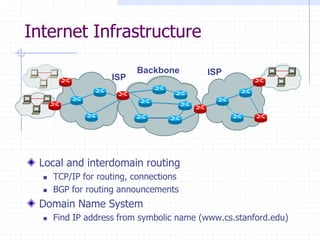
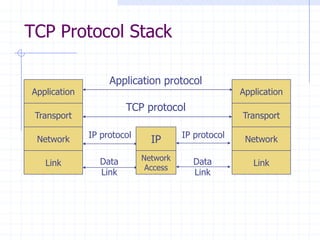
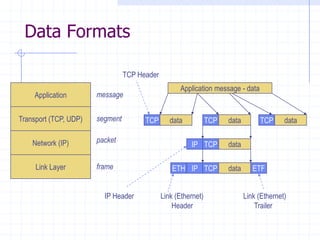
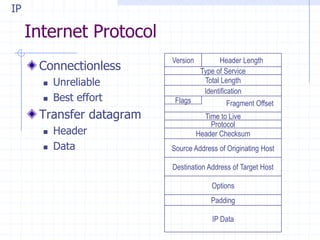
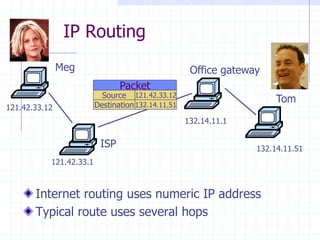
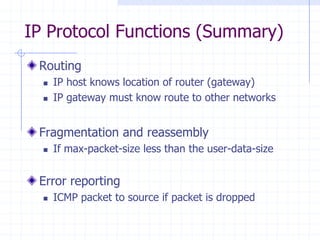
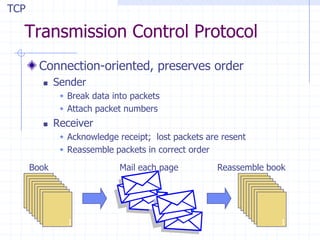
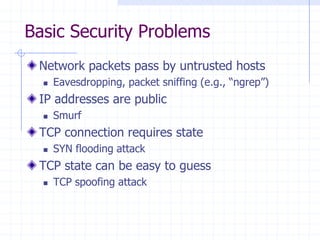
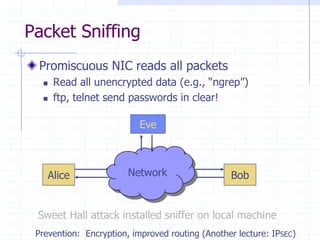
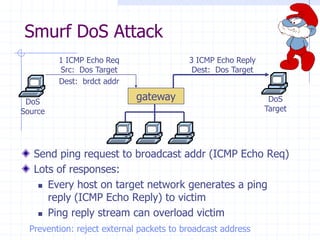
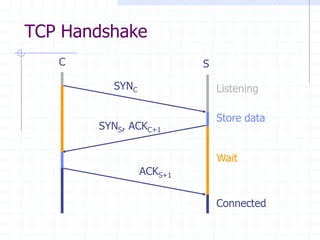
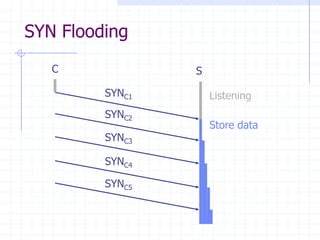
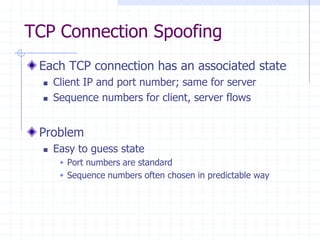
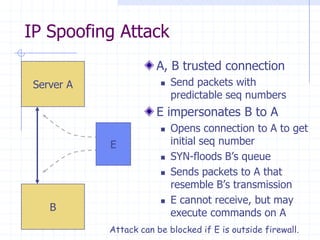
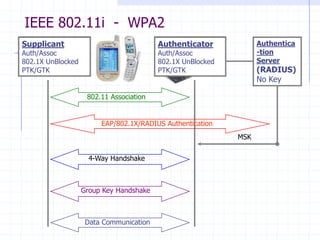
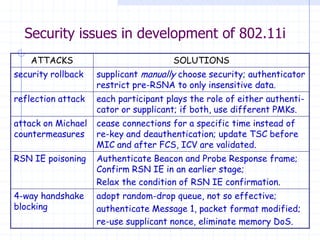
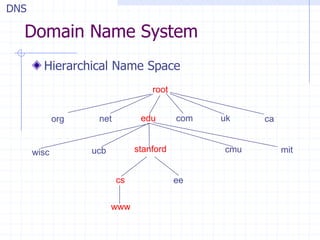
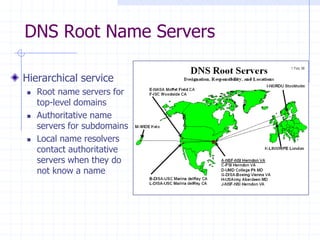
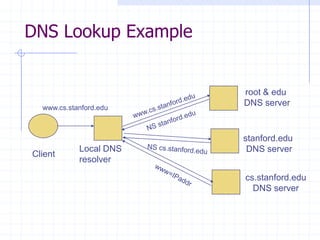
This document discusses several network protocols and common vulnerabilities. It begins with an overview of basic networking concepts like TCP/IP and UDP. It then examines specific attacks such as SYN flooding, packet sniffing, and spoofing. The document also reviews security issues for protocols including IP, TCP, DNS, and wireless networks. It provides examples of how these protocols can be exploited and discusses approaches to improving security, such as TCP sequence number randomization and the evolution of wireless encryption standards.





![Protection against SYN Attacks
Client sends SYN
Server responds to Client with SYN-ACK cookie
sqn = f(src addr, src port, dest addr, dest port, rand)
Normal TCP response but server does not save state
Honest client responds with ACK(sqn)
Server checks response
If matches SYN-ACK, establishes connection
“rand” is top 5 bits of 32-bit time counter
Server checks client response against recent values
See http://cr.yp.to/syncookies.html
[Bernstein, Schenk]](https://image.slidesharecdn.com/12-tcp-dns-140326164729-phpapp01/85/12-tcp-dns-18-320.jpg)

![Recent DoS vulnerability [Watson’04]
Suppose attacker can guess seq. number for an
existing connection:
Attacker can send Reset packet to
close connection. Results in DoS.
Naively, success prob. is 1/232 (32-bit seq. #’s).
Most systems allow for a large window of
acceptable seq. #’s
Much higher success probability.
Attack is most effective against long lived
connections, e.g. BGP.](https://image.slidesharecdn.com/12-tcp-dns-140326164729-phpapp01/85/12-tcp-dns-22-320.jpg)
![Cryptographic network protection
Solutions above the transport layer
Examples: SSL and SSH
Protect against session hijacking and injected data
Do not protect against denial-of-service attacks caused by
spoofed packets
Solutions at network layer
Use cryptographically random ISNs [RFC 1948]
More generally: IPsec
Can protect against
session hijacking and injection of data
denial-of-service attacks using session resets](https://image.slidesharecdn.com/12-tcp-dns-140326164729-phpapp01/85/12-tcp-dns-23-320.jpg)



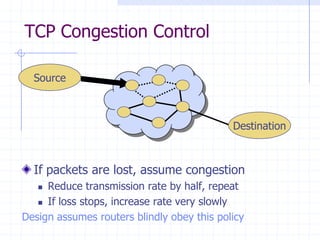
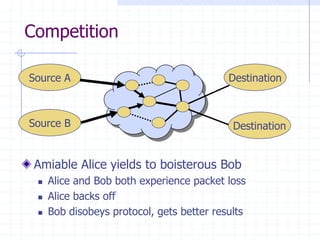

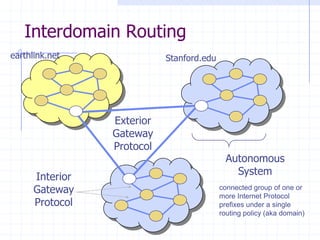

![BGP example [D. Wetherall]
Transit: 2 provides transit for 7
Algorithm seems to work OK in practice
BGP is does not respond well to frequent node outages
3 4
6 5
7
1
8 2
7
7
2 7
2 7
2 7
3 2 7
6 2 7
2 6 52 6 5
2 6 5
3 2 6 5
7 2 6 5
6 5
5
5](https://image.slidesharecdn.com/12-tcp-dns-140326164729-phpapp01/85/12-tcp-dns-36-320.jpg)

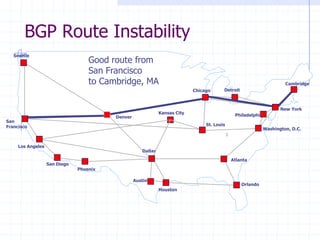
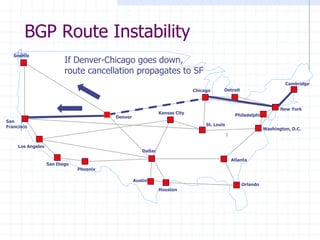
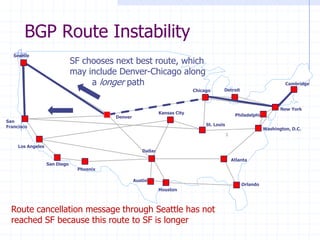



![DNS Rebinding Attack
Read permitted: it’s the “same origin”
Firewall
www.evil.com
web server
ns.evil.com
DNS server
171.64.7.115
www.evil.com?
corporate
web server
171.64.7.115 TTL = 0
<iframe src="http://www.evil.com">
192.168.0.100
192.168.0.100
[DWF’96, R’01]
DNS-SEC cannot
stop this attack](https://image.slidesharecdn.com/12-tcp-dns-140326164729-phpapp01/85/12-tcp-dns-50-320.jpg)


