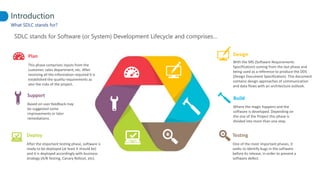
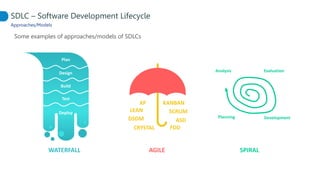
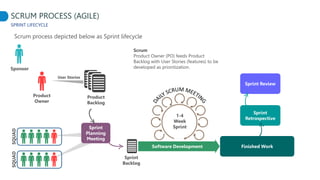
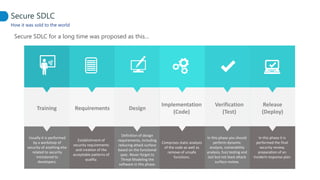
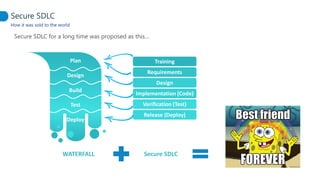
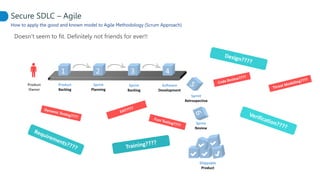
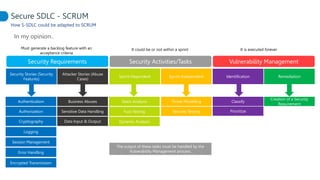
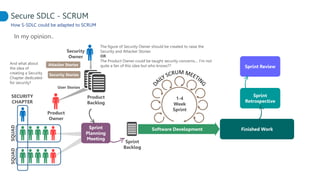
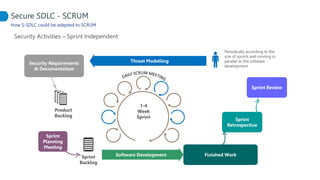
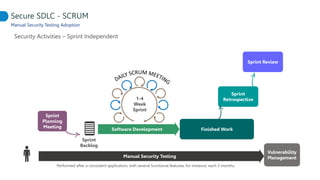
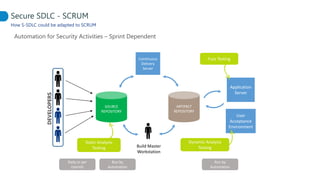
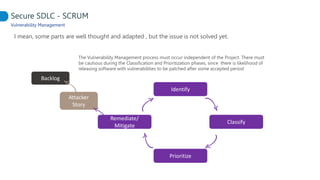
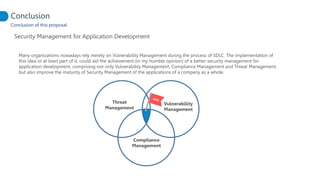
This document proposes adapting a secure software development lifecycle (SDLC) to agile methodologies like Scrum. It discusses how security activities could fit within a Scrum process, with some performed each sprint and others done periodically or independently of sprints. For example, threat modeling could run in parallel with development, while manual security testing may occur every few months. The document also considers how roles like a "Security Owner" or dedicated "Security Chapter" could help prioritize security work. While not a perfect solution, integrating security practices into each phase of an agile process could help organizations better manage application security.