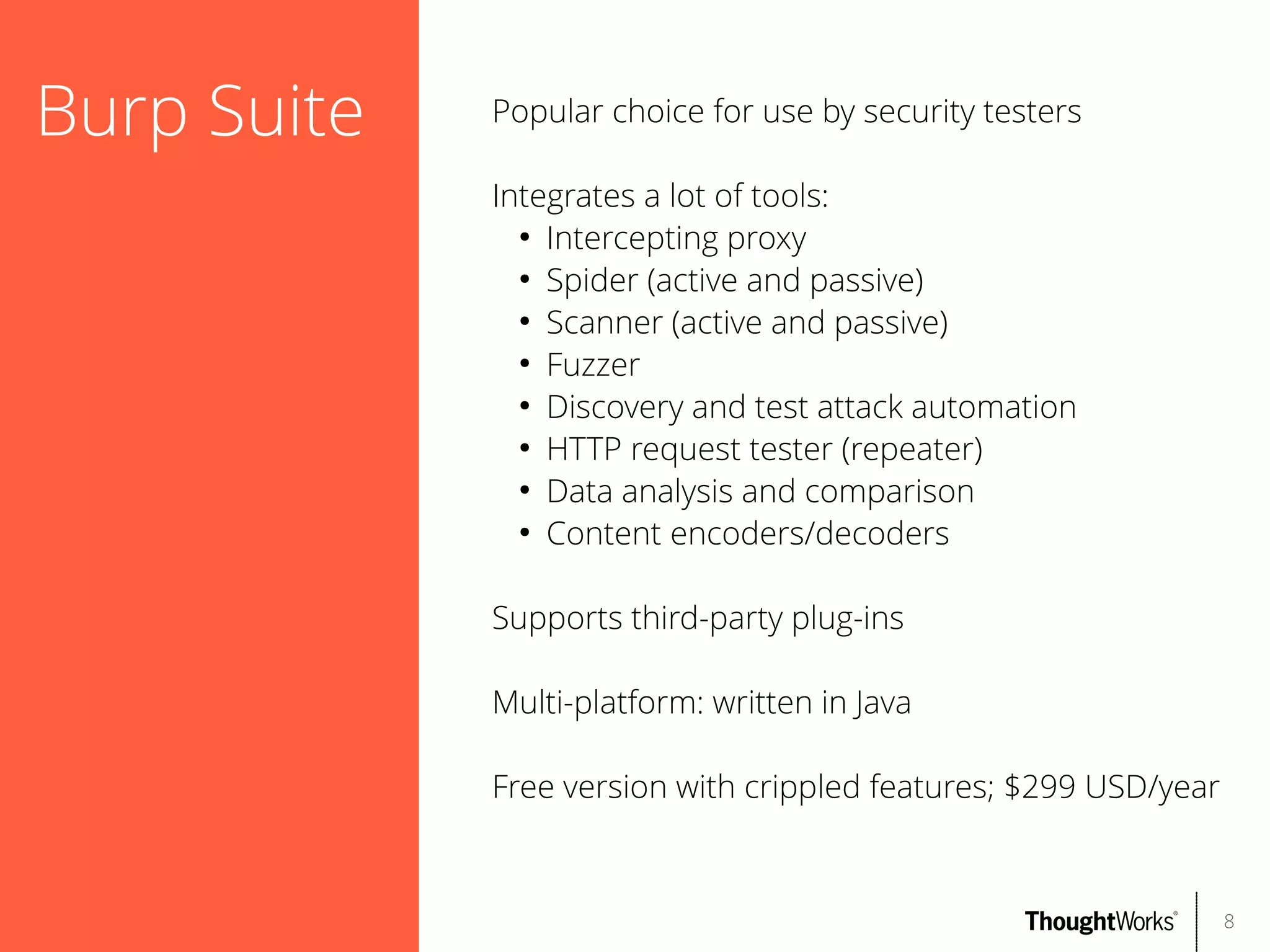
Provides many useful functions:
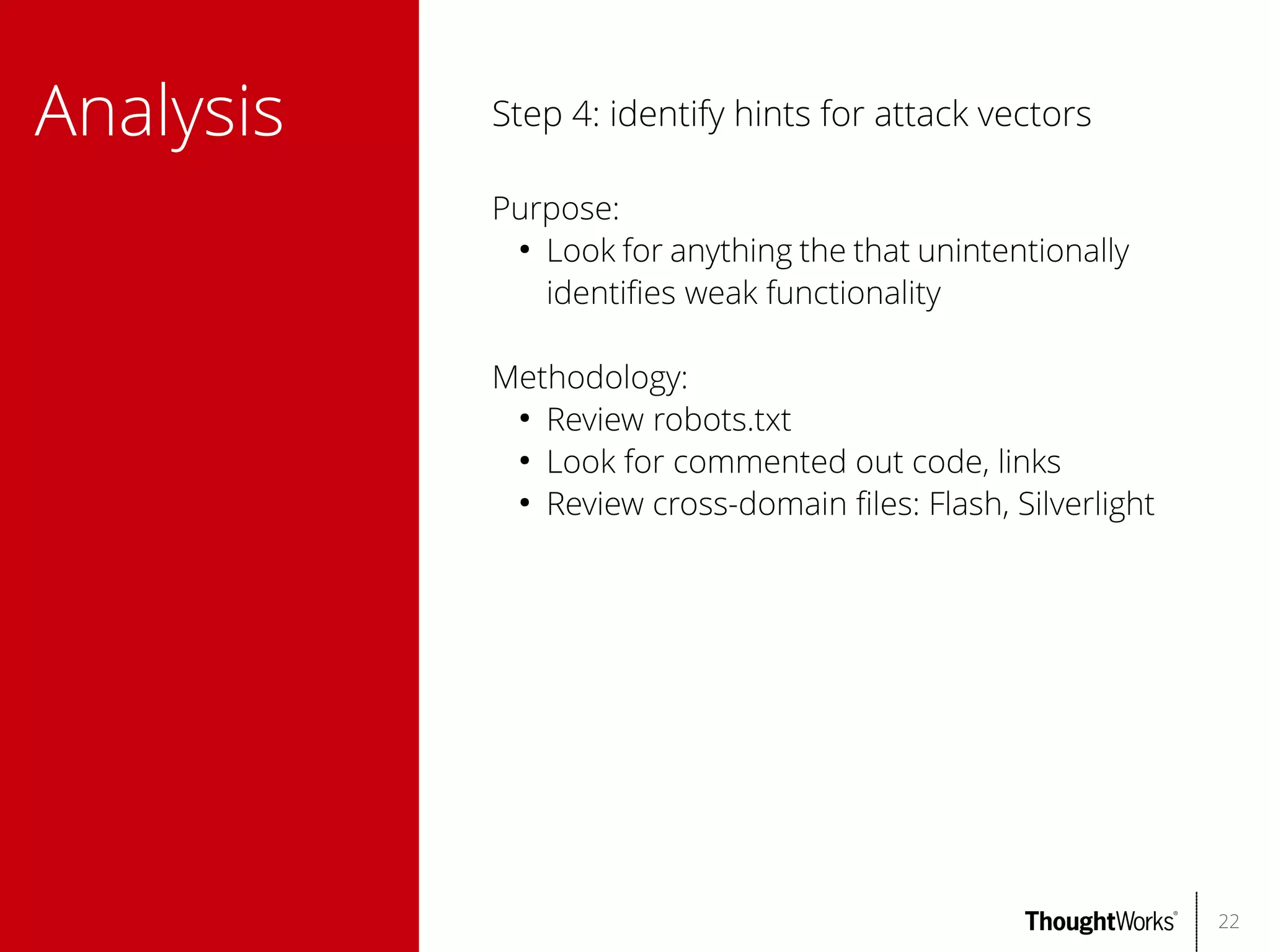
●
Intercepting proxy
●
Spider (active and passive; supports Ajax)
●
Scanner (active and passive)
●
Fuzzer
●
File/directory brute forcer
Supports third-party add-ons; online marketplace
Multi-platform: Swing Java
Open source; Apache License 2.0
[1] http://www.toolswatch.org/2013/12/2013-top-security-tools-as-votedby-toolswatch-org-readers/
9](https://image.slidesharecdn.com/twnochegeekquito-webappsec-140207060321-phpapp01/75/Web-Application-Security-Introduction-to-common-classes-of-security-flaws-and-testing-methodologies-9-2048.jpg)




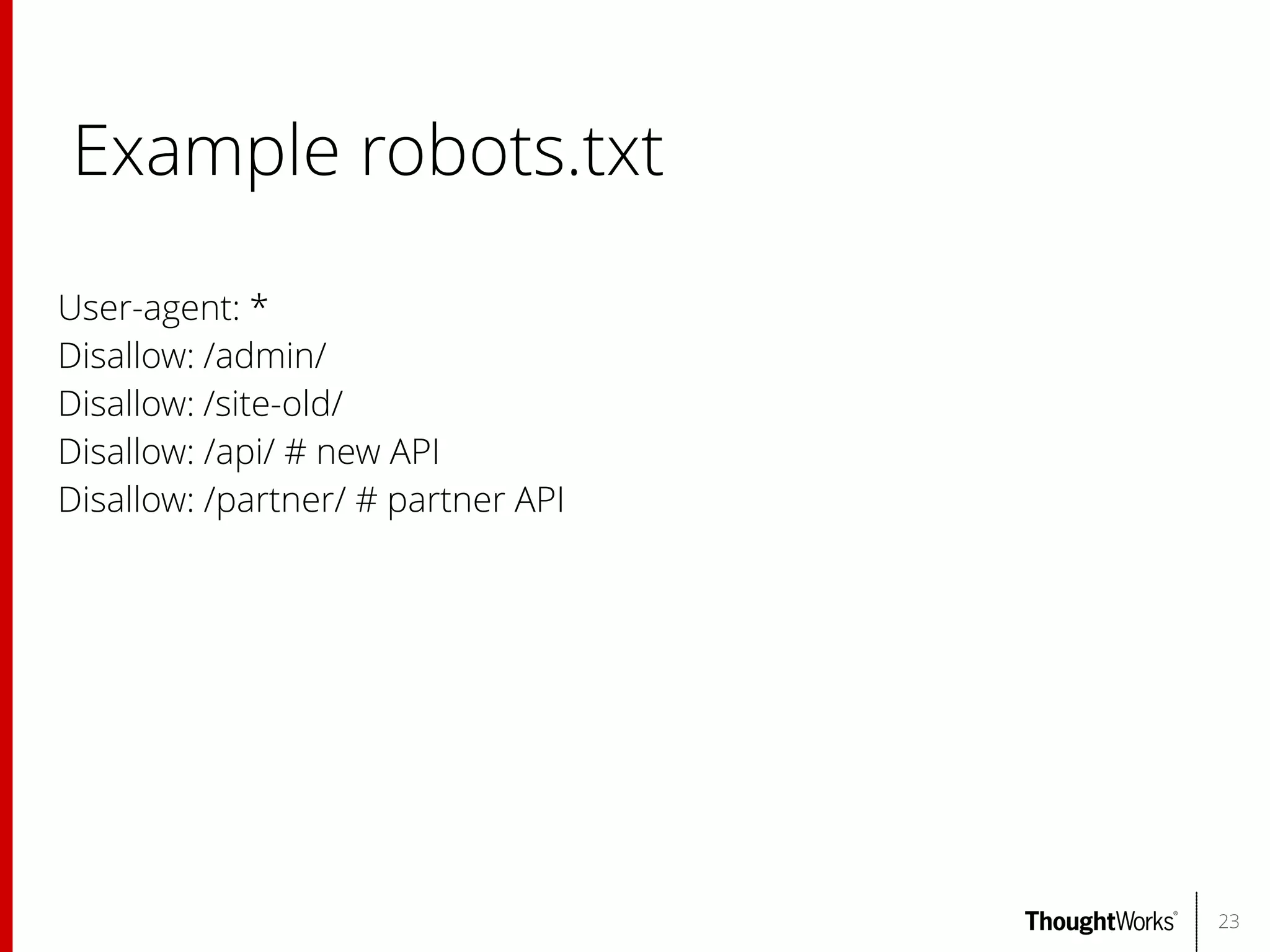


![Authentication
Most common passwords of 2013 [1]
1. 123456 (up 1)
2. password (down 1)
3. 12345678 (unchanged)
4. qwerty (up 1)
5. abc123 (down 1)
6. 123456789 (new)
7. 111111 (up 2)
8. 1234567 (up 5)
9. iloveyou (up 2)
10. adobe123 (new)
11. 123123 (up 5)
12. Admin (new)
13. 1234567890 (new)
14. letmein (down 7)
15. photoshop (new)
[1] http://splashdata.com/press/worstpasswords2013.htm
31](https://image.slidesharecdn.com/twnochegeekquito-webappsec-140207060321-phpapp01/75/Web-Application-Security-Introduction-to-common-classes-of-security-flaws-and-testing-methodologies-31-2048.jpg)