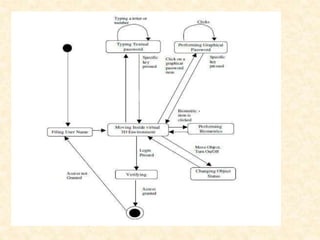
3D passwords combine multiple authentication factors by using a 3D virtual environment. Users authenticate by interacting with virtual objects in a specific sequence based on their location. This addresses limitations of traditional passwords that can be cracked or stolen. The 3D password is constructed through a user's interactions in the virtual world, combining what they know, have, and do for strong multi-factor authentication. While providing increased security, 3D passwords also have drawbacks such as increased storage needs and vulnerability to timing attacks if the virtual environment is not carefully designed.





![How it Works?
• Let us consider a 3D virtual environment space of size G ×G × G.
The 3D environment space is represented by the coordinates (x, y,
z) ∈ [1, . . . , G] ×[1, . . . , G] ×[1, . . . , G].
• The objects are distributed in the 3D virtual environment with
unique (x, y, z) coordinates.
• The user can walk in the virtual environment and type something
on a computer that exist in (x1, y1, z1) position, then walk into a
room that has a white board that exist in a position (x2, y2, z2) and
draw something on the white board. The combination and the
sequence of the previous two actions towards the specific objects
construct the user’s 3D password.](https://image.slidesharecdn.com/3dpassword-140423014905-phpapp02/85/3D-Password-6-320.jpg)