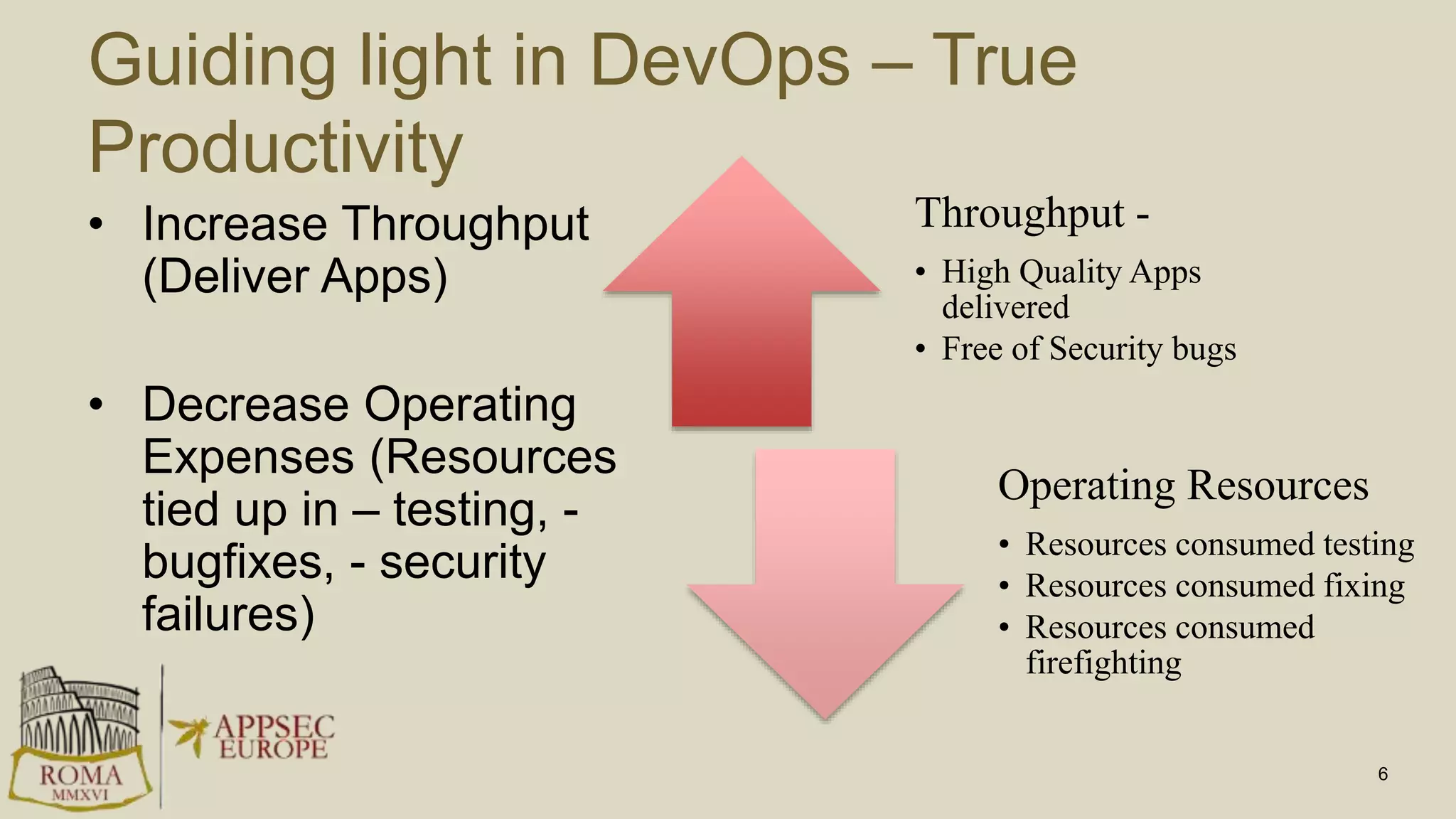
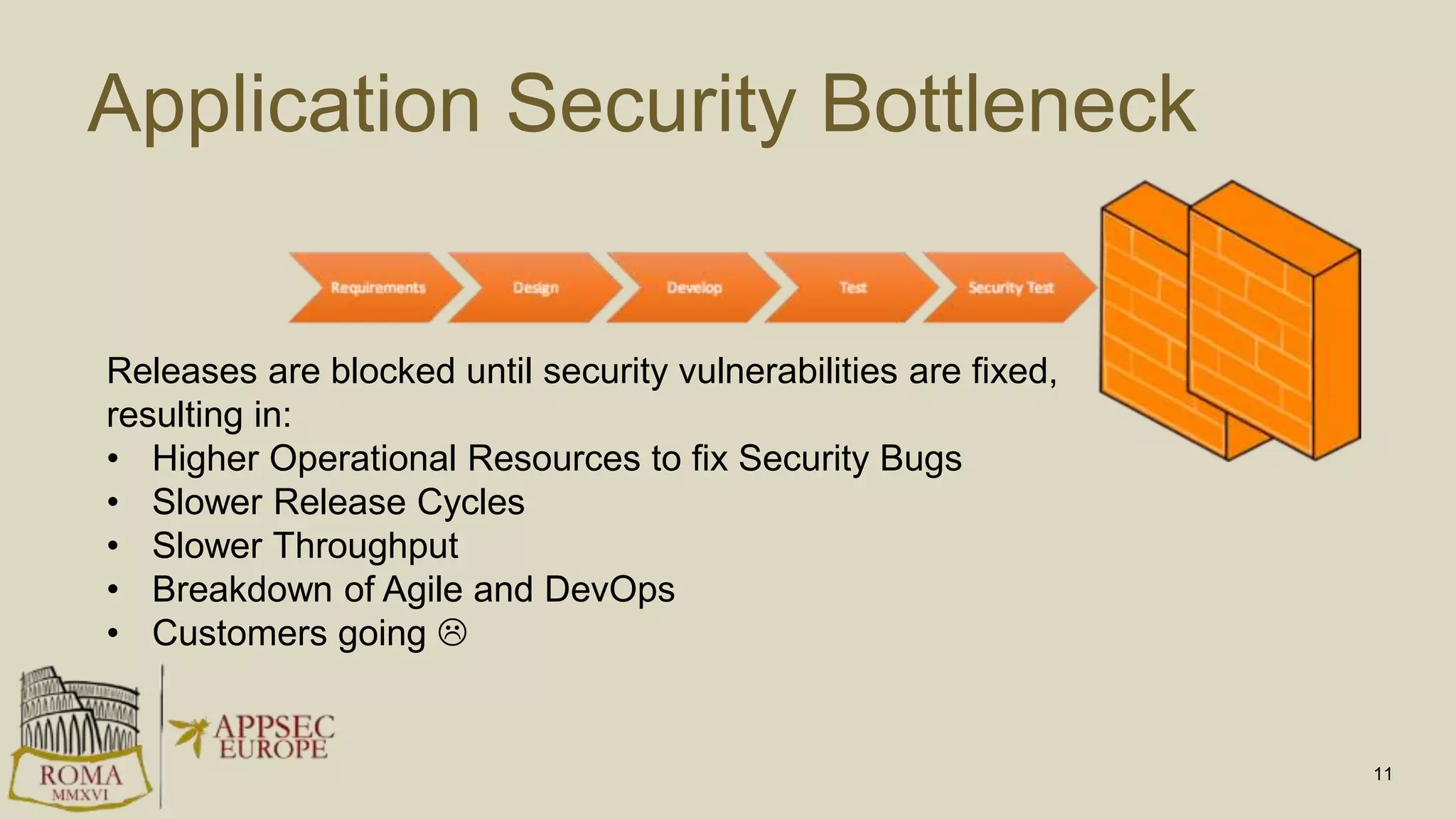
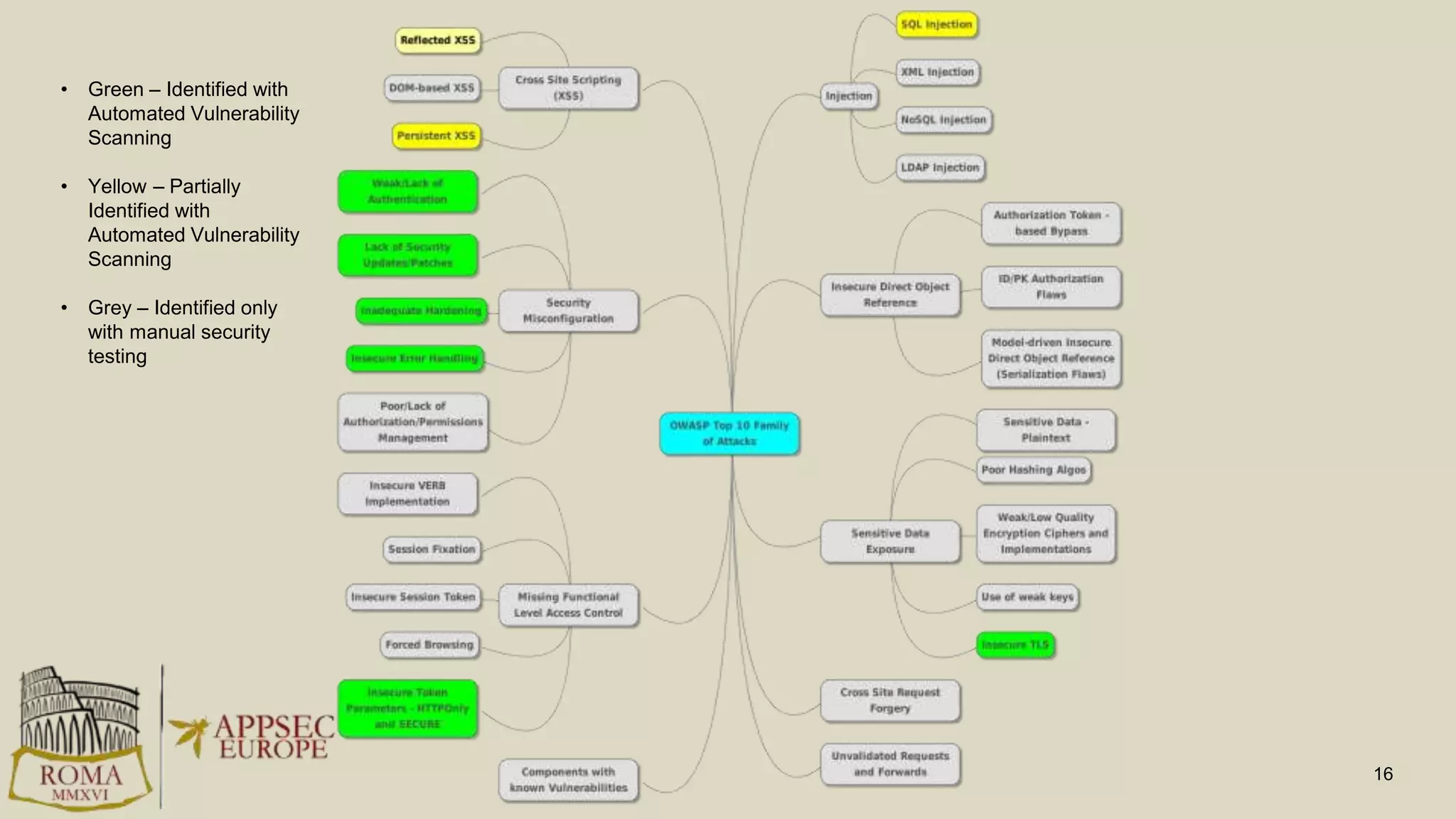
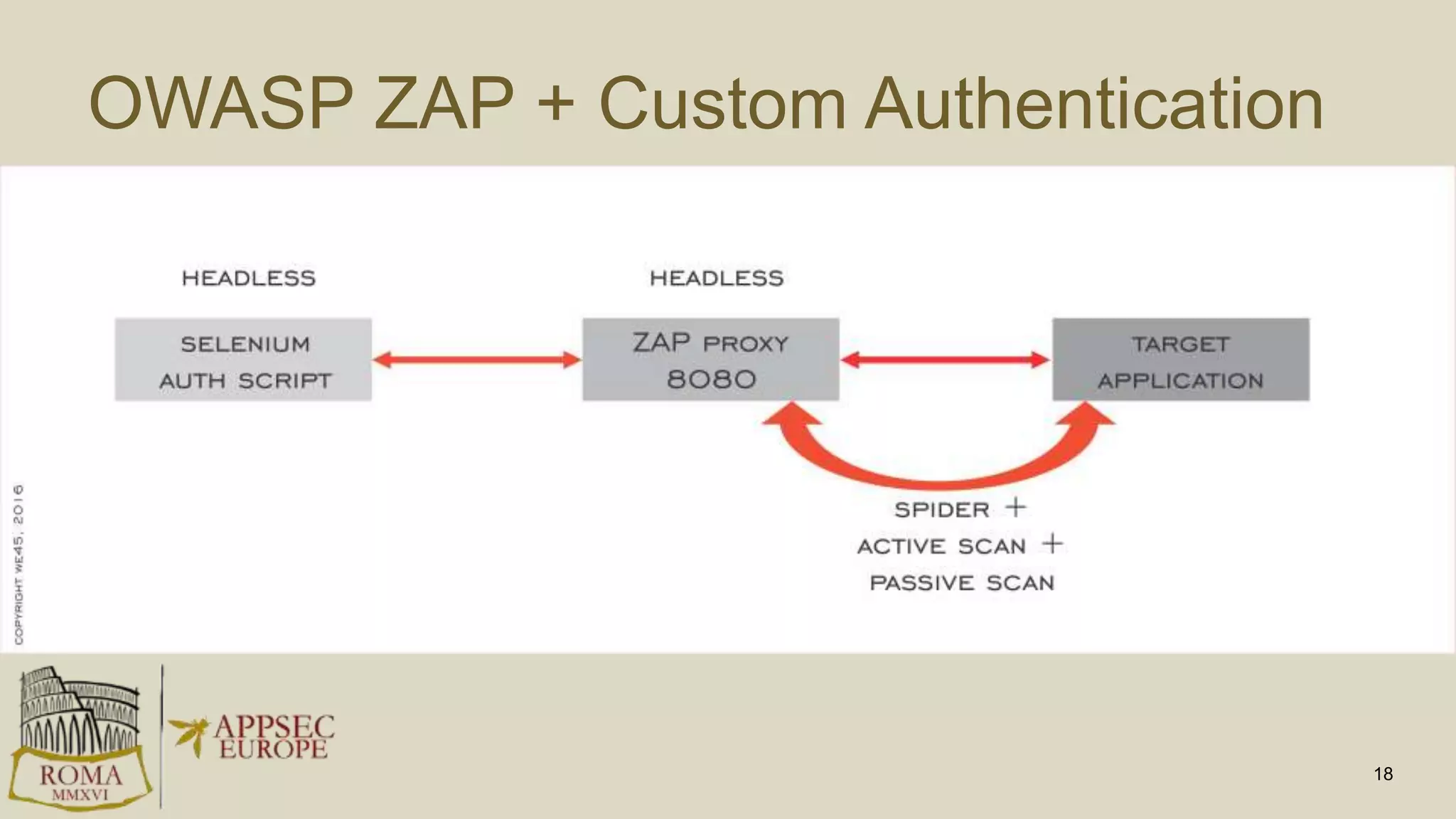
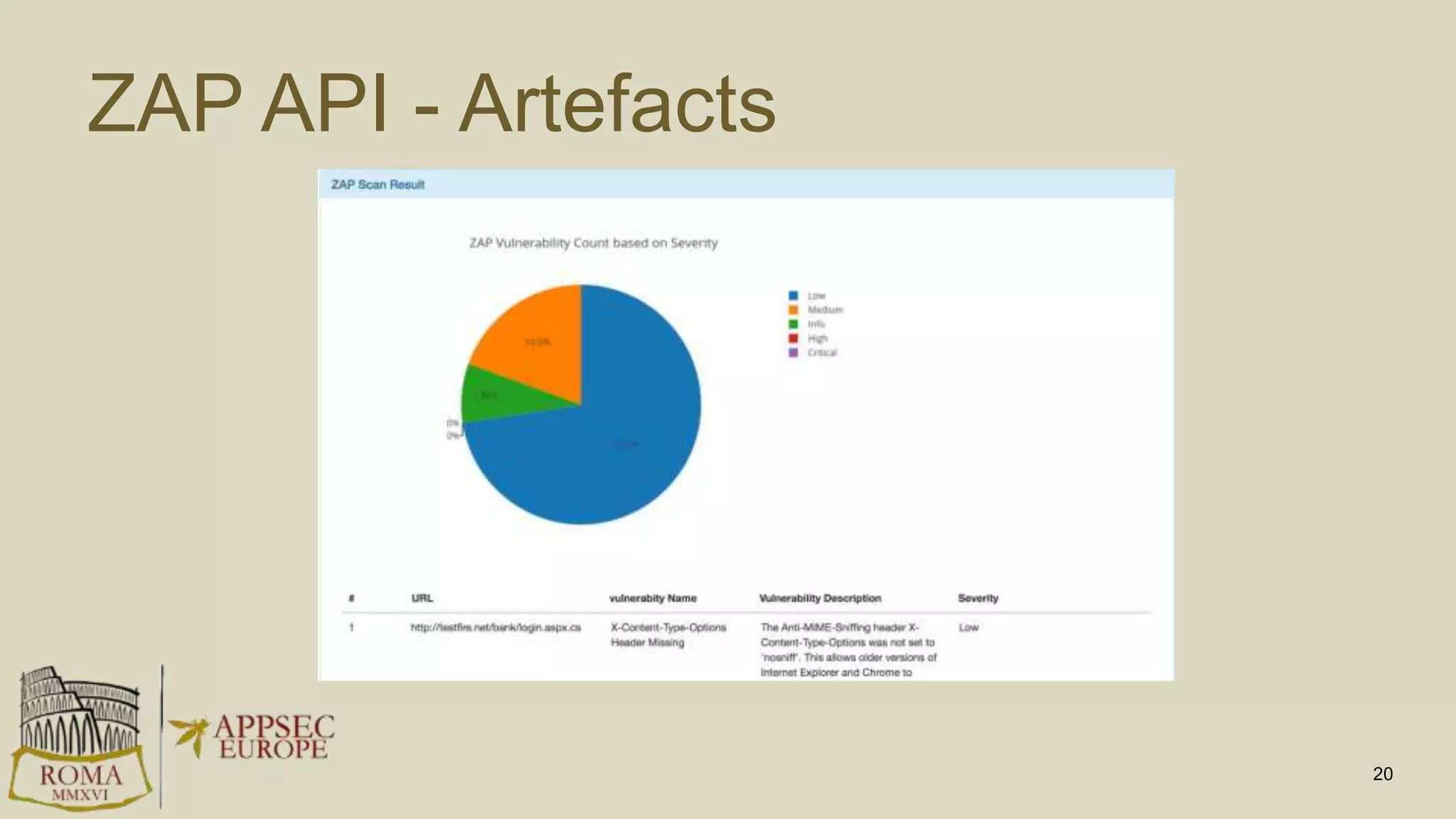
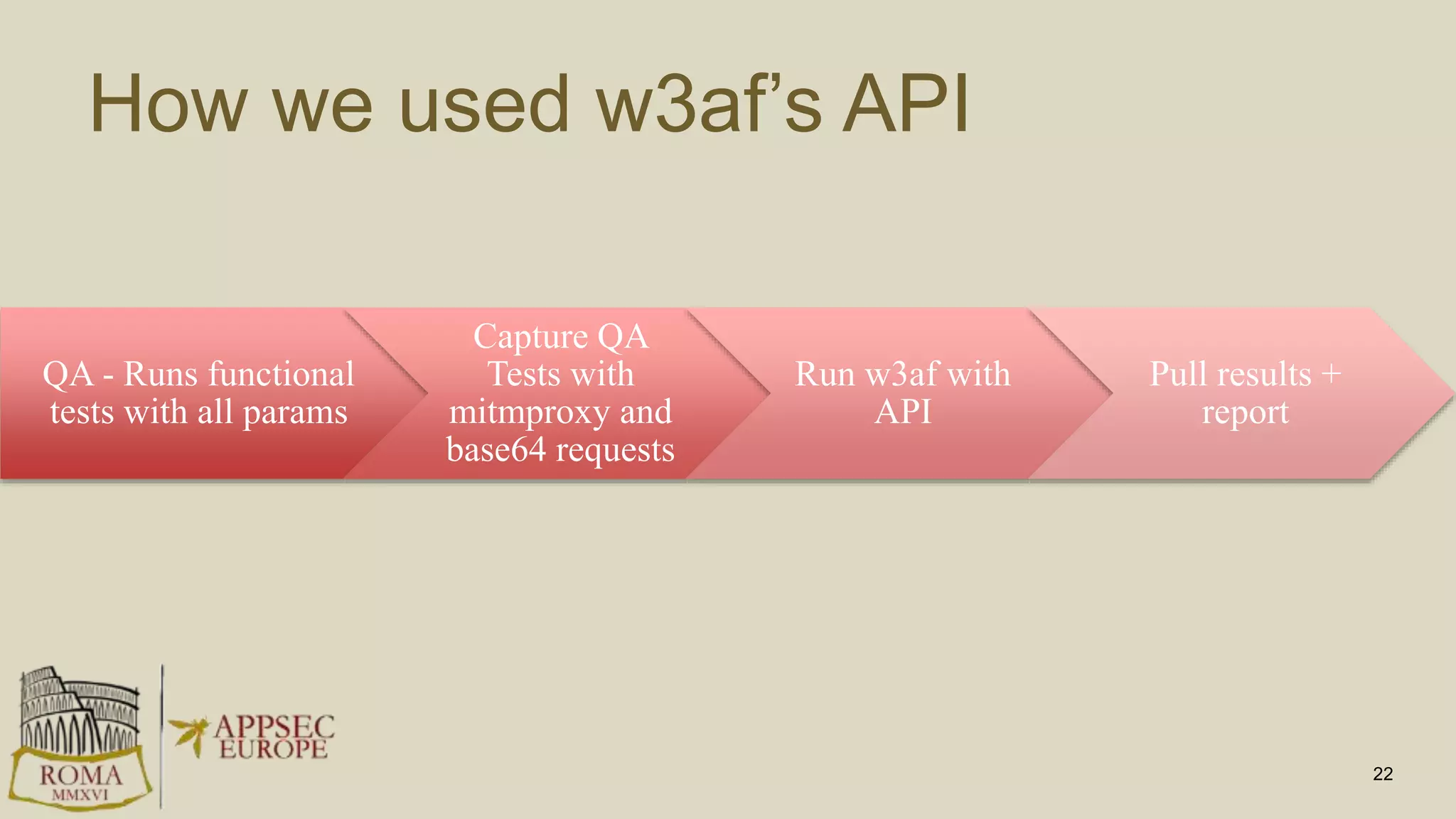
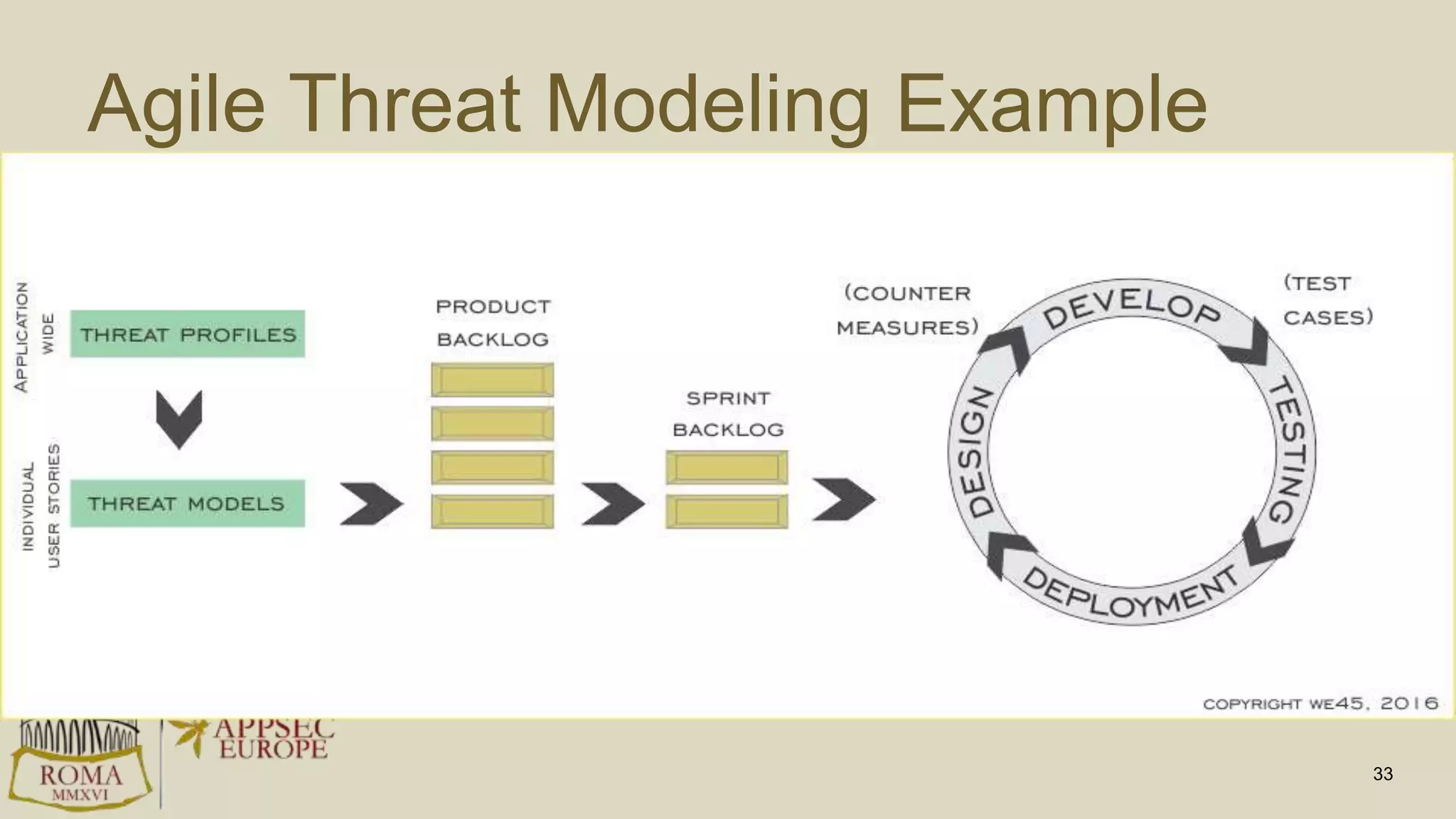
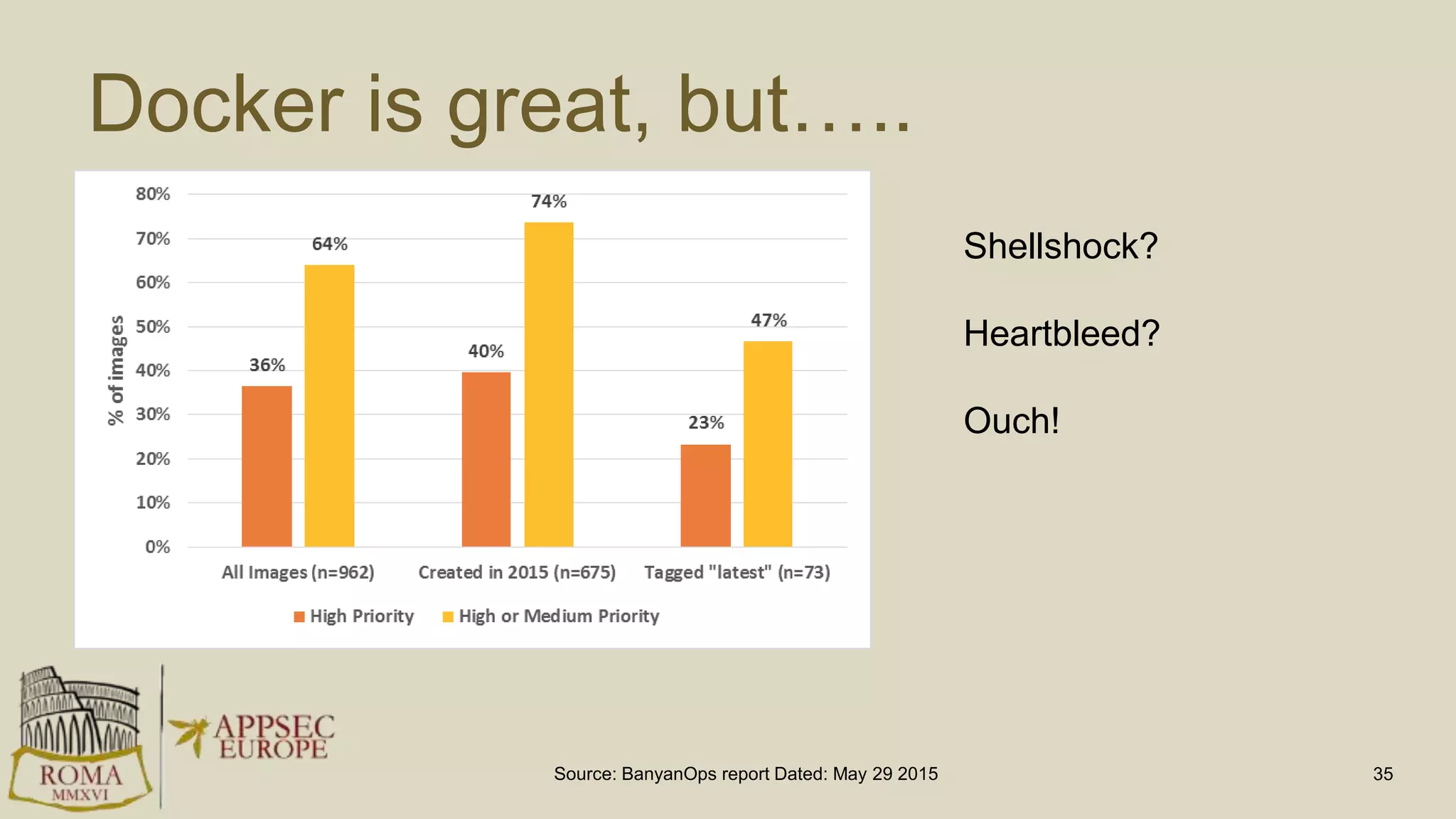
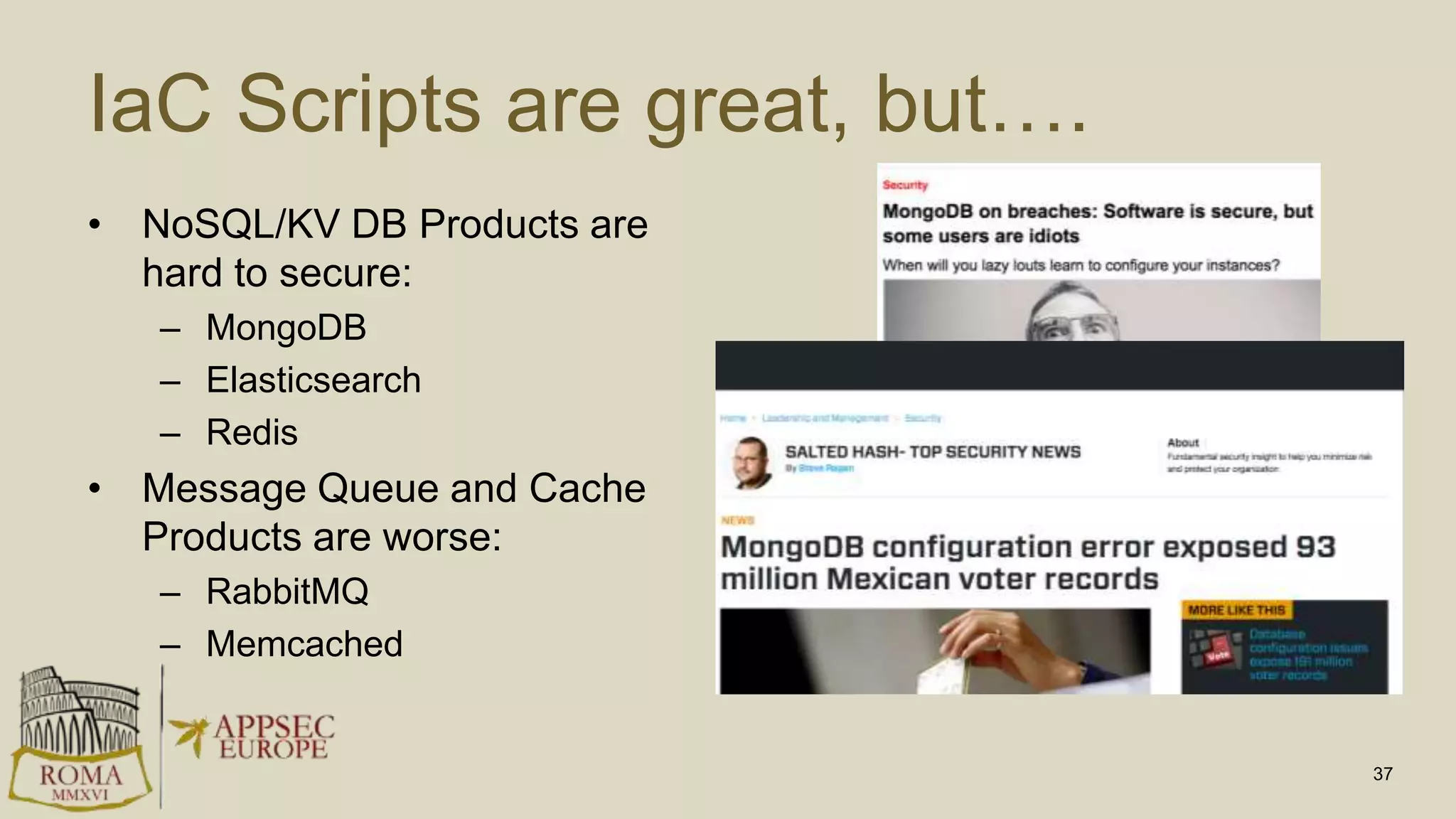
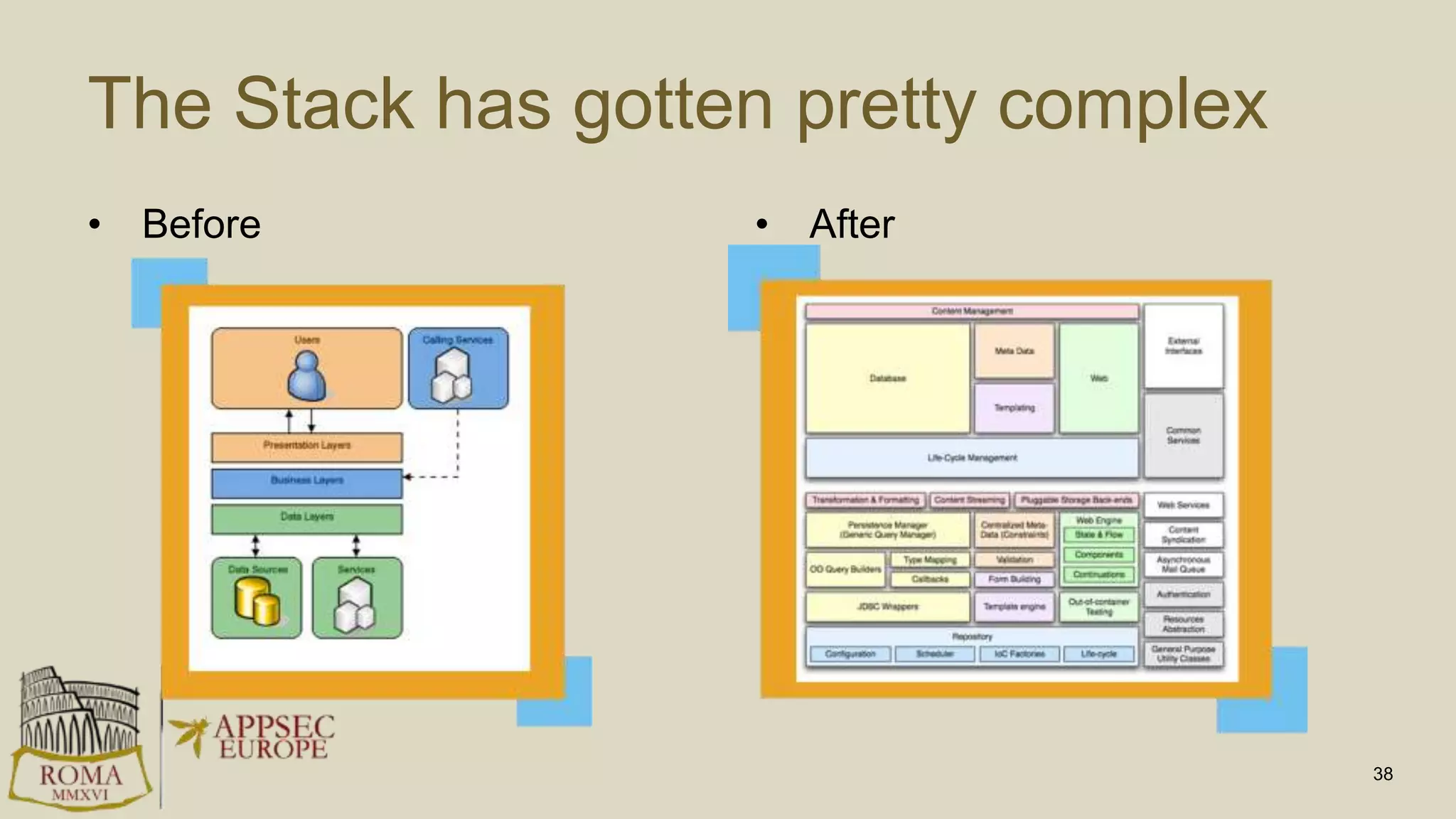
Abhay Bhargav, CEO of we45, discusses the importance of integrating security into DevOps practices, emphasizing the need for improved application security measures to prevent vulnerabilities during rapid deployments. He presents various case studies that highlight the shortcomings of current security scanning methods and advocates for collaborative and iterative threat modeling approaches. The presentation concludes with strategies for ensuring DevOps and security can coexist effectively within an organization.