Kernel modules allow adding and removing functionality from the Linux kernel while it is running. Modules are compiled as ELF binaries with a .ko extension and are loaded and unloaded using commands like insmod, rmmod, and modprobe. Modules can export symbols to be used by other modules and have dependencies on other modules that must be loaded first. The kernel tracks modules and their state using data structures like struct module to manage loading, unloading, and dependencies between modules.






![Inside the kernel module
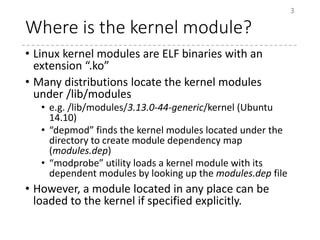
• What sections are inside a kernel module?
8
$ readelf –a hello.ko
Section Headers:
[Nr] Name Type Address Offset
Size EntSize Flags Link Info Align
…
[ 2] .text PROGBITS 0000000000000000 00000064
0000000000000000 0000000000000000 AX 0 0 1
[ 3] .init.text PROGBITS 0000000000000000 00000064
0000000000000016 0000000000000000 AX 0 0 1
[ 4] .rela.init.text RELA 0000000000000000 000009c0
0000000000000030 0000000000000018 16 3 8
[ 5] .exit.text PROGBITS 0000000000000000 0000007a
0000000000000006 0000000000000000 AX 0 0 1
…
[ 7] .modinfo PROGBITS 0000000000000000 00000091
00000000000000c1 0000000000000000 A 0 0 1
[ 8] __versions PROGBITS 0000000000000000 00000160
0000000000000080 0000000000000000 A 0 0 32
…
[18] .gnu.linkonce.thi PROGBITS 0000000000000000 00000280
0000000000000260 0000000000000000 WA 0 0 32](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-9-320.jpg)

![Module load and unload
• The simplest way : “insmod” and “rmmod” commands
• More sophisticated way is “modprobe” and “modprobe –r”
• The former tries to load modules which the specified module
depends on
• The latter tries to unload modules which the specified module
depends on
10
# insmod (file name) [parameters…]
(e.g.) # insmod helloworld.ko msg=hoge
# rmmod (module name)
(e.g.) # rmmod helloworld](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-11-320.jpg)





![Data structures for modules
• struct module (too large..)
16
struct module {
enum module_state state;
/* Member of list of modules */
struct list_head list;
/* Unique handle for this module */
char name[MODULE_NAME_LEN];
/* Sysfs stuff. */
struct module_kobject mkobj;
...
/* Exported symbols */
const struct kernel_symbol *syms;
const unsigned long *crcs;
unsigned int num_syms;
/* Kernel parameters. */
struct kernel_param *kp;
unsigned int num_kp;
“modules” list
Exported symbols
Symbol CRC](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-17-320.jpg)










![sys_init_module/sys_finit_module
• Initialize a load_info structure
• Check whether module load is permitted or not.
(may_init_module function)
• [finit only] Flags check
• [init only] Copy module data in user memory to
kernel memory (copy_module_from_user function)
• [finit only] Read from the fd into kernel memory
(copy_module_from_fd function)
• Call the load_module function
28](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-29-320.jpg)

























![module to final place
• Struct module for the module loaded was pointed
to the temporary module image memory
• Now, it’s loaded and copied to the final location , so
the pointer is also changed to the final location
55
/* Module has been copied to its final place now: return it. */
mod = (void *)info->sechdrs[info->index.mod].sh_addr;](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-56-320.jpg)
![load_module function (1) [RE]
• Signature check (module_sig_check)
• ELF header check (elf_header_check)
• Layout and allocate the final location for the module
(layout_and_allocate)
• Add the module to the “modules” list
(add_unformed_module)
• Allocate per-cpu areas used in the module
(percpu_modalloc)
• Initialize link lists used for dependency management and
unloading features (module_unload_init)
• Find optional sections (find_module_sections)
• License and version dirty hack
(check_module_license_and_versions)
• Setup MODINFO_ATTR fields (setup_modinfo)
56](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-57-320.jpg)



![percpu_modalloc
• Allocate per-cpu area for the size of the per-cpu
section
60
static int percpu_modalloc(struct module *mod, struct load_info *info)
{
Elf_Shdr *pcpusec = &info->sechdrs[info->index.pcpu];
unsigned long align = pcpusec->sh_addralign;
if (!pcpusec->sh_size)
return 0;
...
mod->percpu = __alloc_reserved_percpu(pcpusec->sh_size, align);
if (!mod->percpu) {
pr_warn("%s: Could not allocate %lu bytes percpu datan",
mod->name, (unsigned long)pcpusec->sh_size);
return -ENOMEM;
}
mod->percpu_size = pcpusec->sh_size;
return 0;
}](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-61-320.jpg)





![load_module function (2) [Re]
• Resolve the symbols (simplify_symbols)
• Fix up the addresses in the module (apply_relocations)
• Extable and per-cpu initialization (post_relocation)
• Flush I-cache for the module area
(flush_module_icache)
• Copy the module parameters to mod->args.
• Check duplication of symbols, and setup NX attributes.
(complete_formation)
• Parse the module parameters (parse_args)
• sysfs setup (mod_sysfs_setup)
• Free the copy in the load_info structure (free_copy)
• Call the init function of the module (do_init_module)
66](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-67-320.jpg)
![simplify_symbols
• Change the address of the unresolved symbols in
the “symtab” section to the actual addresses
67
static int simplify_symbols(struct module *mod, const struct load_info *info)
{
Elf_Shdr *symsec = &info->sechdrs[info->index.sym];
Elf_Sym *sym = (void *)symsec->sh_addr;
...
for (i = 1; i < symsec->sh_size / sizeof(Elf_Sym); i++) {
const char *name = info->strtab + sym[i].st_name;
...
case SHN_UNDEF:
ksym = resolve_symbol_wait(mod, info, name);
/* Ok if resolved. */
if (ksym && !IS_ERR(ksym)) {
sym[i].st_value = ksym->value;
break;
}
/* Ok if weak. */
if (!ksym && ELF_ST_BIND(sym[i].st_info) == STB_WEAK)
break;](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-68-320.jpg)
![resolve_symbol_wait
• Waits if the resolved symbol is that of the module
which is under initialization.
68
static const struct kernel_symbol *
resolve_symbol_wait(struct module *mod,
const struct load_info *info,
const char *name)
{
const struct kernel_symbol *ksym;
char owner[MODULE_NAME_LEN];
if (wait_event_interruptible_timeout(module_wq,
!IS_ERR(ksym = resolve_symbol(mod, info, name, owner))
|| PTR_ERR(ksym) != -EBUSY,
30 * HZ) <= 0) {
pr_warn("%s: gave up waiting for init of module %s.n",
mod->name, owner);
}
return ksym;
}](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-69-320.jpg)

![find_symbol (1)
• Well, try to find it from the kernel
70
bool each_symbol_section(bool (*fn)(const struct symsearch *arr,
struct module *owner,
void *data),
void *data)
{
struct module *mod;
static const struct symsearch arr[] = {
{ __start___ksymtab, __stop___ksymtab, __start___kcrctab,
NOT_GPL_ONLY, false },
{ __start___ksymtab_gpl, __stop___ksymtab_gpl,
__start___kcrctab_gpl,
GPL_ONLY, false },
{ __start___ksymtab_gpl_future, __stop___ksymtab_gpl_future,
__start___kcrctab_gpl_future,
WILL_BE_GPL_ONLY, false },
...
};
if (each_symbol_in_section(arr, ARRAY_SIZE(arr), NULL, fn, data))
return true;](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-71-320.jpg)
![find_symbol (2)
• And, try to find in the modules (after UNFORMED)
71
list_for_each_entry_rcu(mod, &modules, list) {
struct symsearch arr[] = {
{ mod->syms, mod->syms + mod->num_syms, mod->crcs,
NOT_GPL_ONLY, false },
{ mod->gpl_syms, mod->gpl_syms + mod->num_gpl_syms,
mod->gpl_crcs,
GPL_ONLY, false },
{ mod->gpl_future_syms,
mod->gpl_future_syms + mod->num_gpl_future_syms,
mod->gpl_future_crcs,
WILL_BE_GPL_ONLY, false },
if (mod->state == MODULE_STATE_UNFORMED)
continue;
if (each_symbol_in_section(arr, ARRAY_SIZE(arr), mod, fn,
data))
return true;
}
return false;
}](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-72-320.jpg)



![apply_relocations
• Apply relocations for each “rel” section
• “rel” sections
• Section Type : SHT_REL or SHT_RELA
75
[Nr] Name Type Address Offset
Size EntSize Flags Link Info Align
[ 2] .text PROGBITS 0000000000000000 00000070
0000000000000019 0000000000000000 AX 0 0 16
[ 3] .rela.text RELA 0000000000000000 00000ca8
0000000000000048 0000000000000018 24 2 8
[ 4] .init.text PROGBITS 0000000000000000 00000089
0000000000000016 0000000000000000 AX 0 0 1
[ 5] .rela.init.text RELA 0000000000000000 00000cf0
0000000000000030 0000000000000018 24 4 8
[24] .symtab SYMTAB 0000000000000000 00000db0
00000000000003c0 0000000000000018 25 32 8
[25] .strtab STRTAB 0000000000000000 00001170
000000000000014a 0000000000000000 0 0 1](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-76-320.jpg)

![apply_relocate[_add]
• Addressing is architecture-dependent, so the
relocation is also architecture-dependent
• x86_64 (RELA)
• An RELA section is an array of Elf64_Rela
• In the “printk” example
• r_offset = 0x13
• r_info = R_X86_64_PC32 (RIP-relative in x86_64)
• r_addend = -0x04
77
typedef struct elf64_rela {
Elf64_Addr r_offset; /* Location at which to apply the action */
Elf64_Xword r_info; /* index and type of relocation */
Elf64_Sxword r_addend; /* Constant addend used to compute value */
} Elf64_Rela;](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-78-320.jpg)
![apply_relocate_add in x86_64
78
int apply_relocate_add(Elf64_Shdr *sechdrs,
const char *strtab,
unsigned int symindex,
unsigned int relsec,
struct module *me)
{
...
for (i = 0; i < sechdrs[relsec].sh_size / sizeof(*rel); i++) {
/* This is where to make the change */
loc = (void *)sechdrs[sechdrs[relsec].sh_info].sh_addr
+ rel[i].r_offset;
/* This is the symbol it is referring to. Note that
all undefined symbols have been resolved. */
sym = (Elf64_Sym *)sechdrs[symindex].sh_addr
+ ELF64_R_SYM(rel[i].r_info);
...
val = sym->st_value + rel[i].r_addend;](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-79-320.jpg)
![apply_relocate_add in x86_64
79
switch (ELF64_R_TYPE(rel[i].r_info)) {
...
case R_X86_64_64:
*(u64 *)loc = val;
break;
...
case R_X86_64_32S:
*(s32 *)loc = val;
if ((s64)val != *(s32 *)loc)
goto overflow;
break;
case R_X86_64_PC32:
val -= (u64)loc;
*(u32 *)loc = val;
#if 0
if ((s64)val != *(s32 *)loc)
goto overflow;
#endif
break;
Calculate the delta between
the current address and the
target address](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-80-320.jpg)

![module_finalize in x86_64
• Alternatives, paravirt and so on.
81
int module_finalize(const Elf_Ehdr *hdr,
const Elf_Shdr *sechdrs,
struct module *me)
{
const Elf_Shdr *s, *text = NULL, *alt = NULL, *locks = NULL,
*para = NULL;
char *secstrings = (void *)hdr + sechdrs[hdr->e_shstrndx].sh_offset;
for (s = sechdrs; s < sechdrs + hdr->e_shnum; s++) {
if (!strcmp(".text", secstrings + s->sh_name))
text = s;
if (!strcmp(".altinstructions", secstrings + s->sh_name))
alt = s;
if (!strcmp(".smp_locks", secstrings + s->sh_name))
locks = s;
if (!strcmp(".parainstructions", secstrings + s->sh_name))
para = s;
if (alt) {
/* patch .altinstructions */
void *aseg = (void *)alt->sh_addr;
apply_alternatives(aseg, aseg + alt->sh_size);
}
...](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-82-320.jpg)


![load_module function (2) [Re]
• Resolve the symbols (simplify_symbols)
• Fix up the addresses in the module (apply_relocations)
• Extable and per-cpu initialization (post_relocation)
• Flush I-cache for the module area
(flush_module_icache)
• Copy the module parameters to mod->args.
• Check duplication of symbols, and setup NX attributes.
(complete_formation)
• Parse the module parameters (parse_args)
• sysfs setup (mod_sysfs_setup)
• Free the copy in the load_info structure (free_copy)
• Call the init function of the module (do_init_module)
84](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-85-320.jpg)





![Now (3.19) [RE]
• Reference count is now atomic_t (was per-cpu int
before) and checked without stop_machine
• (thanks to a mysterious guy)
90
static int try_stop_module(struct module *mod, int flags, int *forced)
{
/* If it's not unused, quit unless we're forcing. */
if (try_release_module_ref(mod) != 0) {
*forced = try_force_unload(flags);
if (!(*forced))
return -EWOULDBLOCK;
}
/* Mark it as dying. */
mod->state = MODULE_STATE_GOING;
return 0;
}](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-91-320.jpg)


![Build steps (1) : .c -> .o
• make .tmp_versions, create .tmp_versions/<module>.mod
• The file contains the names of the final .ko file and source .o files
• Compile .tmp_[name].o from [name].c
• Calculate the CRCs (version) for the exported symbols
• Find a __ksymtab section in .tmp_[name].o
• objdump –h (obj) | grep –q __ksymtab
• Calculate CRC for exported symbols in the source file by genksyms
(Output is LD Script format)
• Compile the CRC values into the object file.
93
cmd_modversions =
if $(OBJDUMP) -h $(@D)/.tmp_$(@F) | grep -q __ksymtab; then
$(call cmd_gensymtypes,$(KBUILD_SYMTYPES),$(@:.o=.symtypes))
> $(@D)/.tmp_$(@F:.o=.ver);
$(LD) $(LDFLAGS) -r -o $@ $(@D)/.tmp_$(@F)
-T $(@D)/.tmp_$(@F:.o=.ver);
rm -f $(@D)/.tmp_$(@F) $(@D)/.tmp_$(@F:.o=.ver);
else
mv -f $(@D)/.tmp_$(@F) $@;
fi;
_crc_say_hello = 0xb37b83db ;](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-94-320.jpg)
![Exported Symbols
• Each exported symbol has a struct in __ksymtab*
section.
94
#define __EXPORT_SYMBOL(sym, sec)
extern typeof(sym) sym;
__CRC_SYMBOL(sym, sec)
static const char __kstrtab_##sym[]
__attribute__((section("__ksymtab_strings"), aligned(1)))
= VMLINUX_SYMBOL_STR(sym);
extern const struct kernel_symbol __ksymtab_##sym;
__visible const struct kernel_symbol __ksymtab_##sym
__used
__attribute__((section("___ksymtab" sec "+" #sym), unused))
= { (unsigned long)&sym, __kstrtab_##sym }
#define EXPORT_SYMBOL(sym)
__EXPORT_SYMBOL(sym, "")
#define EXPORT_SYMBOL_GPL(sym)
__EXPORT_SYMBOL(sym, "_gpl")
#define EXPORT_SYMBOL_GPL_FUTURE(sym)
__EXPORT_SYMBOL(sym, "_gpl_future")
(include/linux/export.h)](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-95-320.jpg)



![modpost (1)
• Collects module information, symbol information
and versions from kernel symbols, object files, and
generate module source file and symvers file.
• Arguments
• Options
98
Option Description
-m CONFIG_MODVERSIONS (Symbol version)
-a CONFIG_MODULE_SRCVERSION_ALL (“srcversion” in modinfo)
MD4 for the source files that made the module
-I (symvers file) Input symbol versions (kernel symbols)
-e (symvers file) Input extra symbol versions
-o (symvers file) Output symbol versions (for exported symbols of the module)
-T (files) Source (object) file list
$ modpost [Options...] [(Module object files...)]](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-99-320.jpg)
![modpost (2)
• Generate the source file
99
for (mod = modules; mod; mod = mod->next) {
char fname[PATH_MAX];
...
buf.pos = 0;
add_header(&buf, mod);
add_intree_flag(&buf, !external_module);
add_staging_flag(&buf, mod->name);
err |= add_versions(&buf, mod);
add_depends(&buf, mod, modules);
add_moddevtable(&buf, mod);
add_srcversion(&buf, mod);
sprintf(fname, "%s.mod.c", mod->name);
write_if_changed(&buf, fname);
}
(scripts/mod/modpost.c)](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-100-320.jpg)
![modpost (3)
• Dump the symbol versions
100
static void write_dump(const char *fname)
{
struct buffer buf = { };
struct symbol *symbol;
int n;
for (n = 0; n < SYMBOL_HASH_SIZE ; n++) {
symbol = symbolhash[n];
while (symbol) {
if (dump_sym(symbol))
buf_printf(&buf, "0x%08xt%st%st%sn",
symbol->crc, symbol->name,
symbol->module->name,
export_str(symbol->export));
symbol = symbol->next;
}
}
write_if_changed(&buf, fname);
}
(scripts/mod/modpost.c)0xb37b83db say_hello /home/shimos/test_module/hello EXPORT_SYMBOL](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-101-320.jpg)
![Generated <module>.mod.c (1)
• Example
101
#include <linux/module.h>
#include <linux/vermagic.h>
#include <linux/compiler.h>
MODULE_INFO(vermagic, VERMAGIC_STRING);
__visible struct module __this_module
__attribute__((section(".gnu.linkonce.this_module"))) = {
.name = KBUILD_MODNAME,
.init = init_module,
#ifdef CONFIG_MODULE_UNLOAD
.exit = cleanup_module,
#endif
.arch = MODULE_ARCH_INIT,
};
static const struct modversion_info ____versions[]
__used
__attribute__((section("__versions"))) = {
{ 0x9412fa01, __VMLINUX_SYMBOL_STR(module_layout) },
{ 0x27e1a049, __VMLINUX_SYMBOL_STR(printk) },
{ 0xbdfb6dbb, __VMLINUX_SYMBOL_STR(__fentry__) },
}; ...
Additional modinfo is included
Base of struct module
Symbols and (expected) versions
which this module depends on.](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-102-320.jpg)
![Generated <module>.mod.c (2)
• Example
102
static const char __module_depends[]
__used
__attribute__((section(".modinfo"))) =
"depends=";
MODULE_INFO(srcversion, "8D5BACDC1EA9421ABFF79DD")
Modinfo about dependency
(but the kernel does not use this)
Modinfo “srcversion”](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-103-320.jpg)
![modinfo
• The modinfo string is created by macros, and concatenated
by collecting the string into a single section
103
#define __MODULE_INFO(tag, name, info)
static const char __UNIQUE_ID(name)[]
__used __attribute__((section(".modinfo"), unused, aligned(1)))
= __stringify(tag) "=" info
(include/linux/moduleparam.h)
#define MODULE_INFO(tag, info) __MODULE_INFO(tag, tag, info)
...
#define MODULE_LICENSE(_license) MODULE_INFO(license, _license)
...
#define MODULE_AUTHOR(_author) MODULE_INFO(author, _author)
...
(include/linux/module.h)](https://image.slidesharecdn.com/nlkb20150221-150629103624-lva1-app6892/85/Linux-Kernel-Module-For-NLKB-104-320.jpg)
