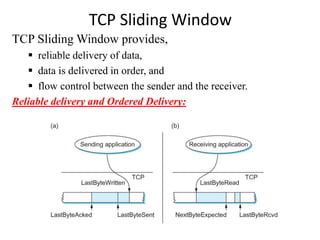
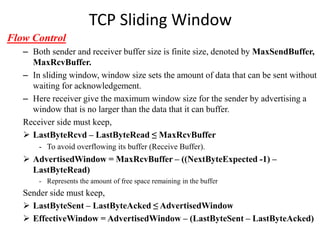
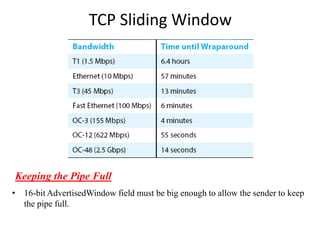
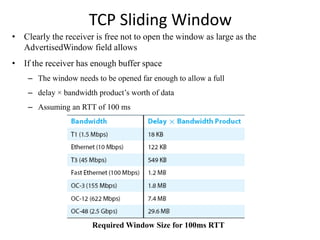
TCP sliding window provides reliable data delivery, ordered data delivery, and flow control between sender and receiver. It works by having the sender track the highest byte sent and acknowledged, and the receiver track the highest byte received and read. This allows each side to know how much buffer space is available. The receiver advertises its available window size to limit how much unacknowledged data the sender can have outstanding.