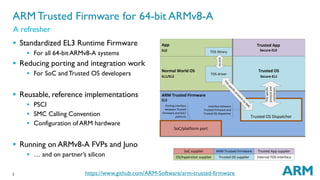
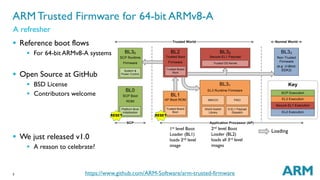
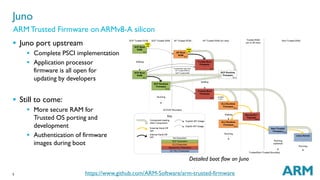
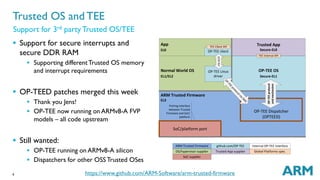
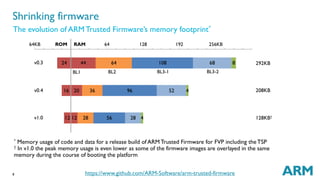
The document outlines the capabilities and updates of ARM Trusted Firmware for 64-bit ARMv8-A systems. It discusses standardized firmware, reference implementations, and integration with trusted operating systems, while highlighting recent developments such as a complete PSCI implementation and the integration of OP-TEE. The presentation emphasizes the open-source nature of the firmware and invites contributions from developers.