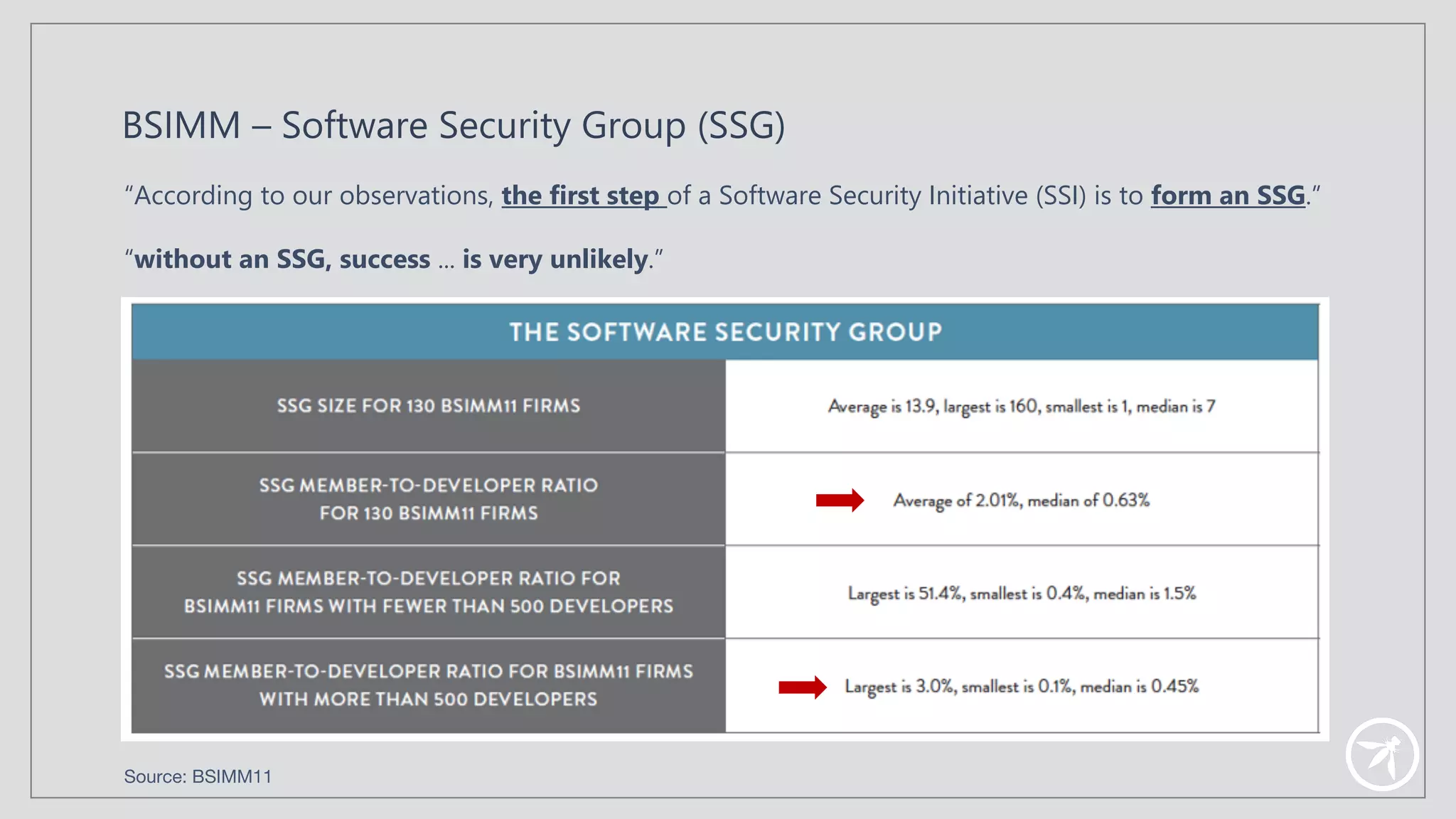
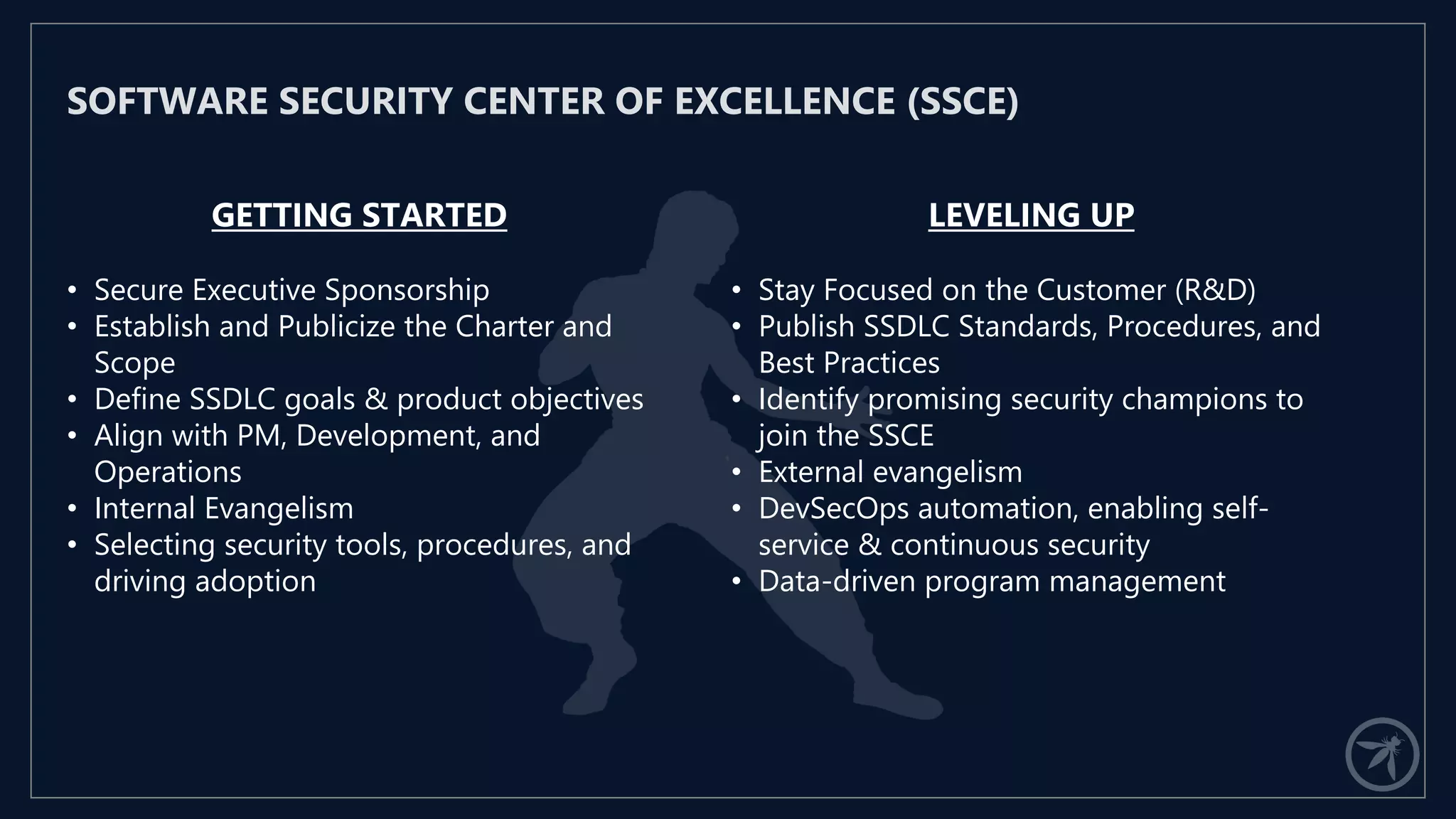
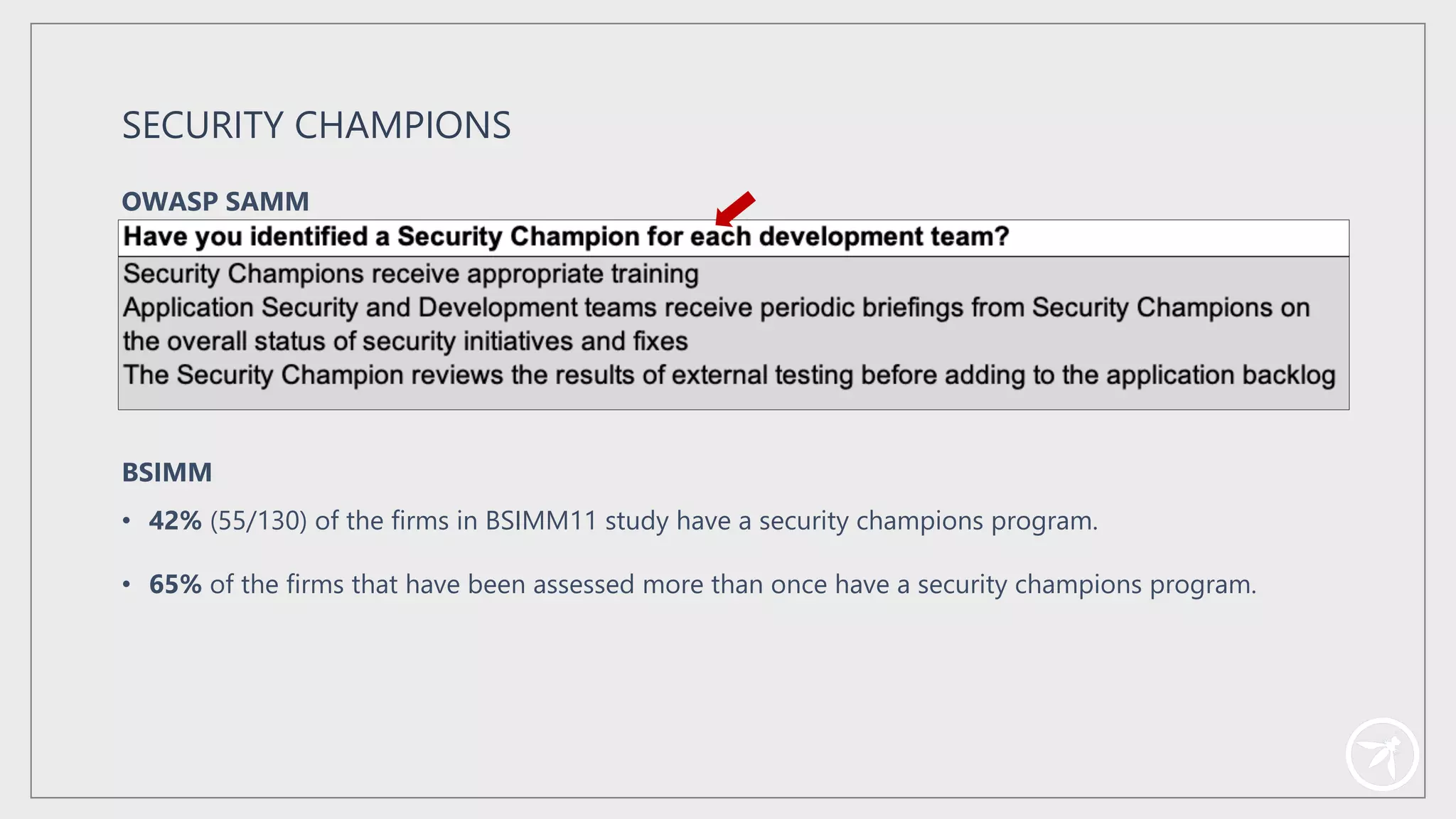
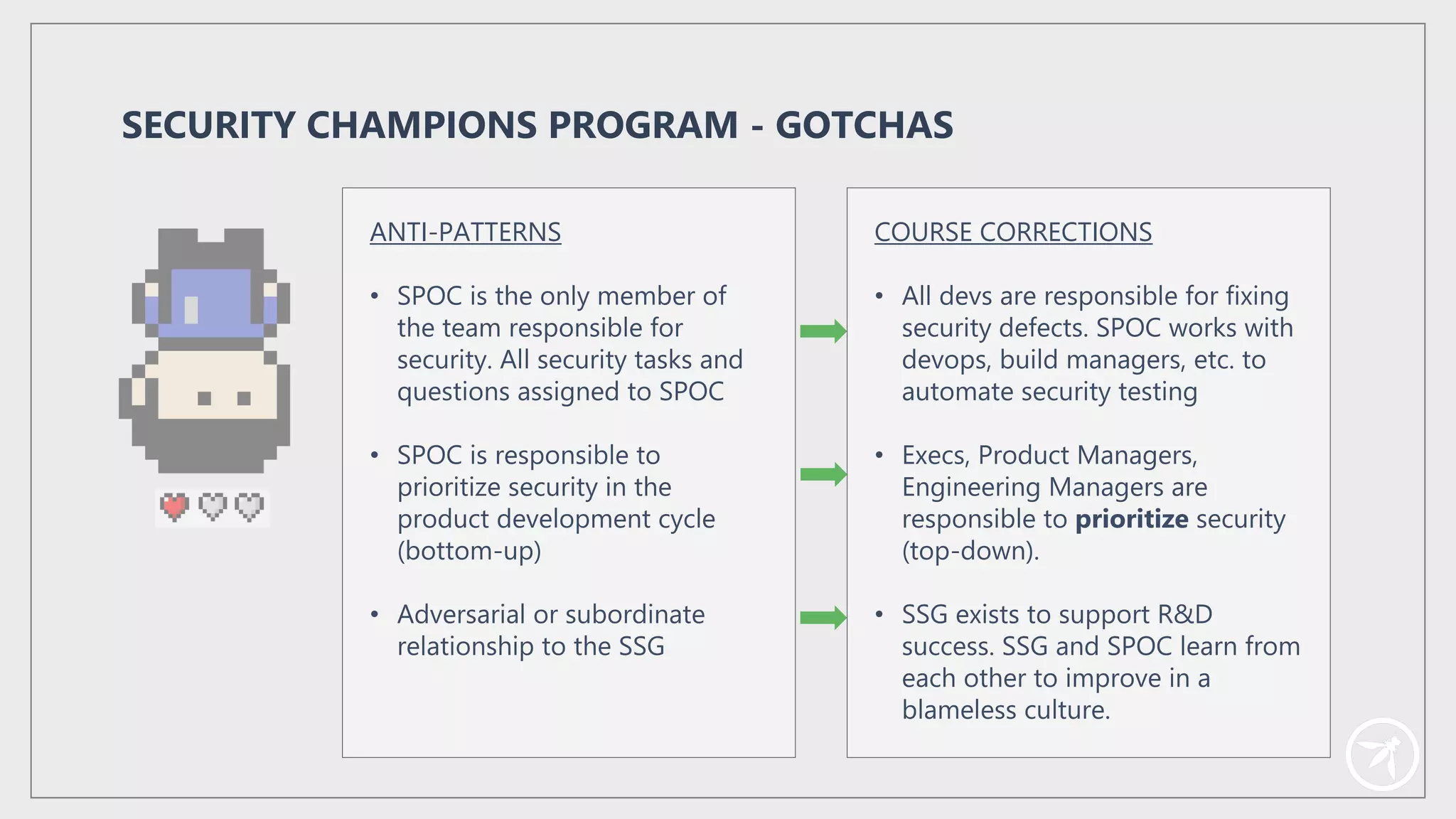
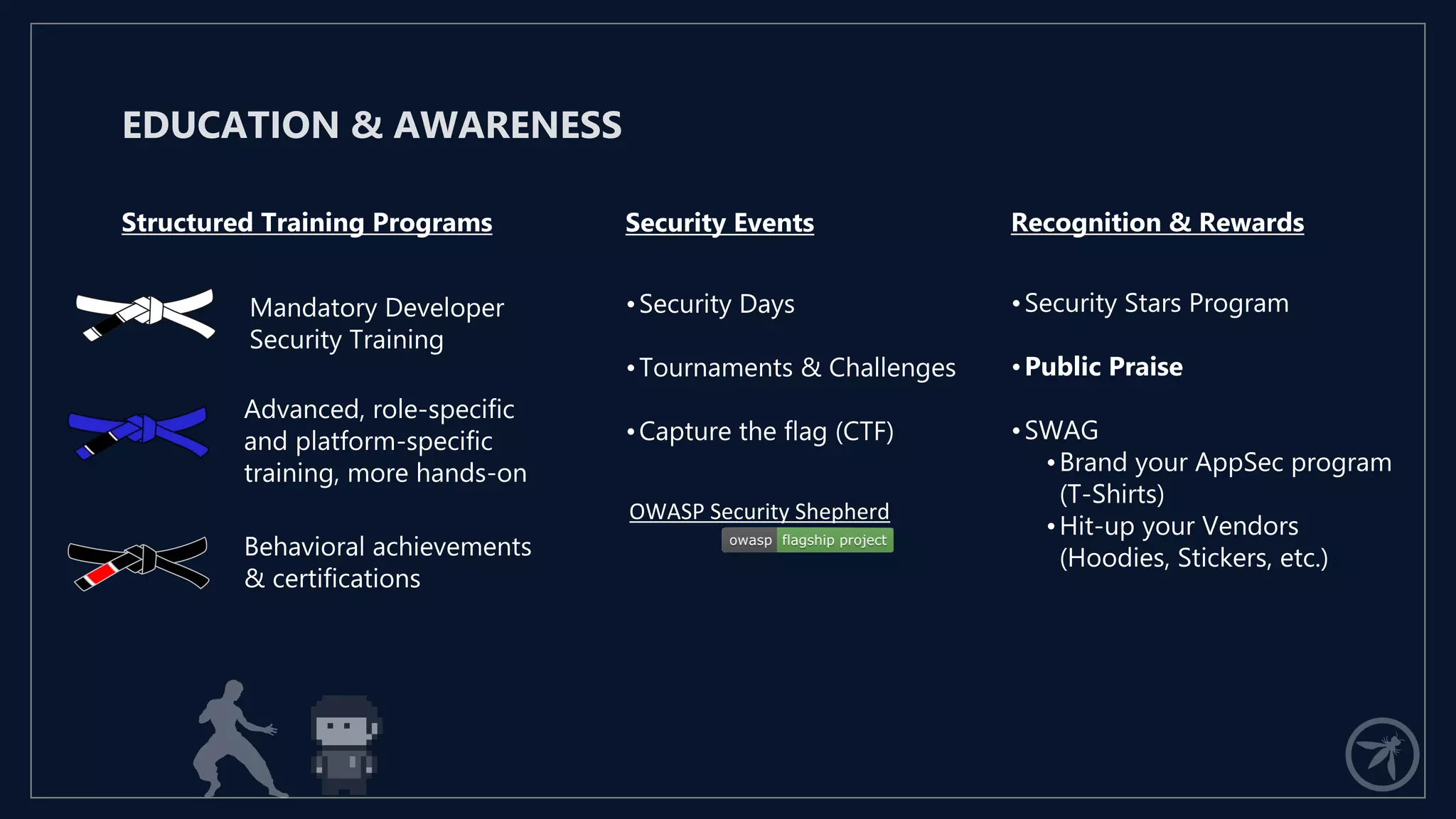
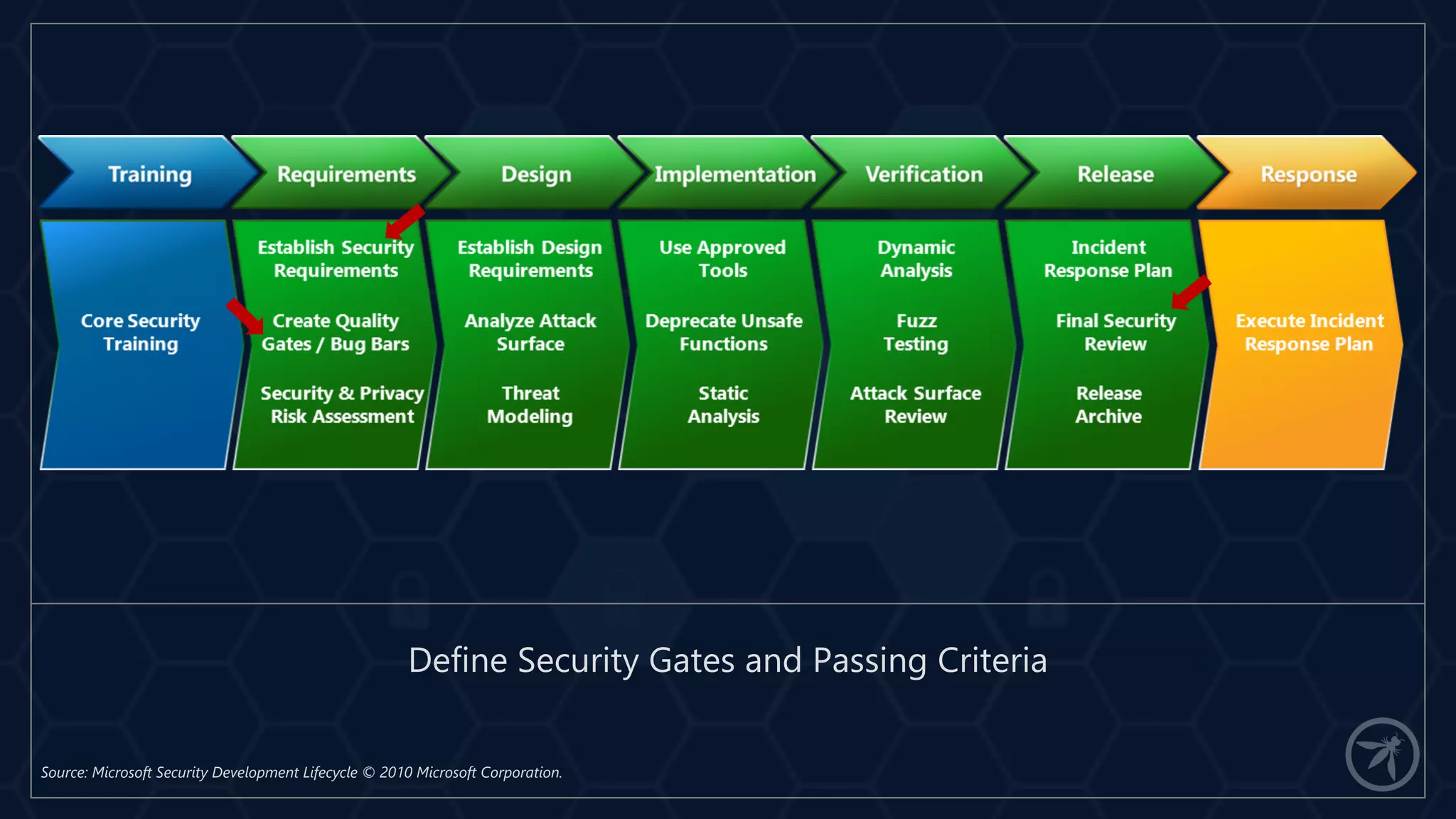
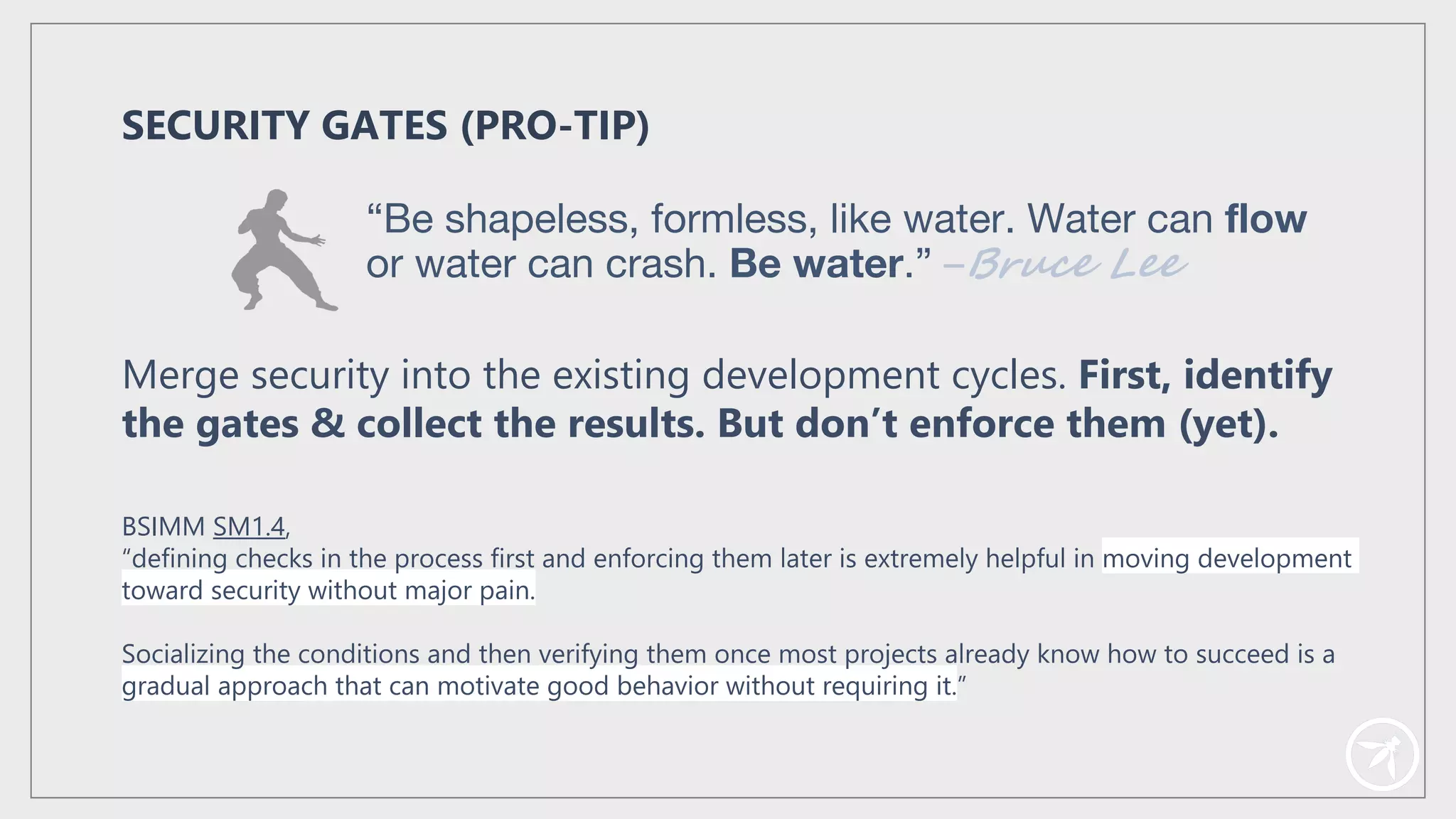
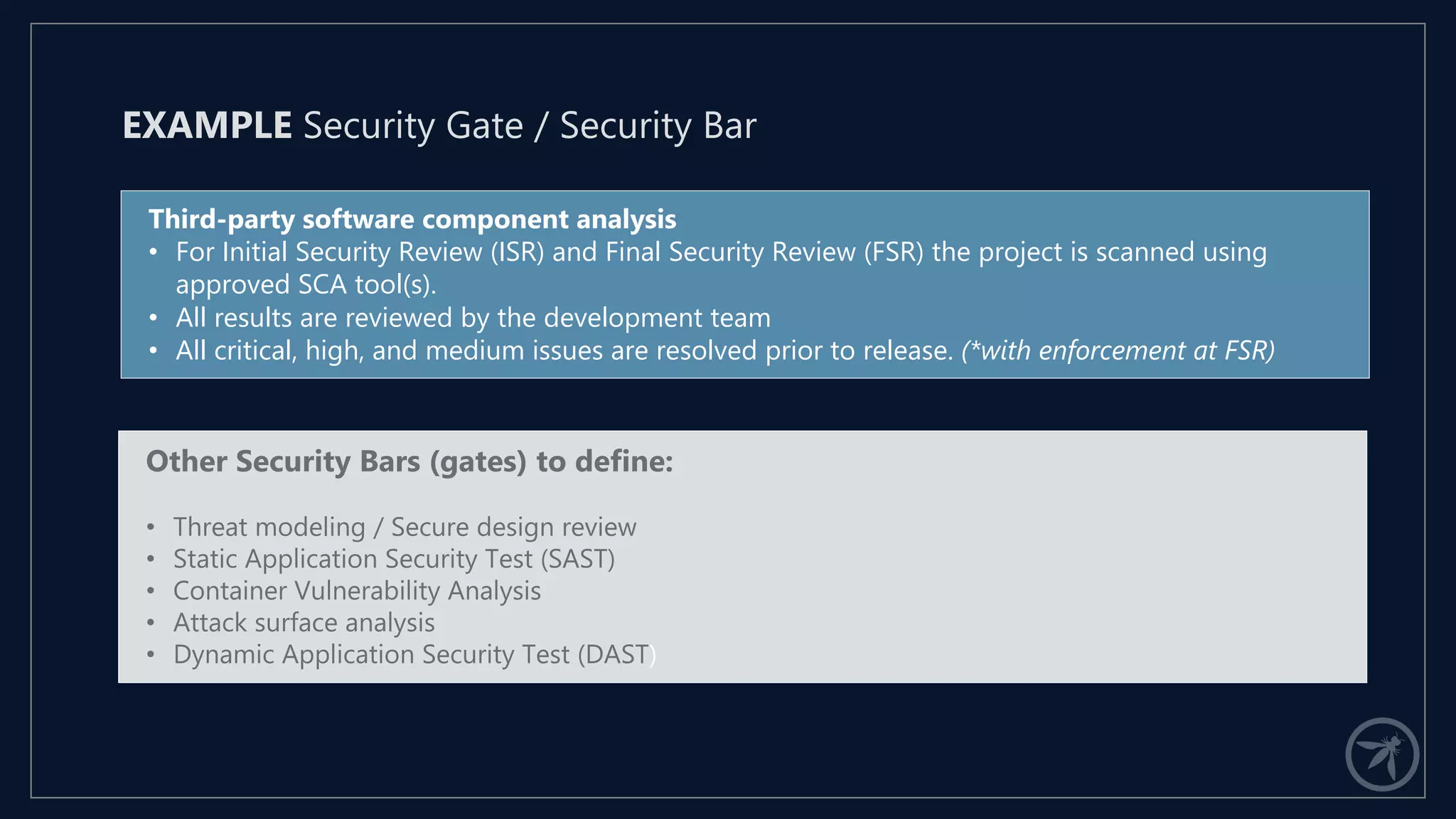
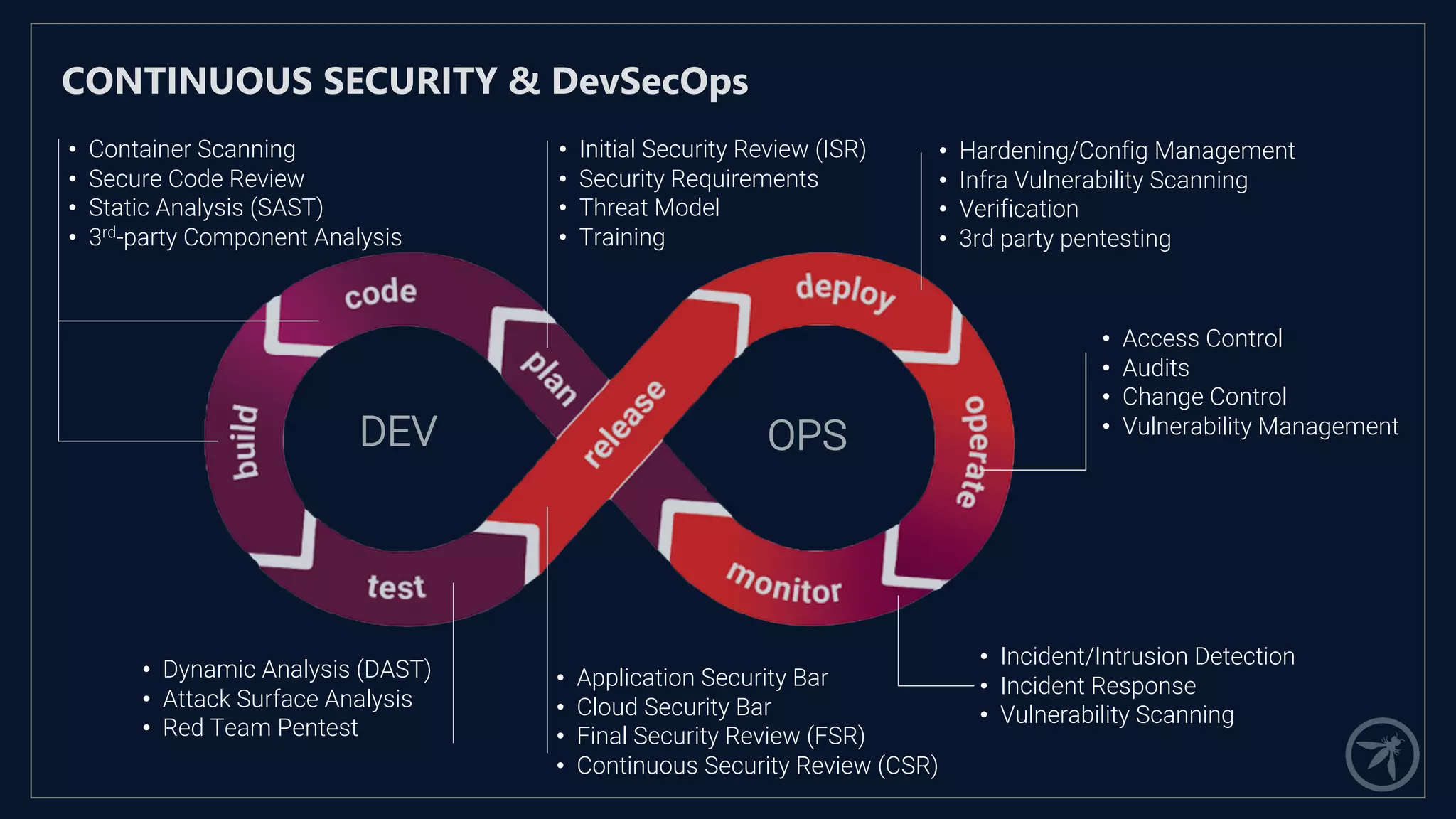
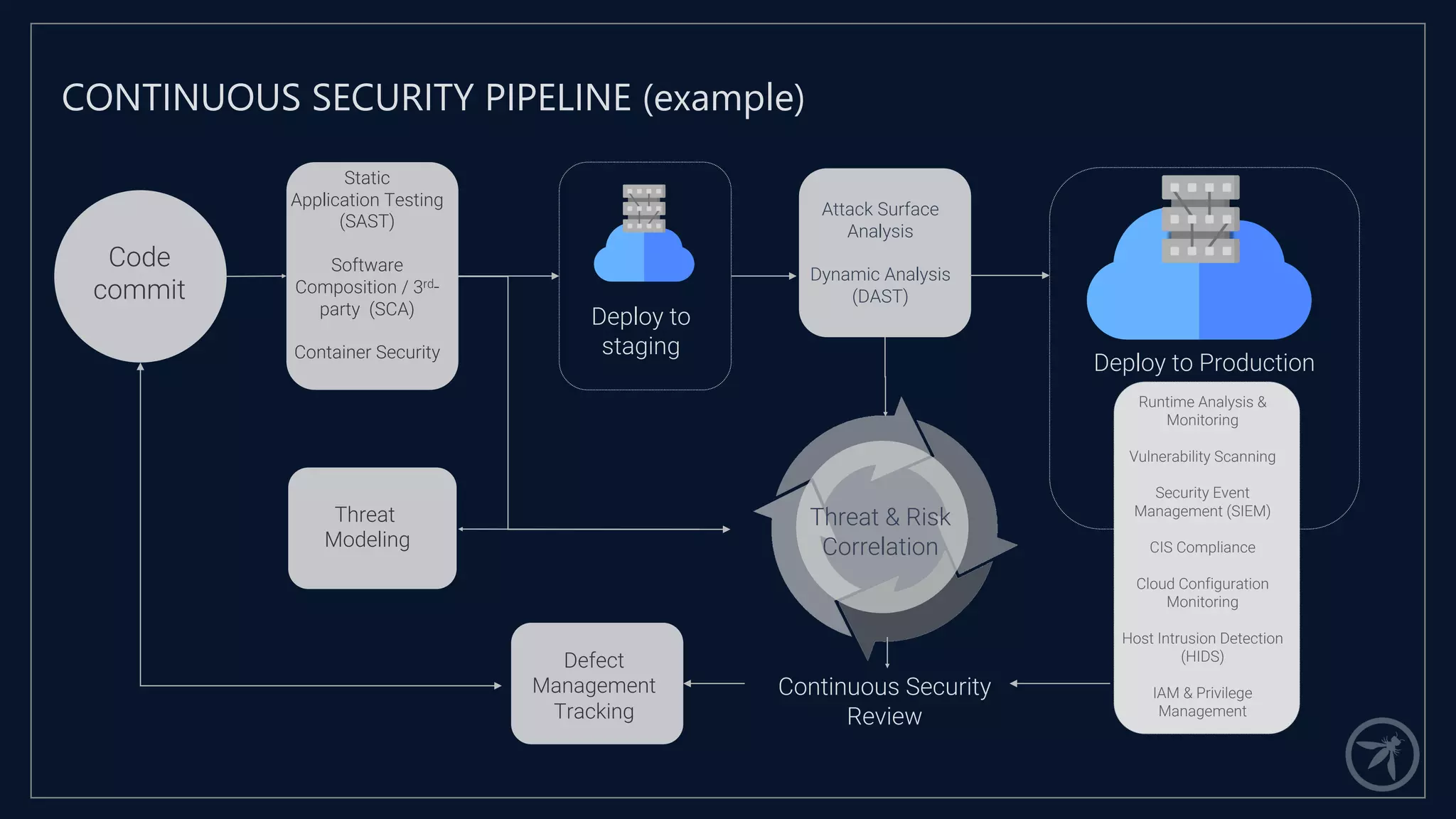
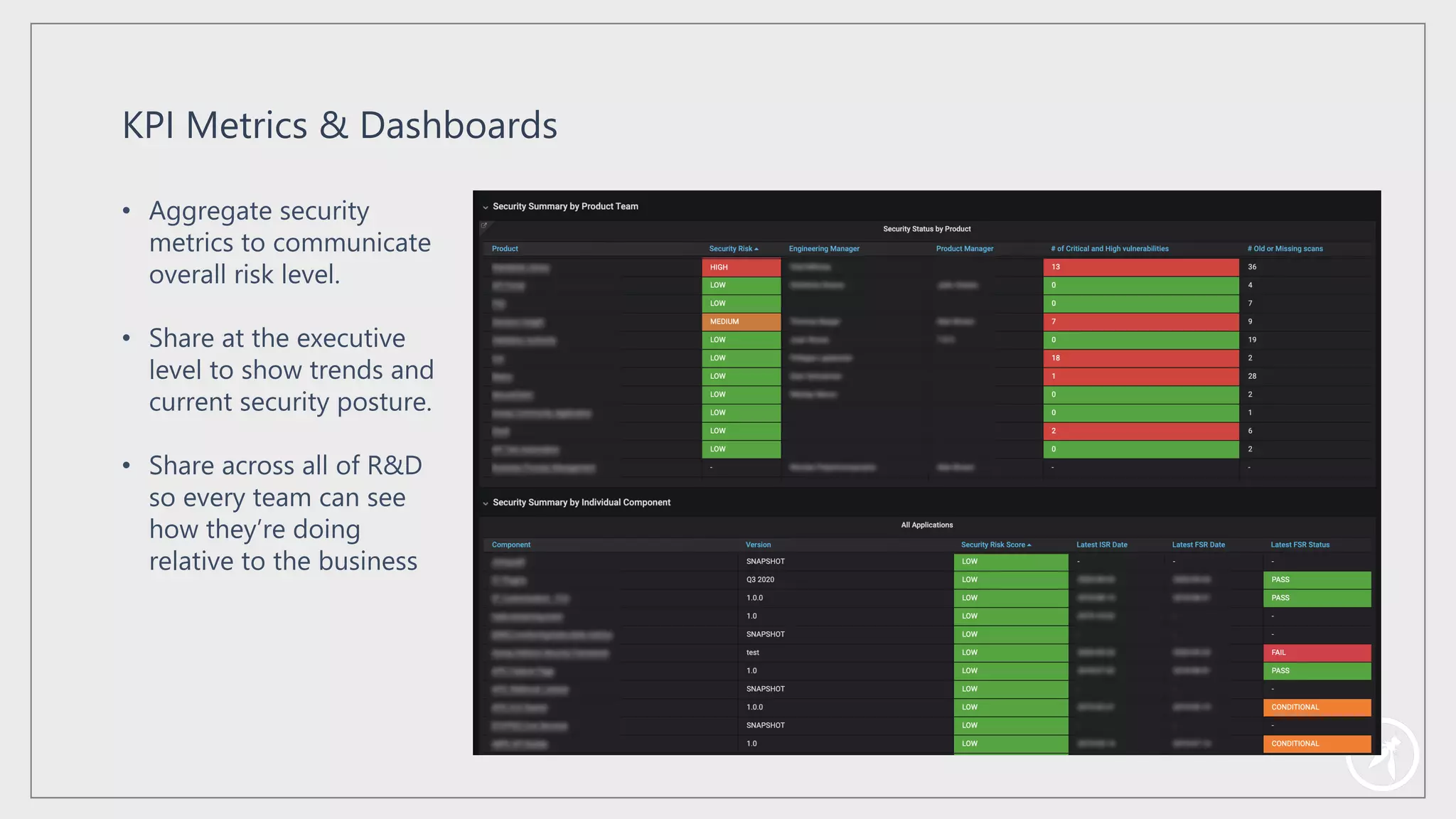
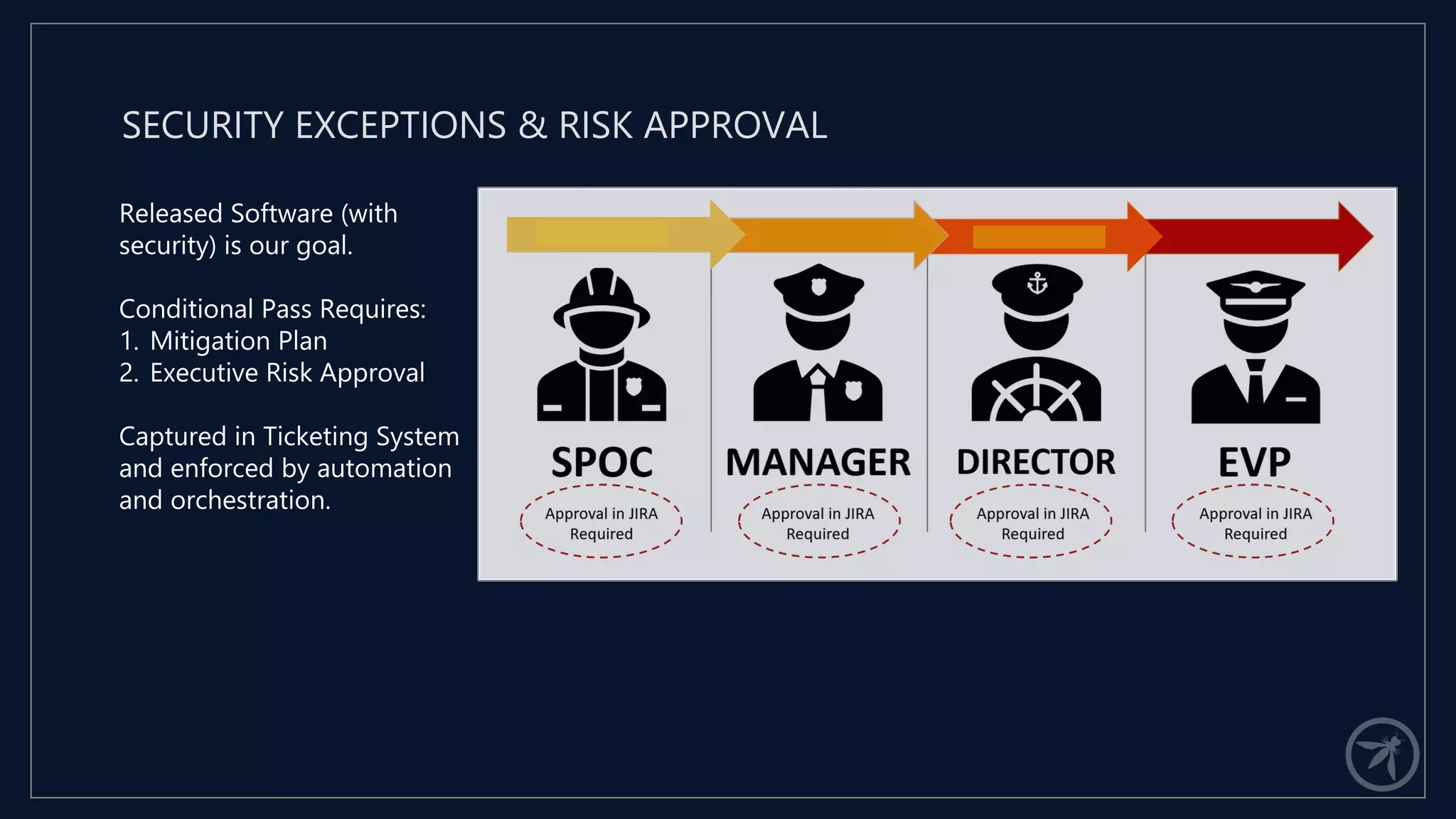
The document presents a comprehensive framework for building a scalable global application security program by leveraging established strategies such as OWASP SAMM and BSIMM. It emphasizes the importance of culture, process, and governance in fostering security initiatives, and outlines practical steps for organizations at different maturity levels. Key elements include establishing a centralized security group, promoting security champions, and integrating security into development cycles to achieve continuous security at scale.