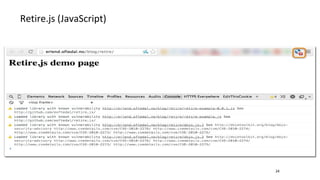
- Modern web application frameworks have powerful security features built-in like template escaping, database abstraction, session management, and authentication that help prevent vulnerabilities like XSS and SQL injection. These features are standard, well-tested, and usually more robust than custom code.
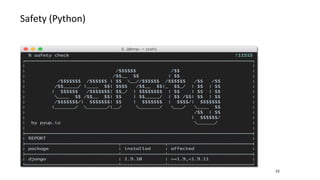
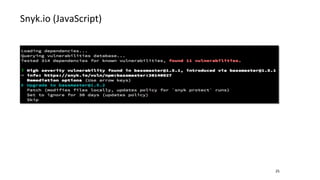
- Libraries and dependencies make up a large portion of modern applications. It is important to keep dependencies up-to-date with security patches and be careful about dependencies from untrusted sources like some examples on StackOverflow.
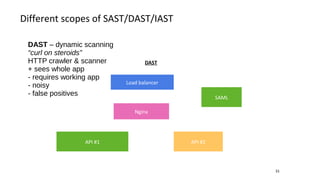
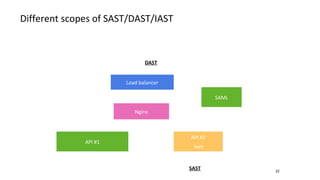
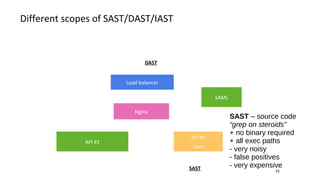
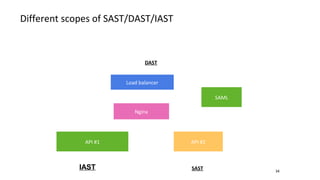
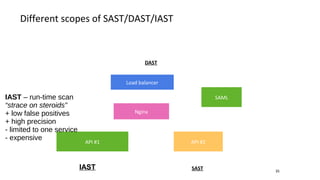
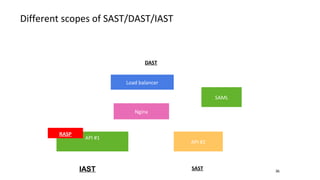
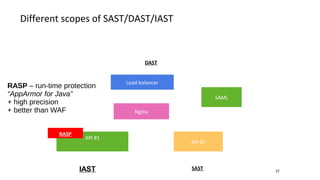
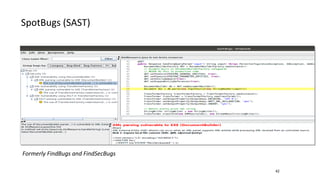
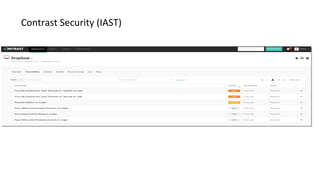
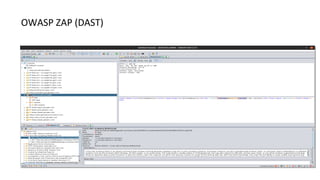
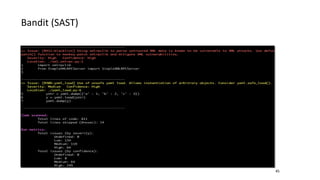
- Different security scanners like SAST, DAST, and IAST scan applications in different ways and at different stages, but an important factor is how well they understand the specific programming languages, frameworks, and technologies used in the application being