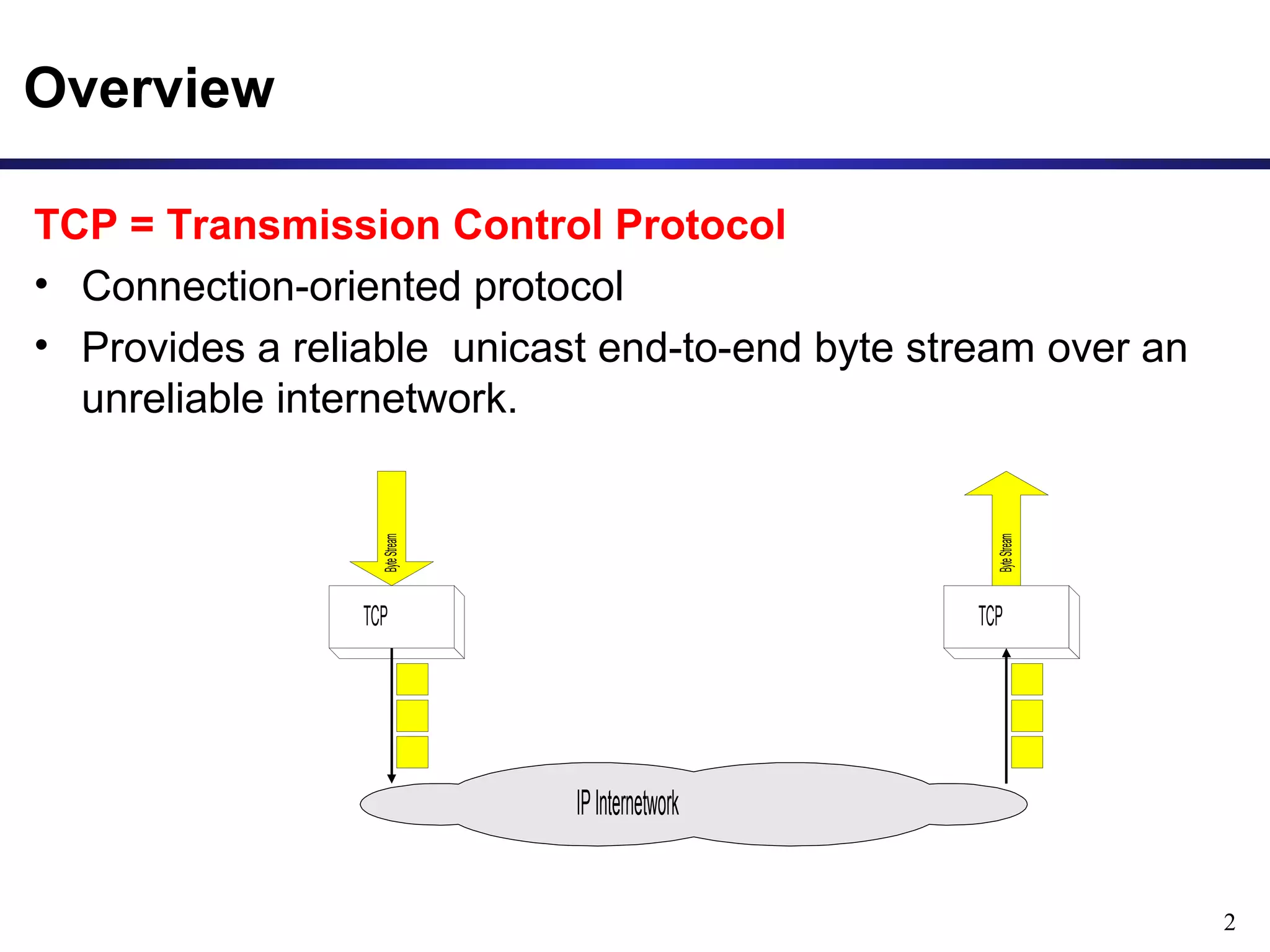
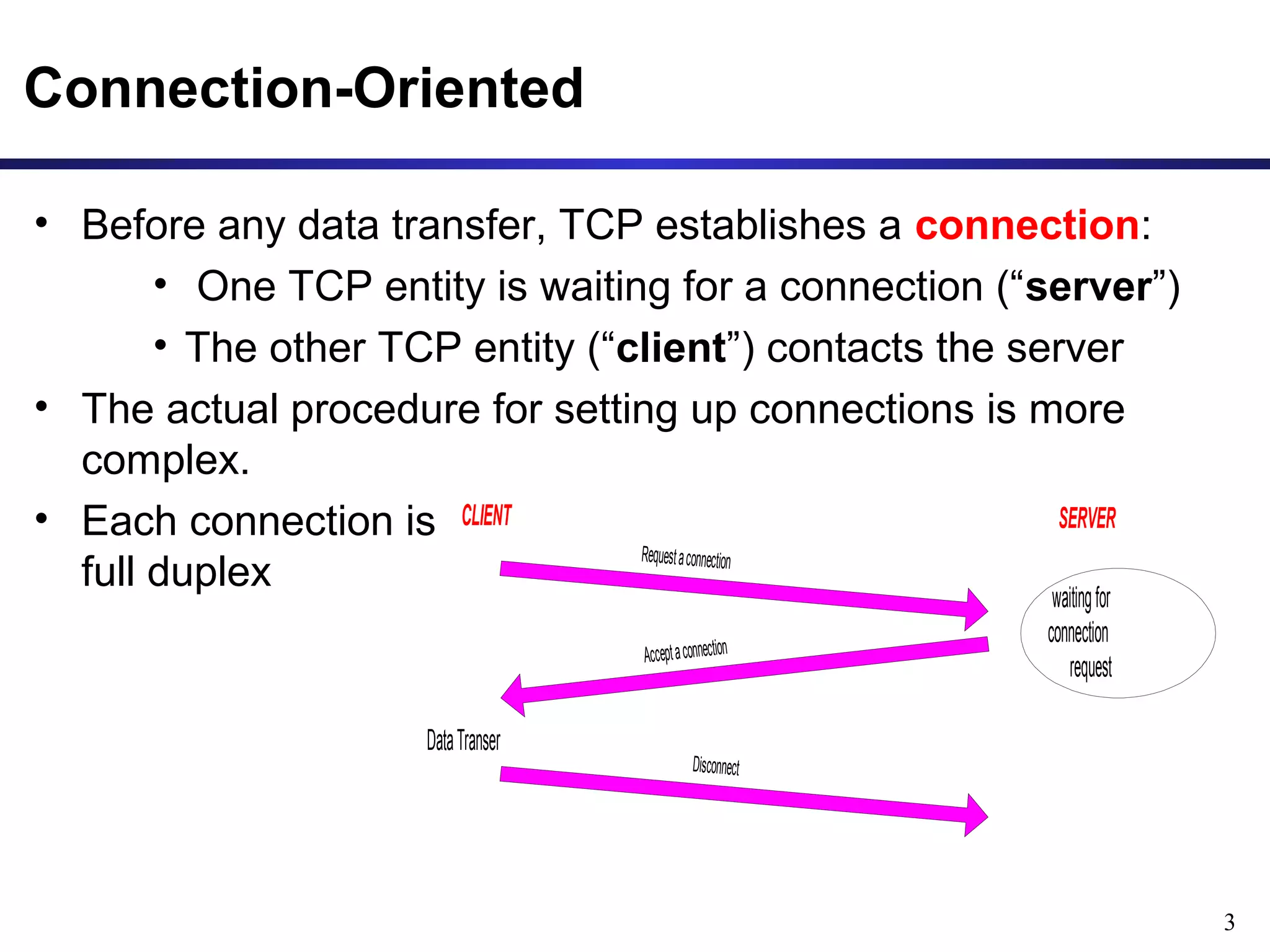
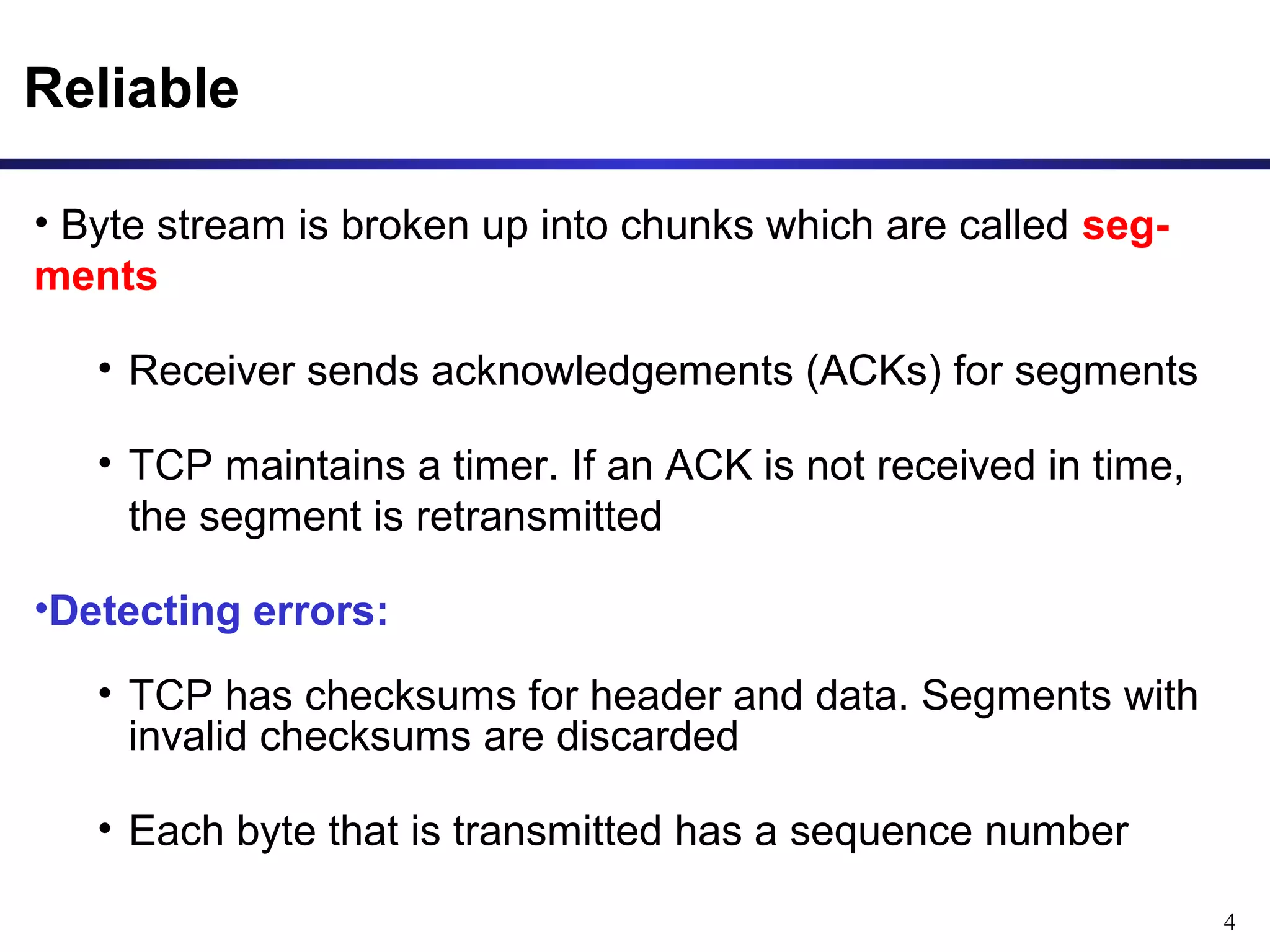
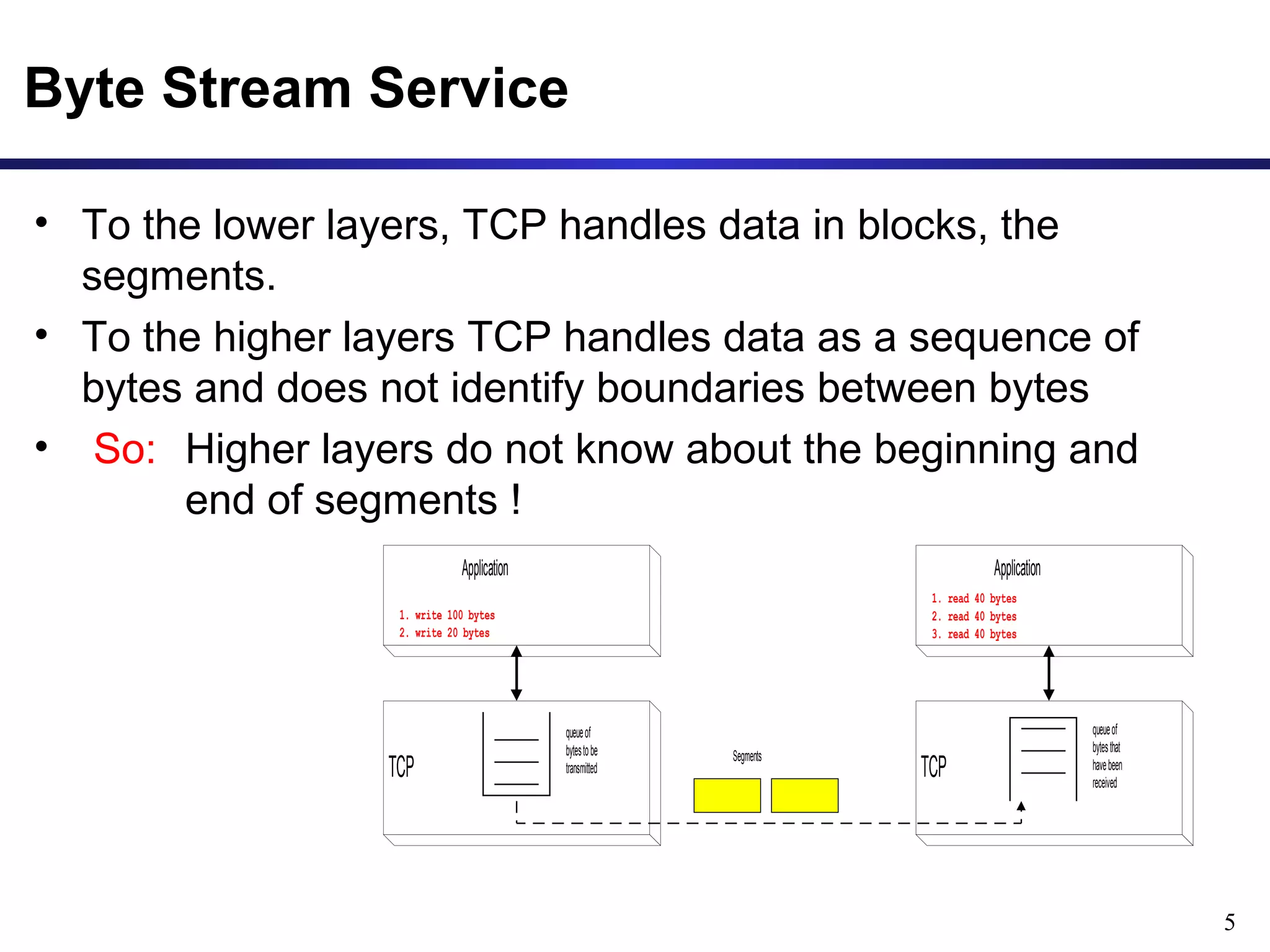
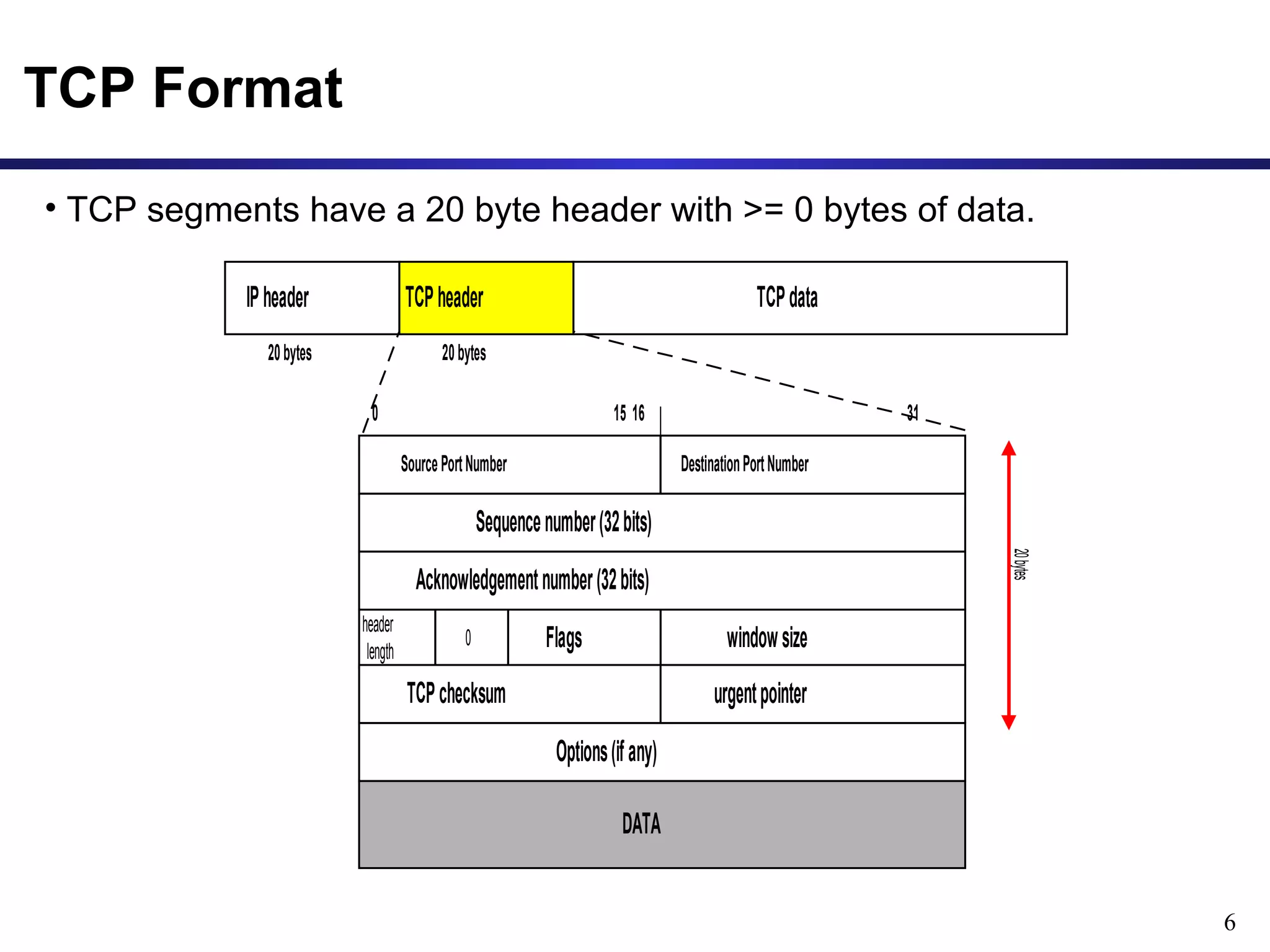
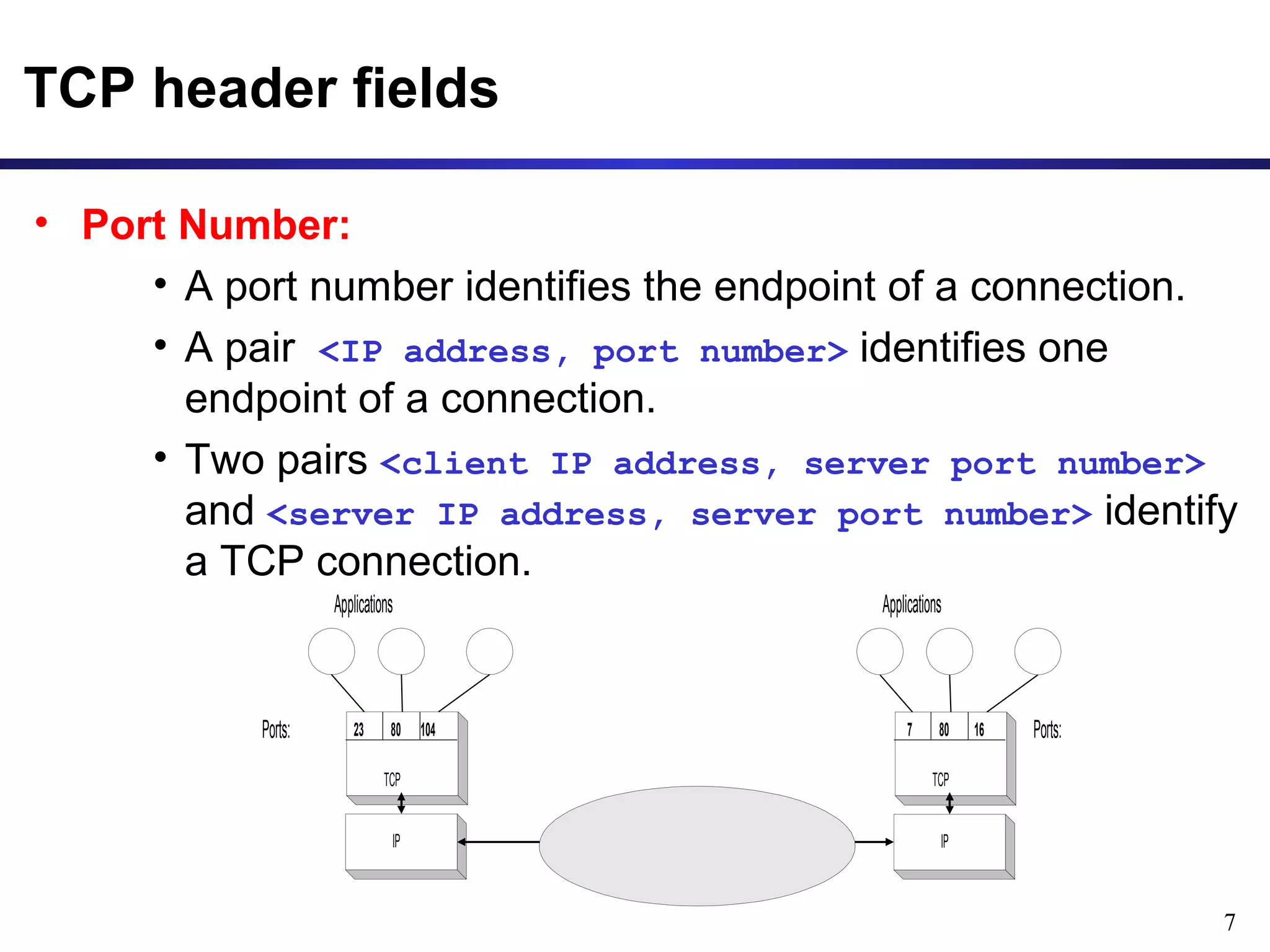
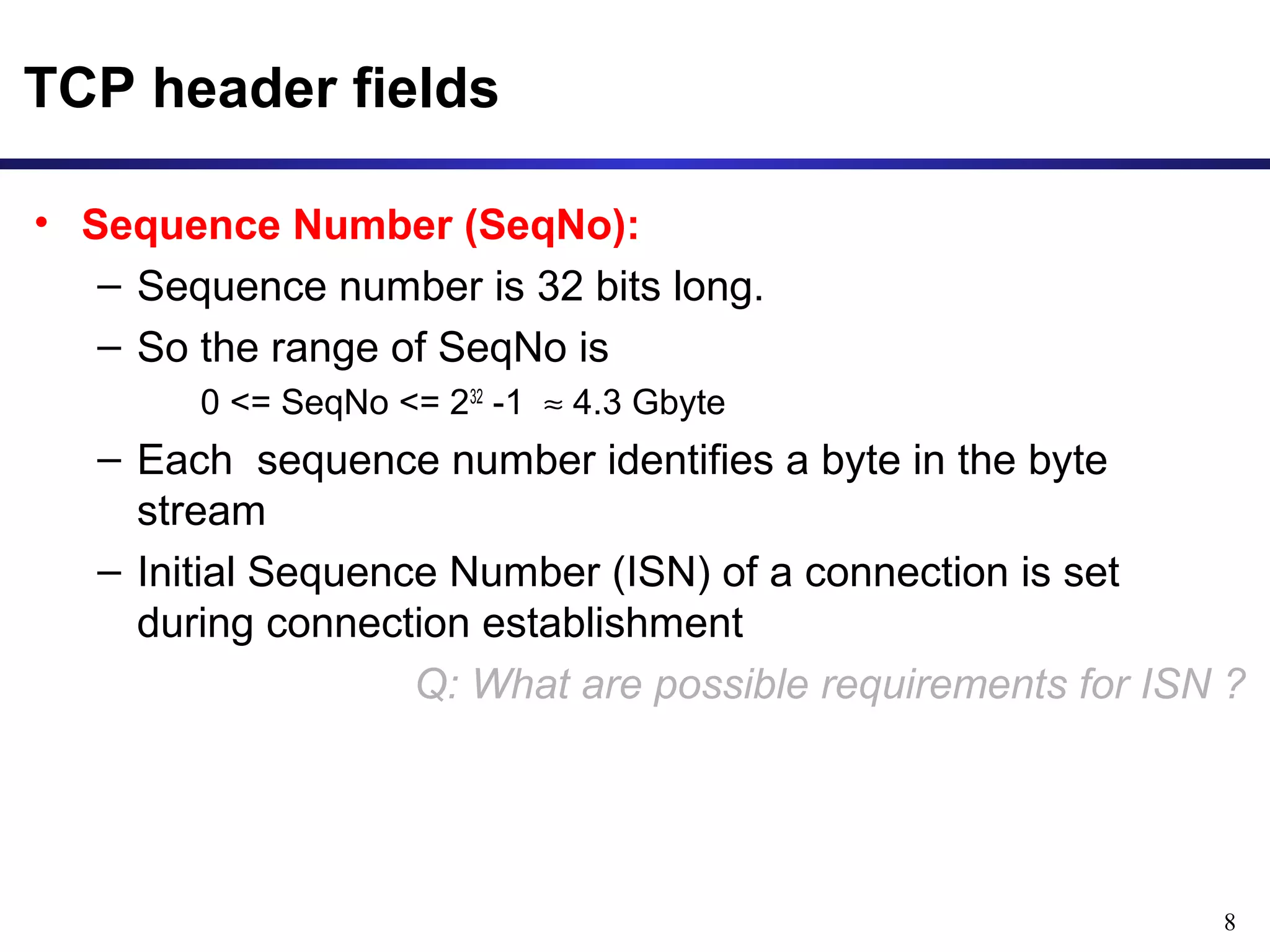
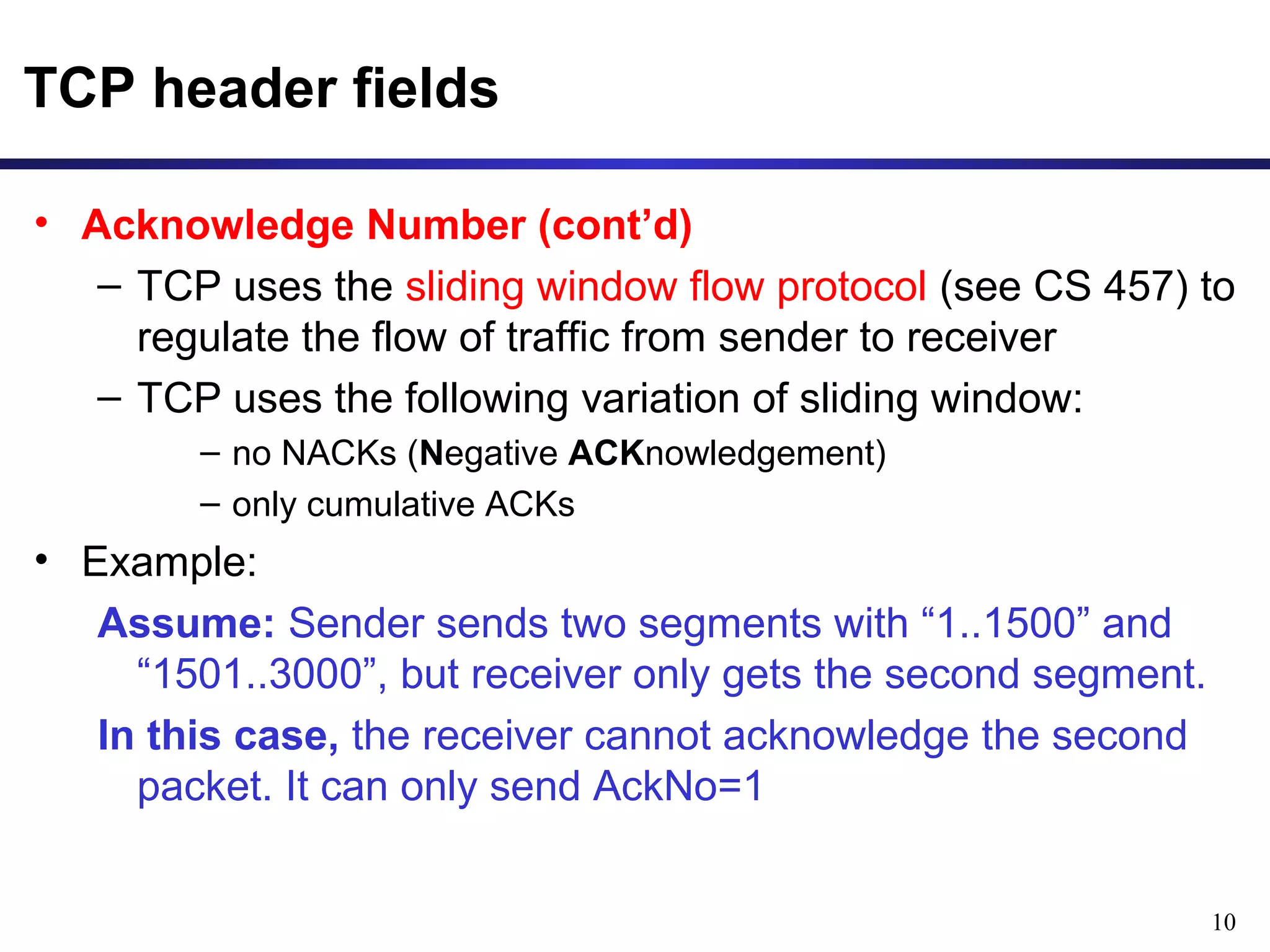
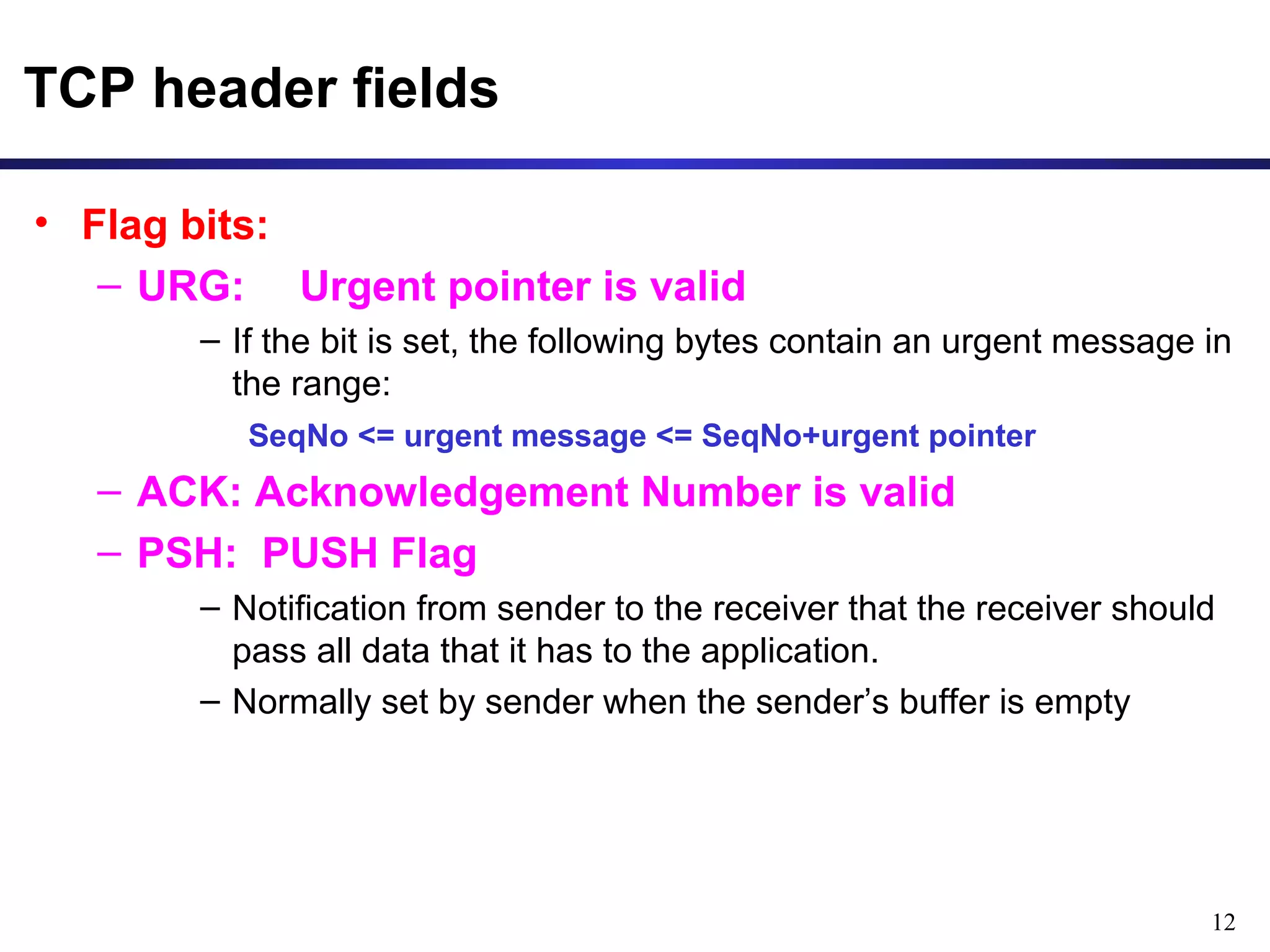
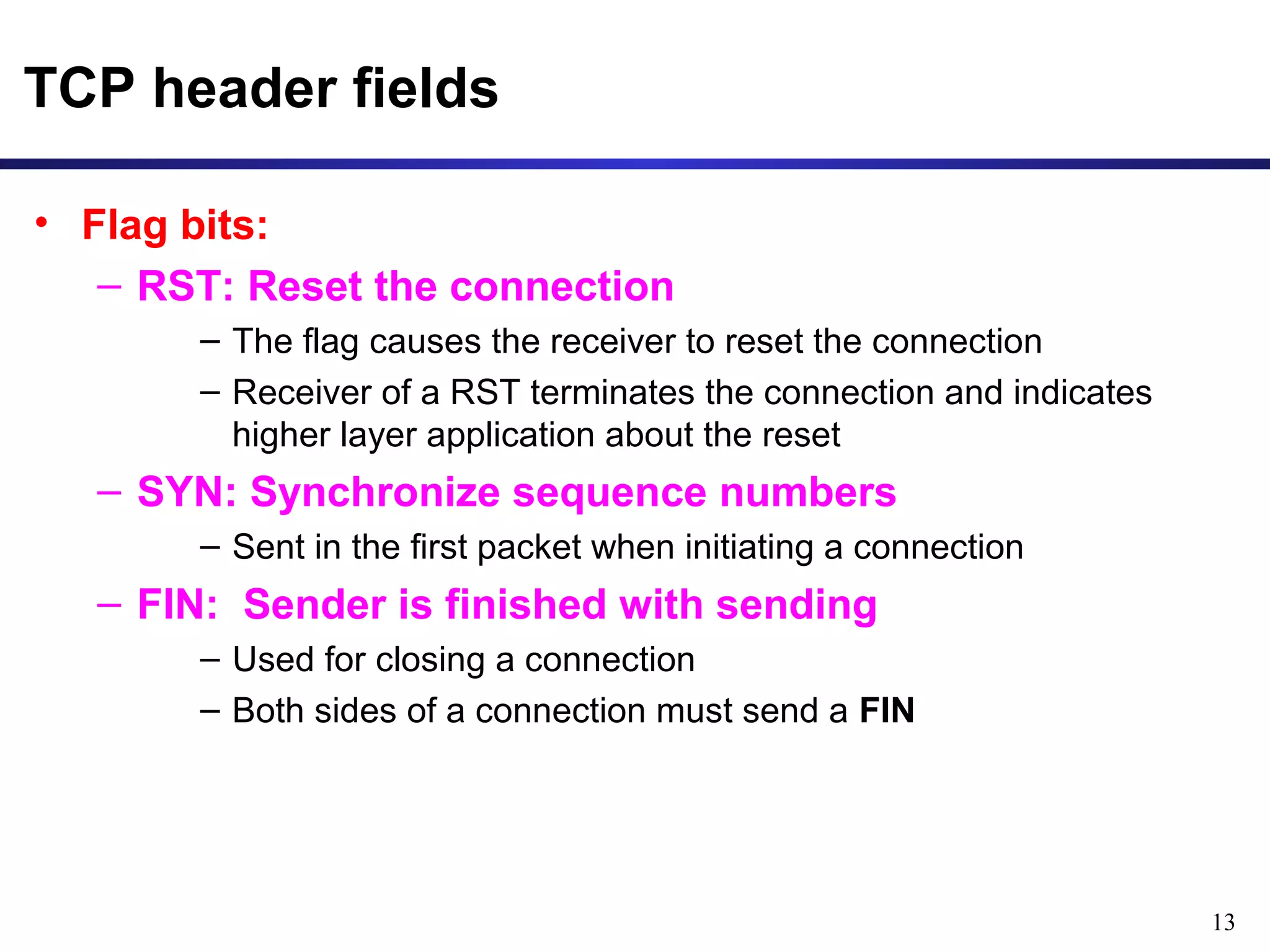
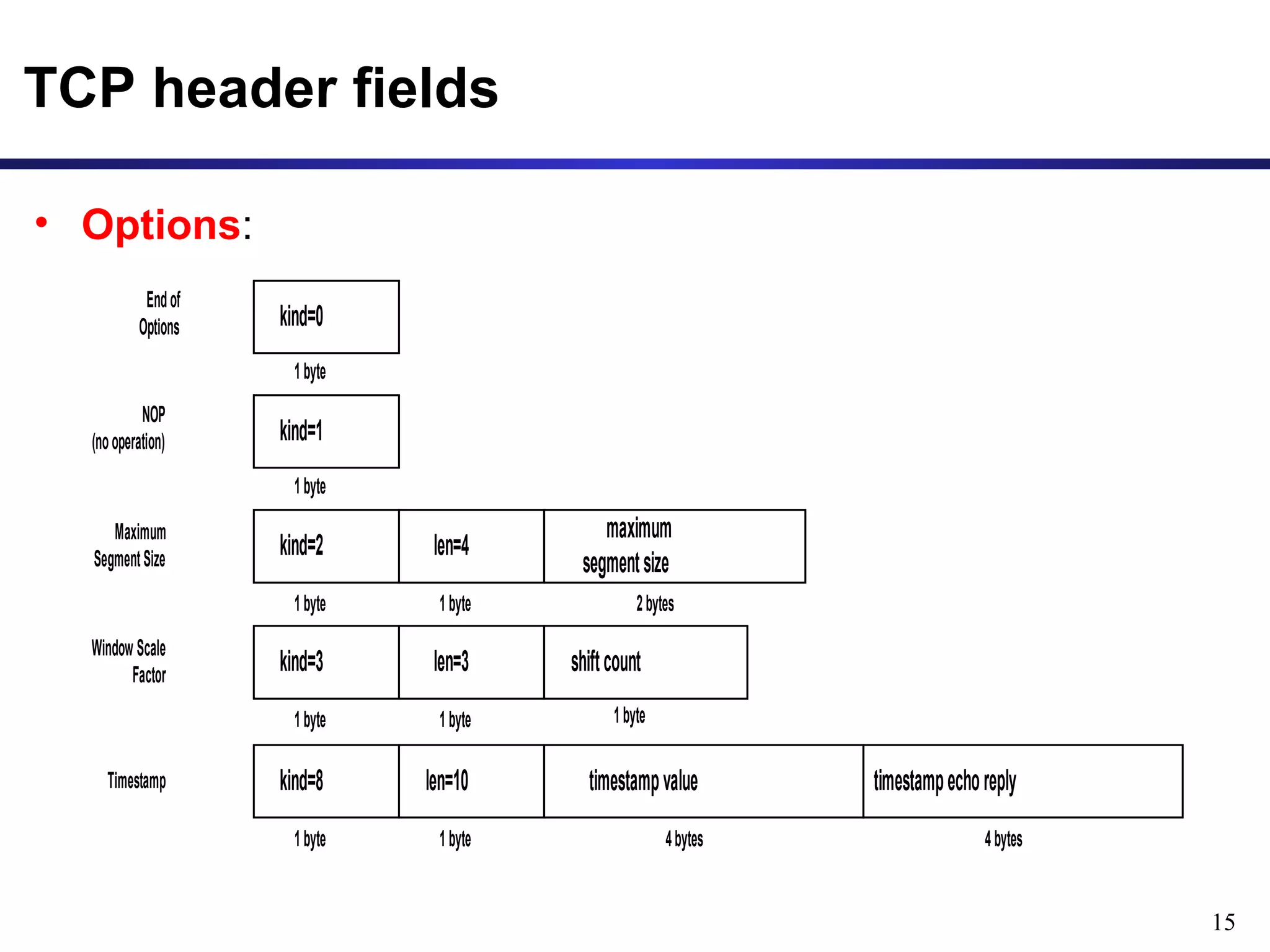
This document provides an overview of the Transmission Control Protocol (TCP). TCP is a connection-oriented protocol that provides reliable data transmission over the internet by establishing connections between clients and servers, using acknowledgements and retransmissions to ensure reliable delivery of data. It handles data as a byte stream for applications but transmits data in segments over IP networks. The TCP header contains fields like port numbers, sequence numbers, acknowledgement numbers, flags, checksum, and options to support its functions.