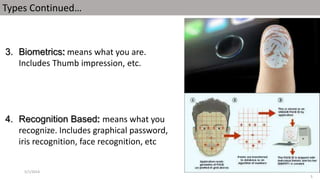
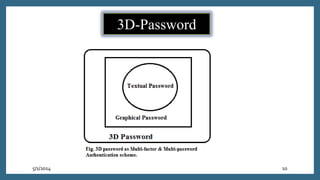
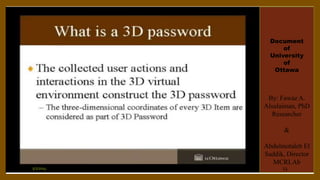
The document discusses a proposed 3D password authentication scheme. It begins with an introduction to common authentication techniques and their drawbacks. It then describes the concept of a 3D virtual environment for creating multi-factor passwords combining recall and recognition. The document outlines the objective to develop a more secure and user-friendly authentication system. It further explains the 3D password scheme, potential attacks and countermeasures, applications, advantages and disadvantages, and future scope.


















![[1].Fawaz A. Alsulaiman and Abdulmotaleb El Saddik, “A Novel 3D Graphical Password
Schema‖, IEEE International Conference on Virtual Environments, Human-Computer
Interfaces, and Measurement Systems, July 2006.
[2].Duhan Pooja, Gupta Shilpi , Sangwan Sujata, & Gulati Vinita, ―SECURED
AUTHENTICATION: 3D PASSWORD‖, I.J.E.M.S., VOL.3(2),242 – 245, 2012.
[3].Vishal Kolhe, Vipul Gunjal, Sayali Kalasakar & Pranjal Rathod, Secure Authentication
with 3D Password‖ , IJESIT, Volume 2, Issue 2, ISSN: 2319-5967 ISO 9001:2008
[4].Tejal Kognule, Yugandhara Thumbre, Snehal Kognule-3D PASSWORD, ICACACT,
IJCA
[5].en.wikipedia.org/wiki/3-D_Secure
[6] www.google.com
5/1/2014 25](https://image.slidesharecdn.com/newmicrosoftpowerpointpresentation-140501164846-phpapp01/85/3D-Password-25-320.jpg)


