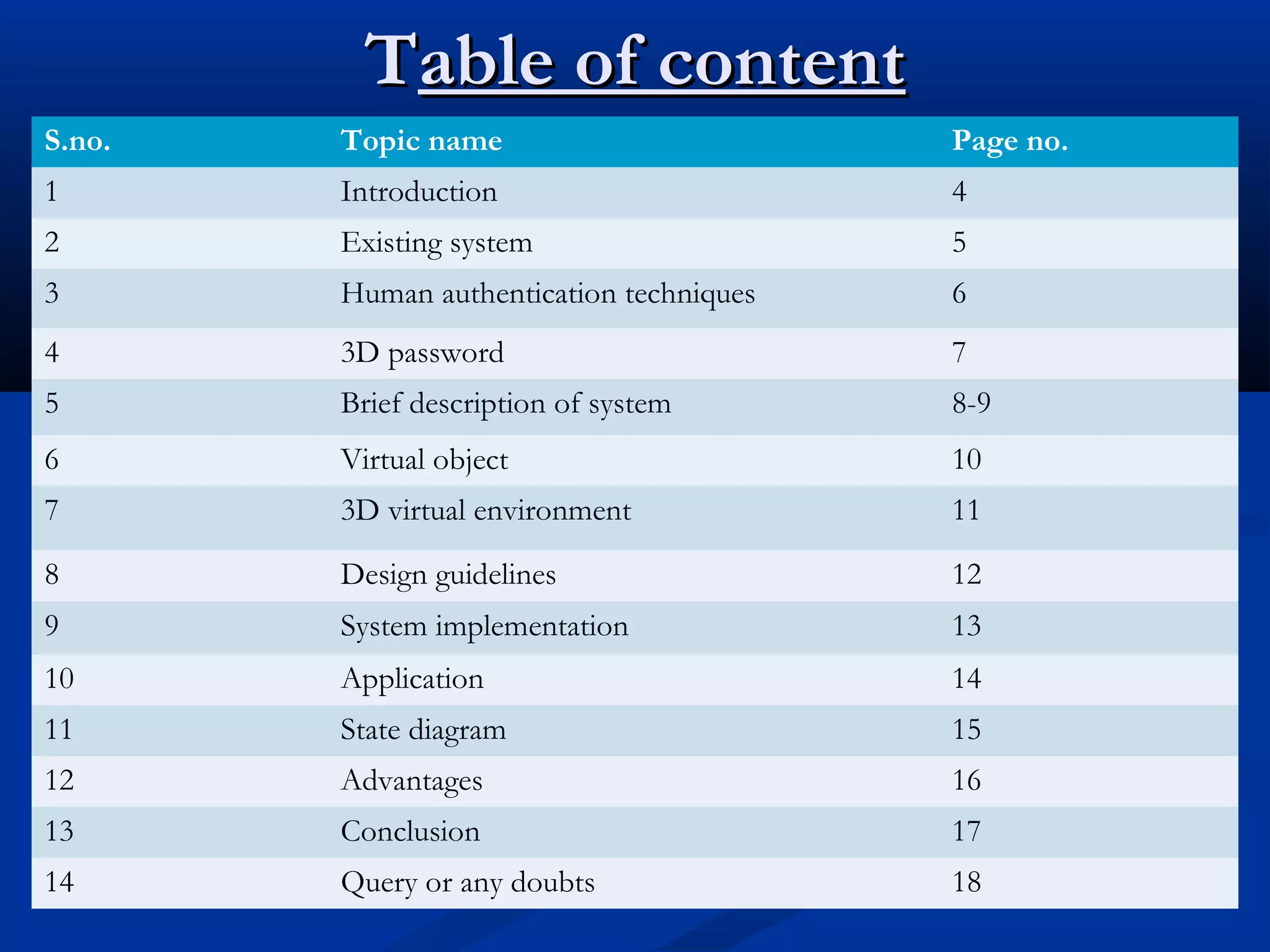
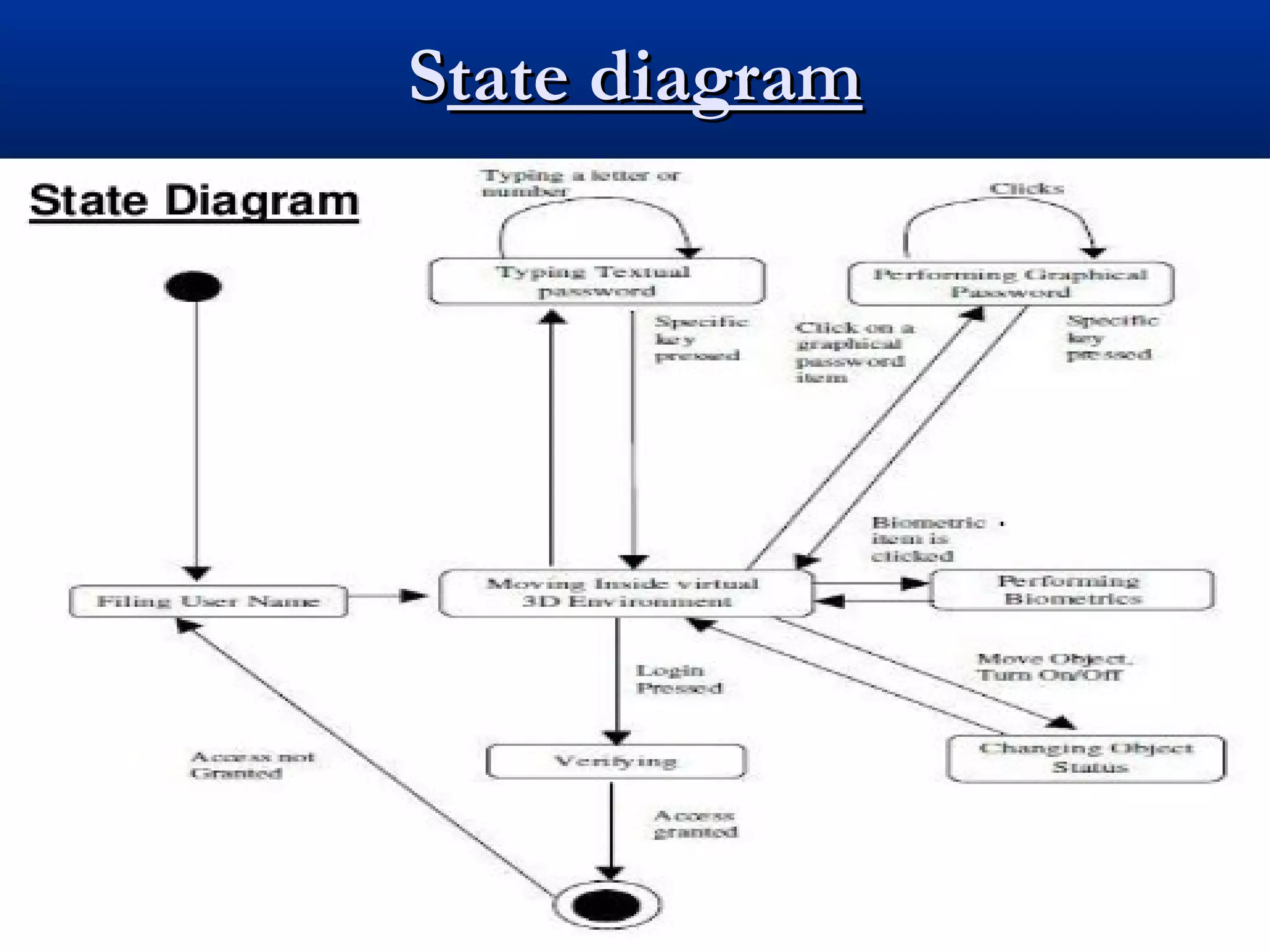
The document describes a 3D password authentication system. It begins with an introduction that outlines the need for more secure passwords beyond simple text passwords due to weaknesses in memorability. It then discusses existing security systems like text, graphical and biometric passwords. The document proposes a 3D password that combines recognition, recall, tokens and biometrics for multifactor authentication in an interactive 3D virtual environment containing various objects. It provides guidelines for implementation, examples of applications, and advantages of the 3D password system being difficult to crack without knowing the specific object interaction sequence.