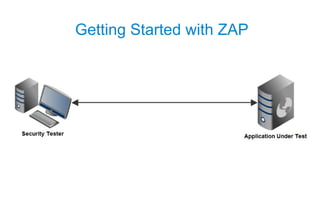
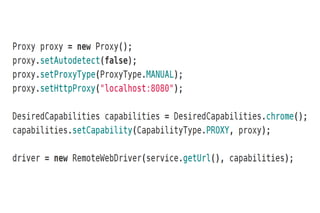
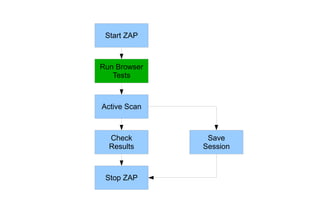
This document discusses automated security testing using the Zed Attack Proxy (ZAP) tool. It describes how ZAP can be used to passively and actively scan web applications for security vulnerabilities by intercepting HTTP traffic. It also provides examples of integrating ZAP into continuous integration builds using its REST API and tasks for Ant and Maven. While automated testing finds many issues, some vulnerabilities still require human intelligence to identify false positives and negatives.