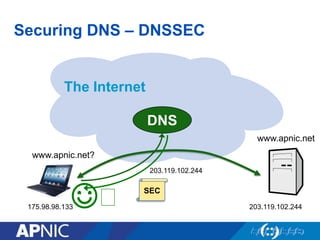
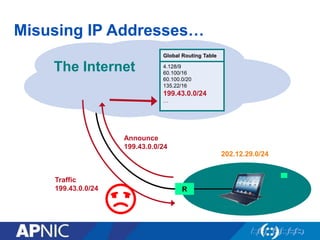
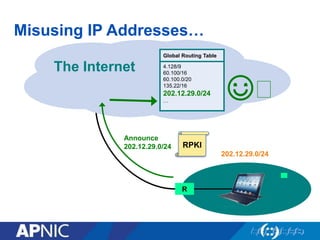
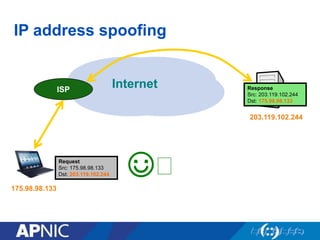
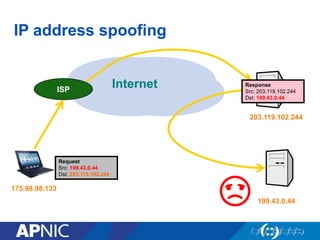
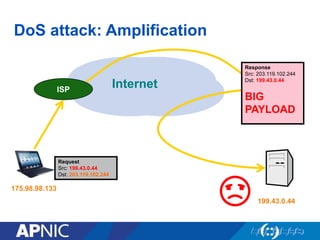
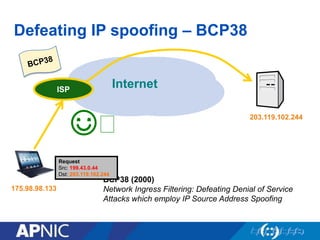
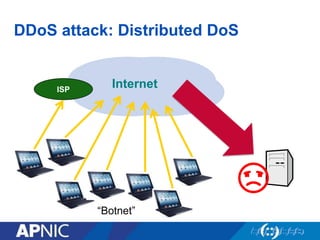
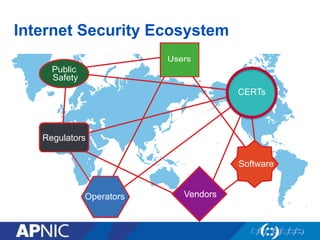
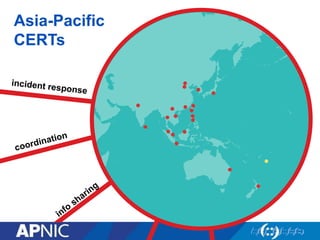
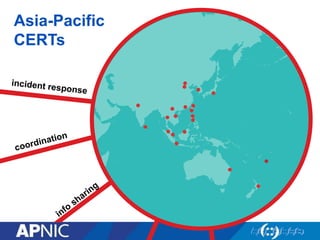
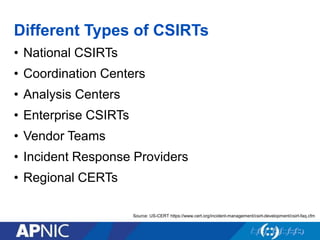
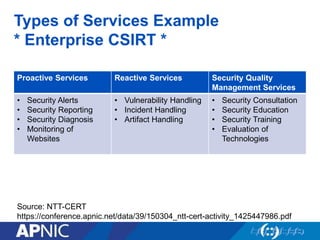
The document discusses cybersecurity challenges and the importance of establishing a Computer Emergency Response Team (CERT) for enhancing security incident response across the Asia-Pacific region. It outlines the various threats organizations face, the components necessary for an effective CERT, and the need for information sharing and collaboration among stakeholders. Additionally, it emphasizes the necessity of a structured approach to incident handling and the establishment of policies and procedures to manage security threats effectively.