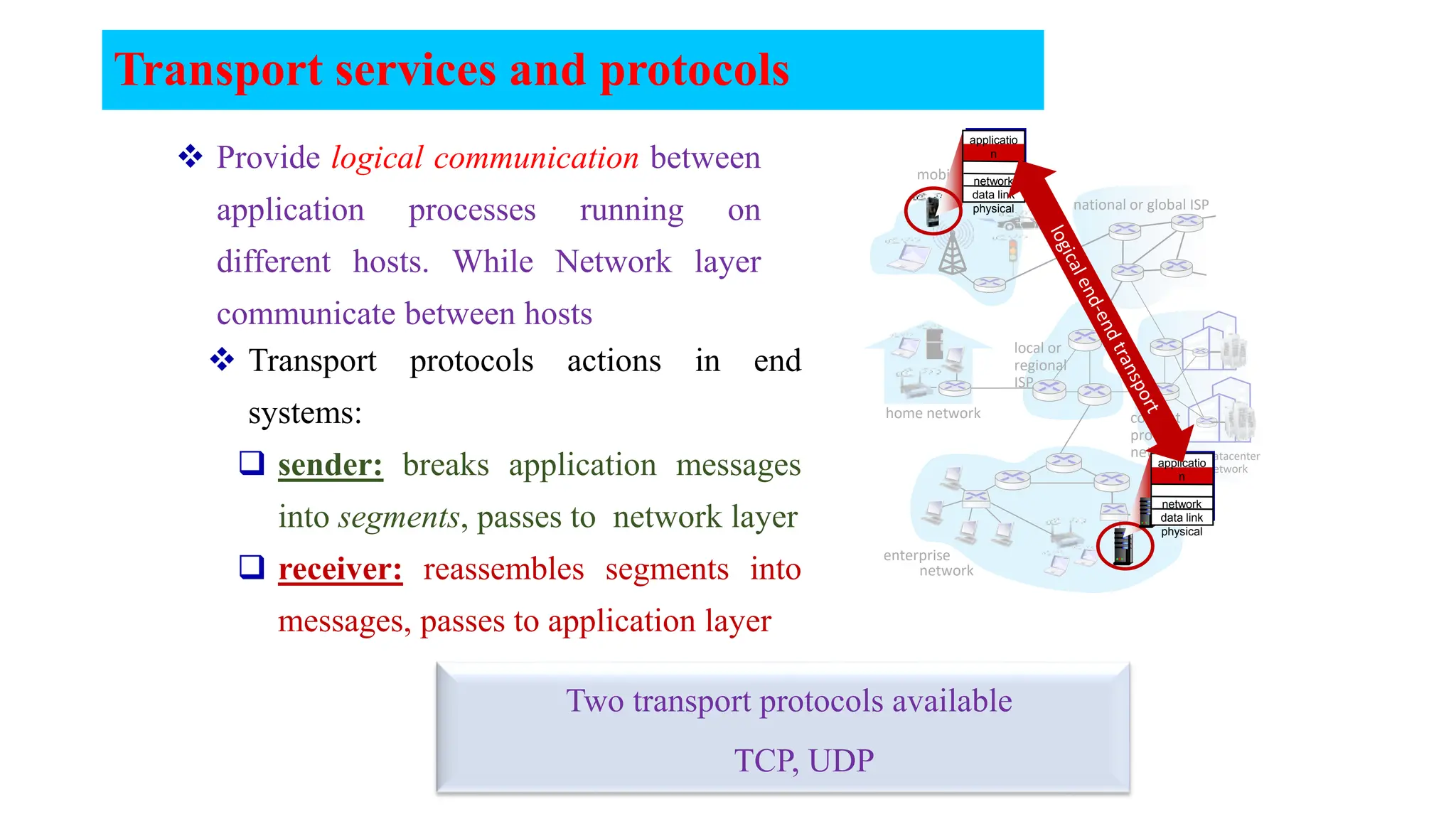
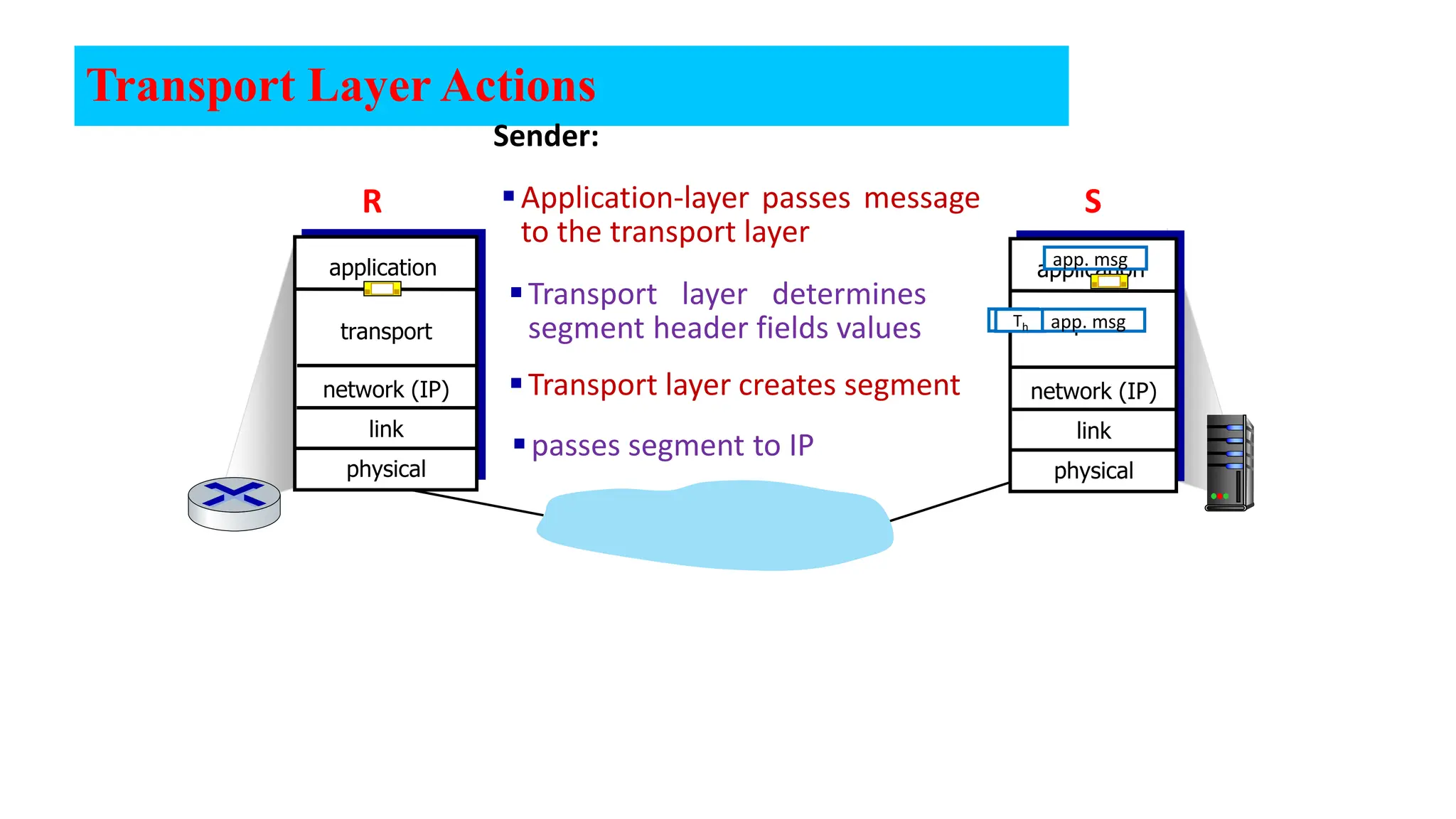
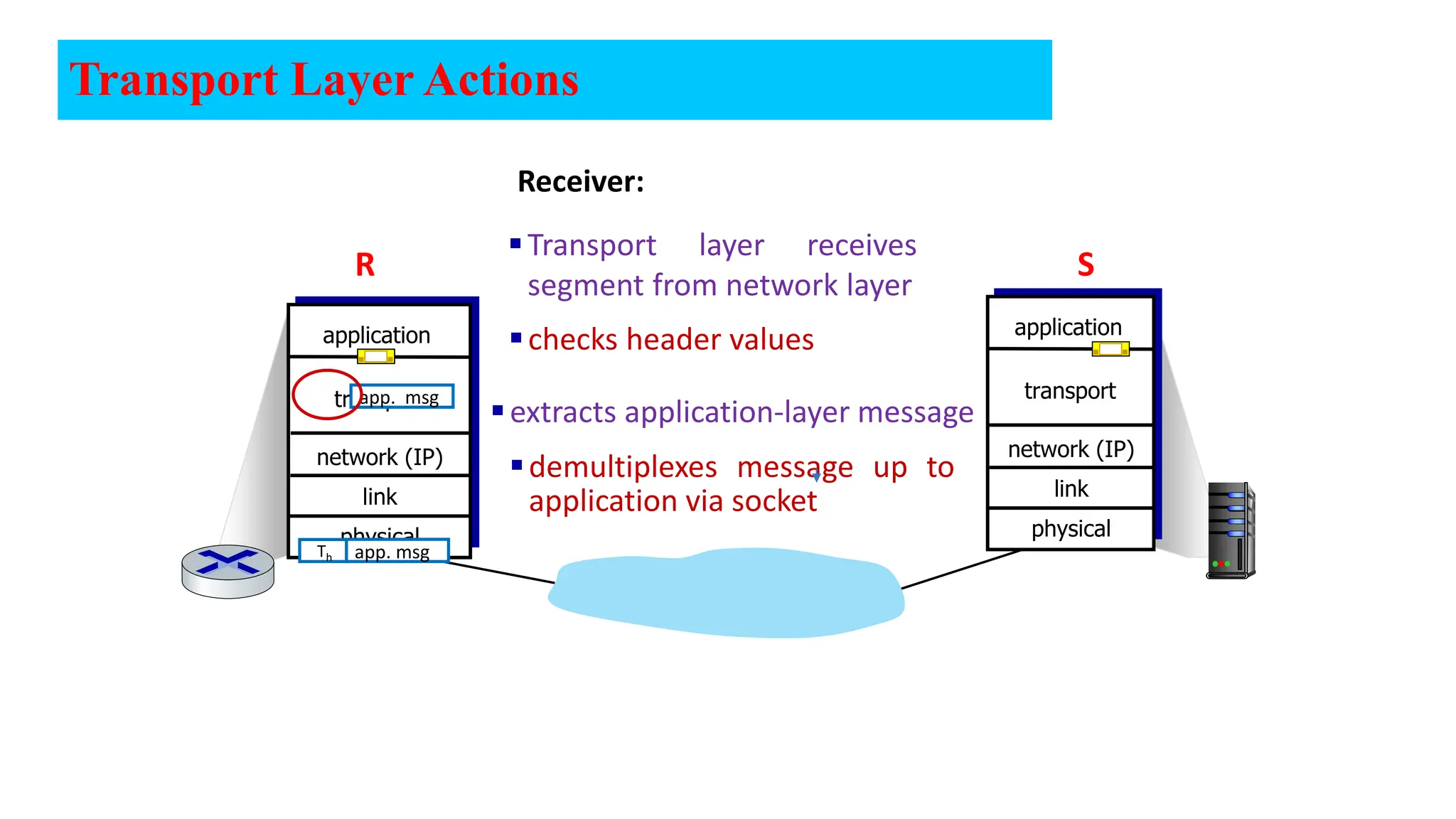
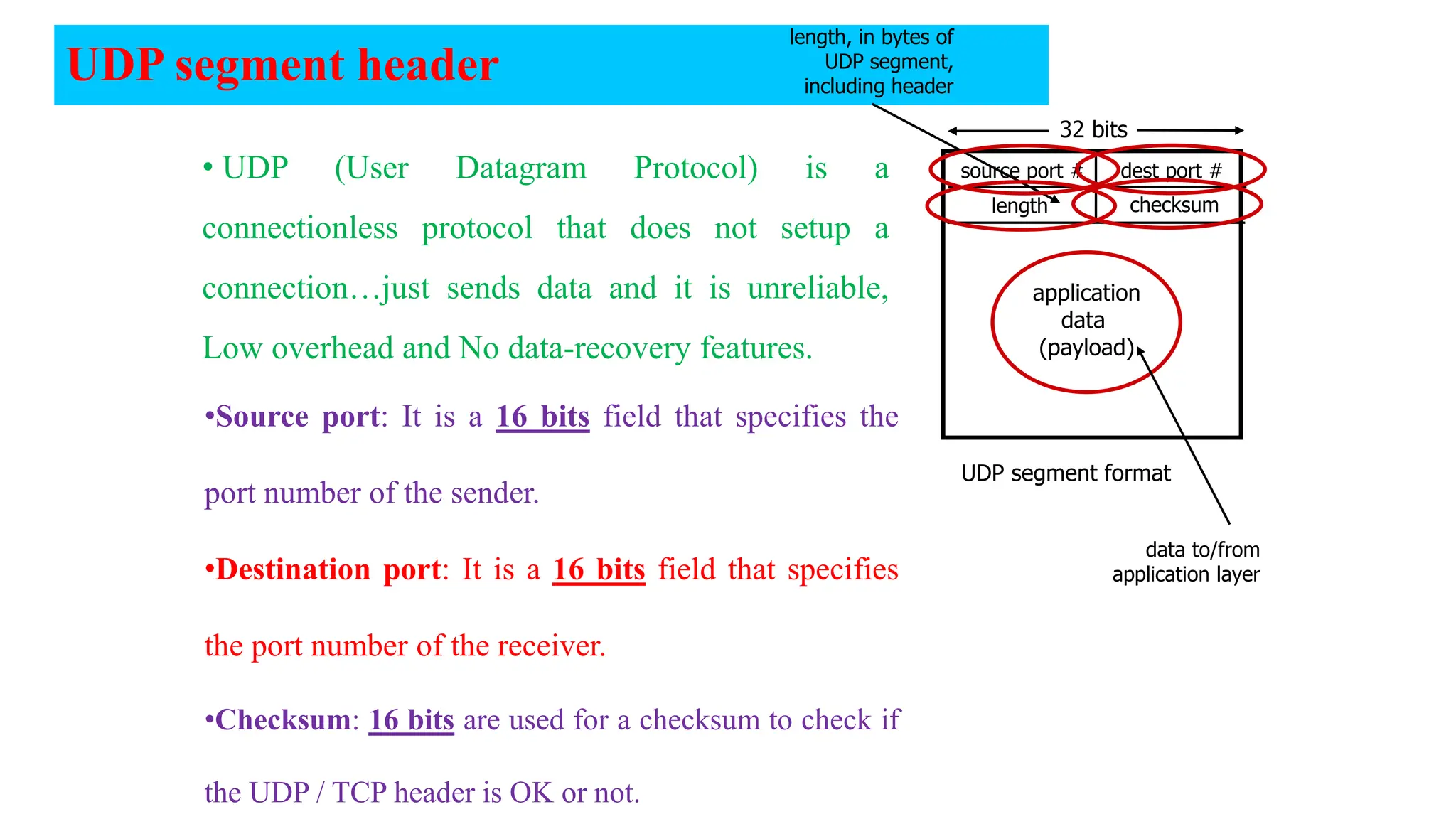
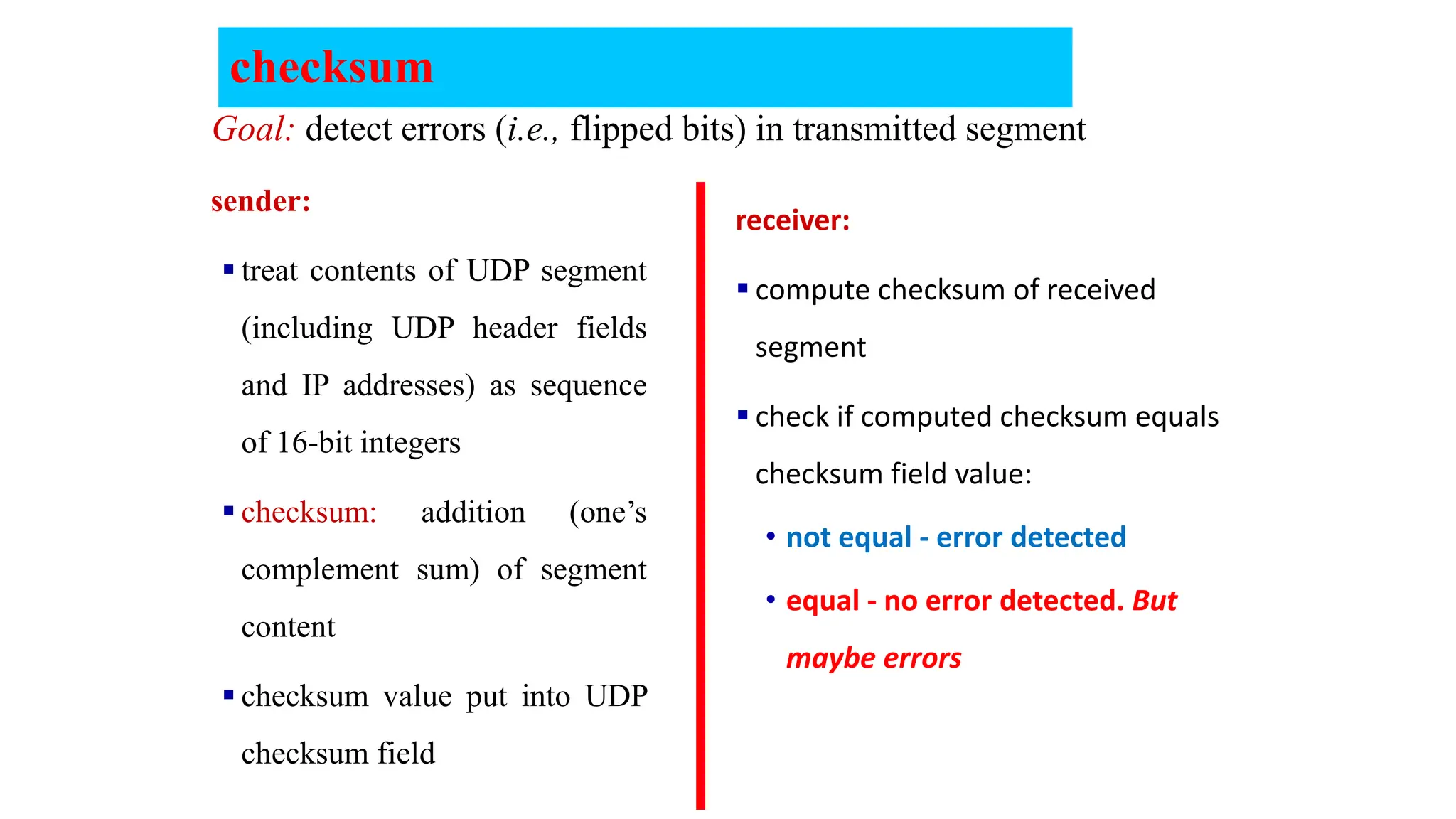
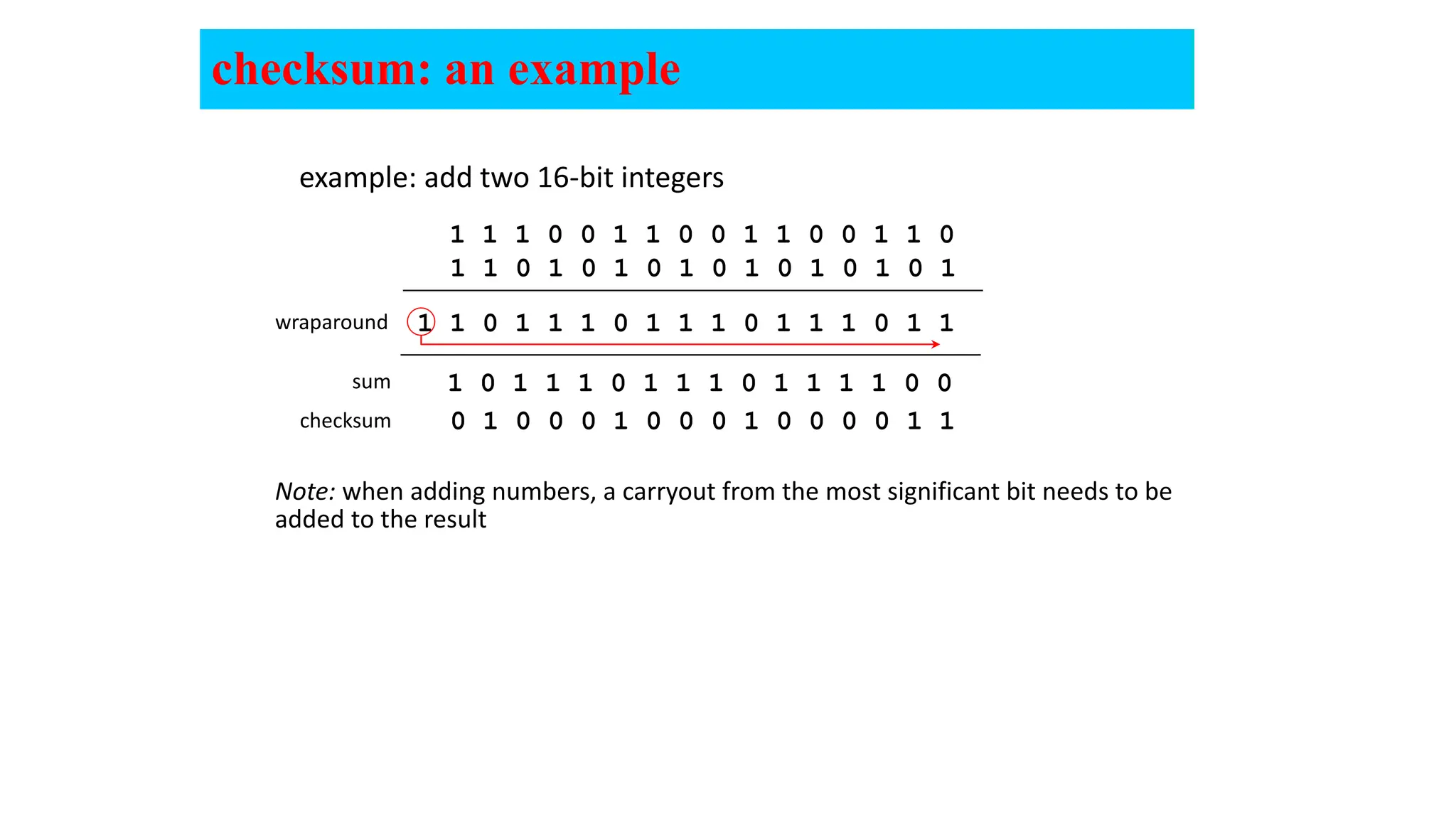
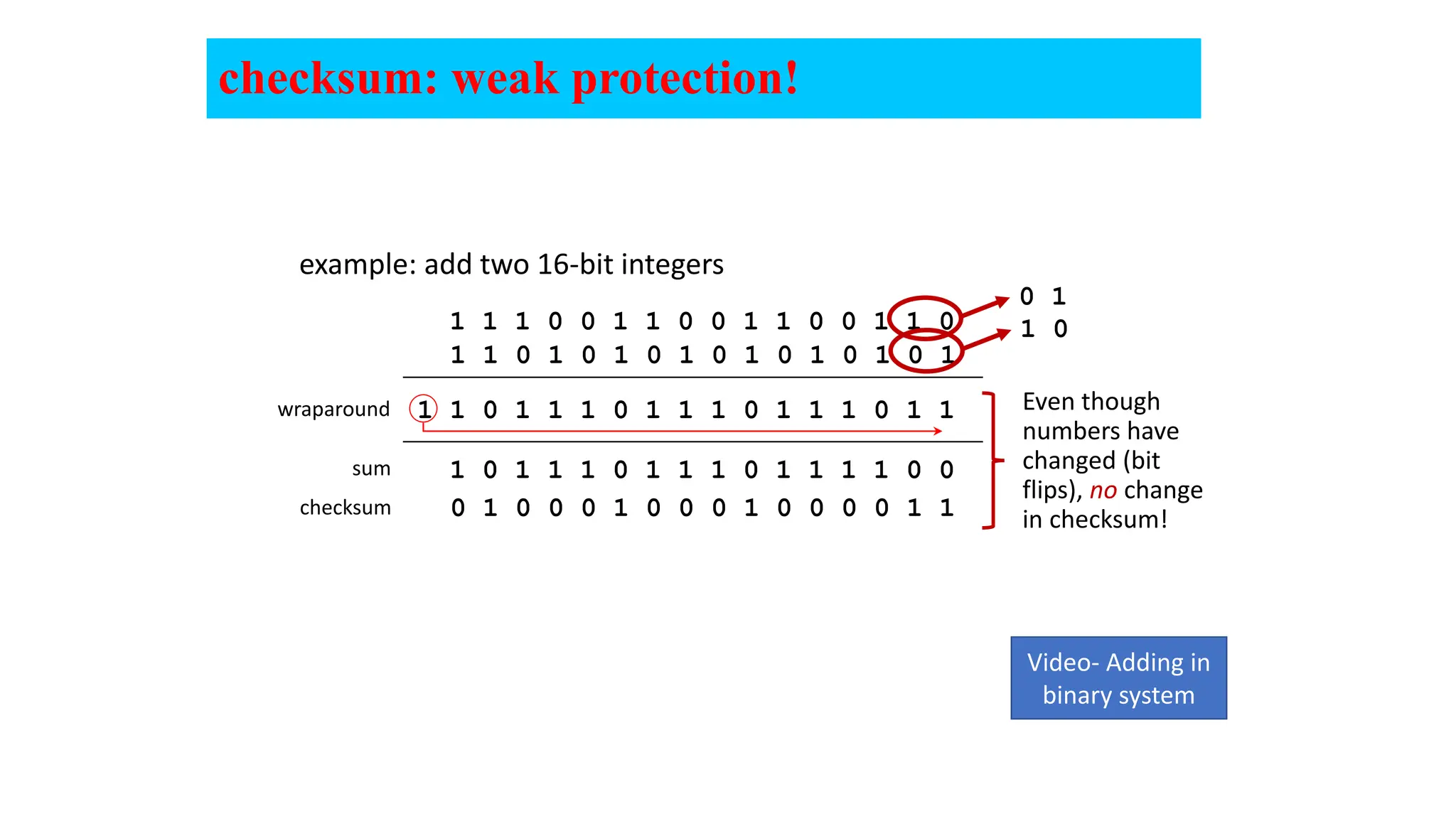
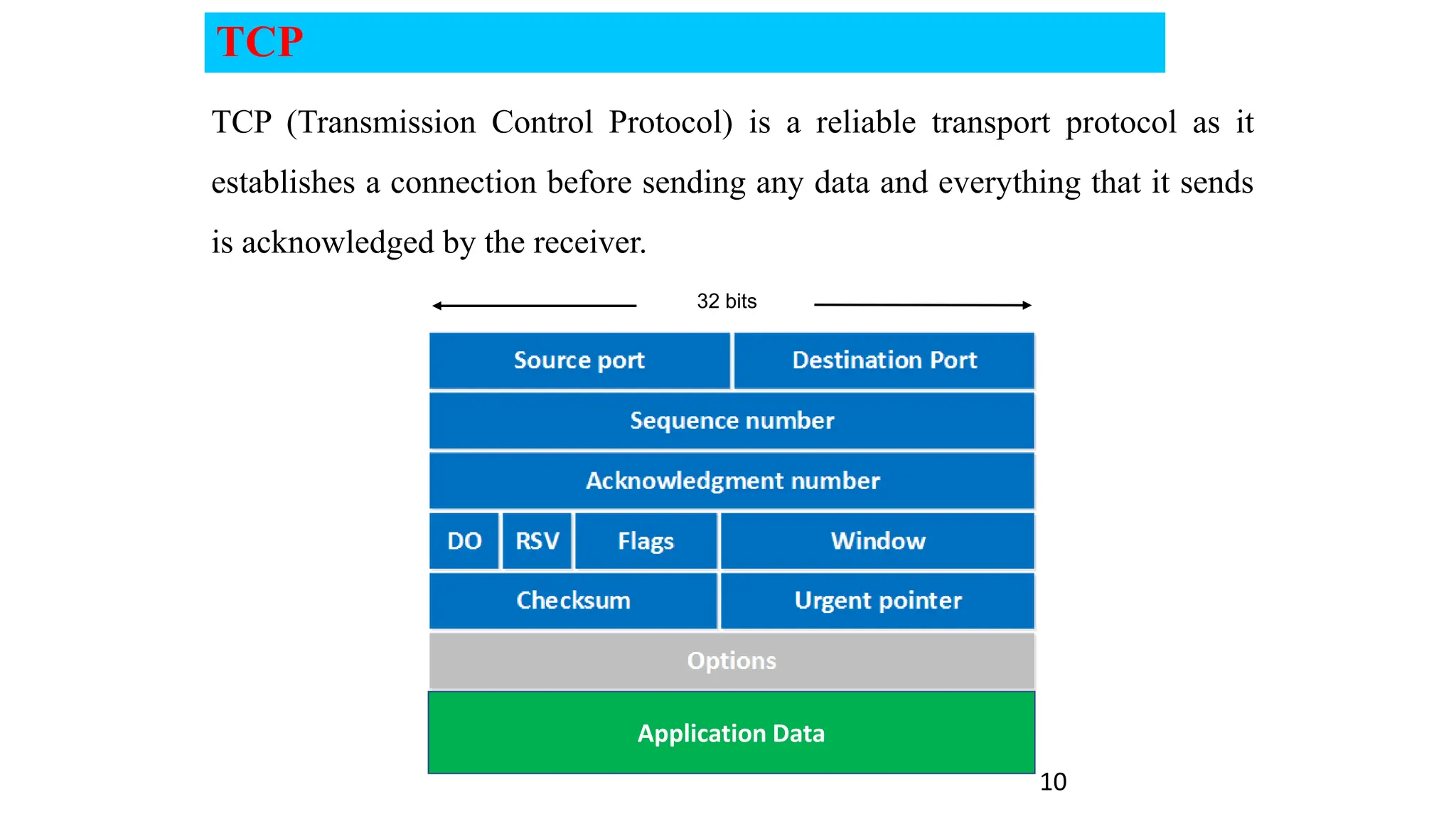
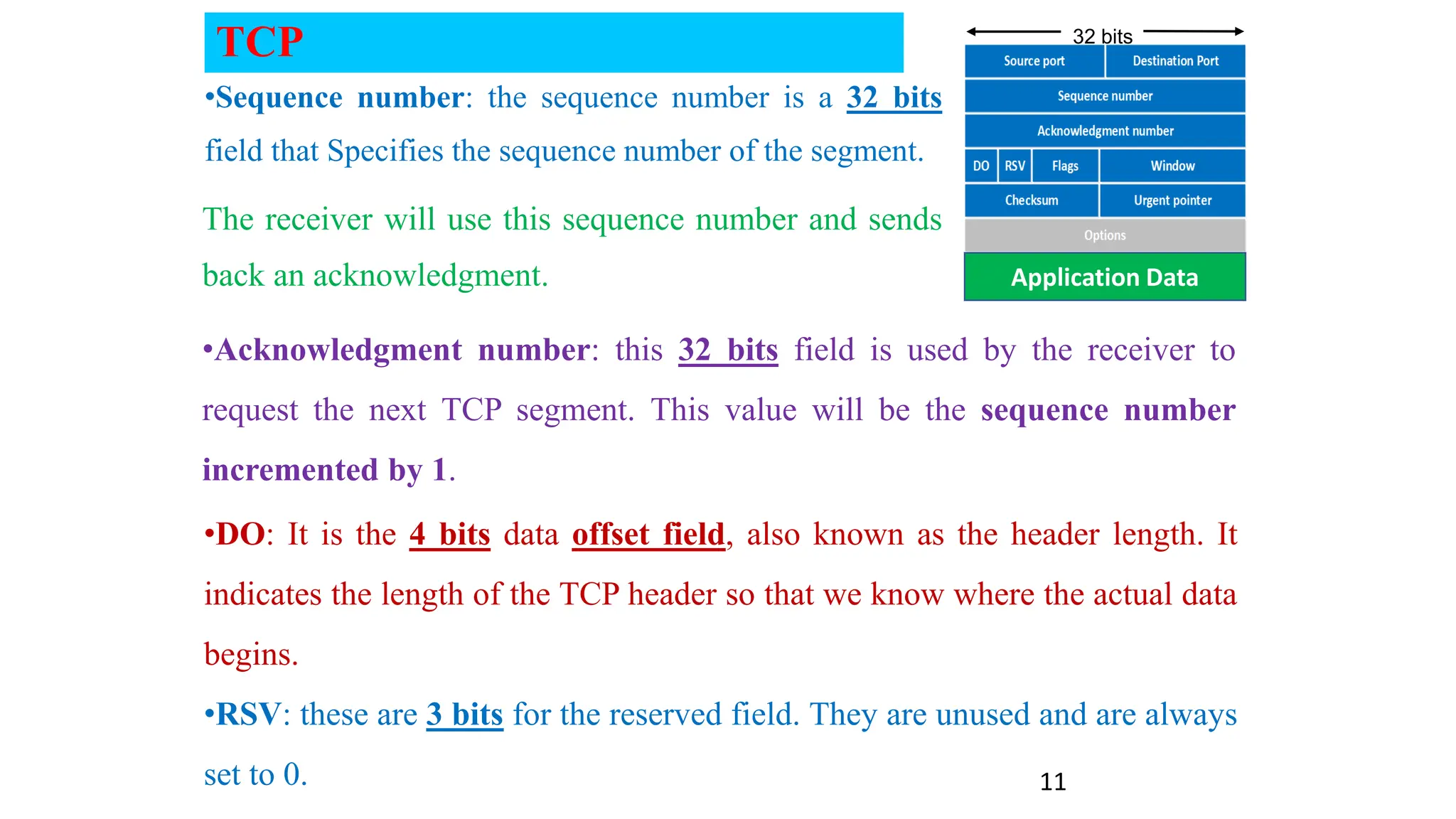
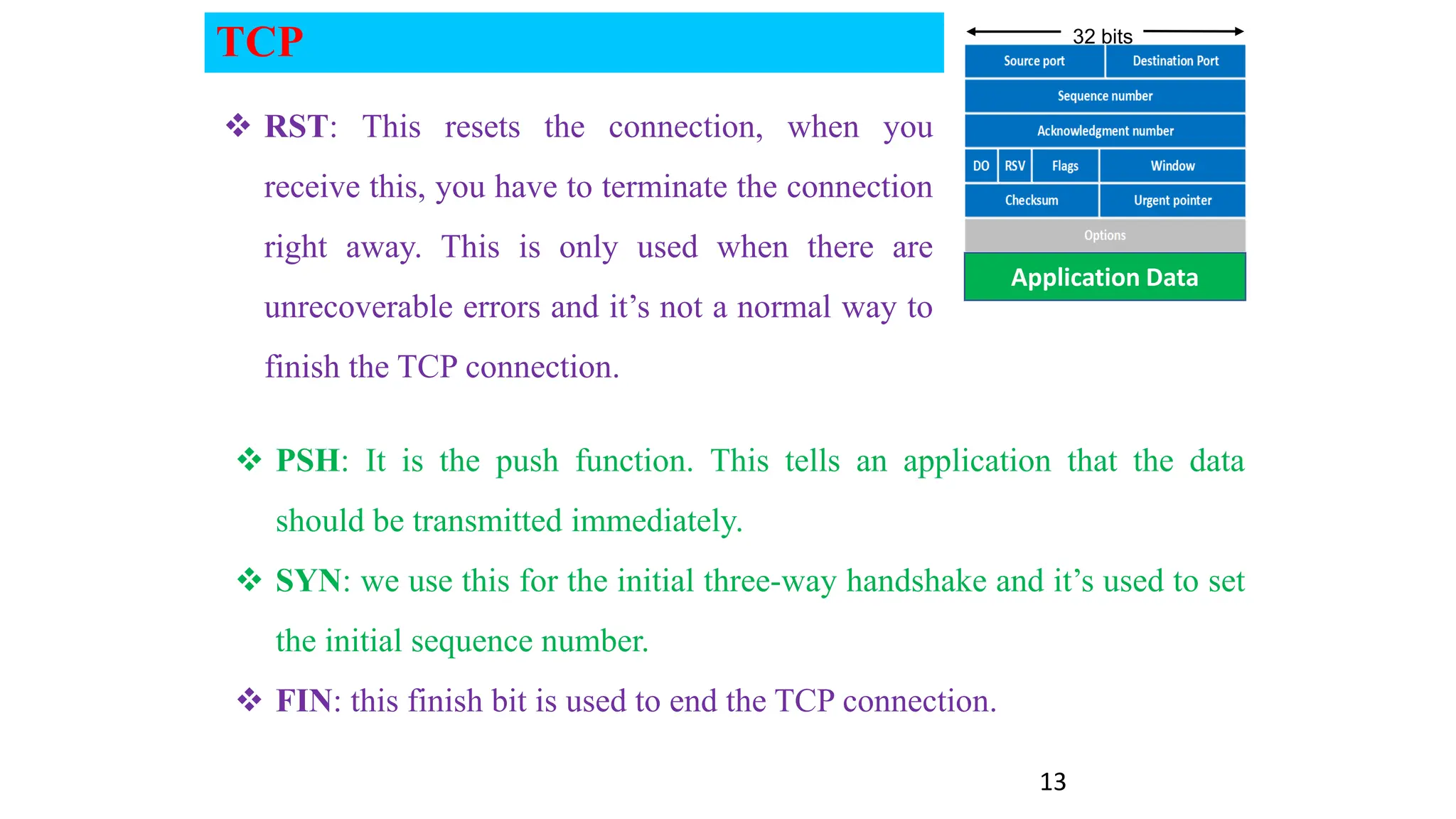
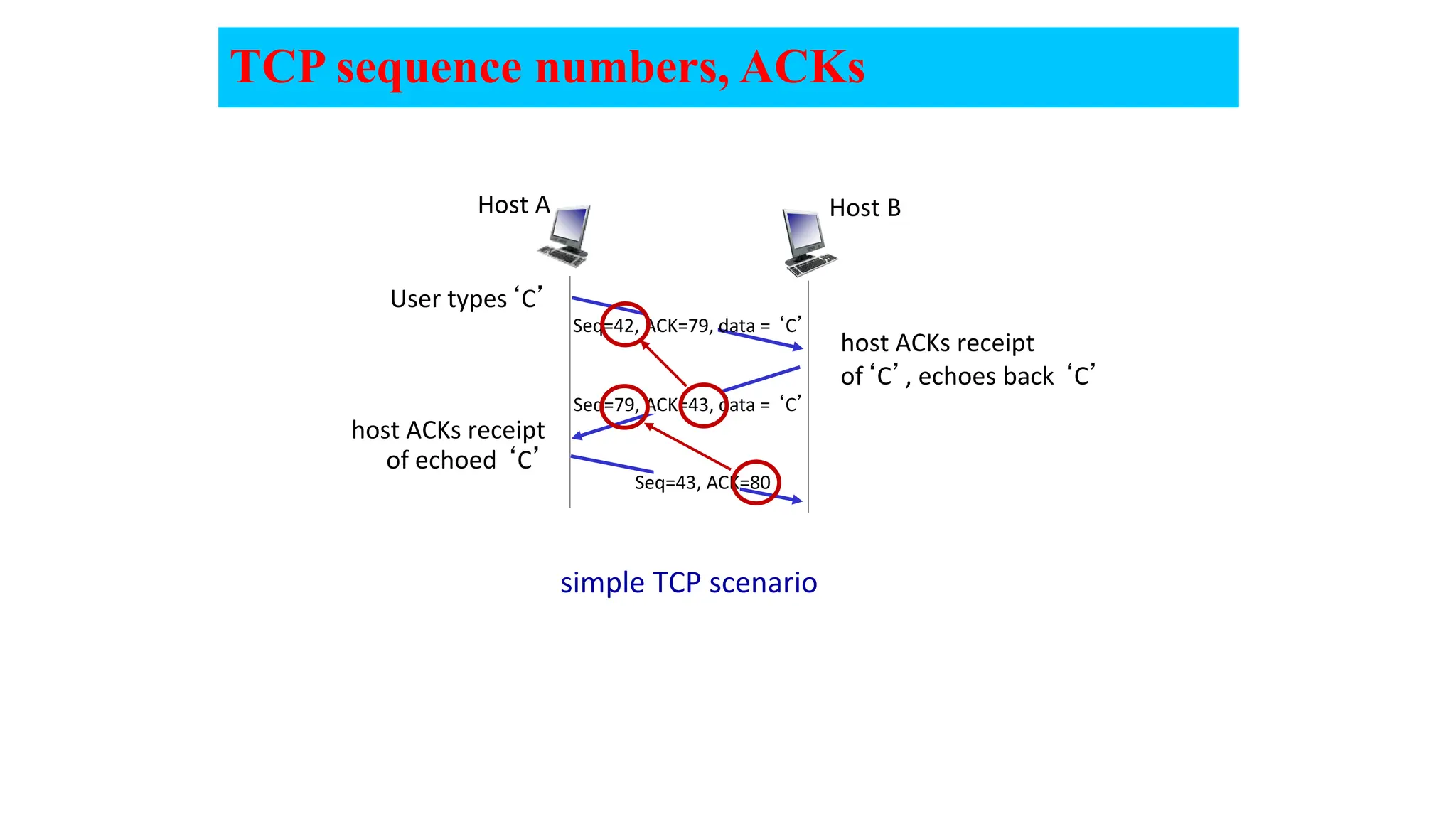
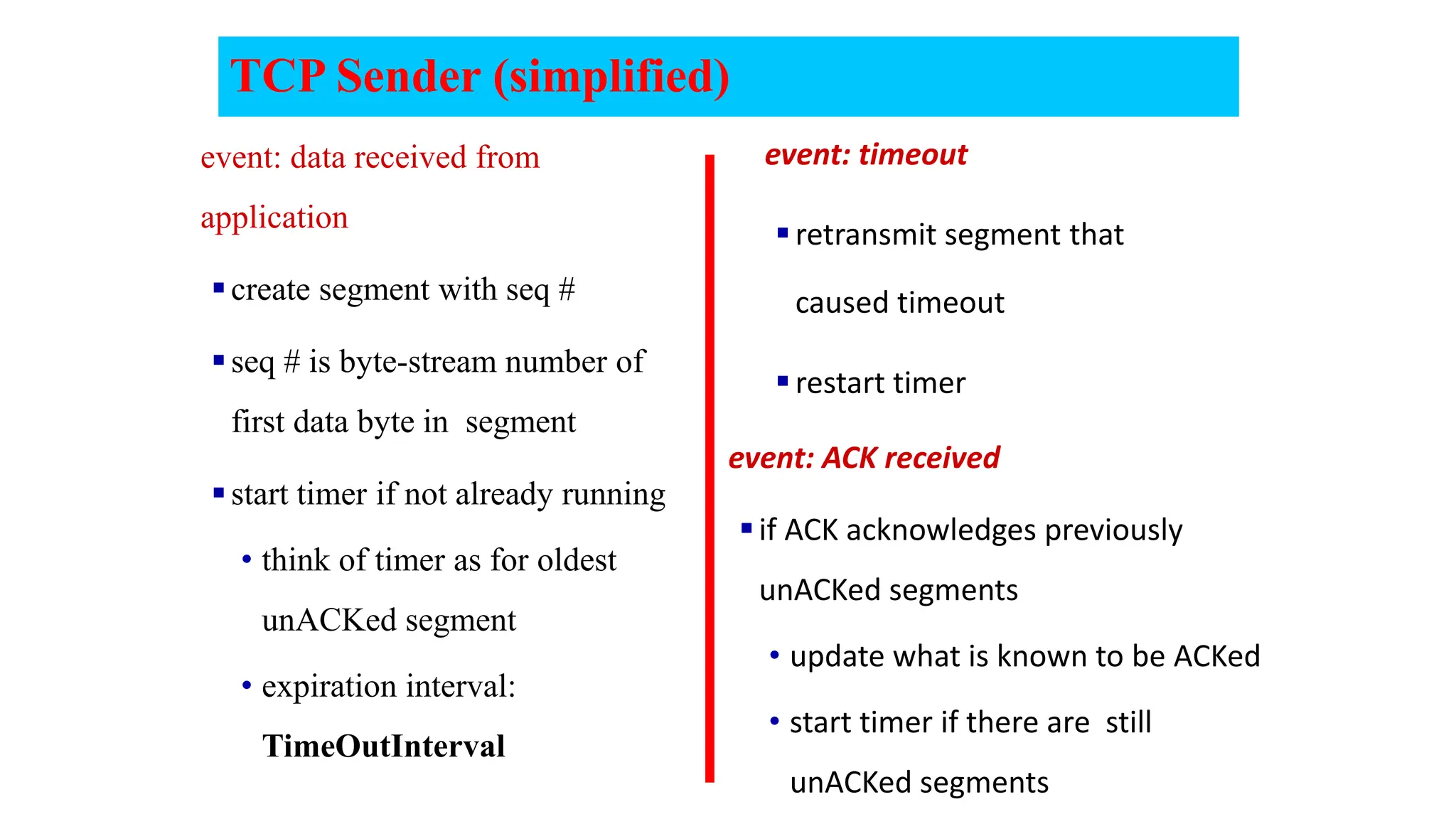
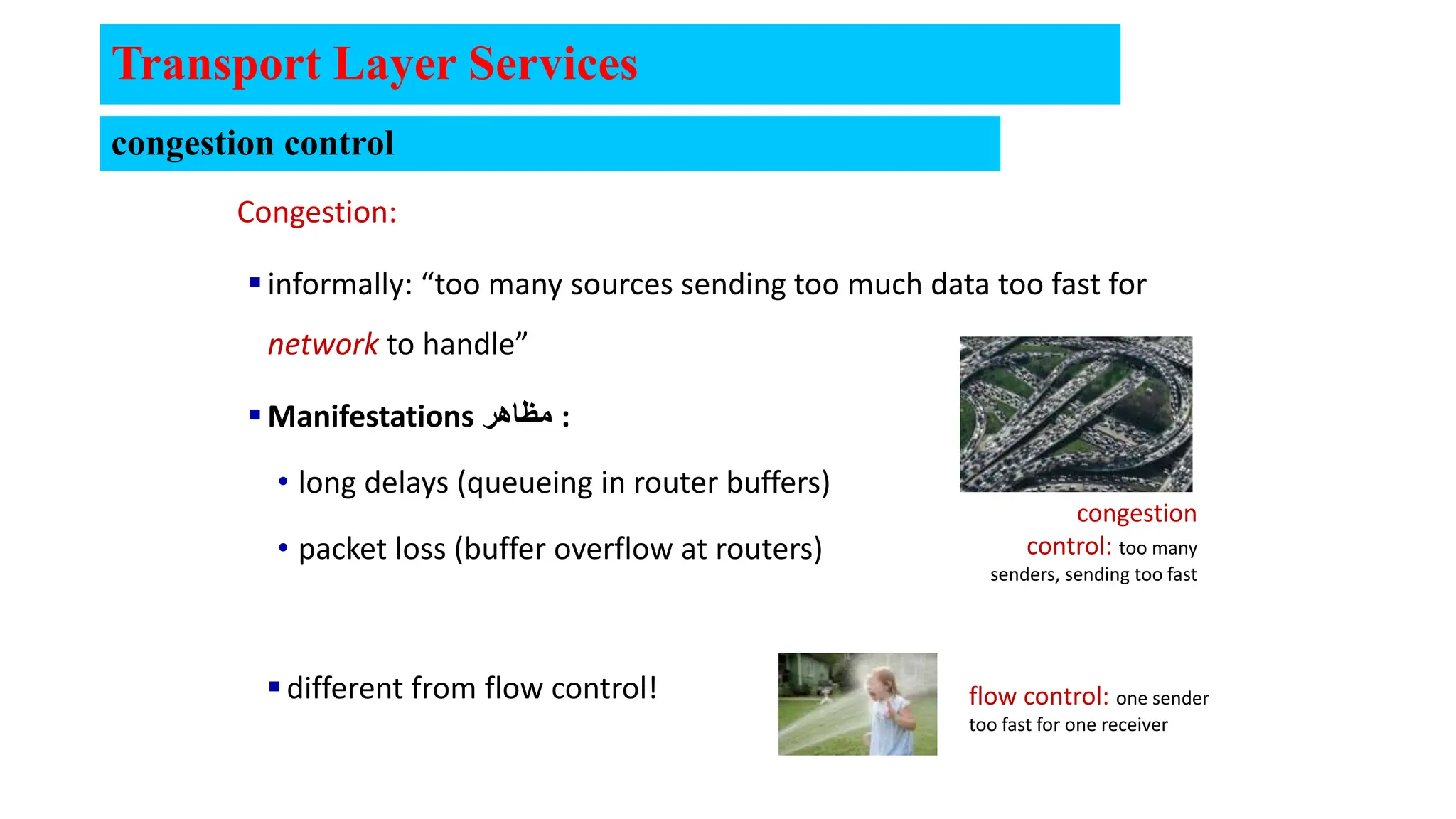
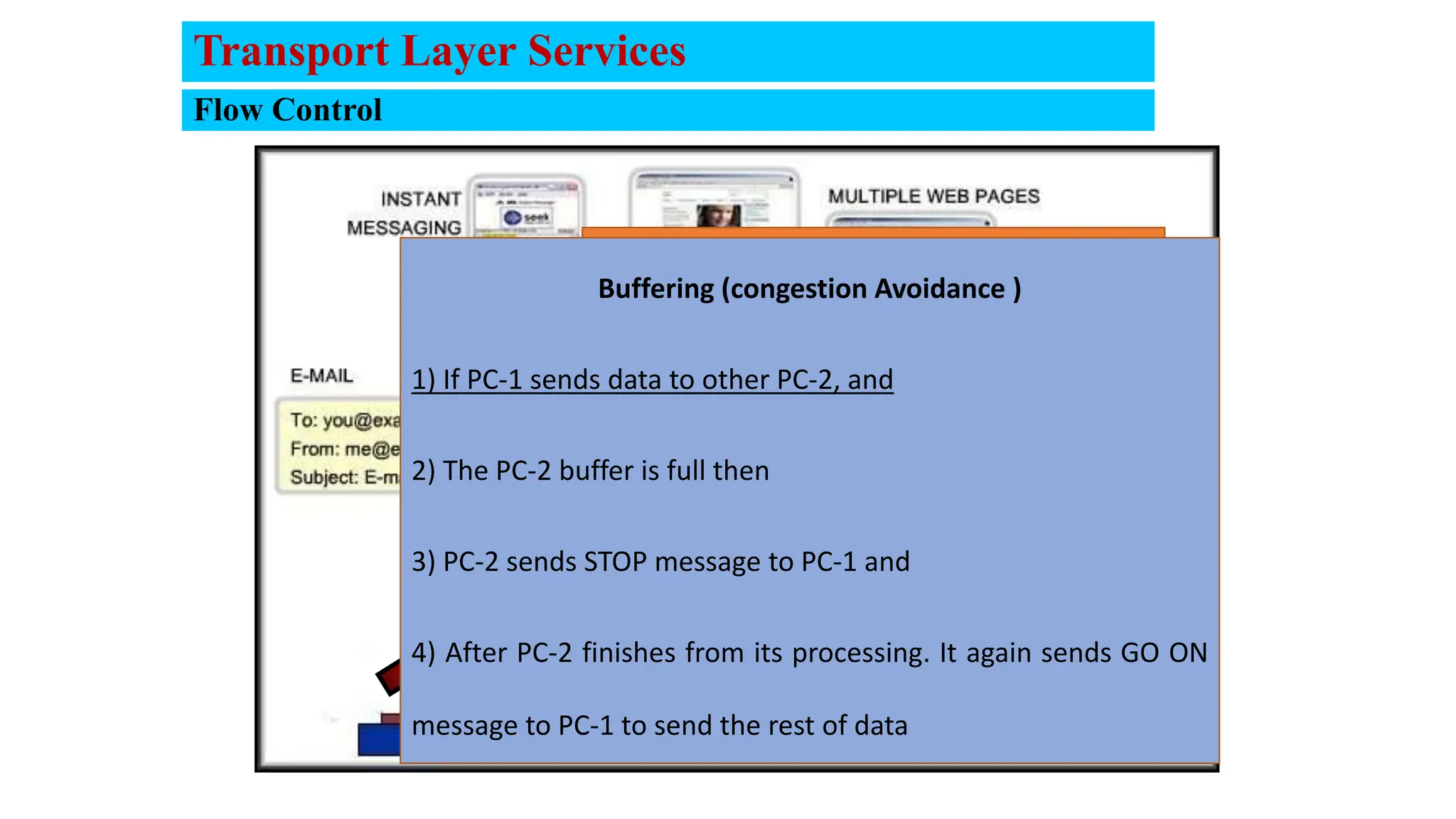
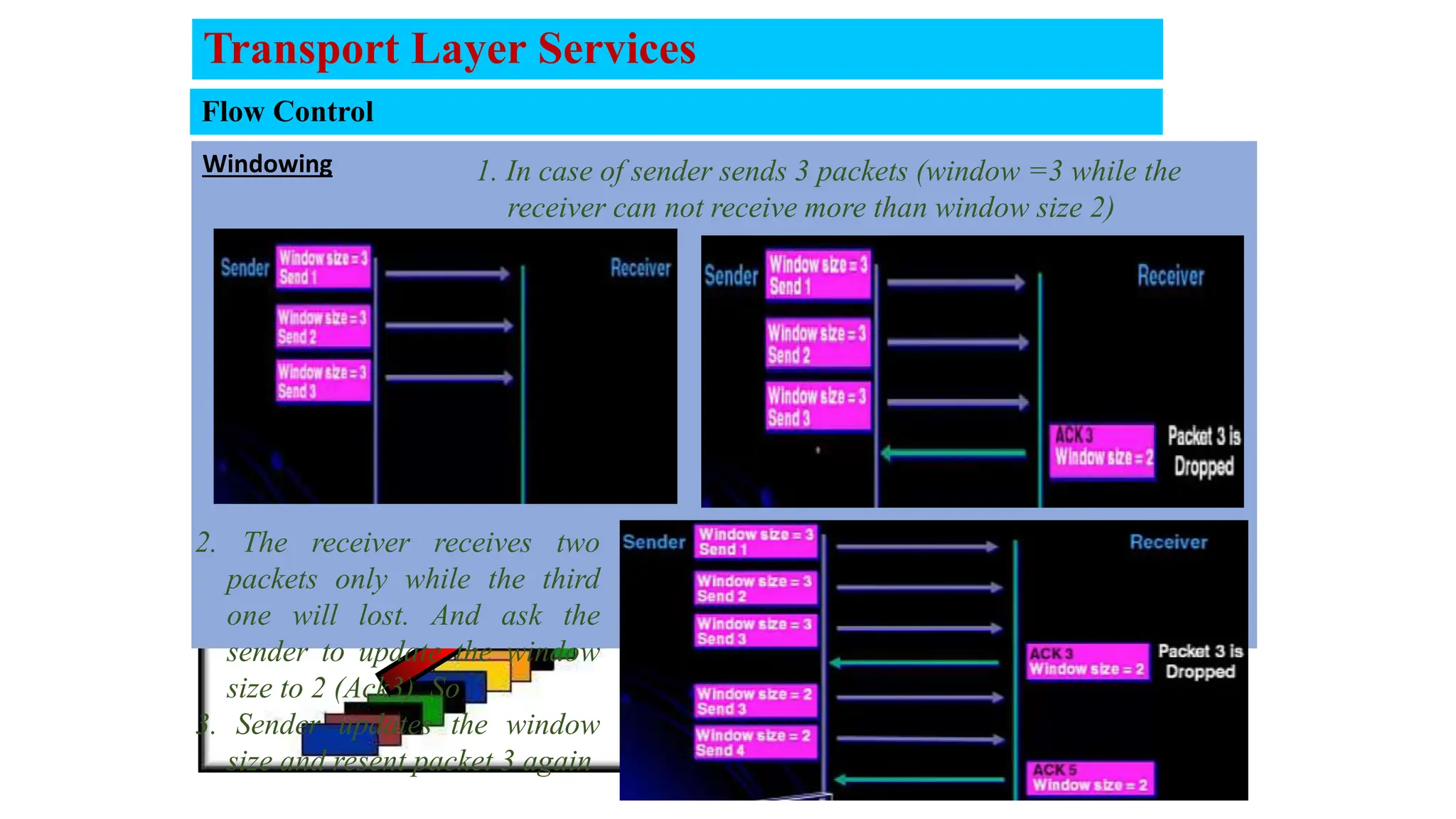
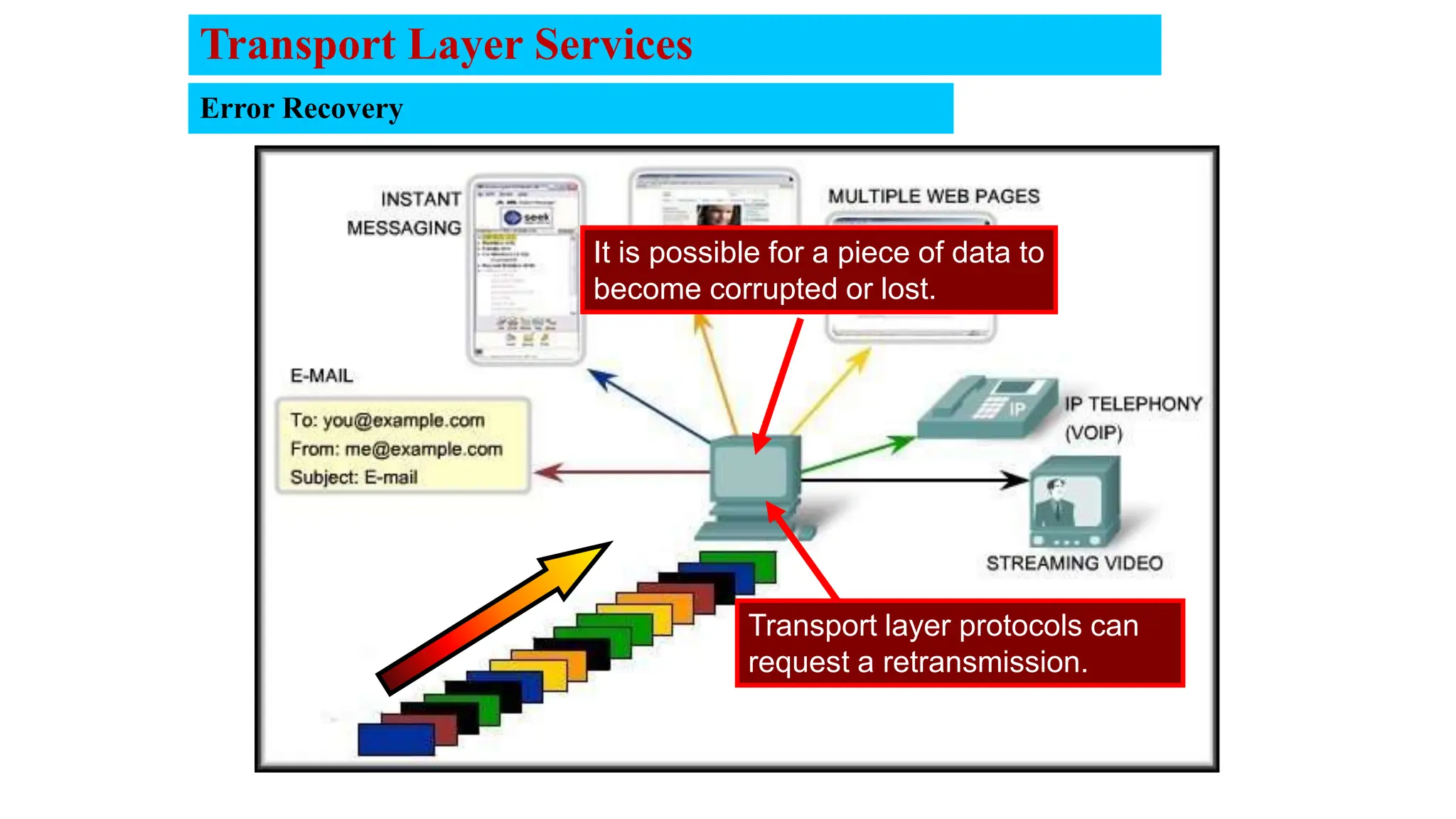
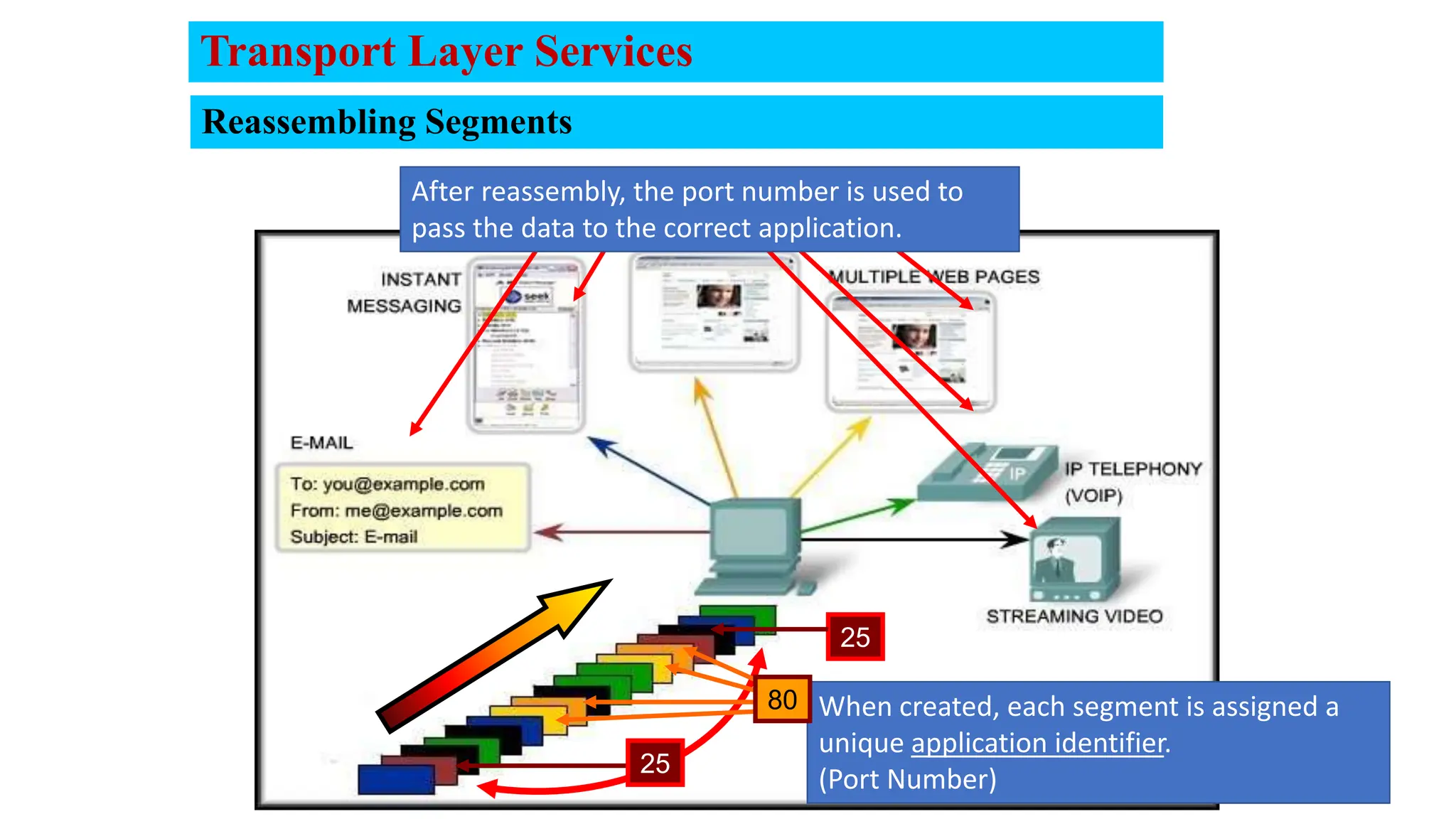
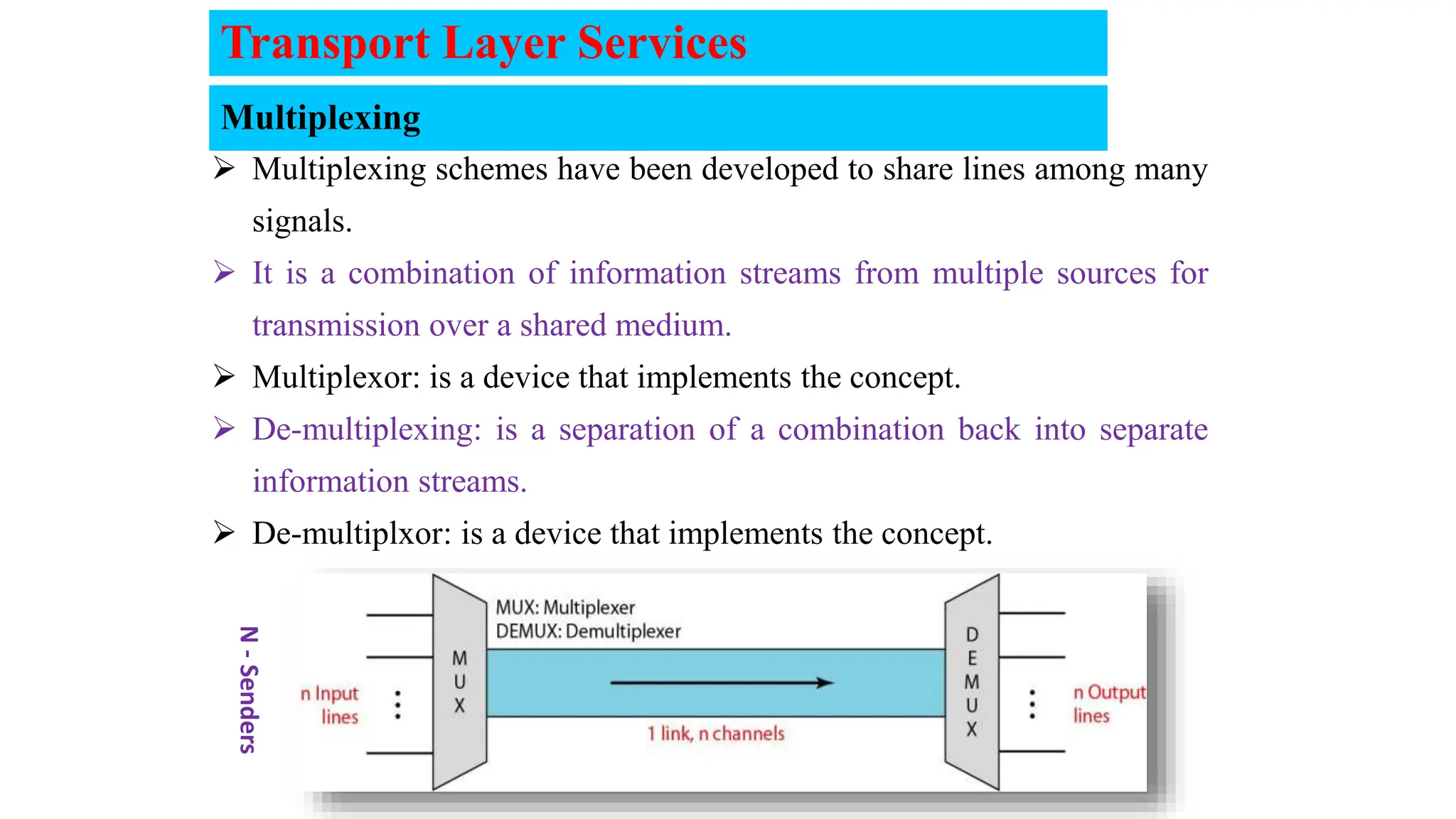
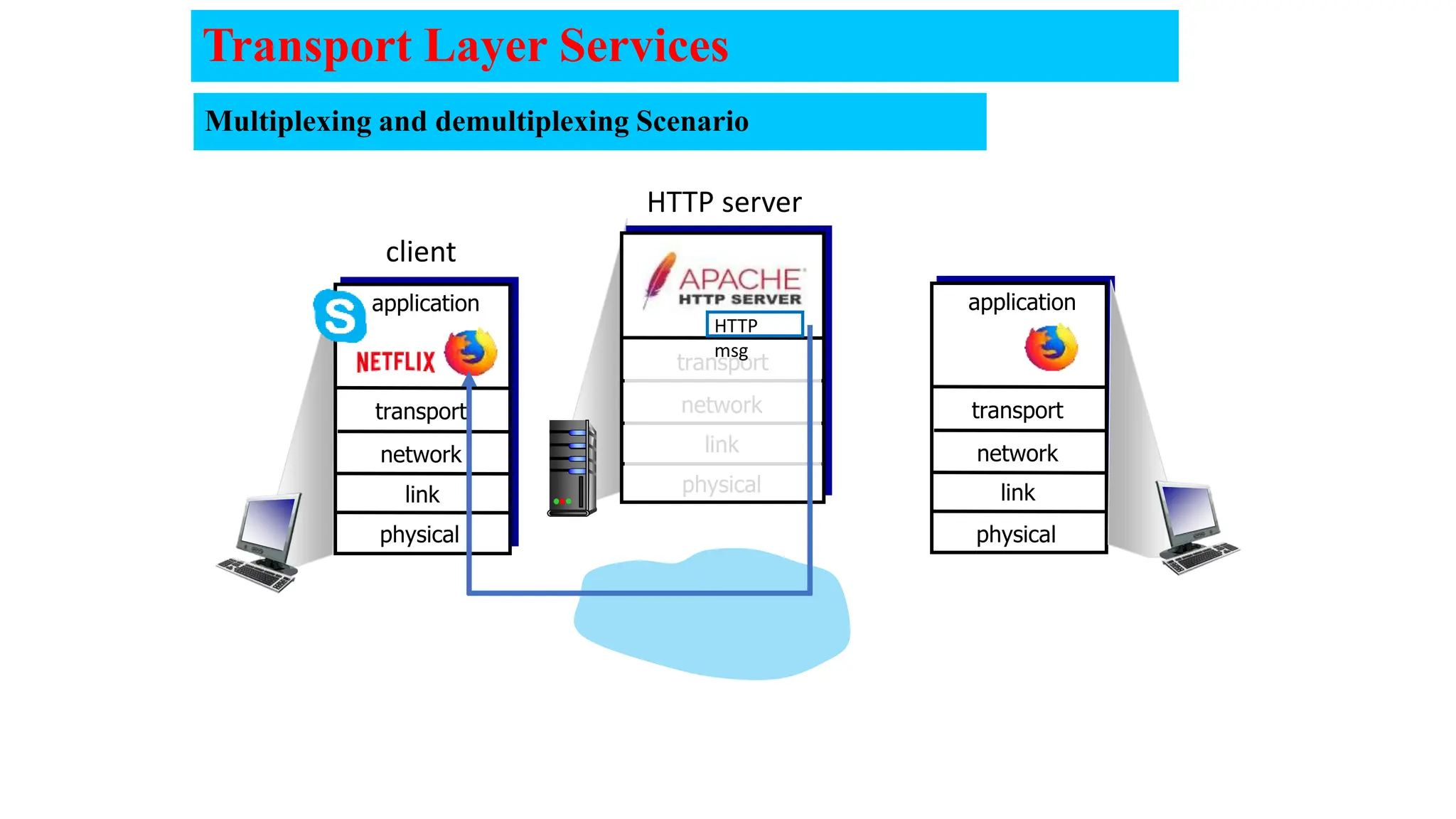
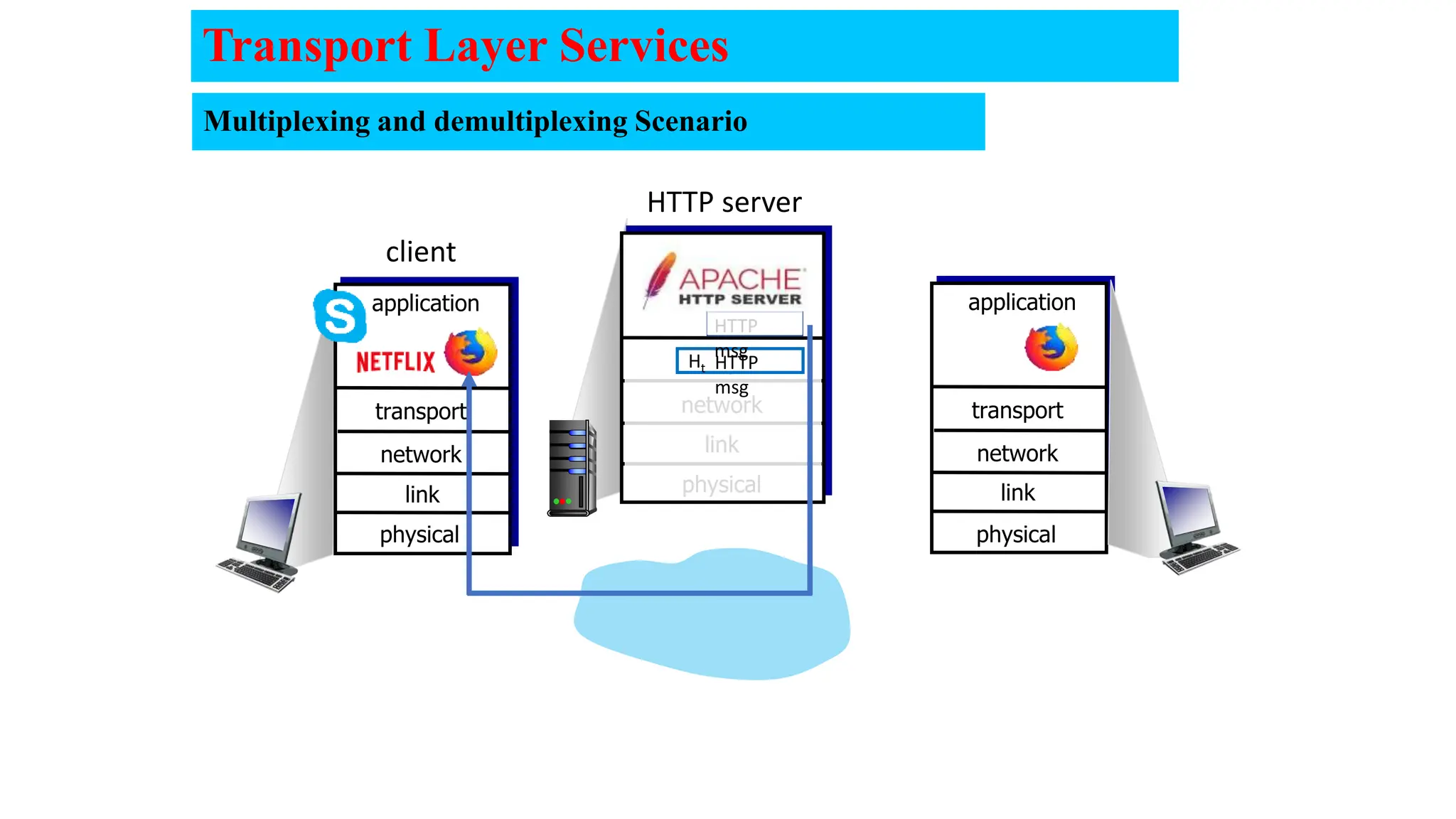
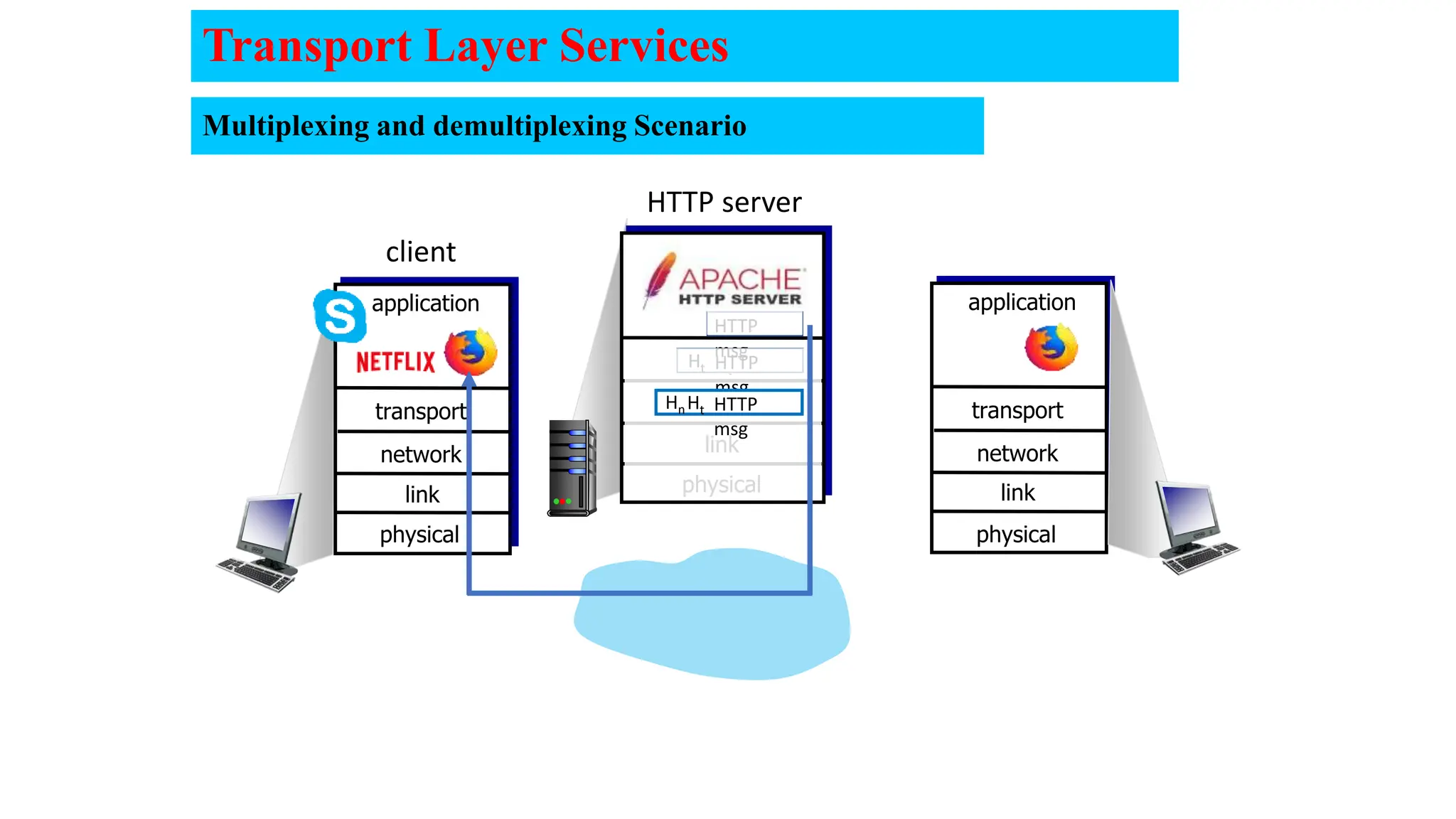
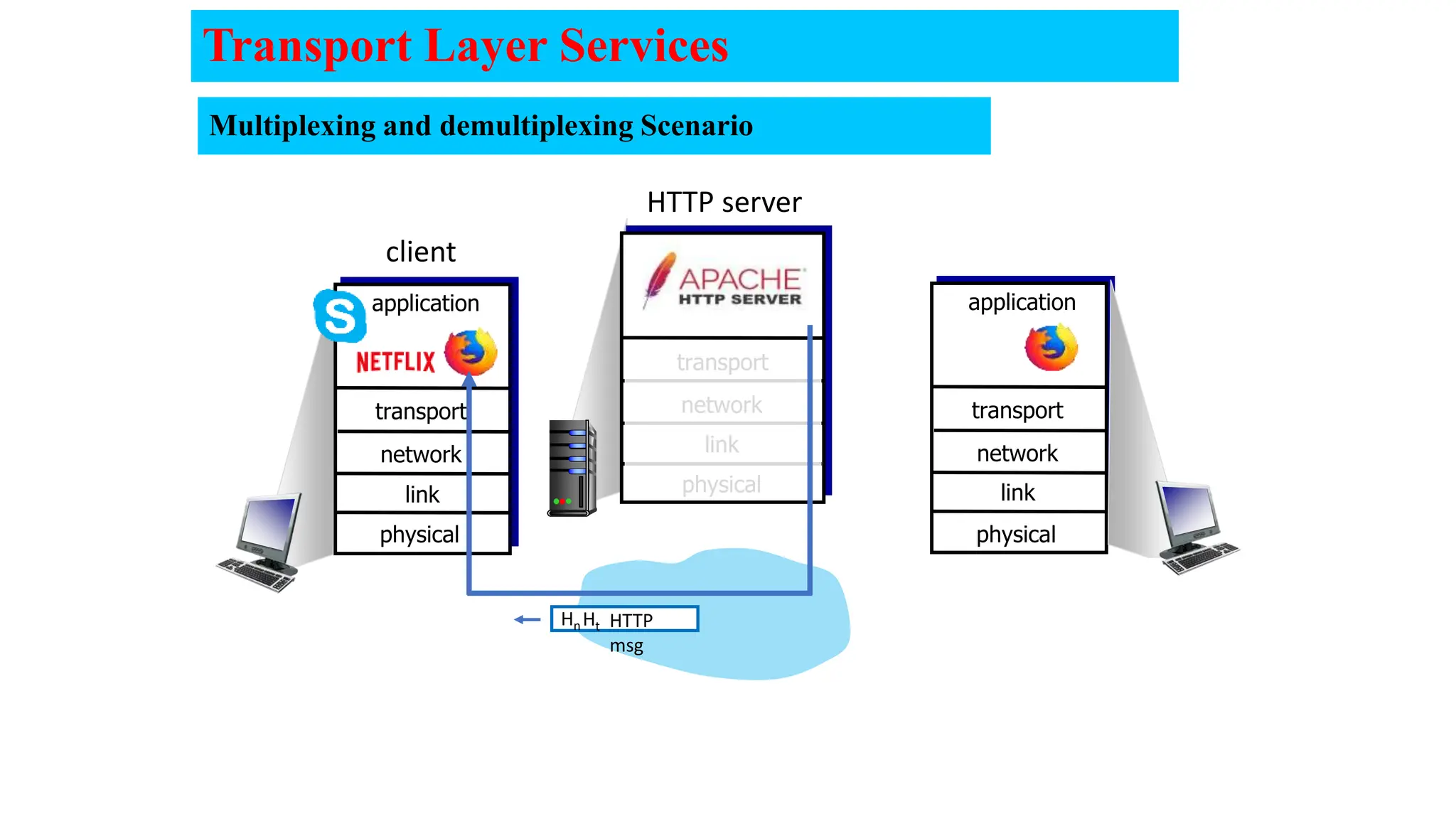
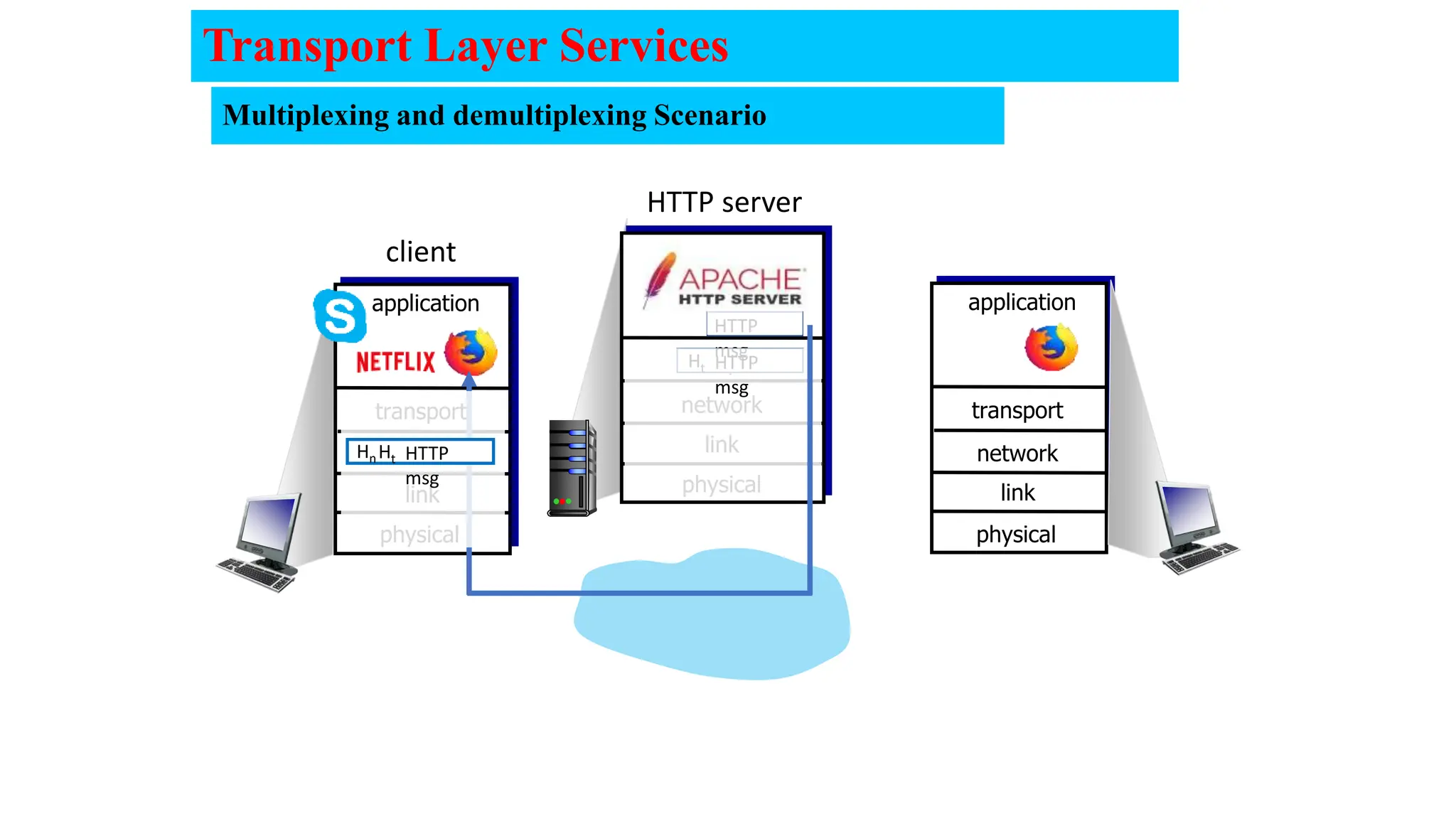
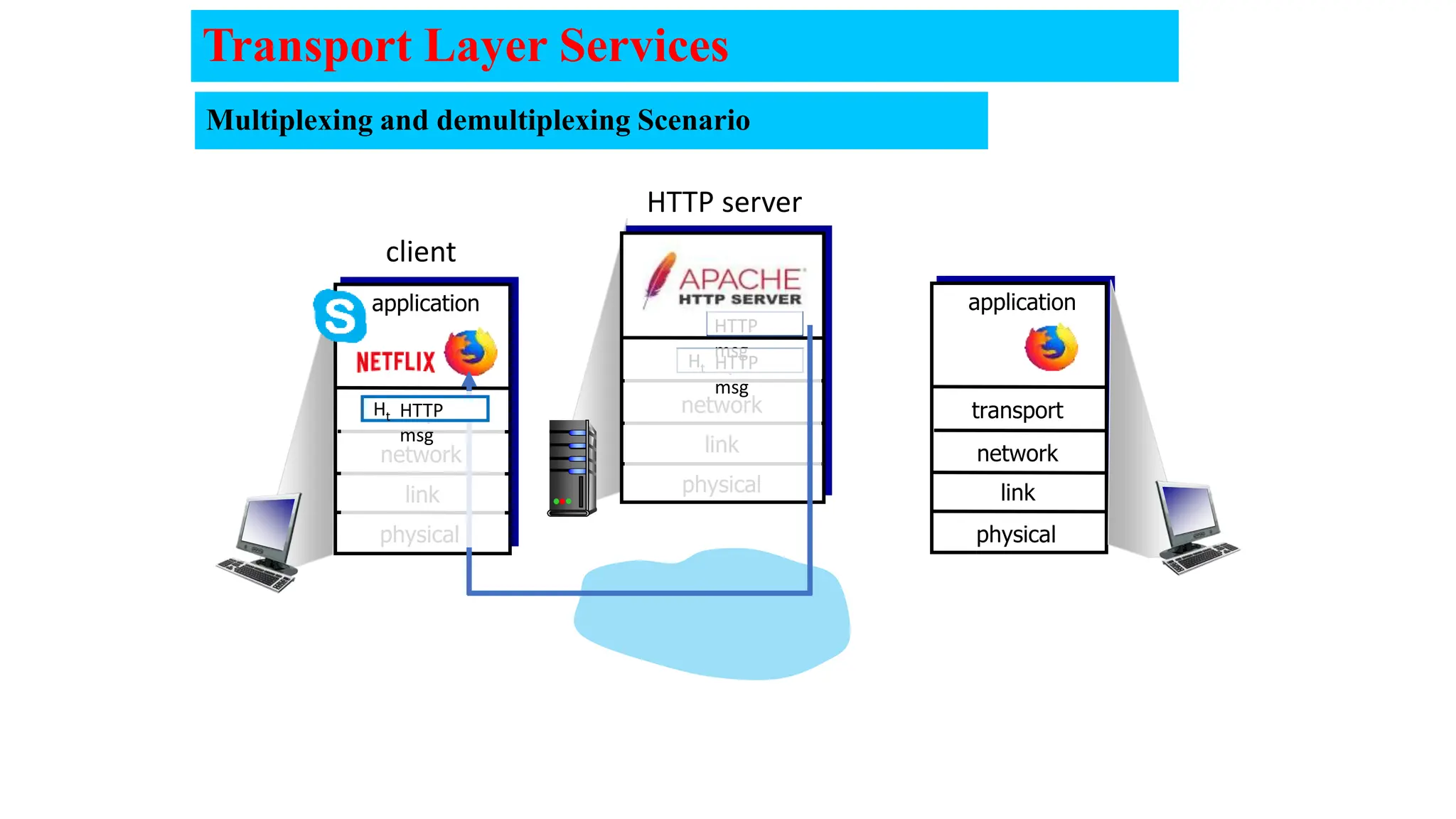
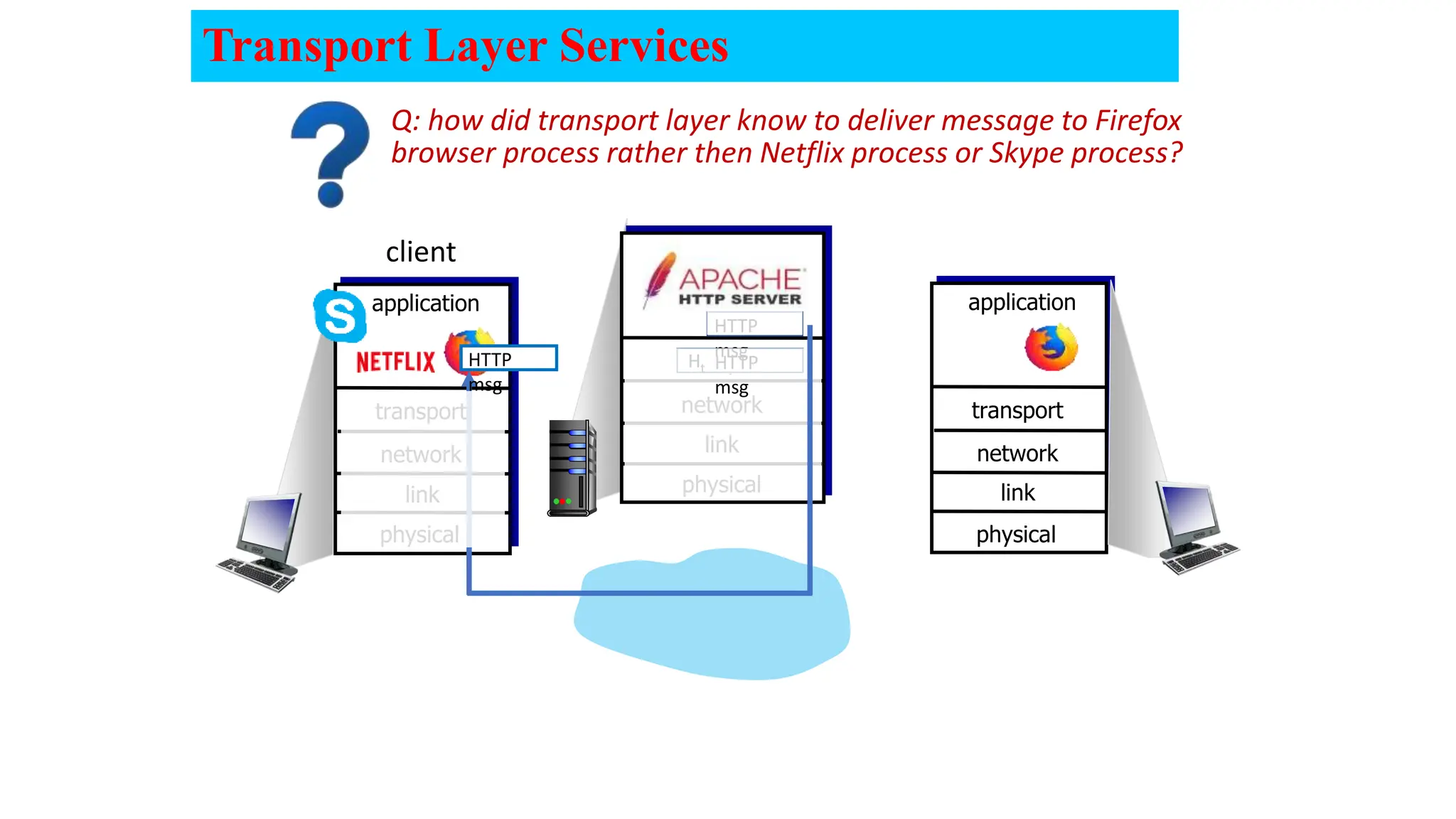
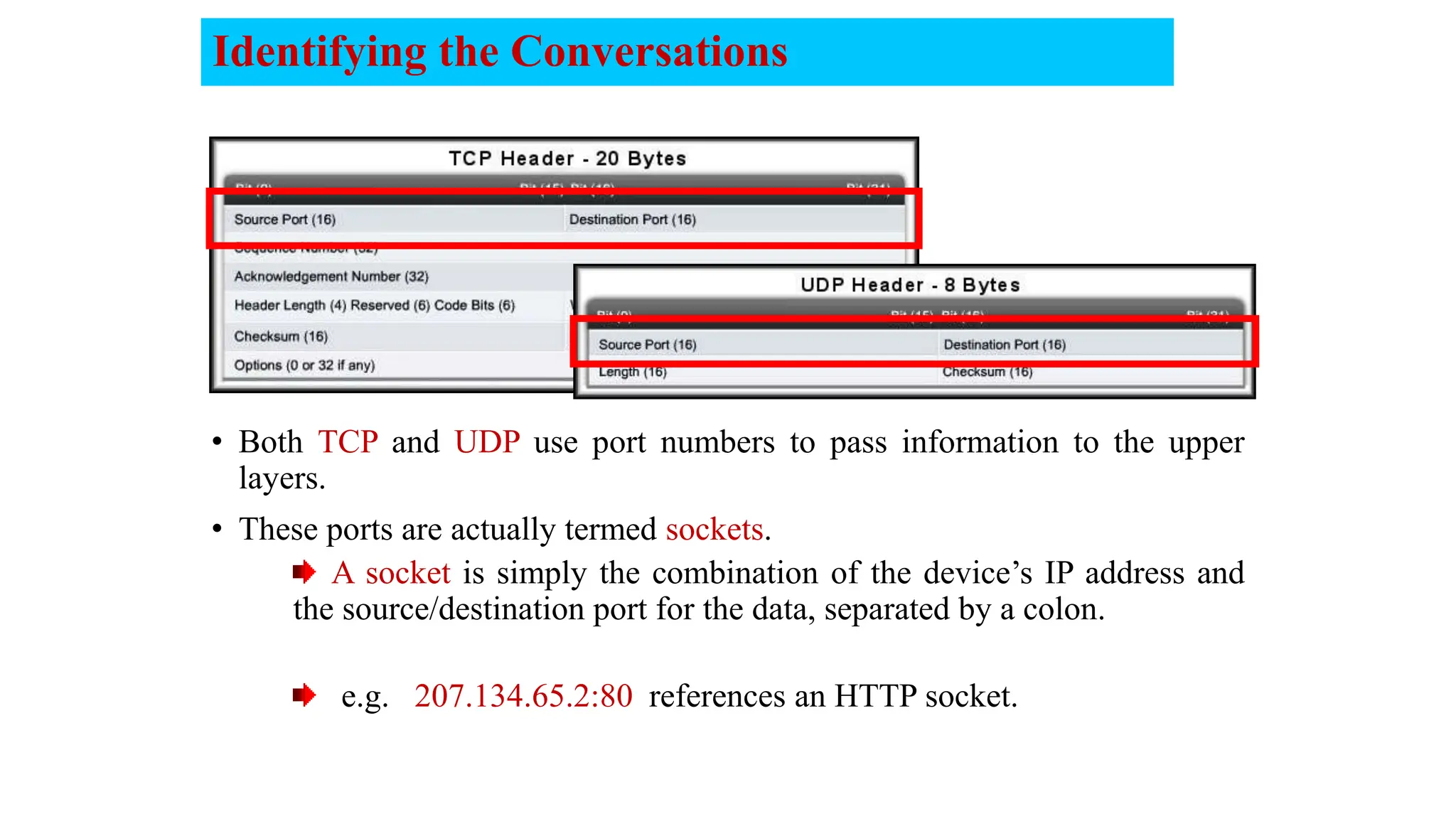
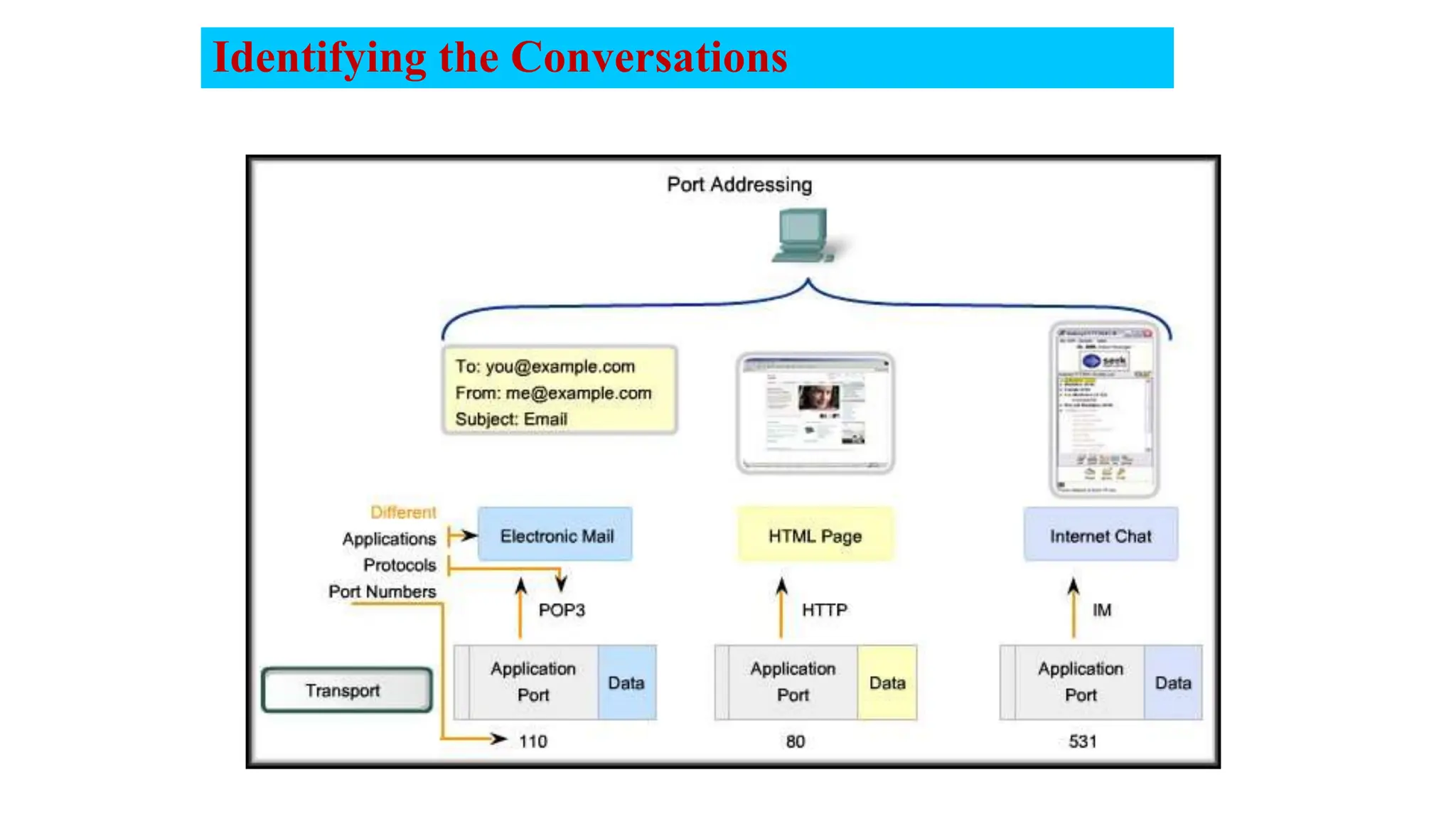
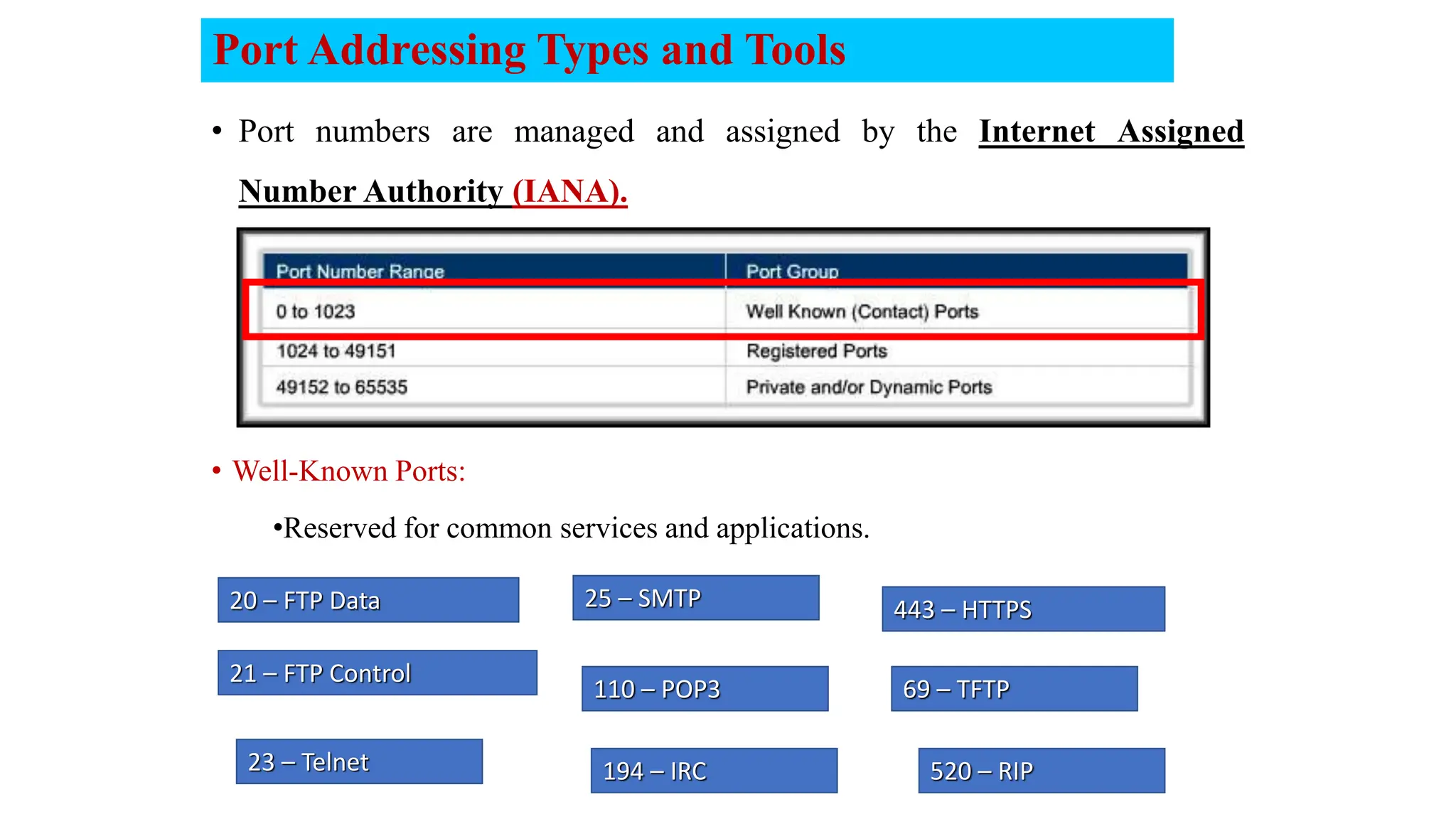
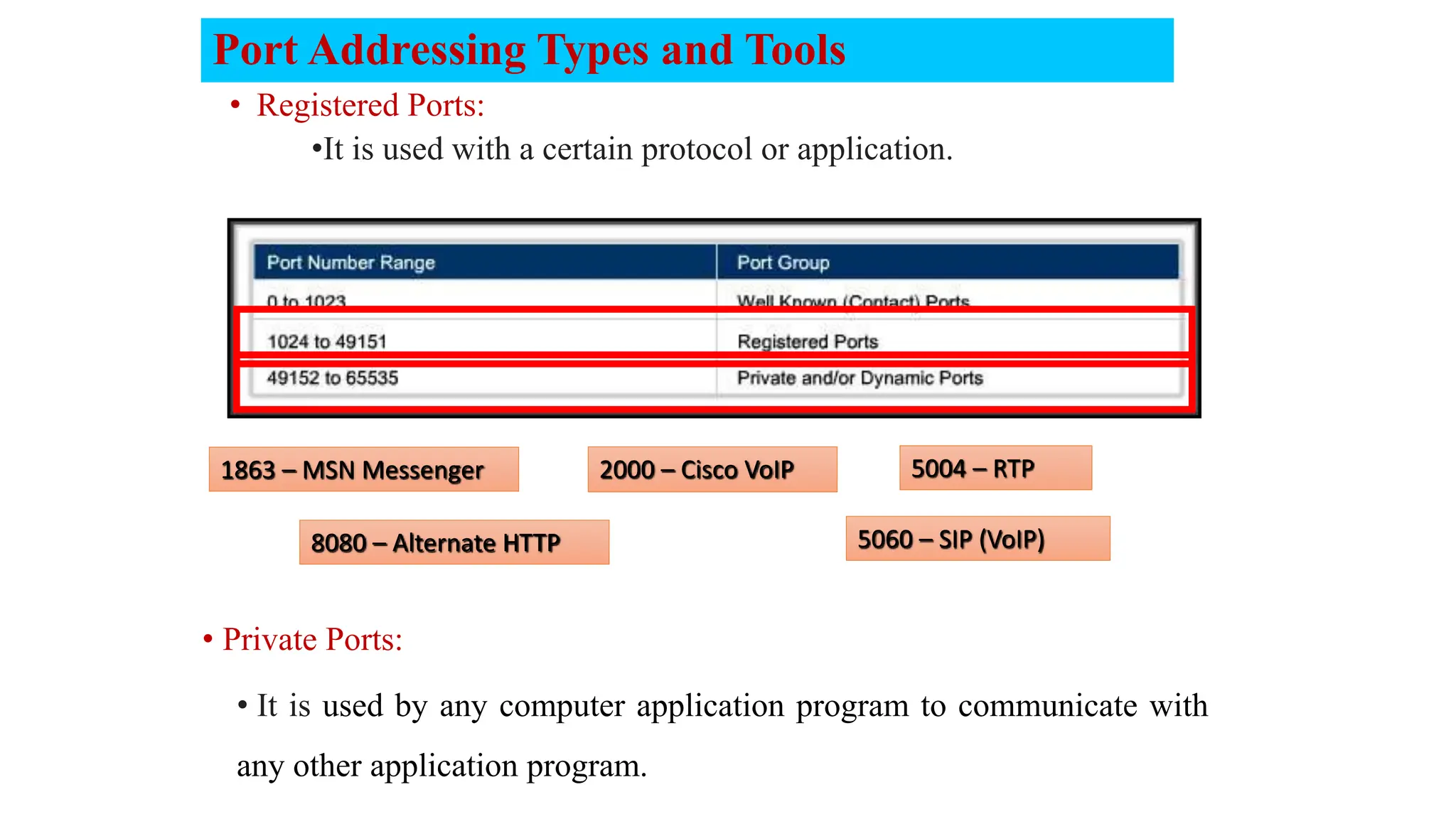
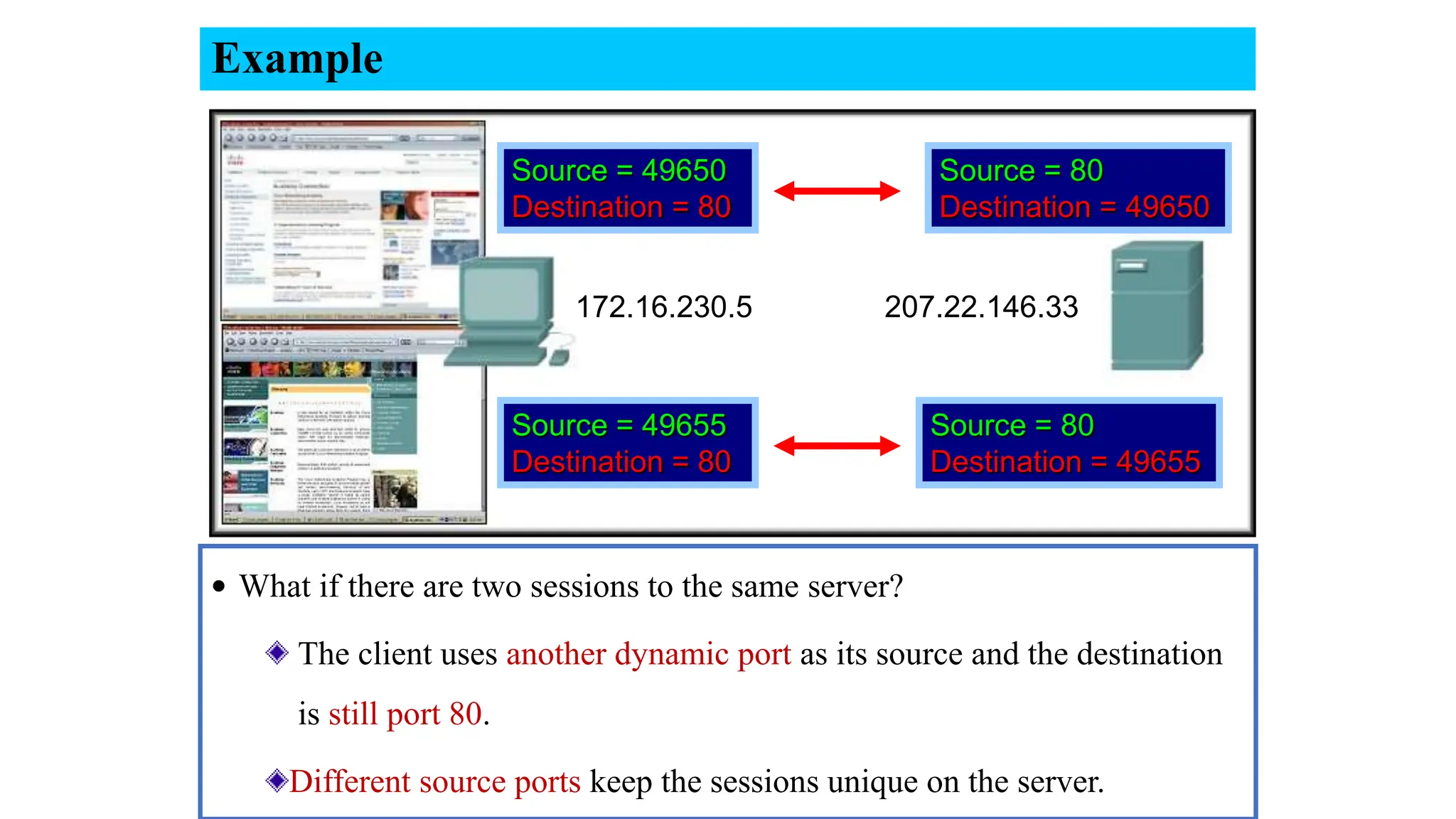
The document provides an in-depth overview of the transport layer in computer networks, focusing on protocols such as TCP and UDP, and their functionalities in data transmission. It details how data is segmented, the role of ports in demultiplexing, and mechanisms for error detection, flow control, and congestion control. Additionally, it describes the structural components of protocol headers and the process of reassembling messages at the receiver's end.