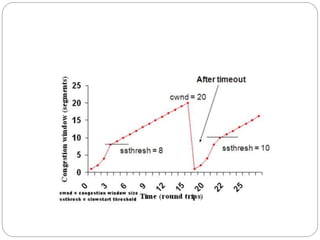
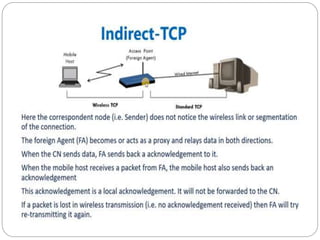
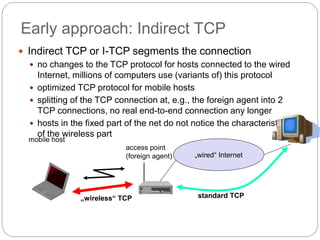
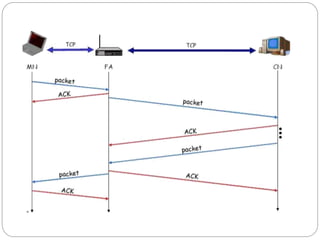
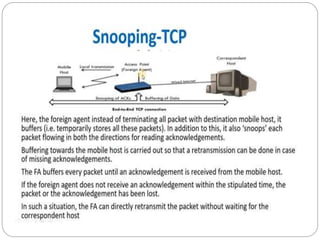
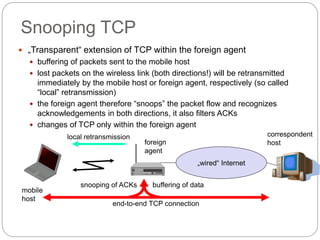
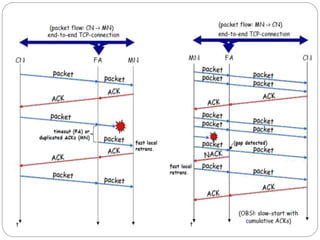
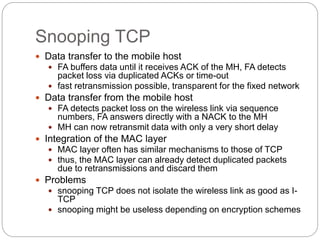
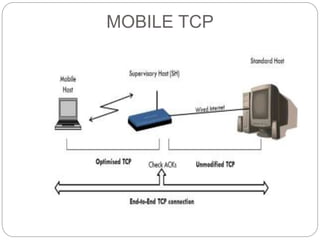
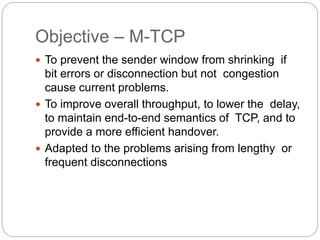
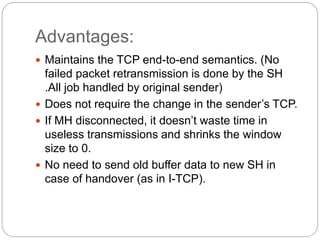
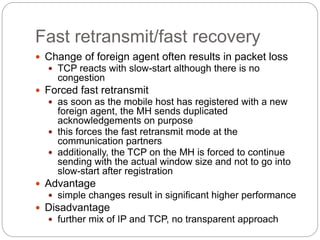
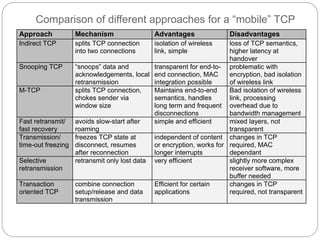
This document discusses various approaches to improving TCP performance over mobile networks. It describes Indirect TCP, Snooping TCP, Mobile TCP, optimizations like fast retransmit/recovery and transmission freezing, and transaction-oriented TCP. Each approach is summarized in terms of its key mechanisms, advantages, and disadvantages. Overall, the document evaluates different ways TCP has been adapted to better support mobility and address challenges like frequent disconnections, packet losses during handovers, and high bit error rates over wireless links.