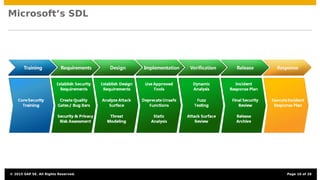
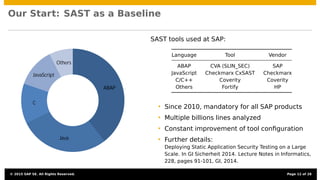
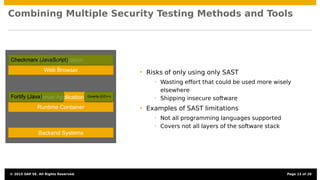
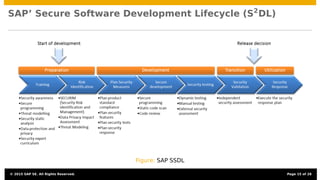
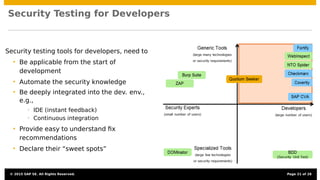
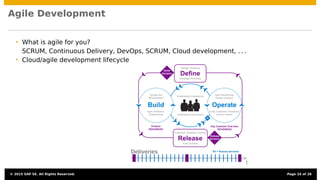
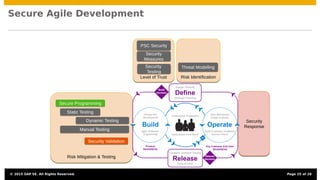
The document discusses the integration of security testing within agile software development processes, specifically at SAP, emphasizing that security testing should be a continual part of development rather than a final step. It outlines SAP’s risk-based security testing strategy, which incorporates multiple methods and tools to identify vulnerabilities early in the lifecycle. The presentation highlights the importance of promoting security awareness among developers and establishing collaboration between security experts and development teams to ensure robust secure software practices.