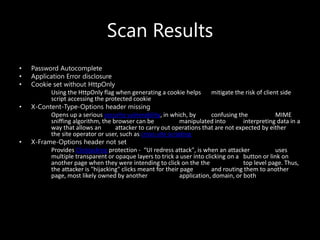
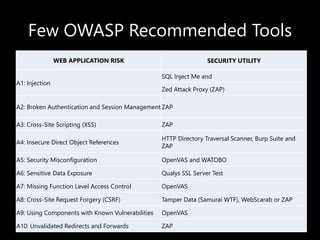
This document discusses security test automation. It defines security testing and some key terms like vulnerability, spoofing, and SQL injection. It recommends tools from the OWASP project like ZAP and describes how to integrate ZAP into an automation workflow. An example workflow is described that uses ZAP to find issues like password autocomplete, application errors, and missing security headers. Integrating security scans with CI builds is advocated to improve security with little additional effort.






![Zed Attack Proxy [ZAP]
• An easy to use web application security
testing tool
• Completely Free and Open Source
• An OWASP flagship project
• Ideal for Beginners
• But also used by Professionals
• Framework for advanced testing
• Ideal for Dev and QA. Especially for Test
Automation Engineers](https://image.slidesharecdn.com/securitytestautomation-150107070343-conversion-gate01/85/Security-testautomation-11-320.jpg)