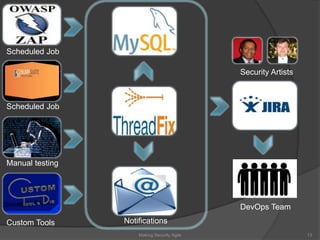
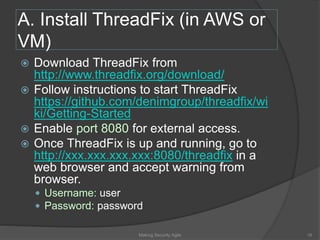
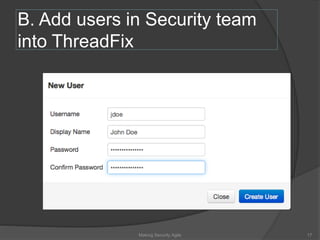
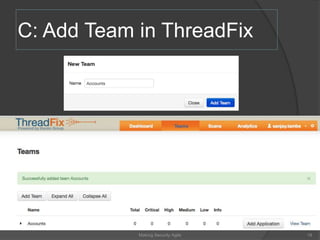
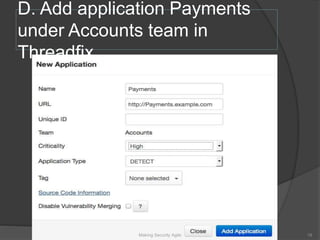
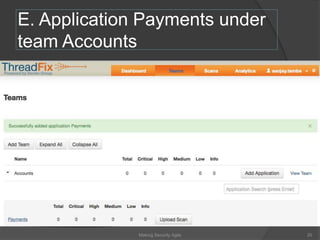
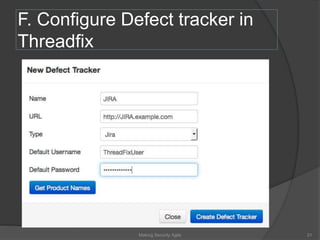
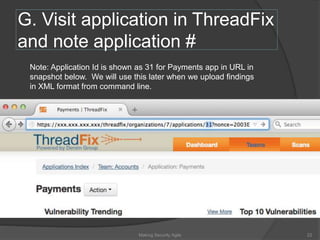
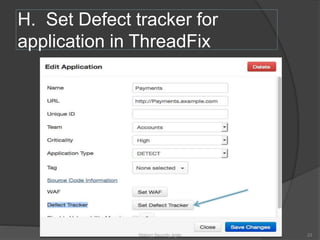
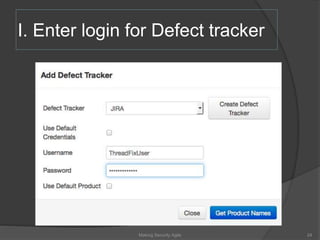
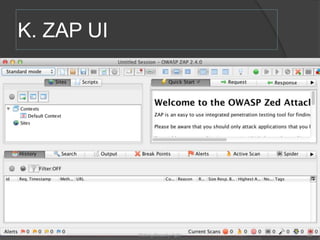
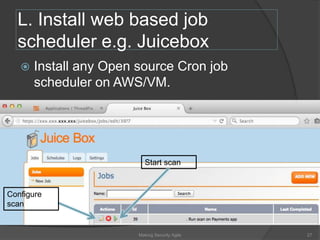
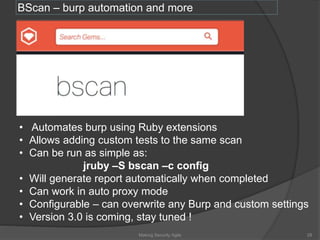
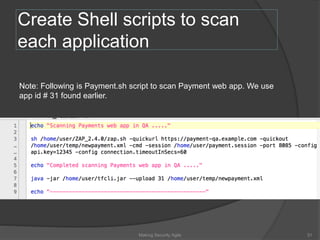
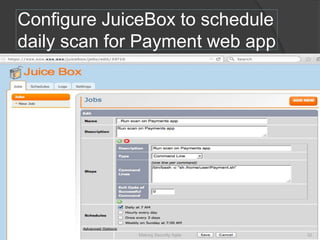
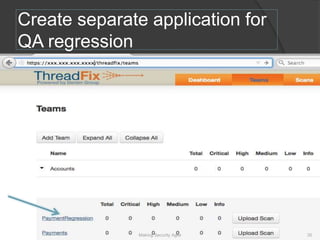
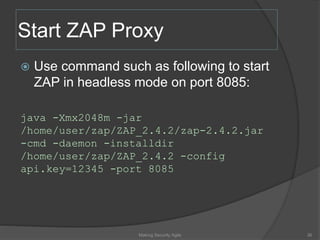
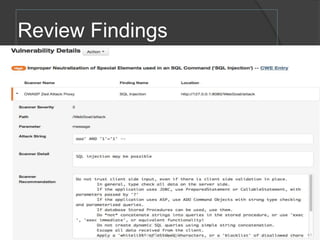
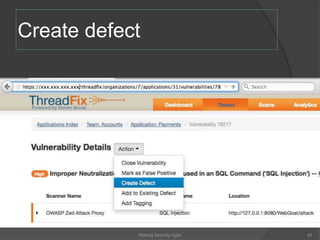
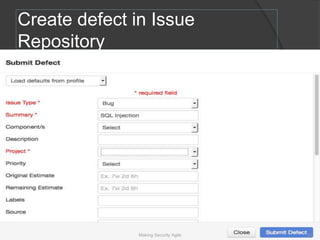
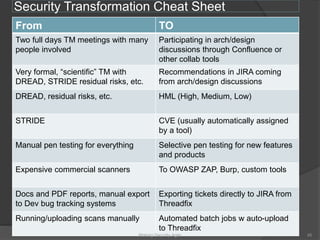
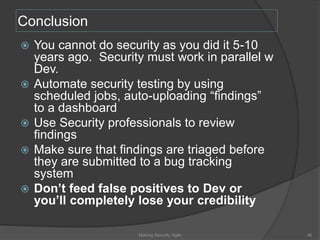
The document discusses integrating security into development processes, emphasizing the need for agility in security practices due to rapid competition. It highlights the importance of automation and collaboration between security, development, and QA teams, while also outlining challenges with traditional security testing methods. The conclusion stresses that security must evolve with development methodologies to remain effective.