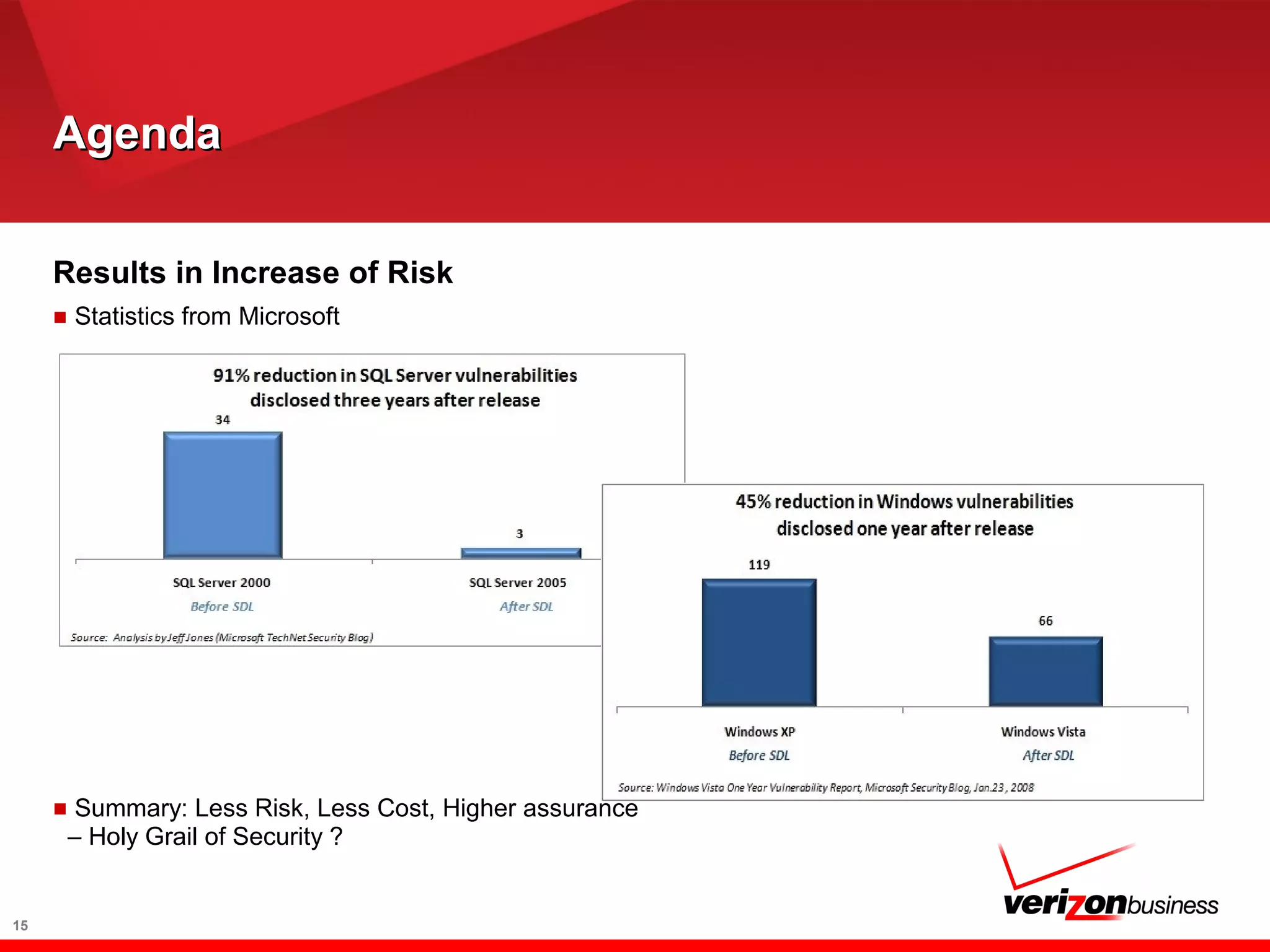
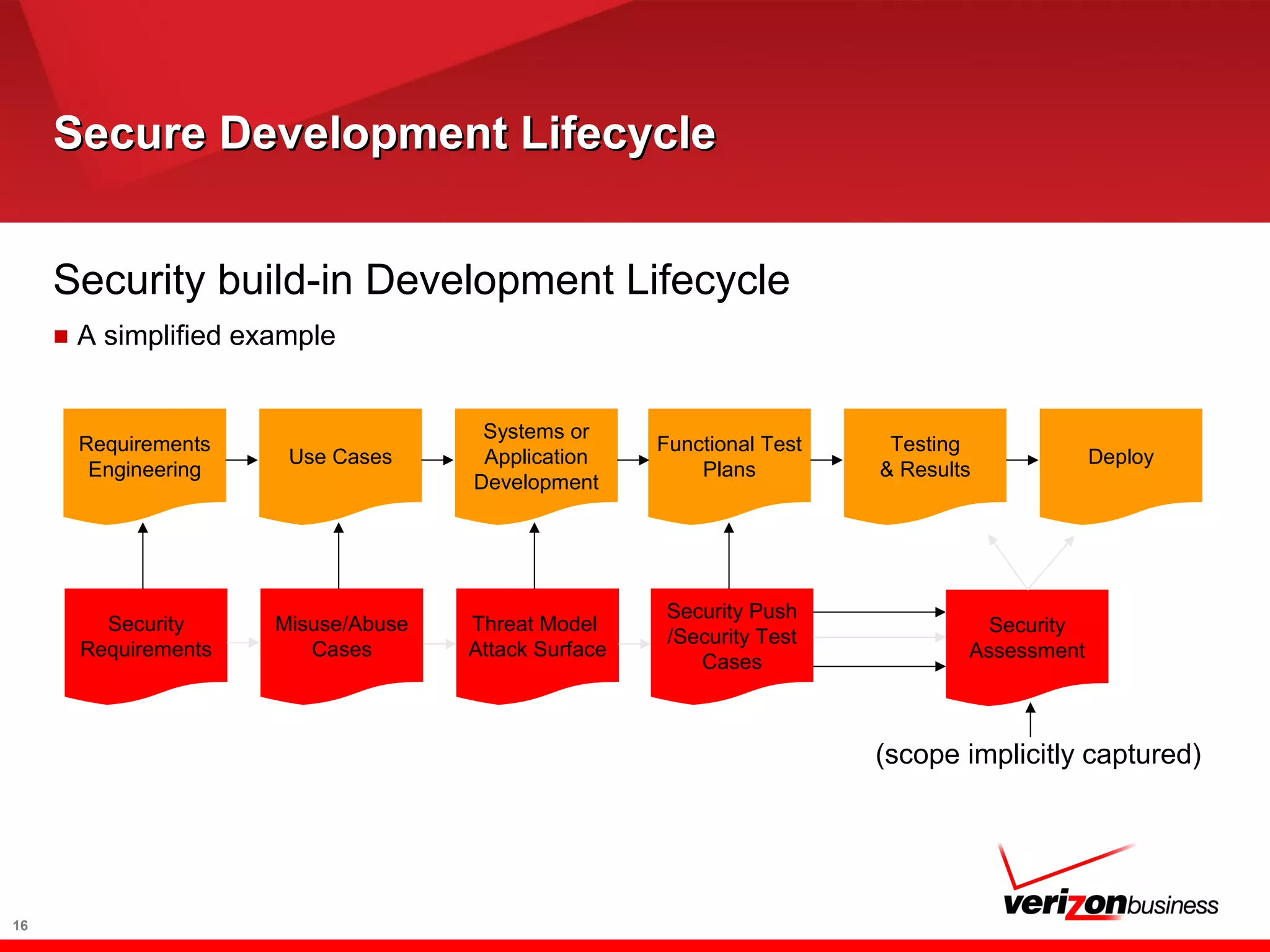
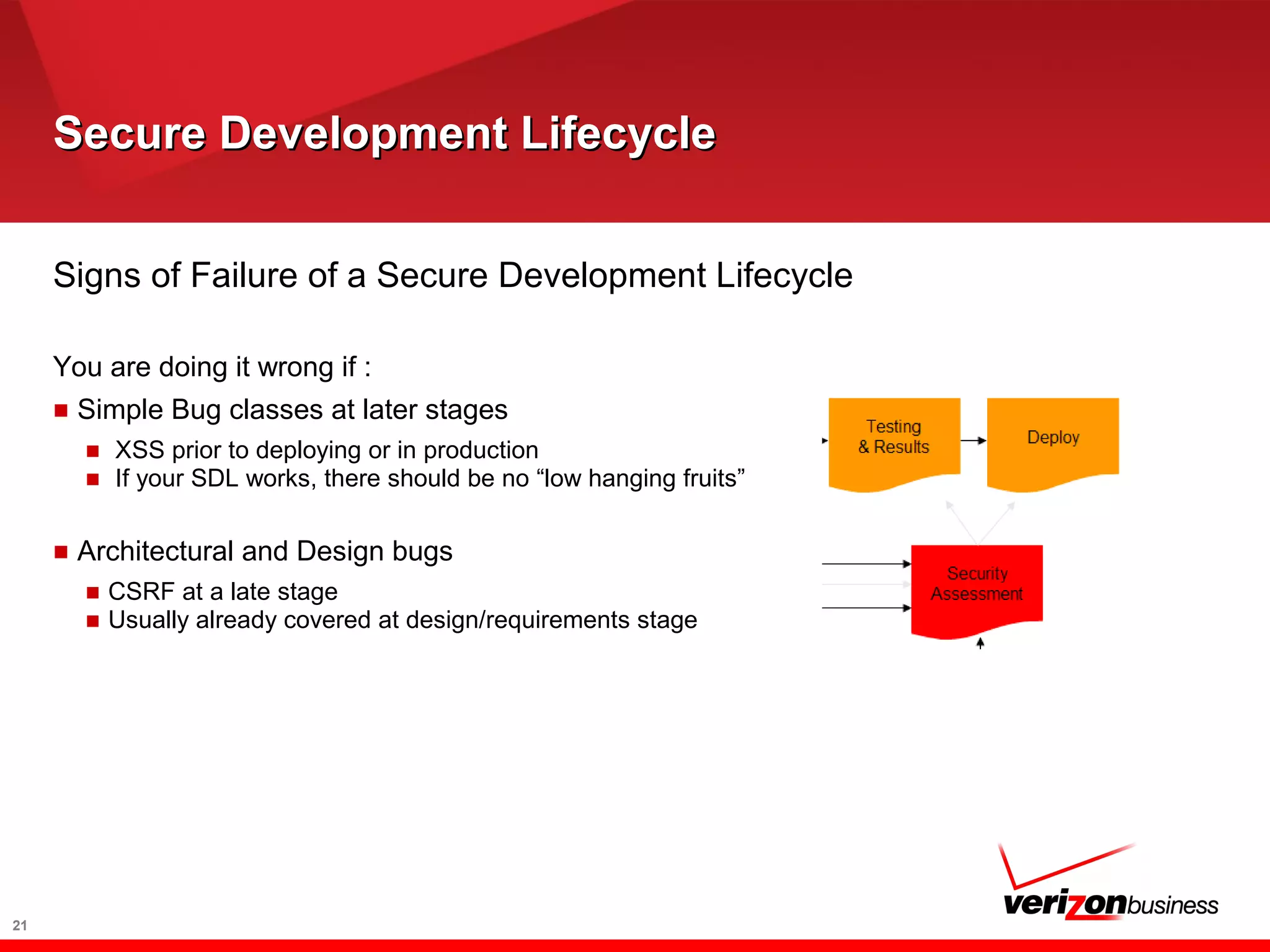
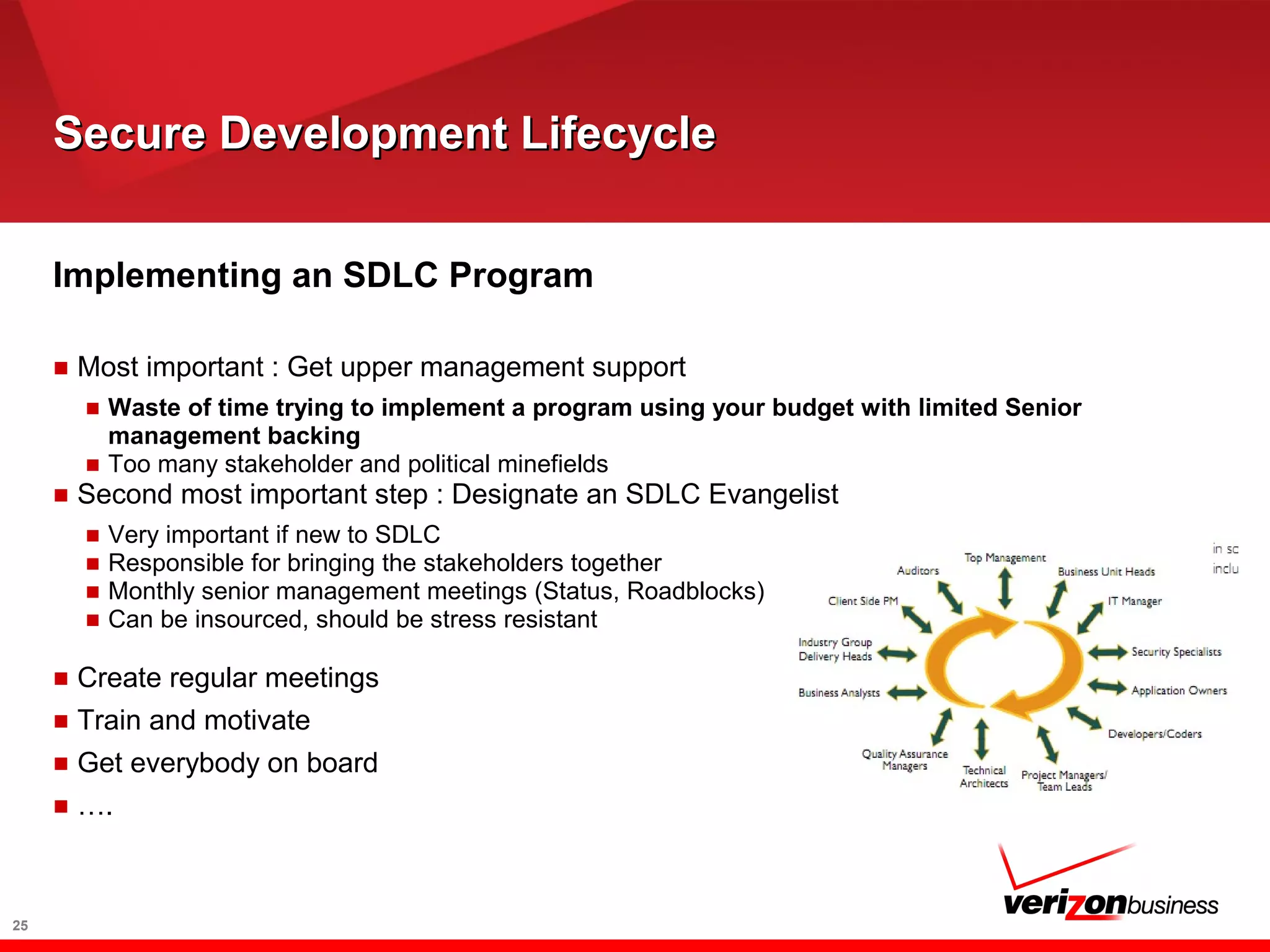
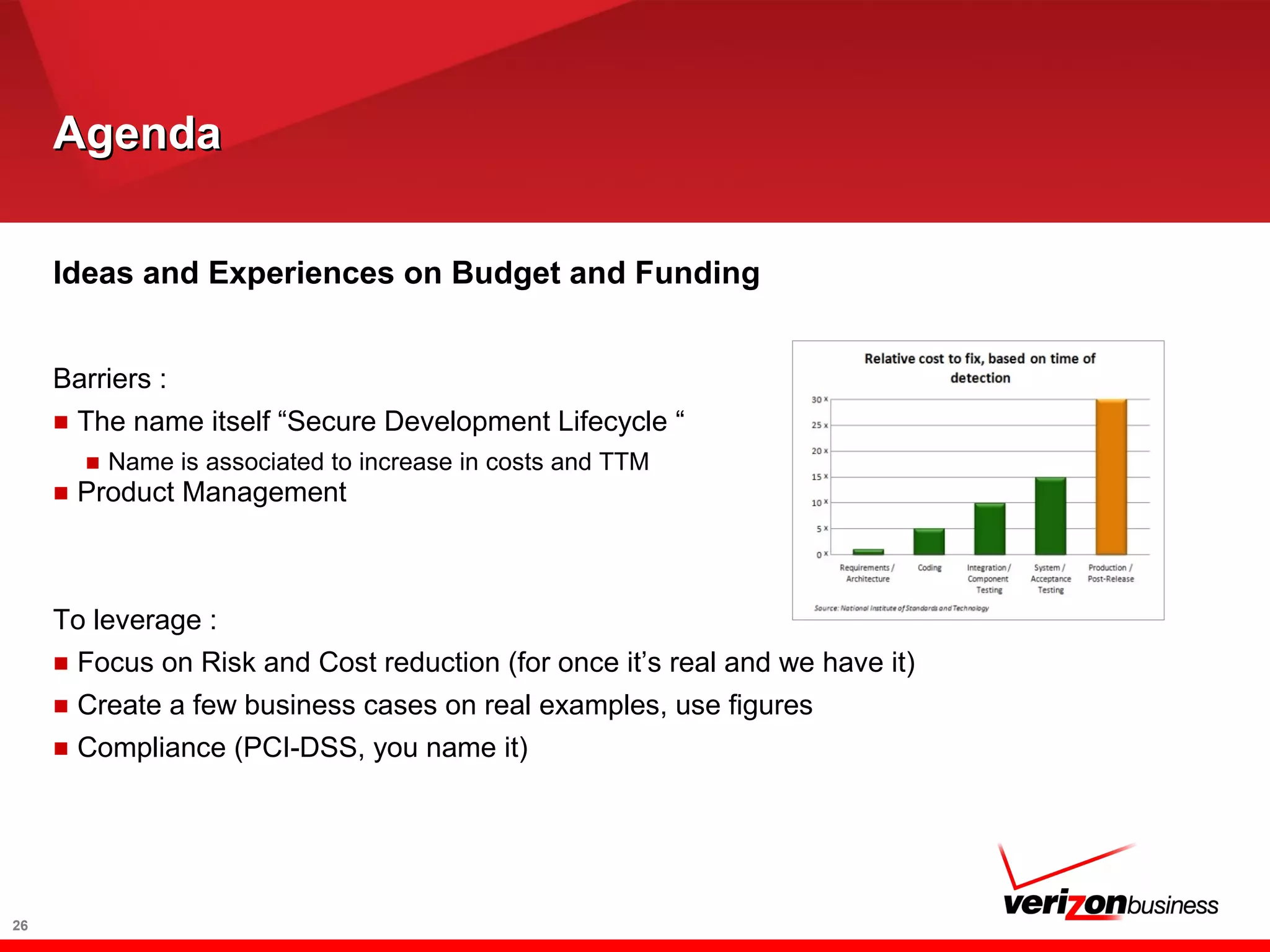
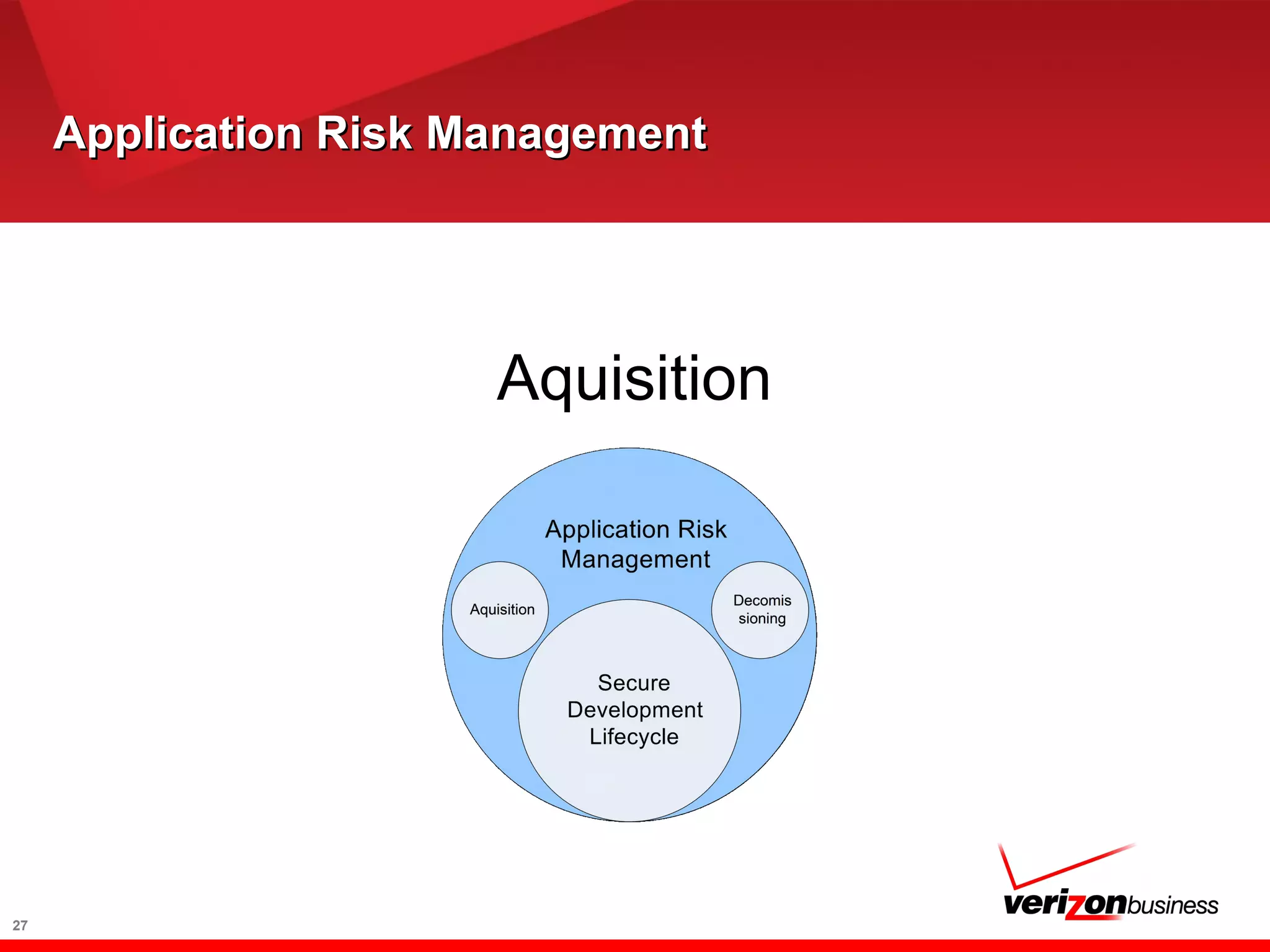
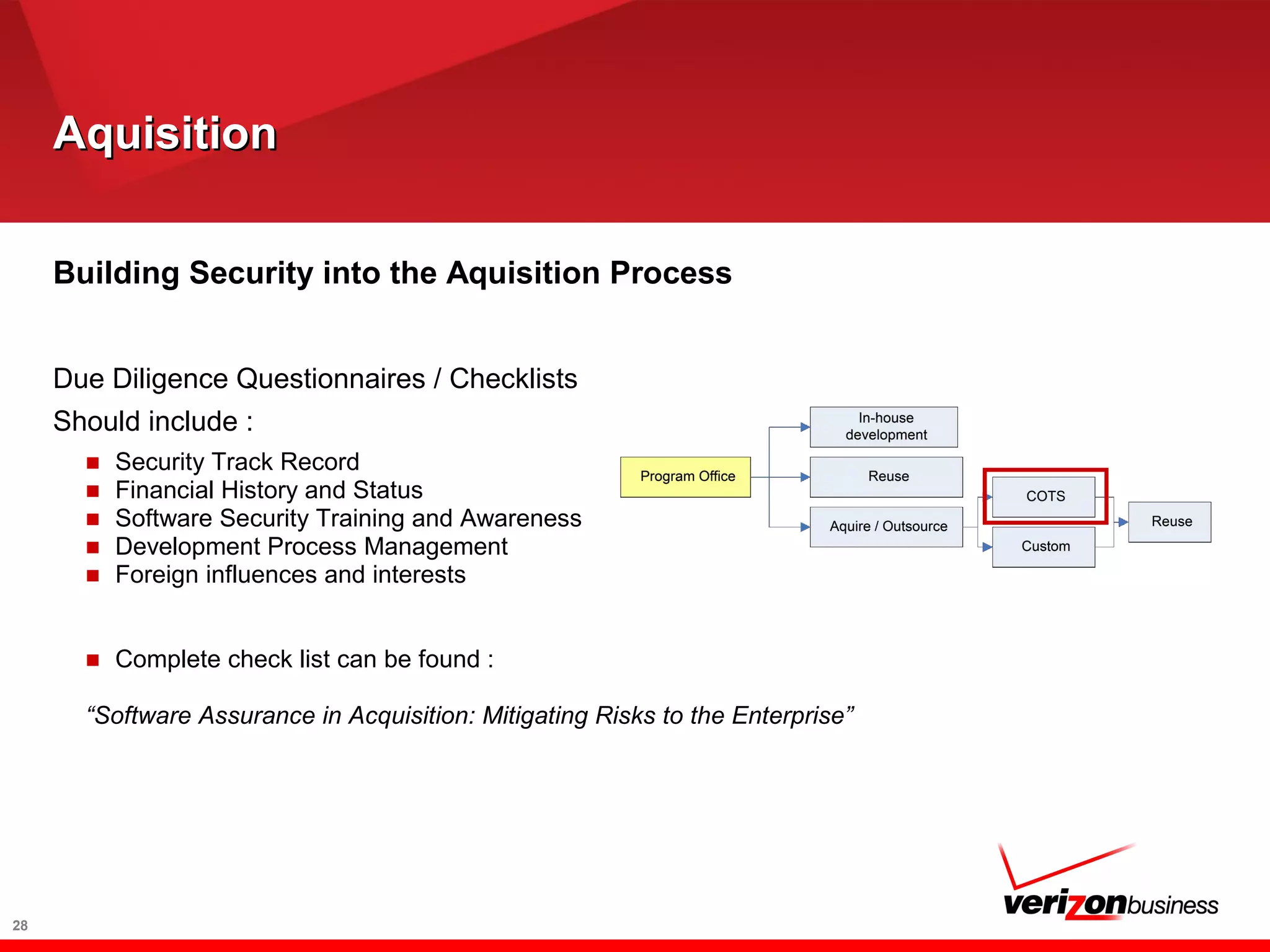
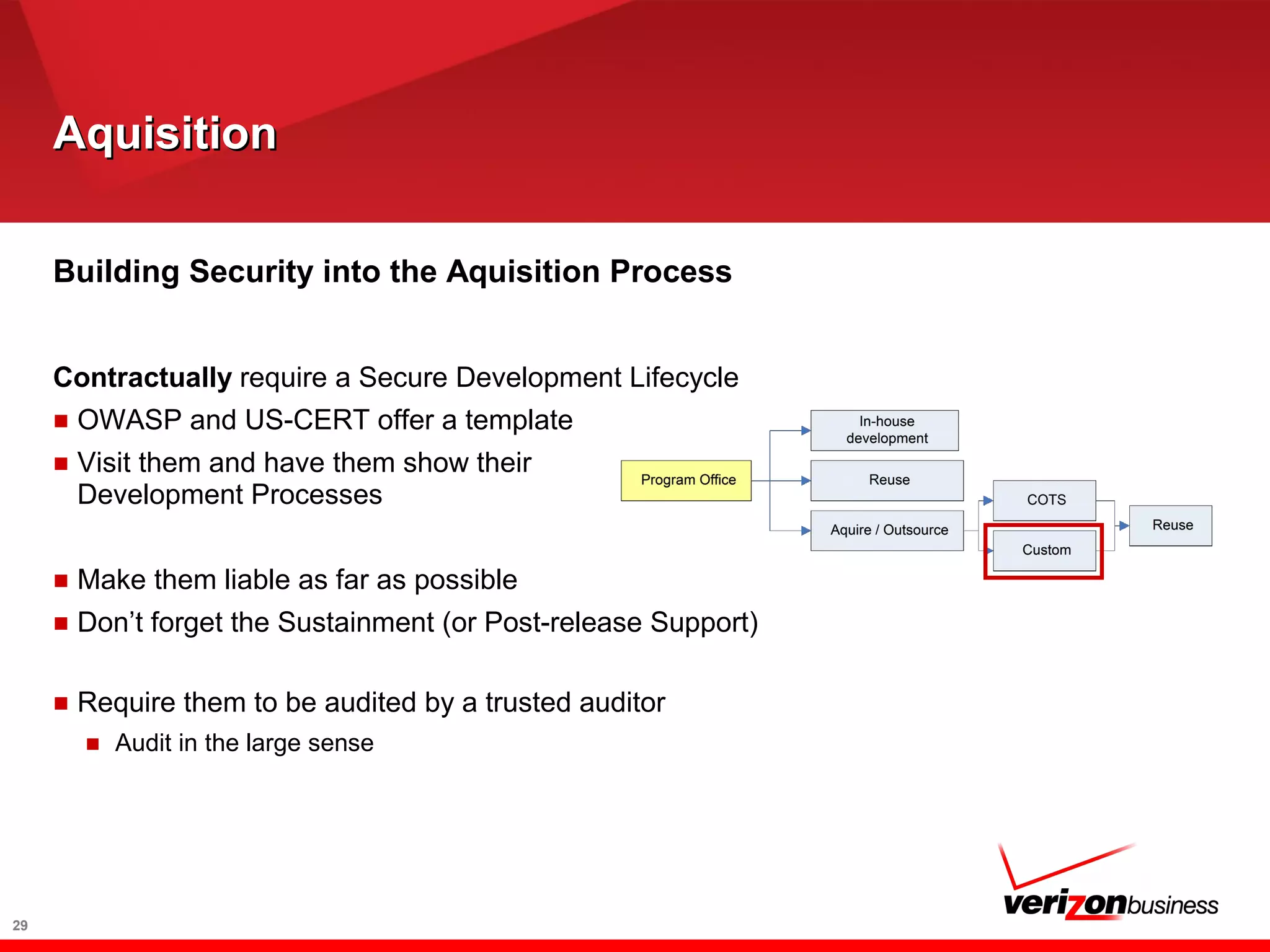
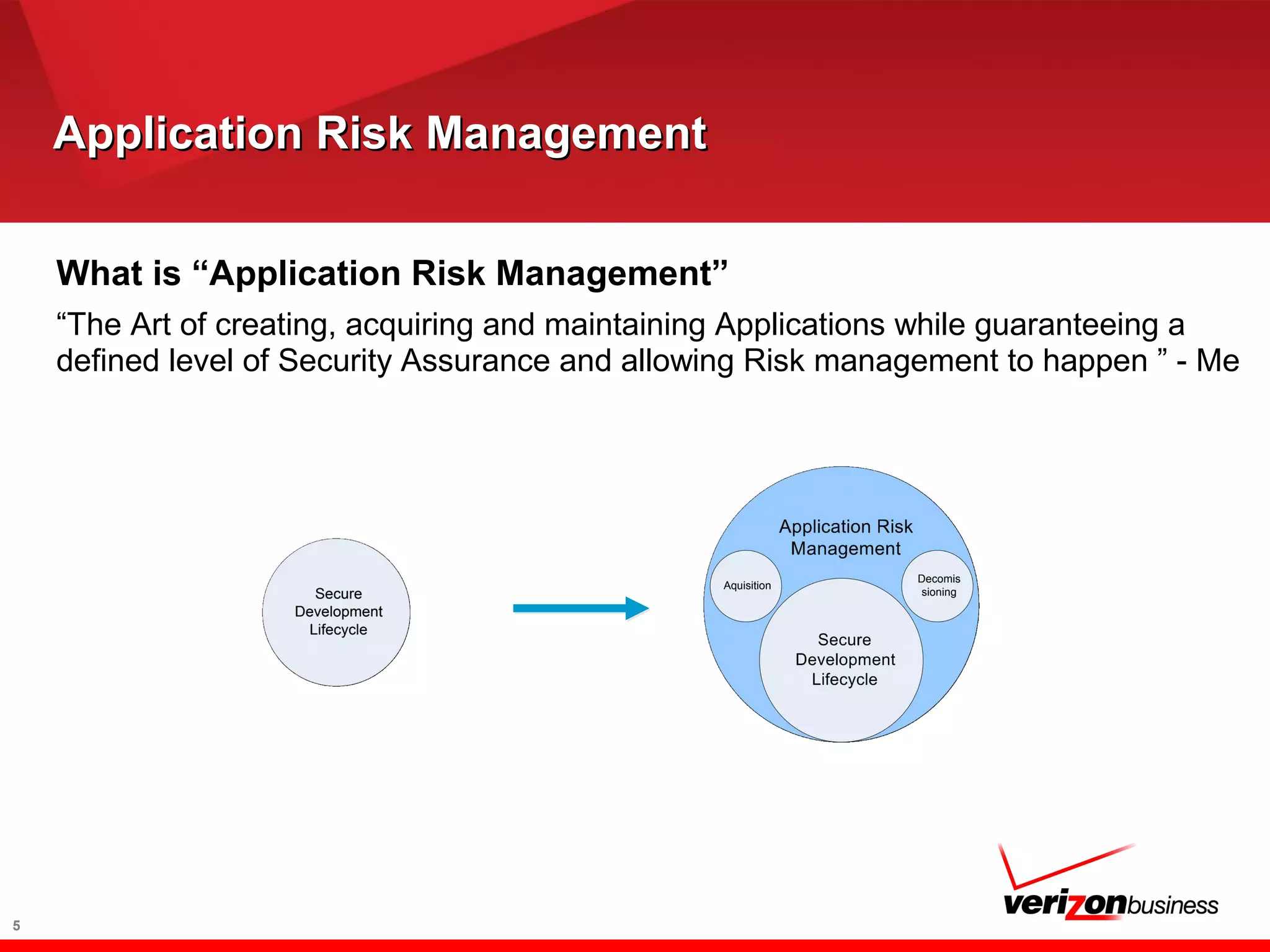
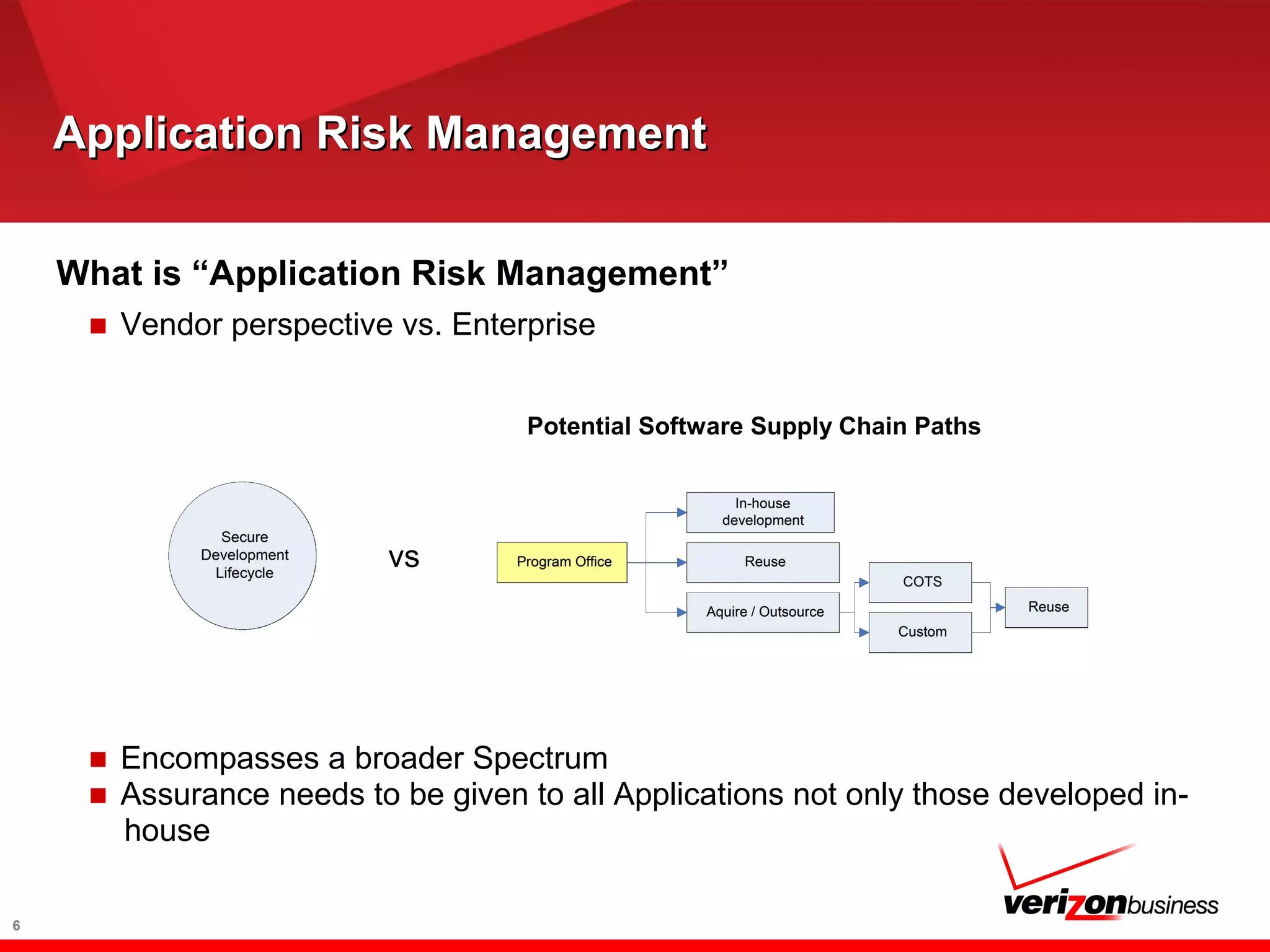
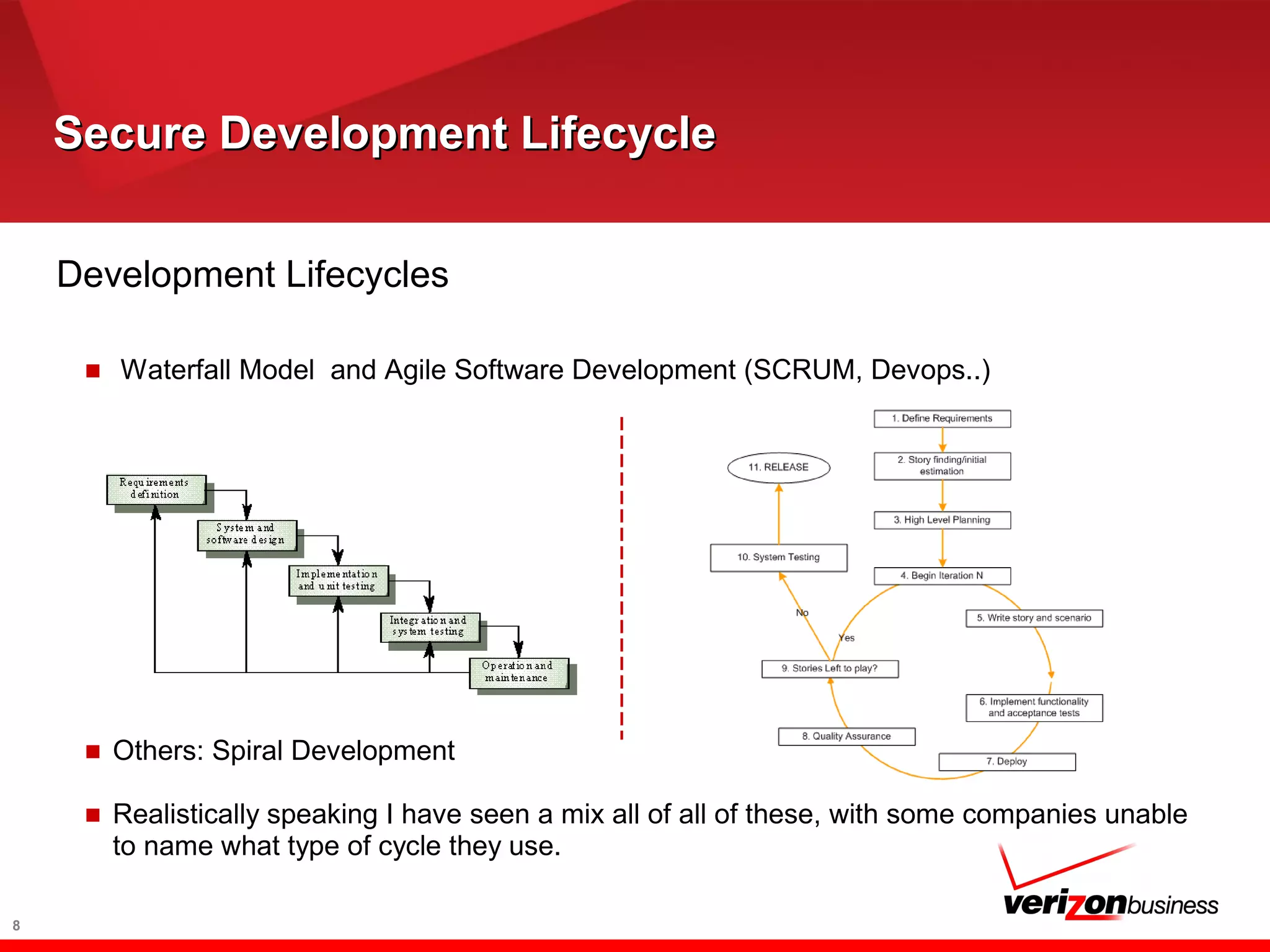
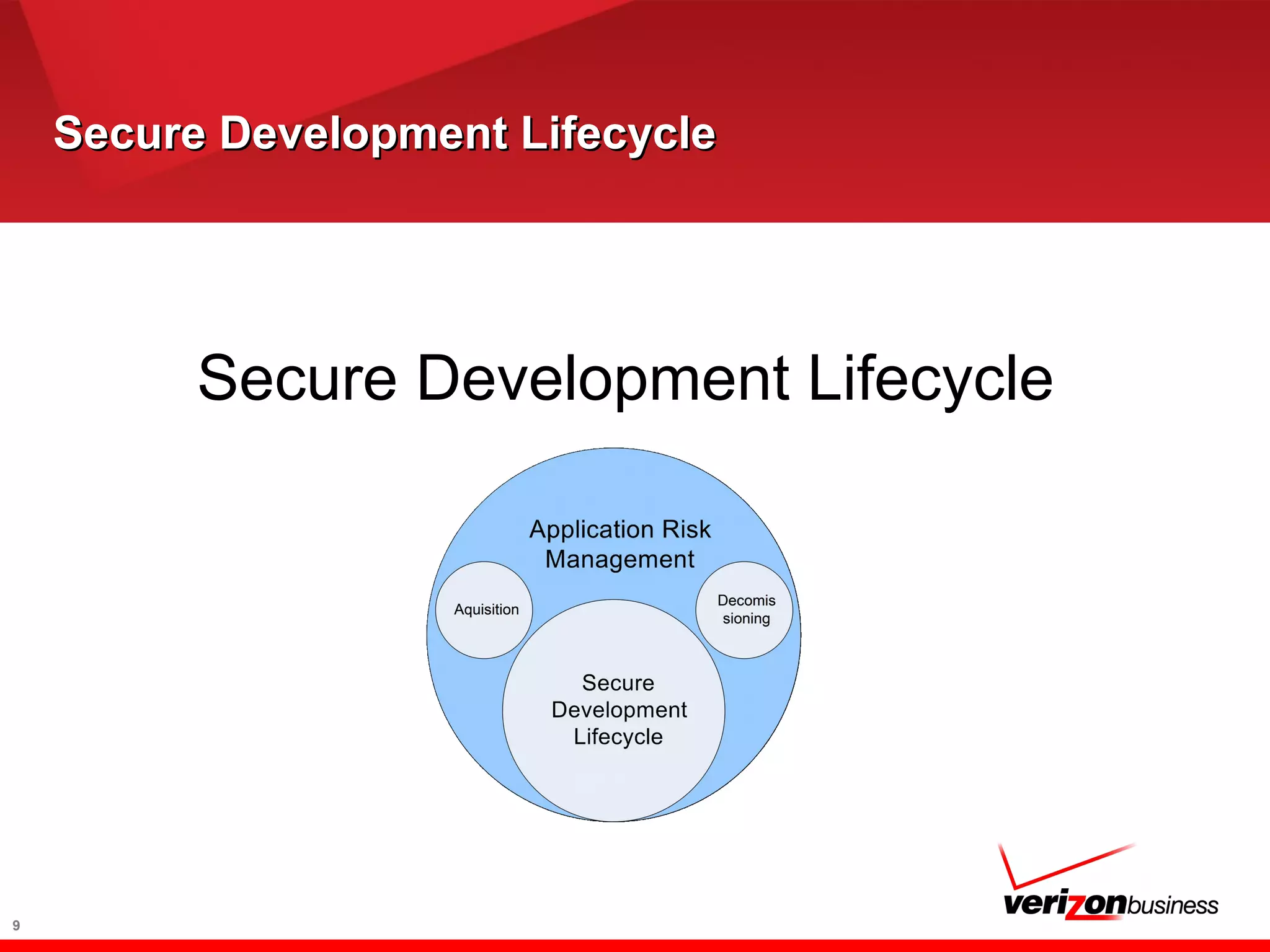
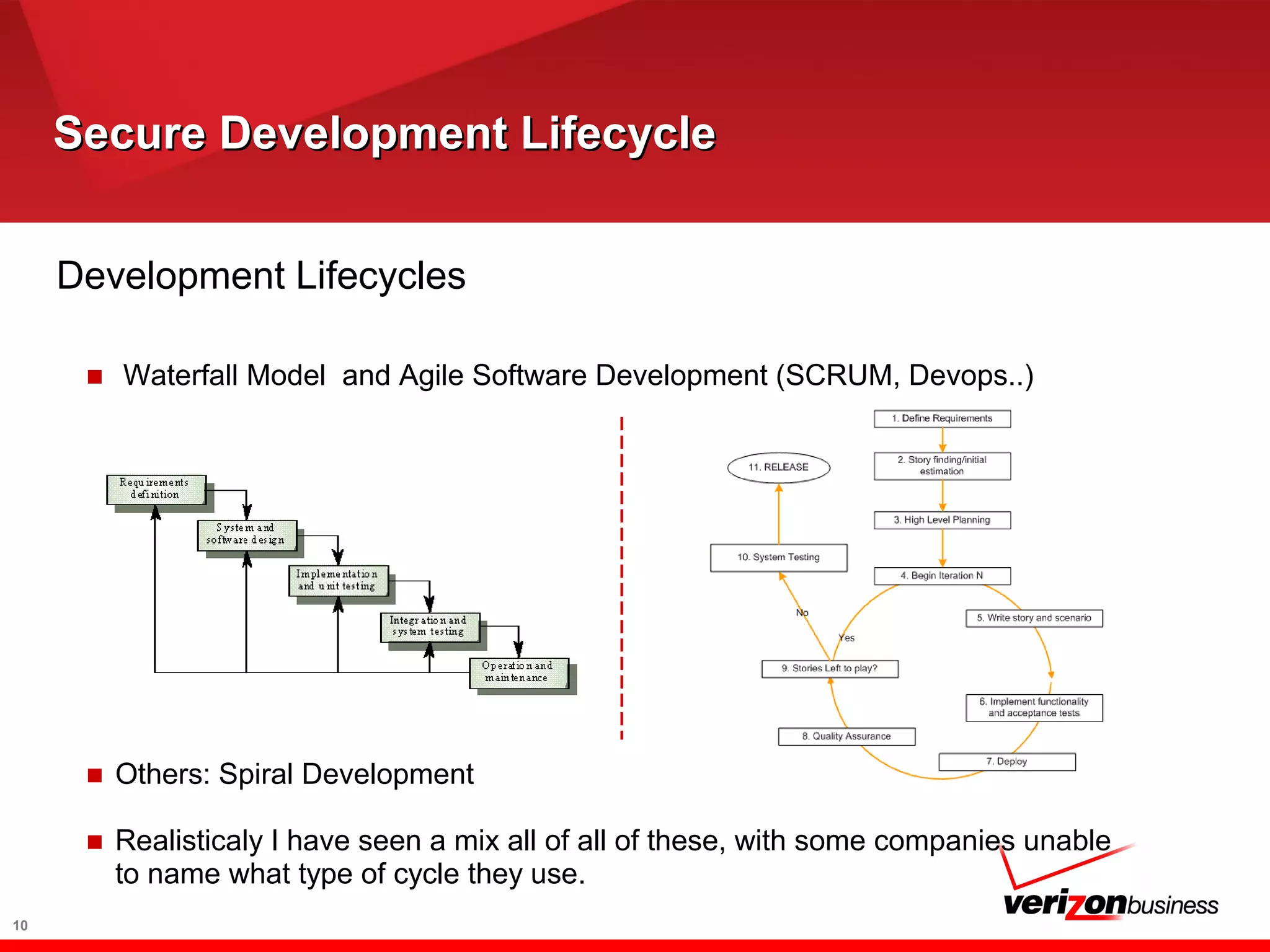
The document discusses application risk management and emphasizes the importance of secure development lifecycles (SDL) in ensuring security assurance for applications. It outlines various development models and suggests that effective SDL strategies reduce costs and risks while enhancing security assurance. Additionally, it highlights the need for upper management support and proper training to successfully implement SDL programs.

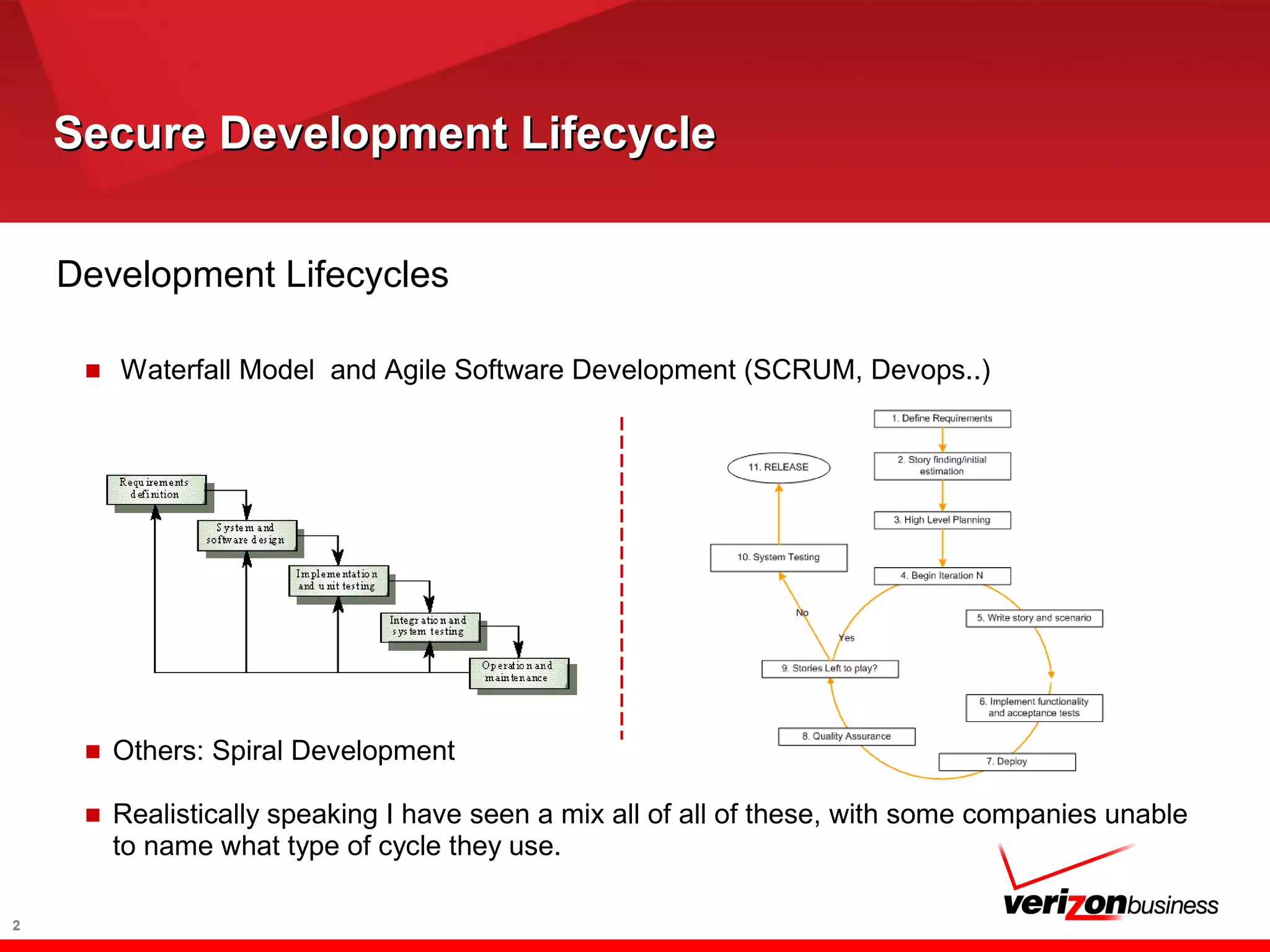


![Secure Development LifecycleSecure Development Lifecycle
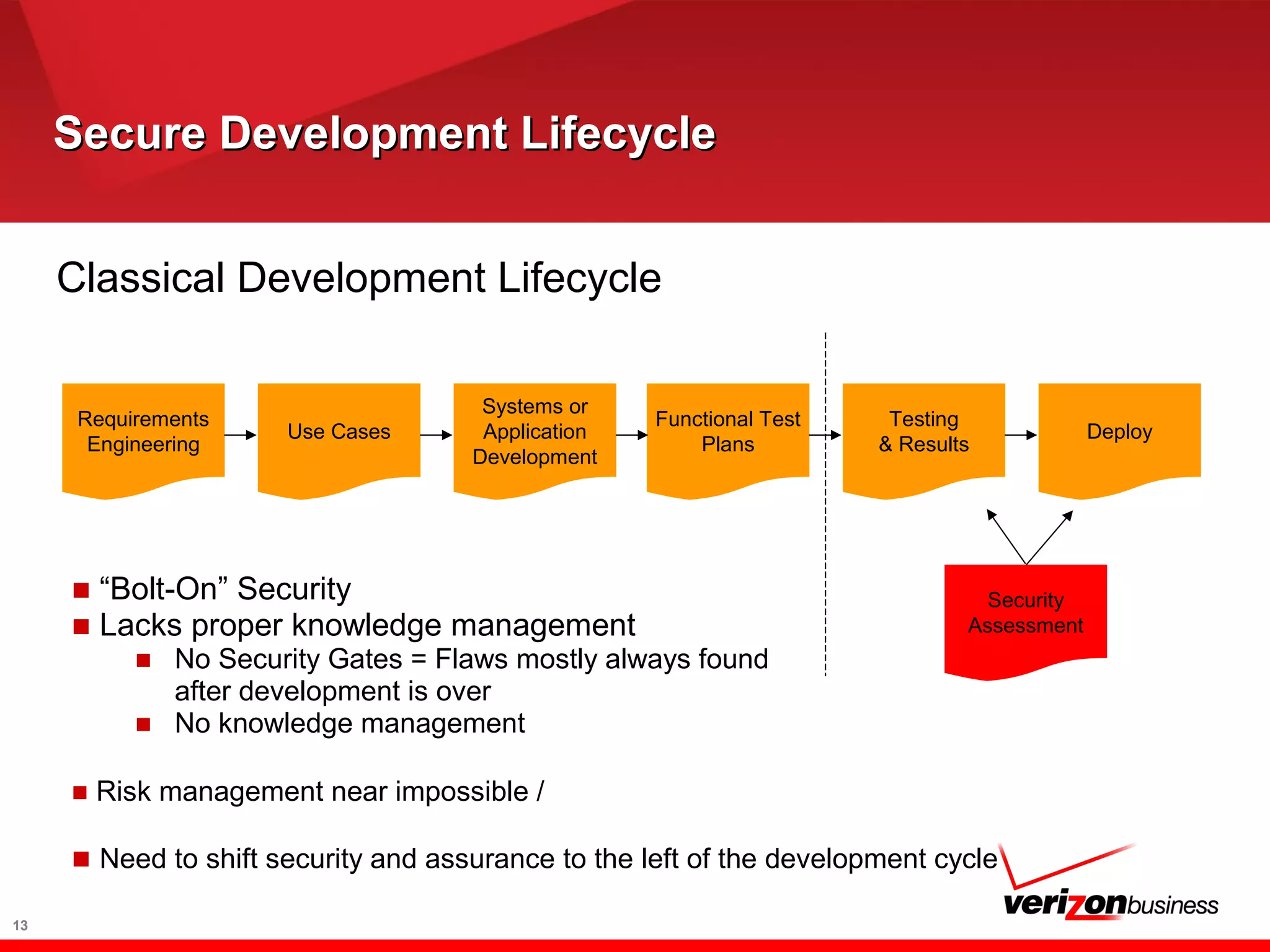
A Secure Development Lifecycle
■ Different shapes and colors - SDL, SDLC, SSDL, Software
Assurance
■ Types
■ Heavy Processes
■ [Hall 2002a] [NSA 2002, Chapter 3]
■ Clean Room and TSP-Secure
■ Lightweight Processes
■ Microsoft SDL
■ CLASP
■ They are all fine if they fit the needs of your enterprise / organization
11
Source: DHS](https://image.slidesharecdn.com/applicationriskmanagementinenterprises-170710124443/75/Managing-Application-Security-Risk-in-Enterprises-Thoughts-and-recommendations-11-2048.jpg)