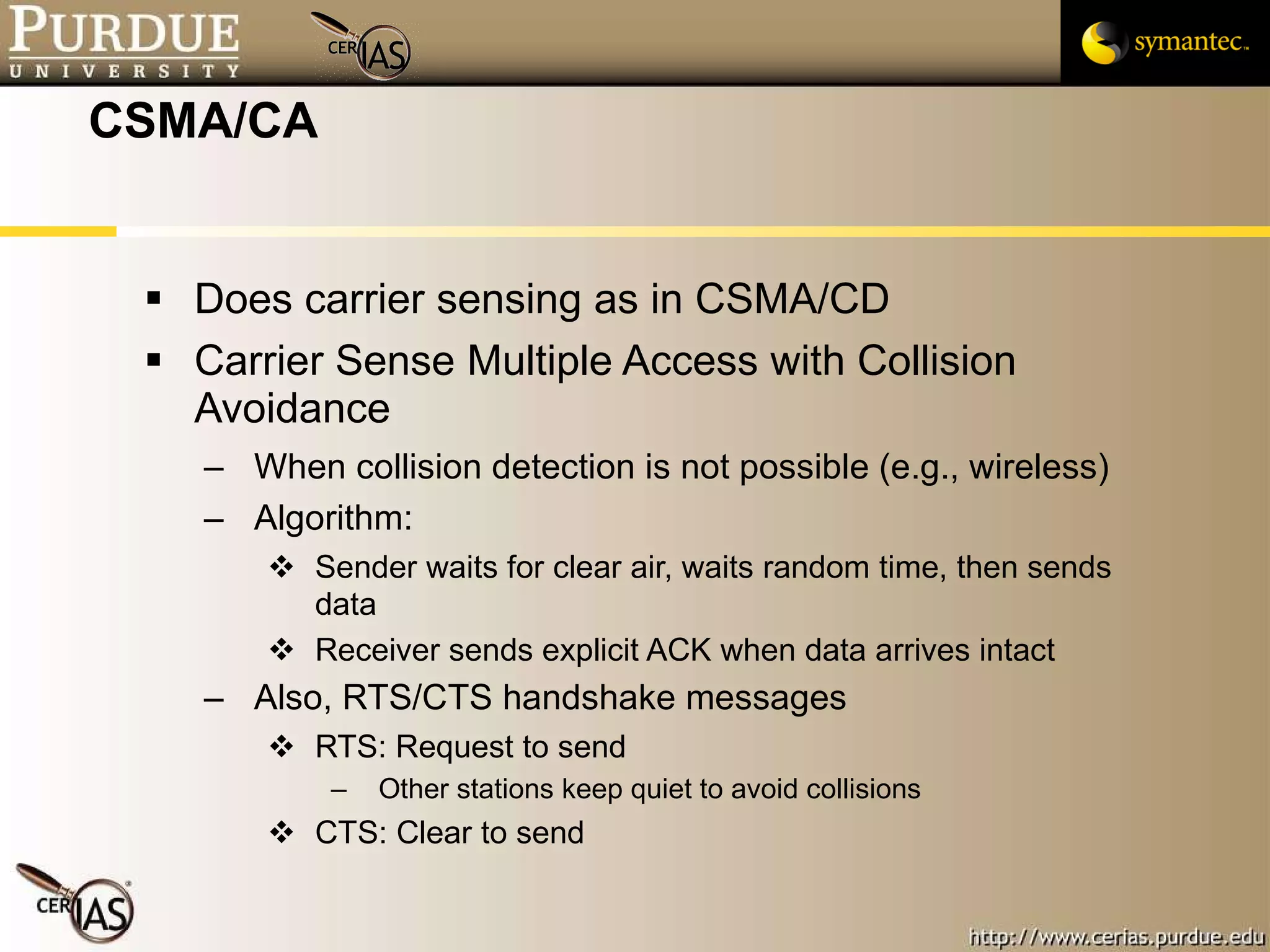
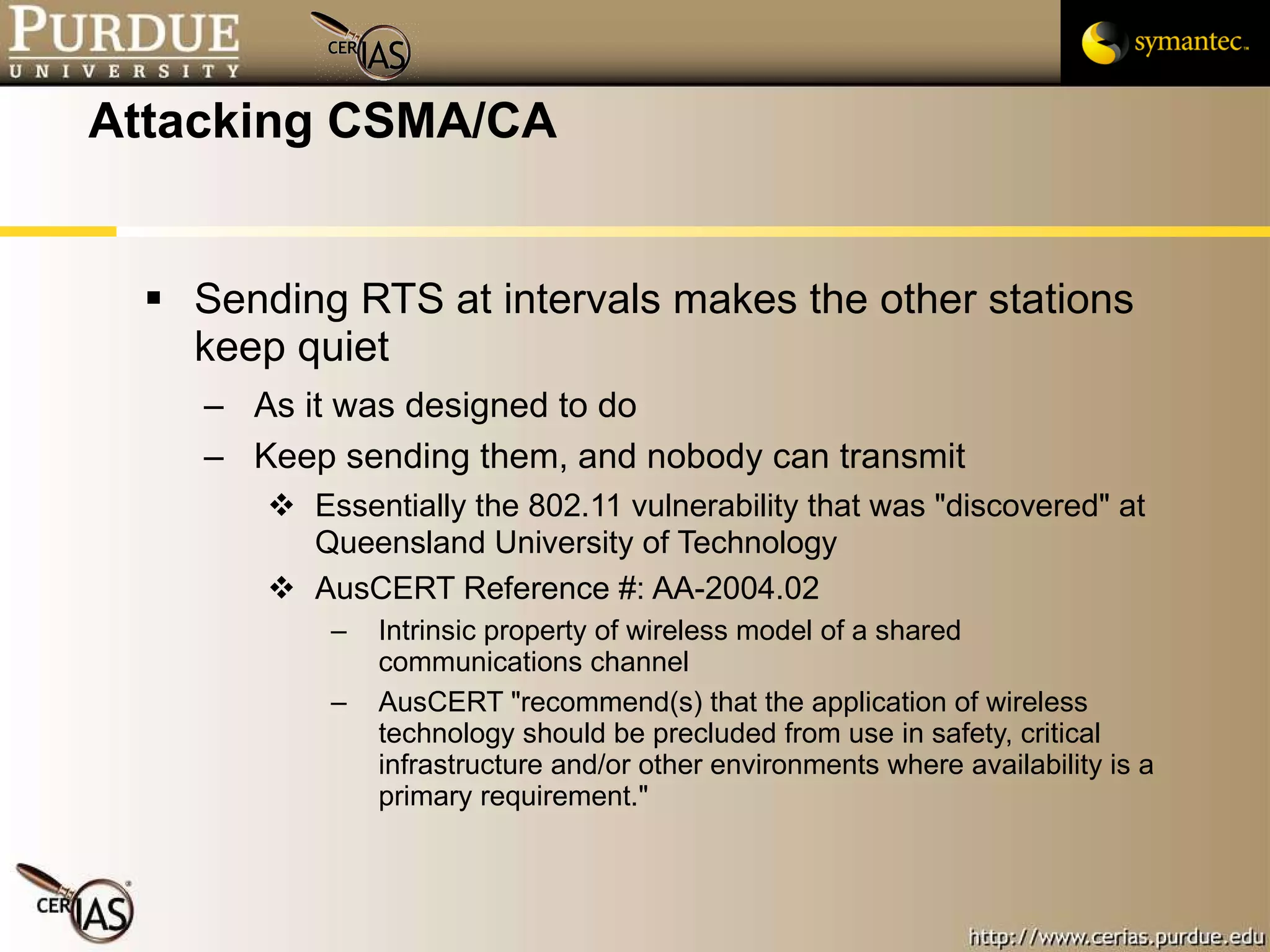
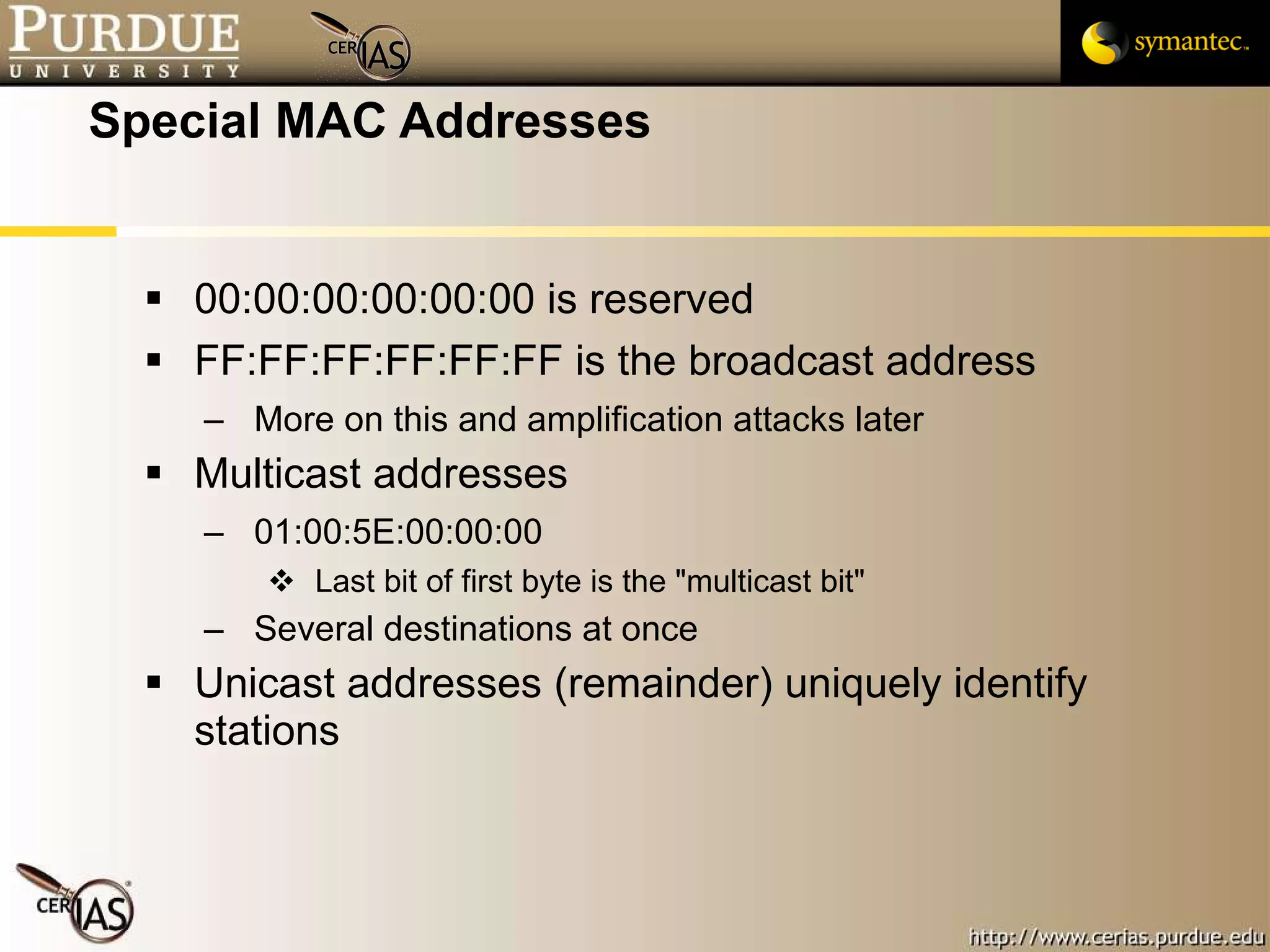
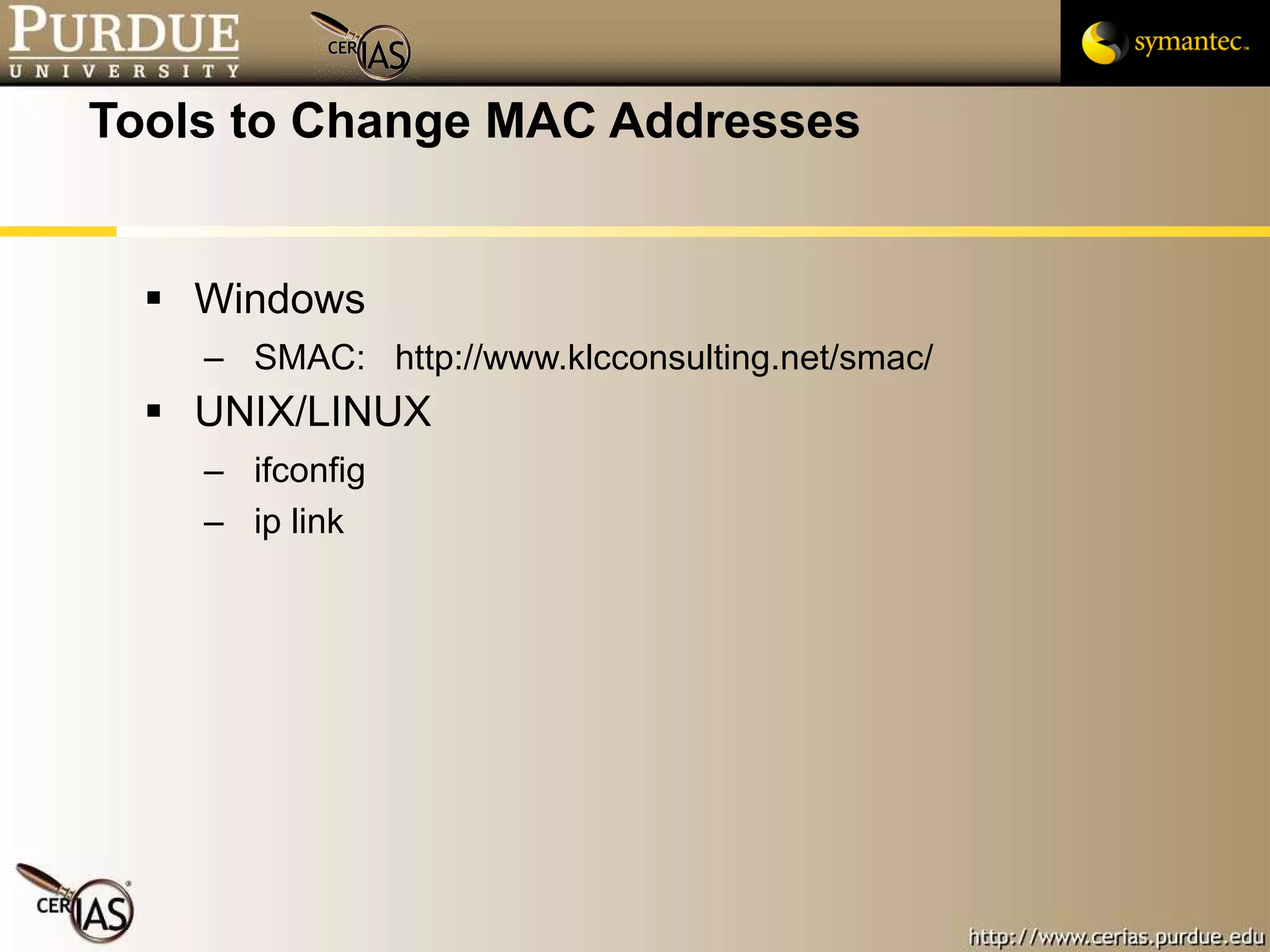
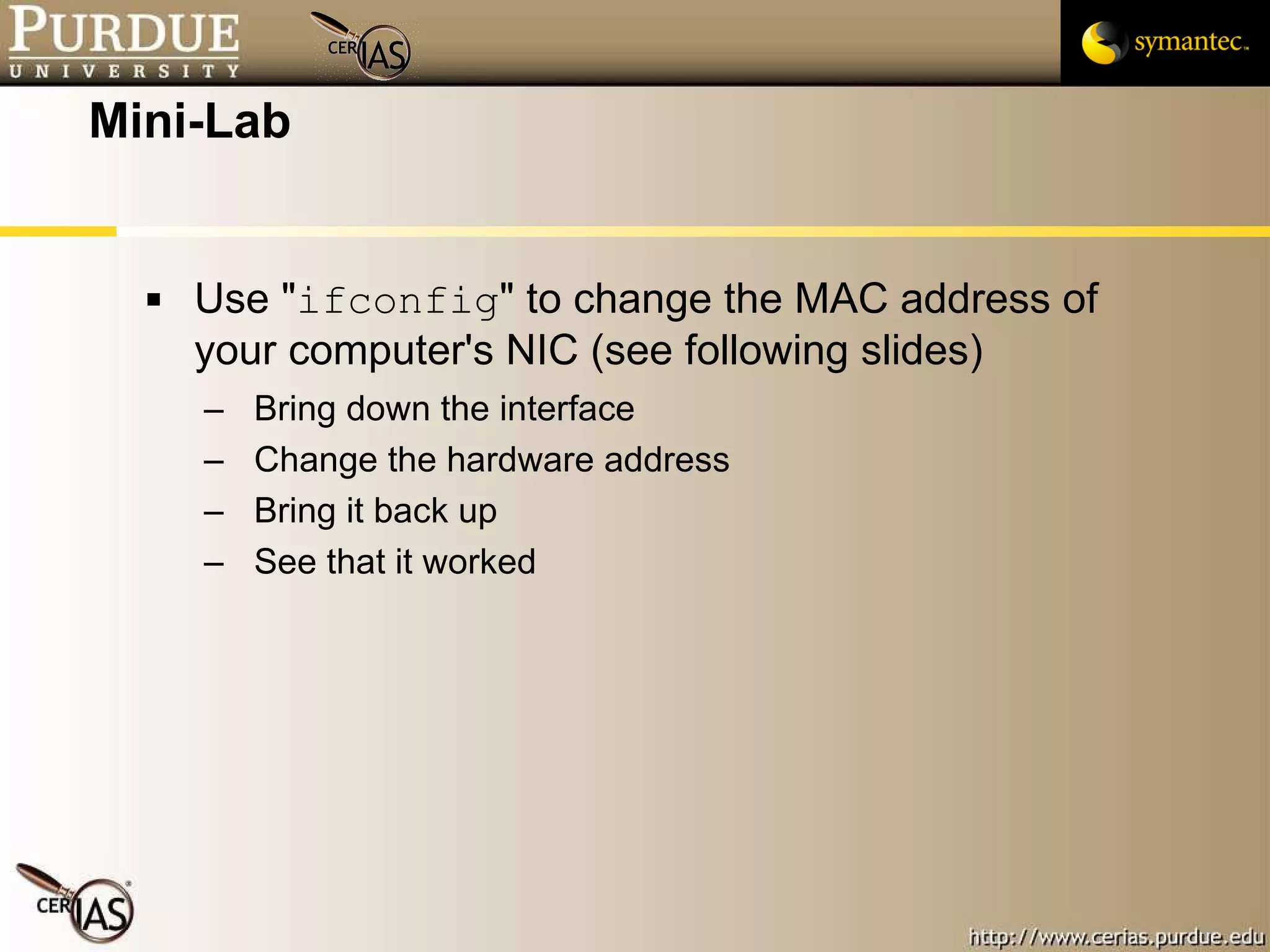
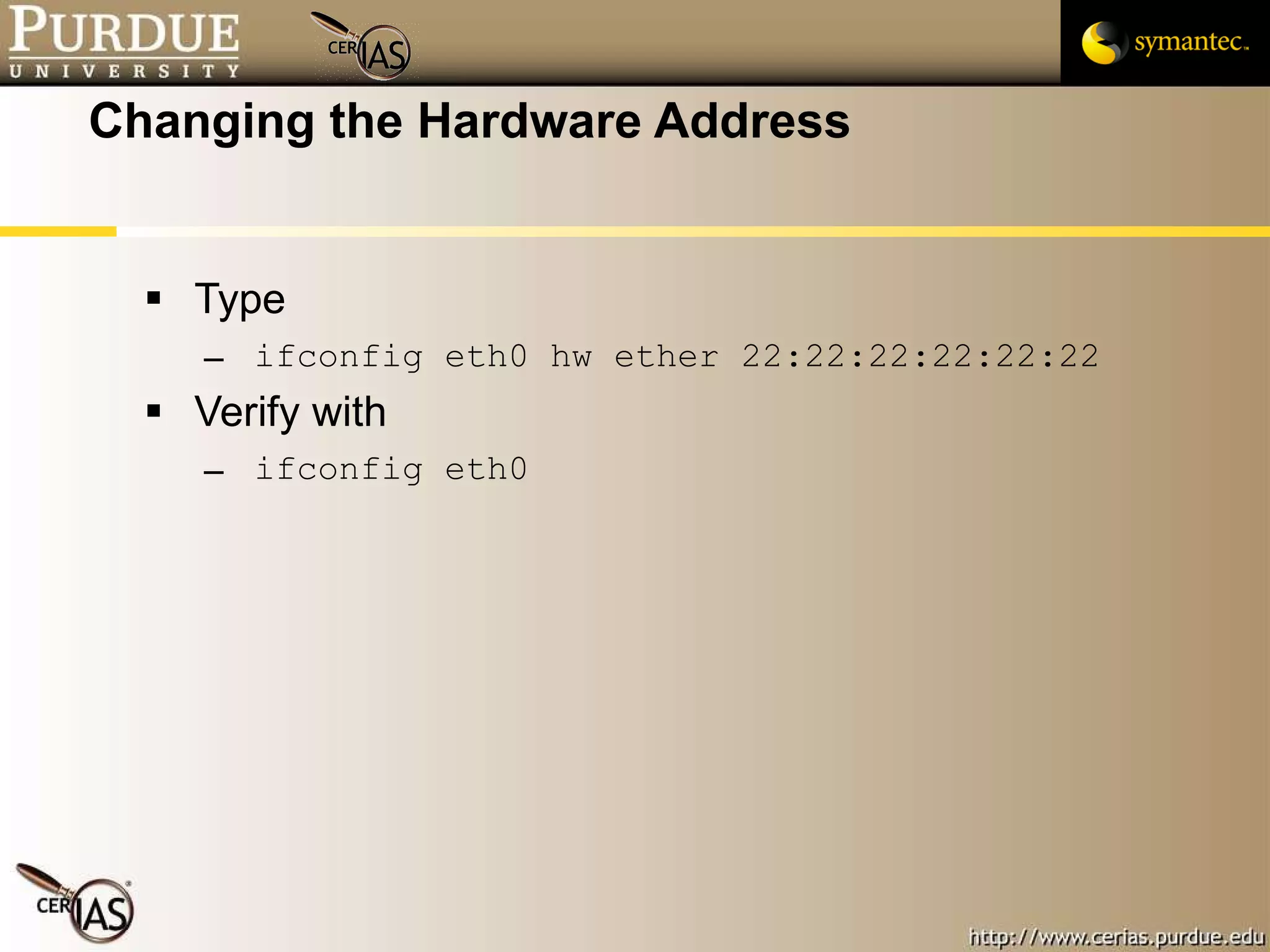
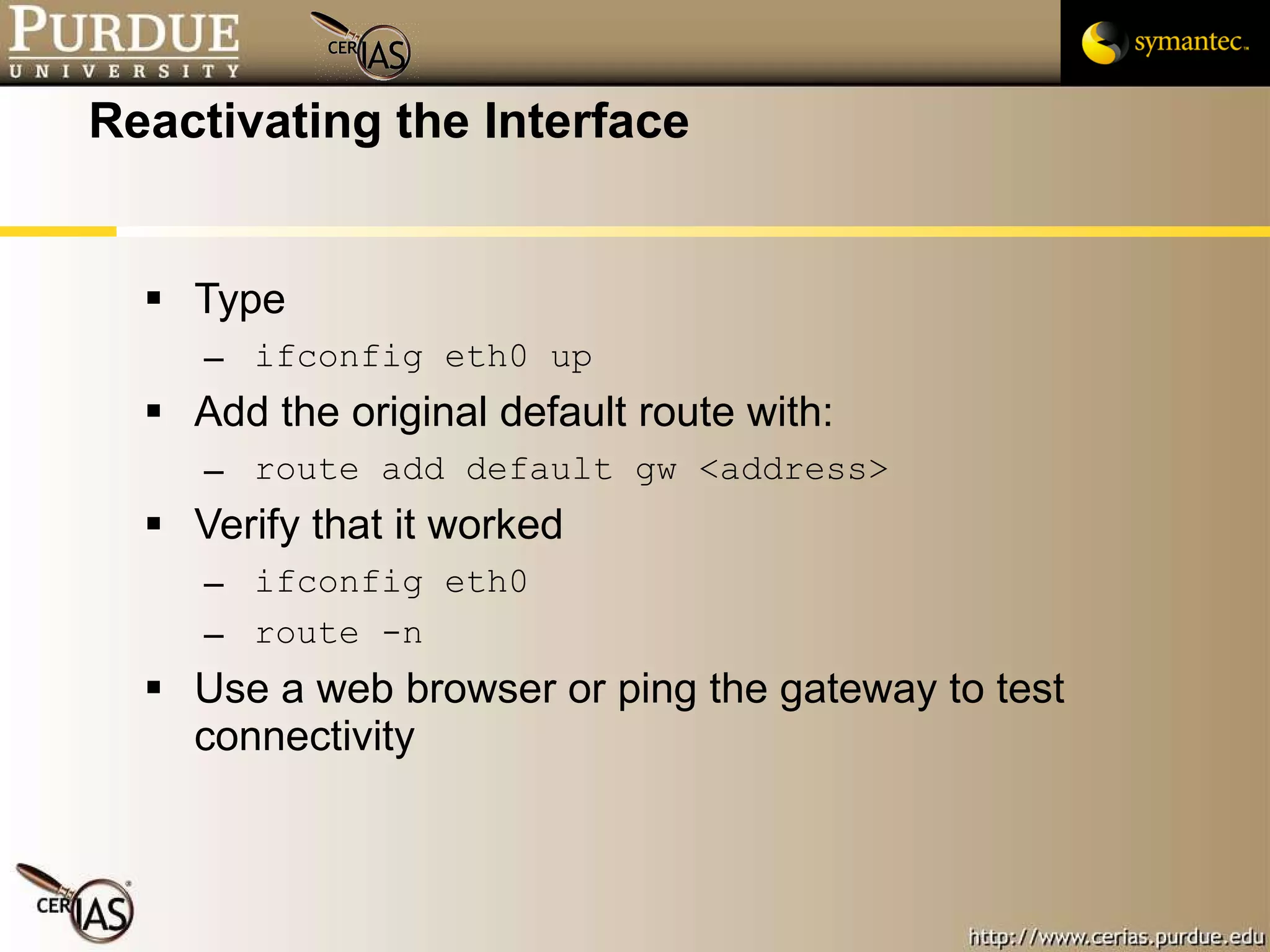
This document provides an overview and learning objectives for a course on network security. It covers topics like physical layer risks, link layer vulnerabilities, media access control, logical link control, ARP, and wireless network attacks. The goals are to understand vulnerabilities in network designs and protocols, and to identify tools that can detect relevant policy violations for each layer.













![Pascal Meunier [email_address] Contributors: Jared Robinson, Alan Krassowski, Craig Ozancin, Tim Brown, Wes Higaki, Melissa Dark, Chris Clifton, Gustavo Rodriguez-Rivera](https://image.slidesharecdn.com/2-physlink-091013224258-phpapp02/75/2-Phys-Link-56-2048.jpg)