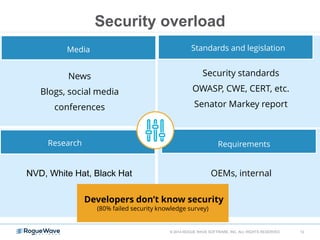
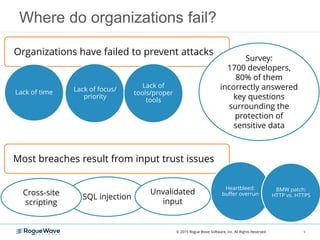
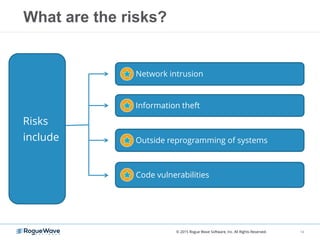
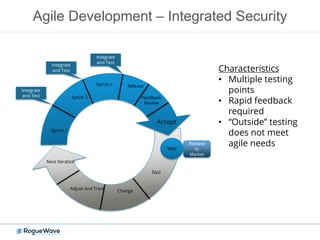
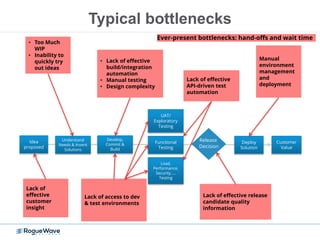
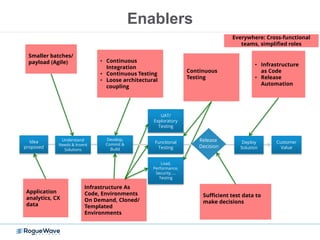
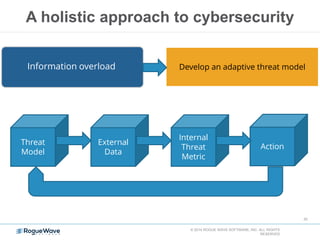
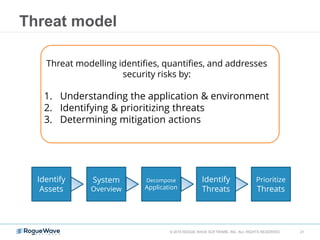
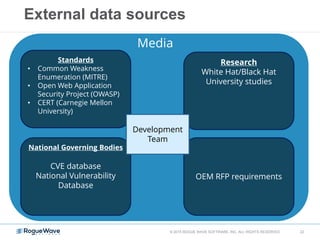
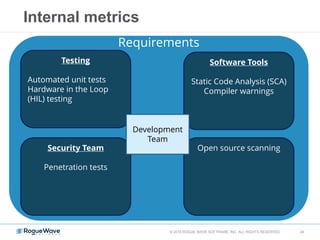
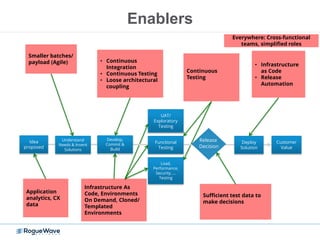
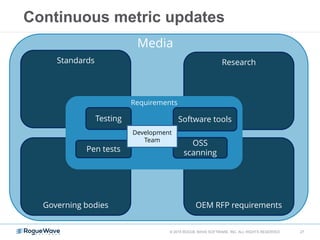
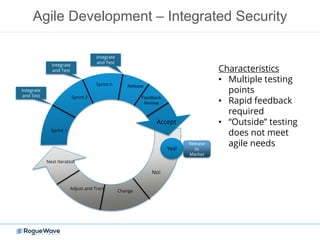
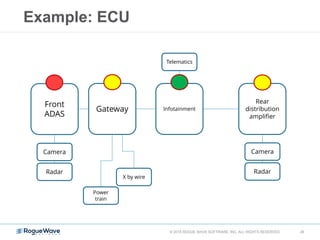
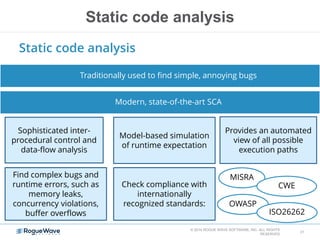
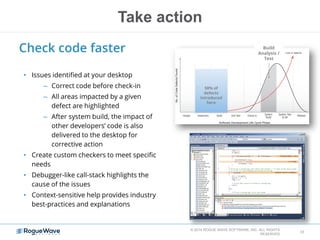
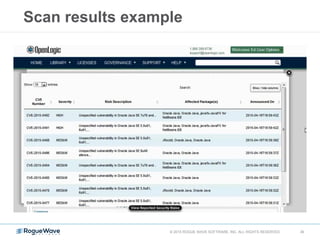
The document discusses enhancing application security through improved code confidence, emphasizing the need for a holistic cybersecurity strategy and addressing risks like network intrusion and code vulnerabilities. It suggests that organizations must integrate security into their software development processes, educate teams, and implement automated testing. Key takeaways include the importance of maintaining a secure supply chain, regular updates to security metrics, and the need for adaptable threat models tailored to specific needs.