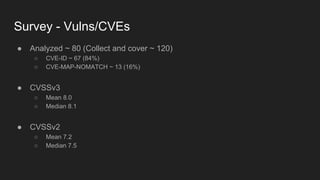
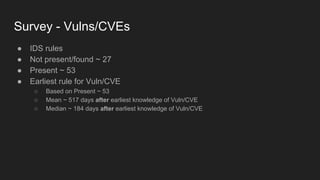
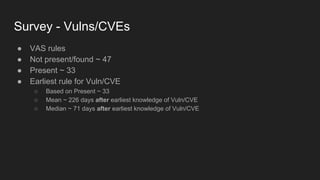
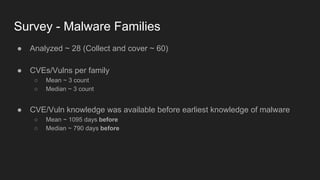
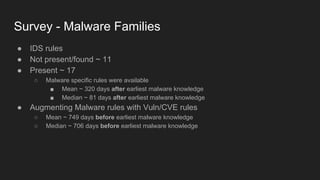
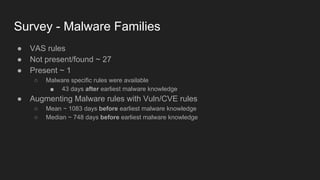
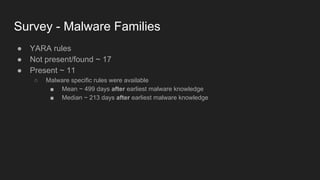
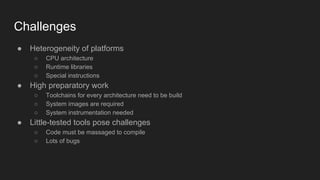
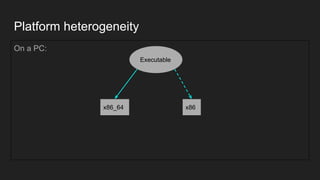
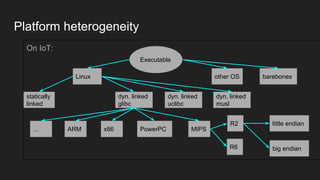
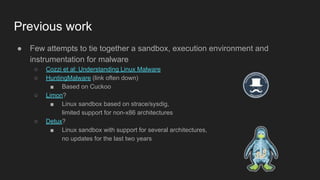
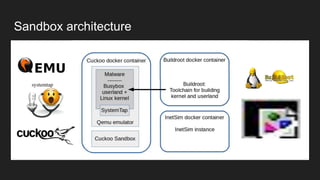
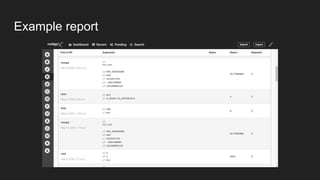
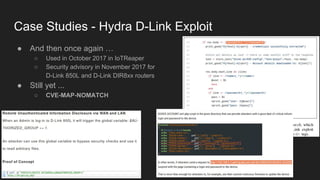
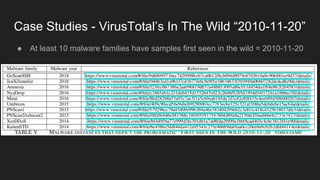
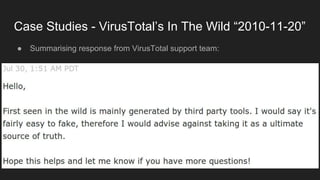
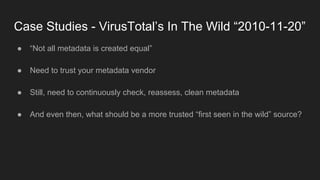
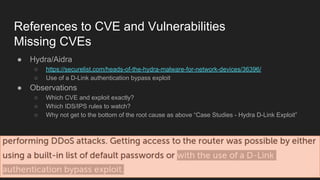
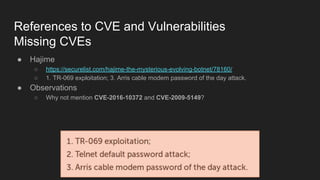
This document provides an overview of a study on IoT malware. It discusses the challenges of analyzing IoT malware due to platform heterogeneity. It outlines the methodology used, which included collecting malware samples, metadata, and reports. Metadata and surveys of vulnerabilities and malware families are presented. The document describes a sandbox for dynamic analysis of IoT malware and provides example reports. It includes two case studies on the Hydra exploit and issues with metadata. Key takeaways focus on the importance of metadata analysis and improving vulnerability management and defense for IoT security.