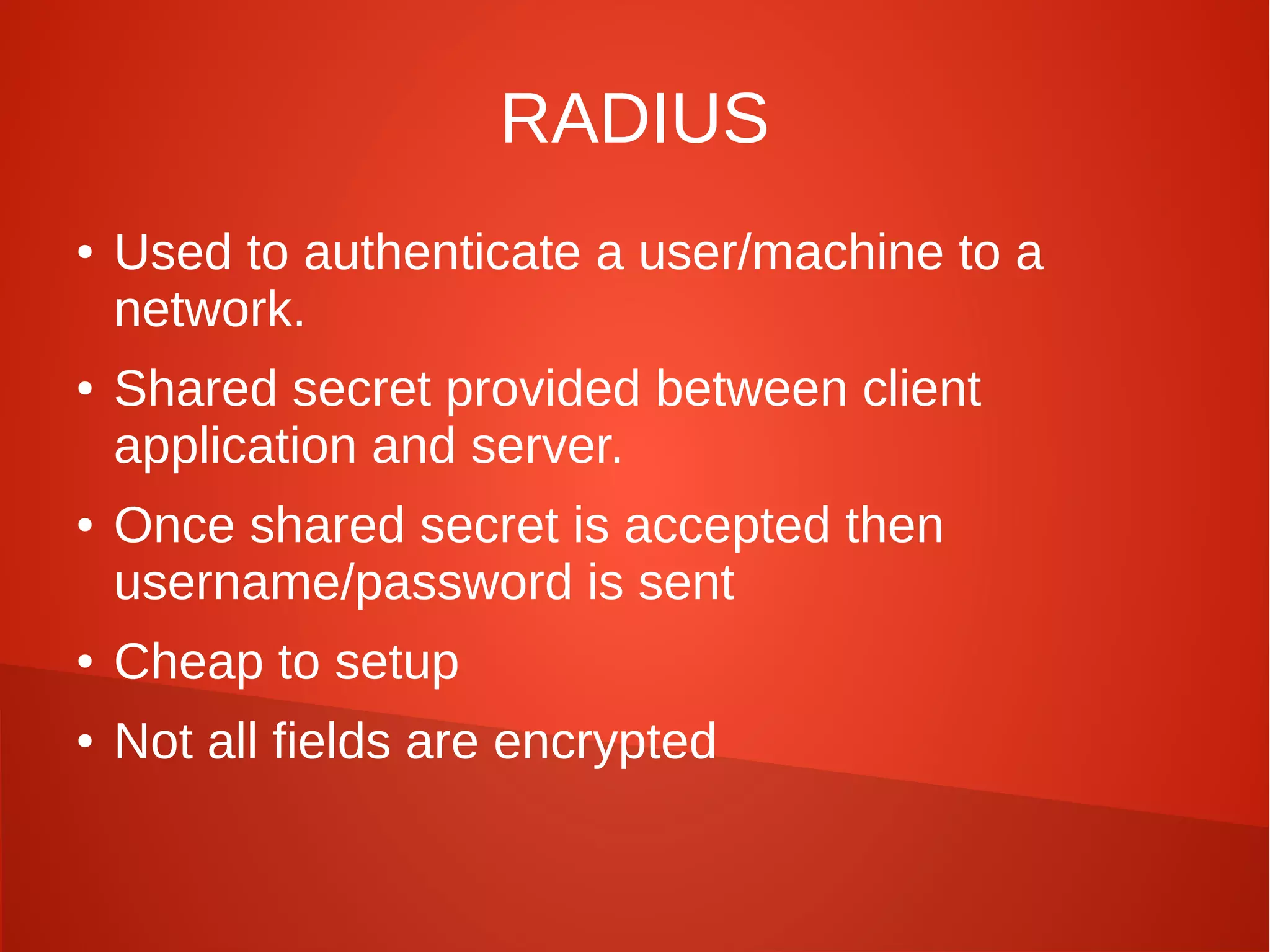
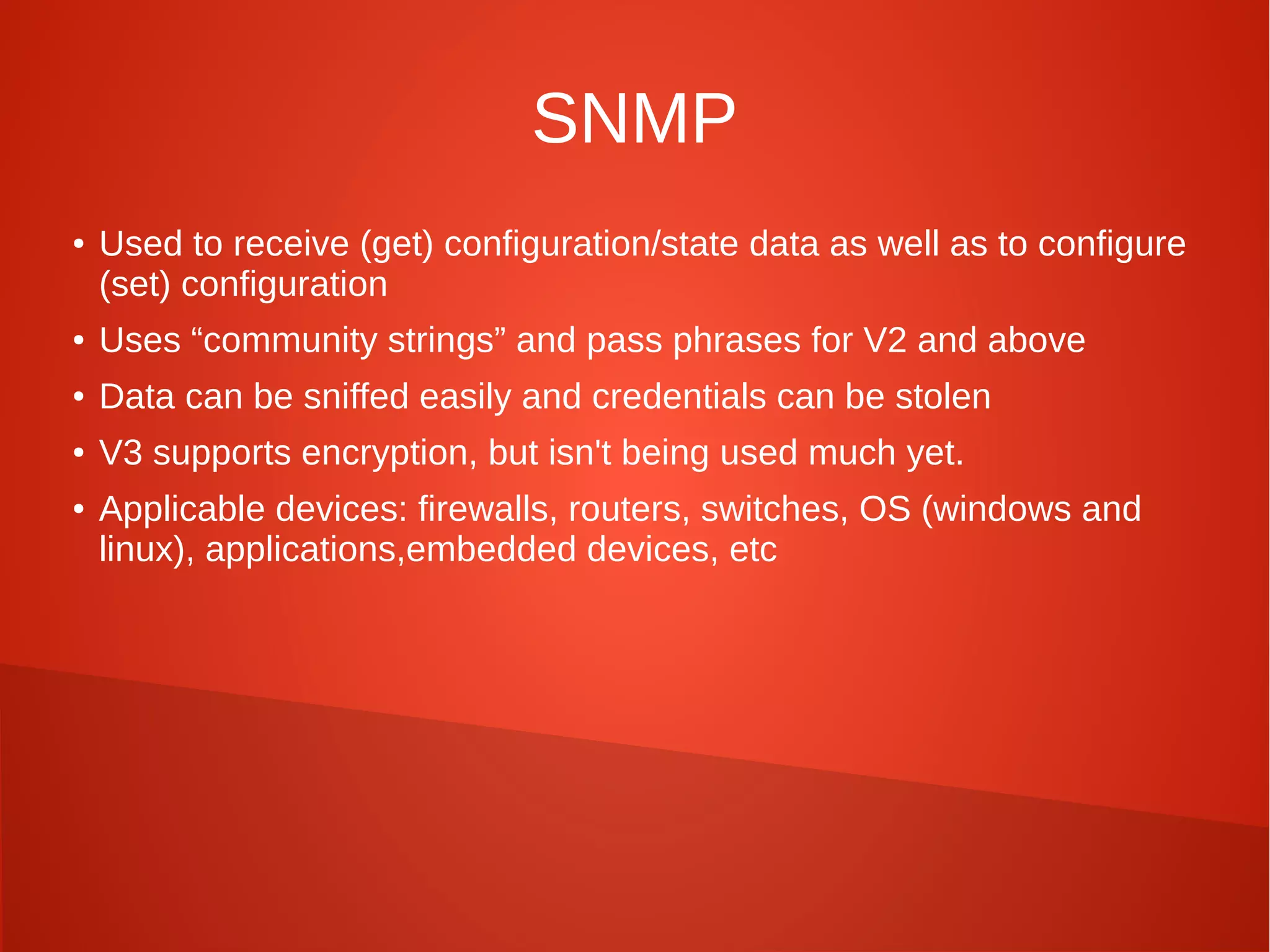
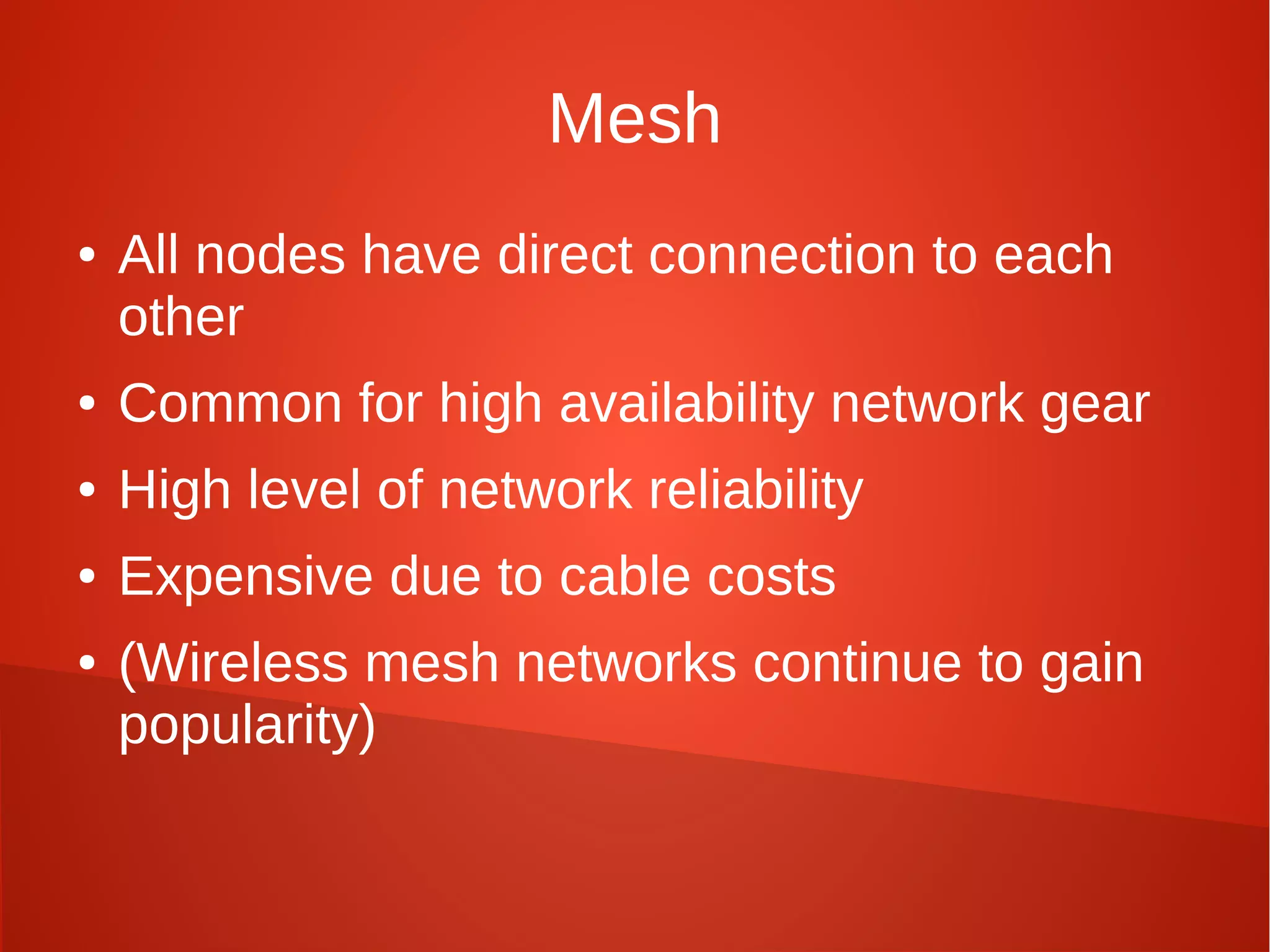
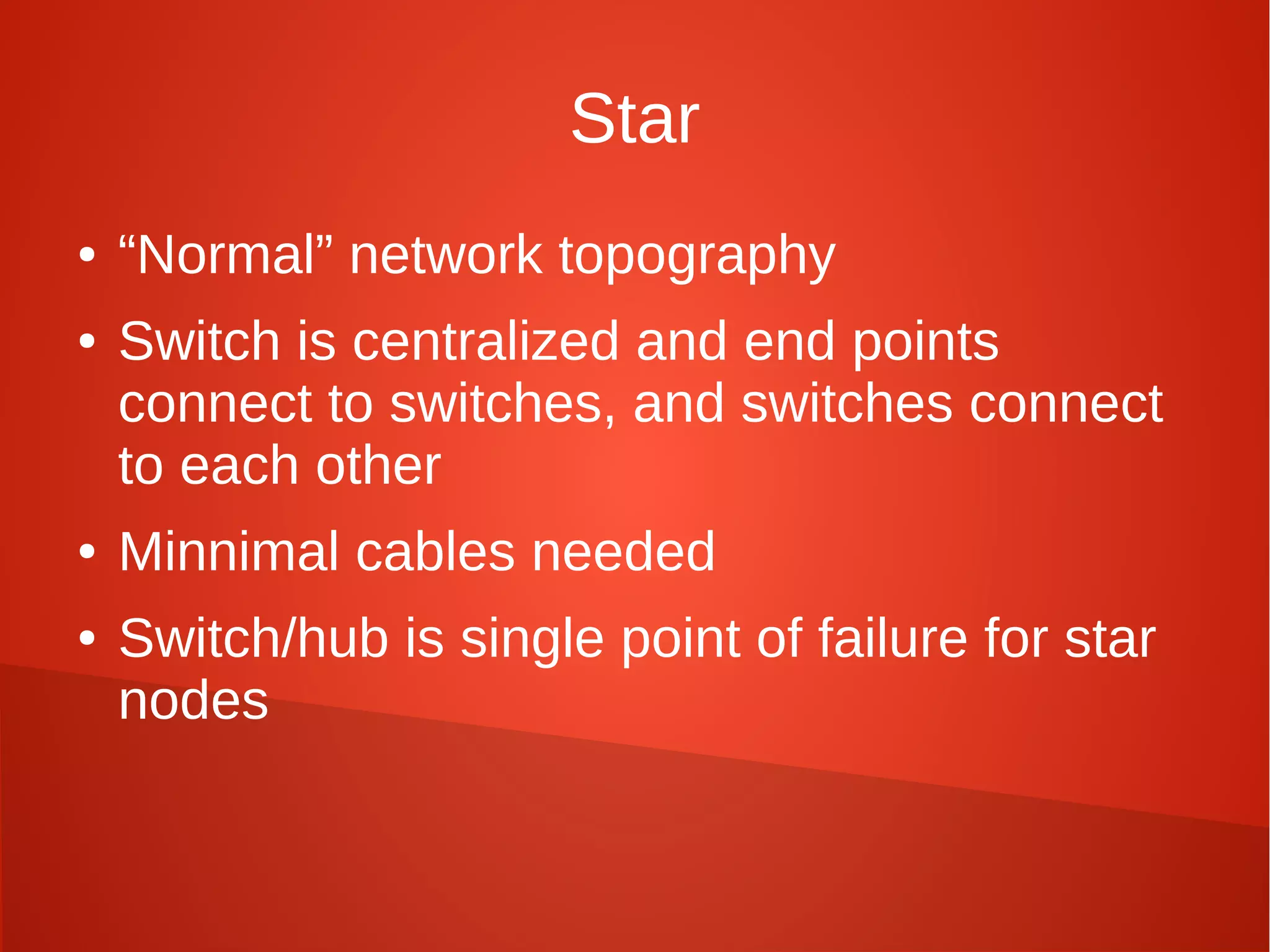
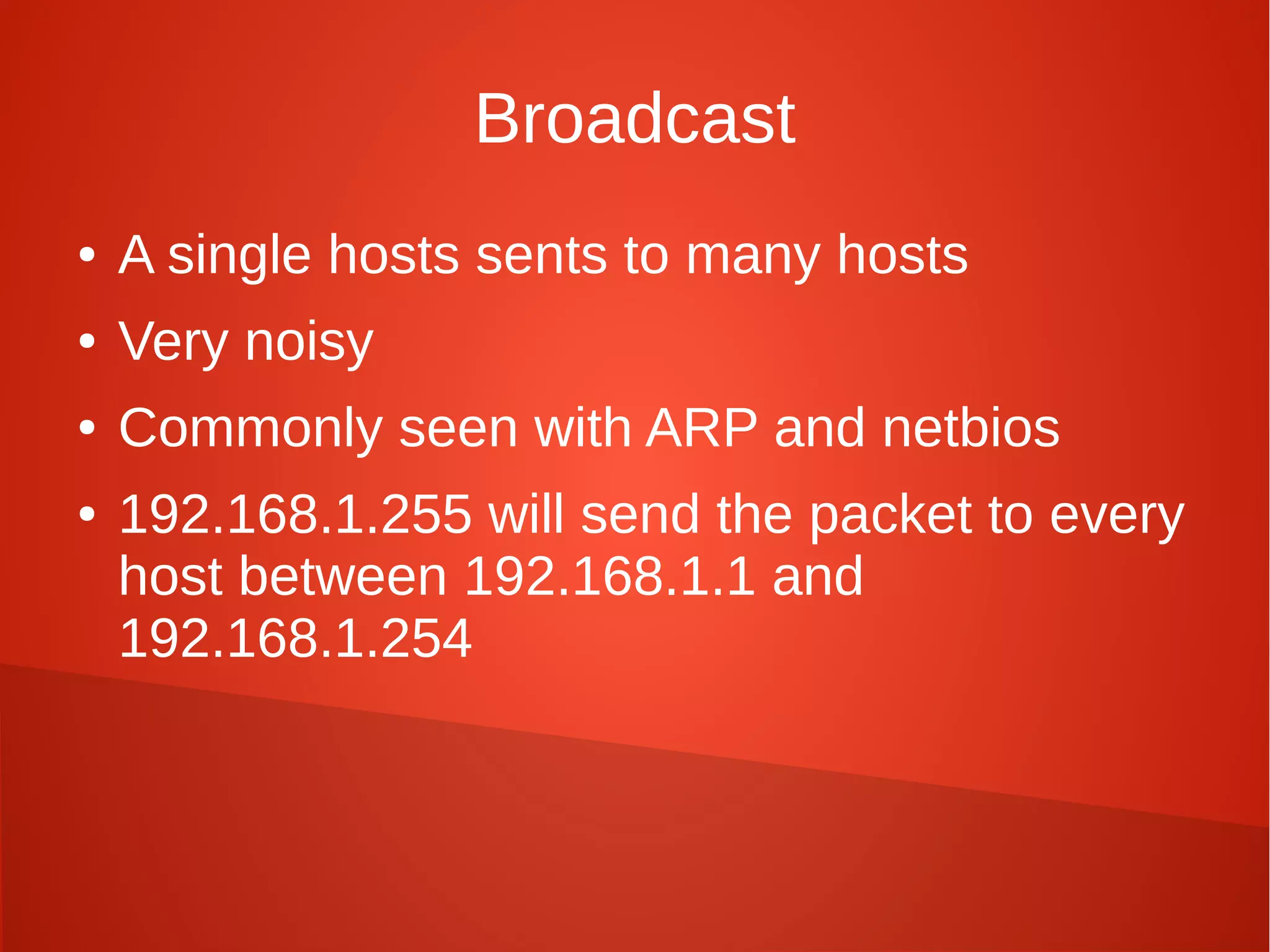
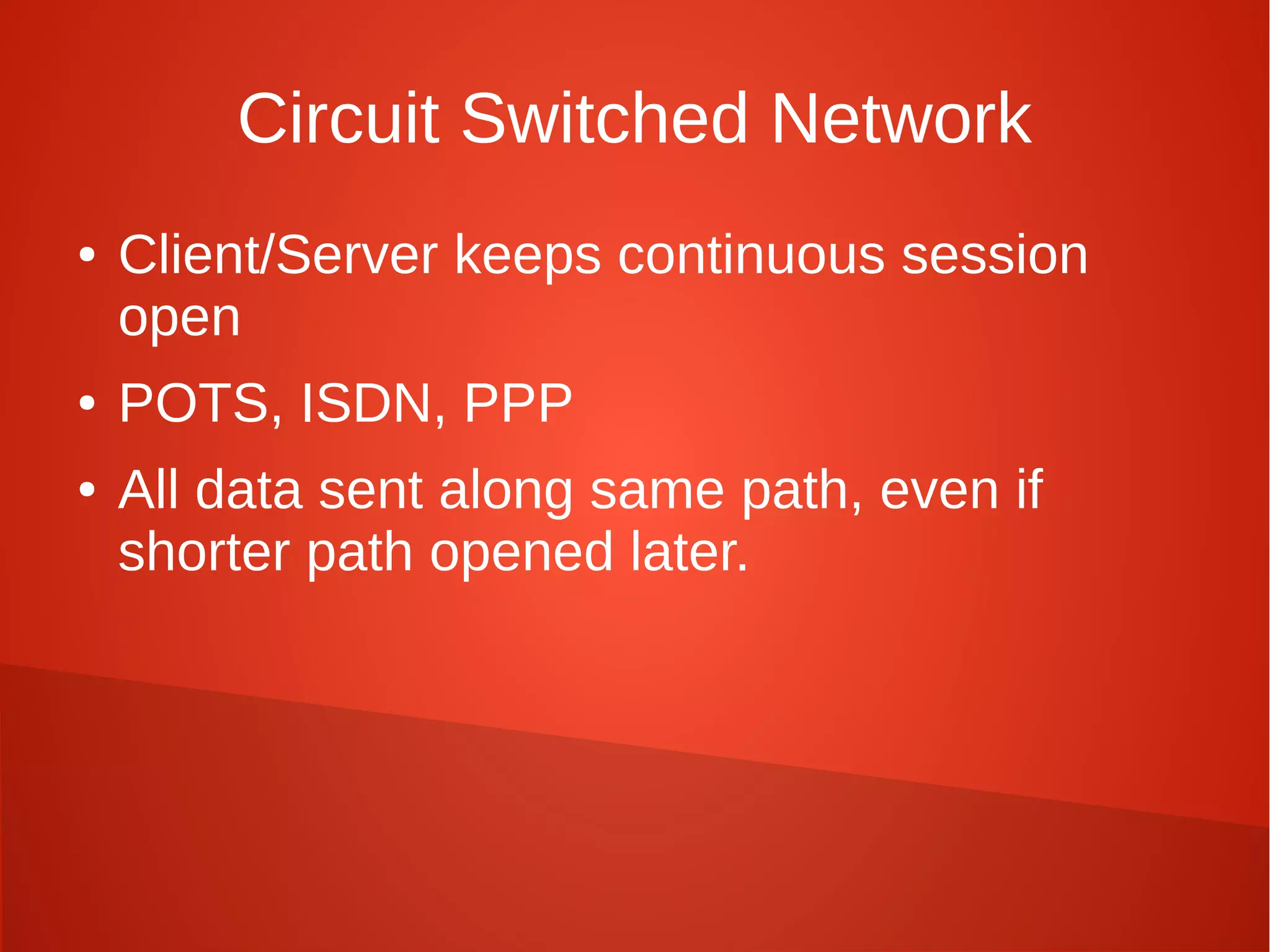
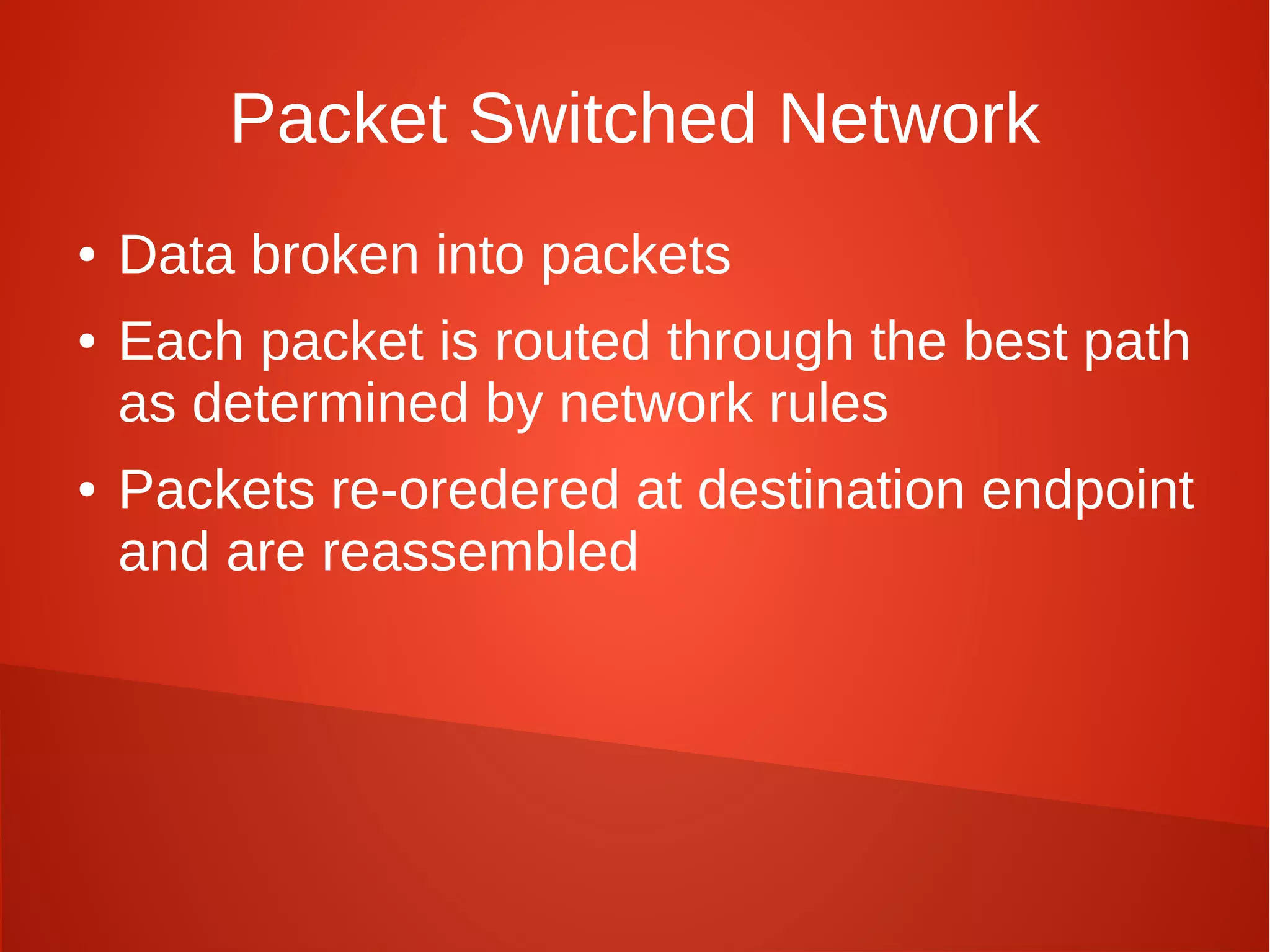
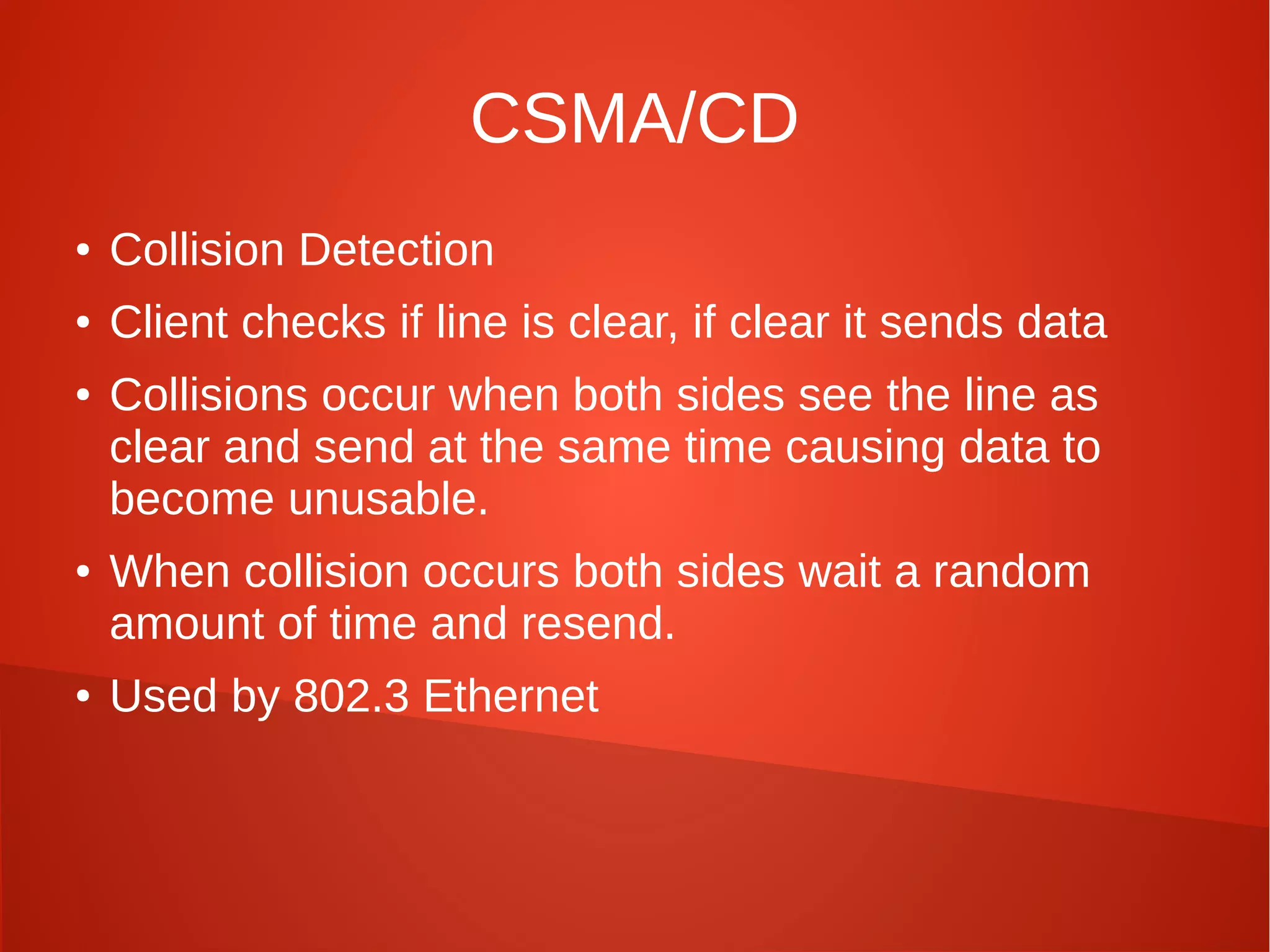
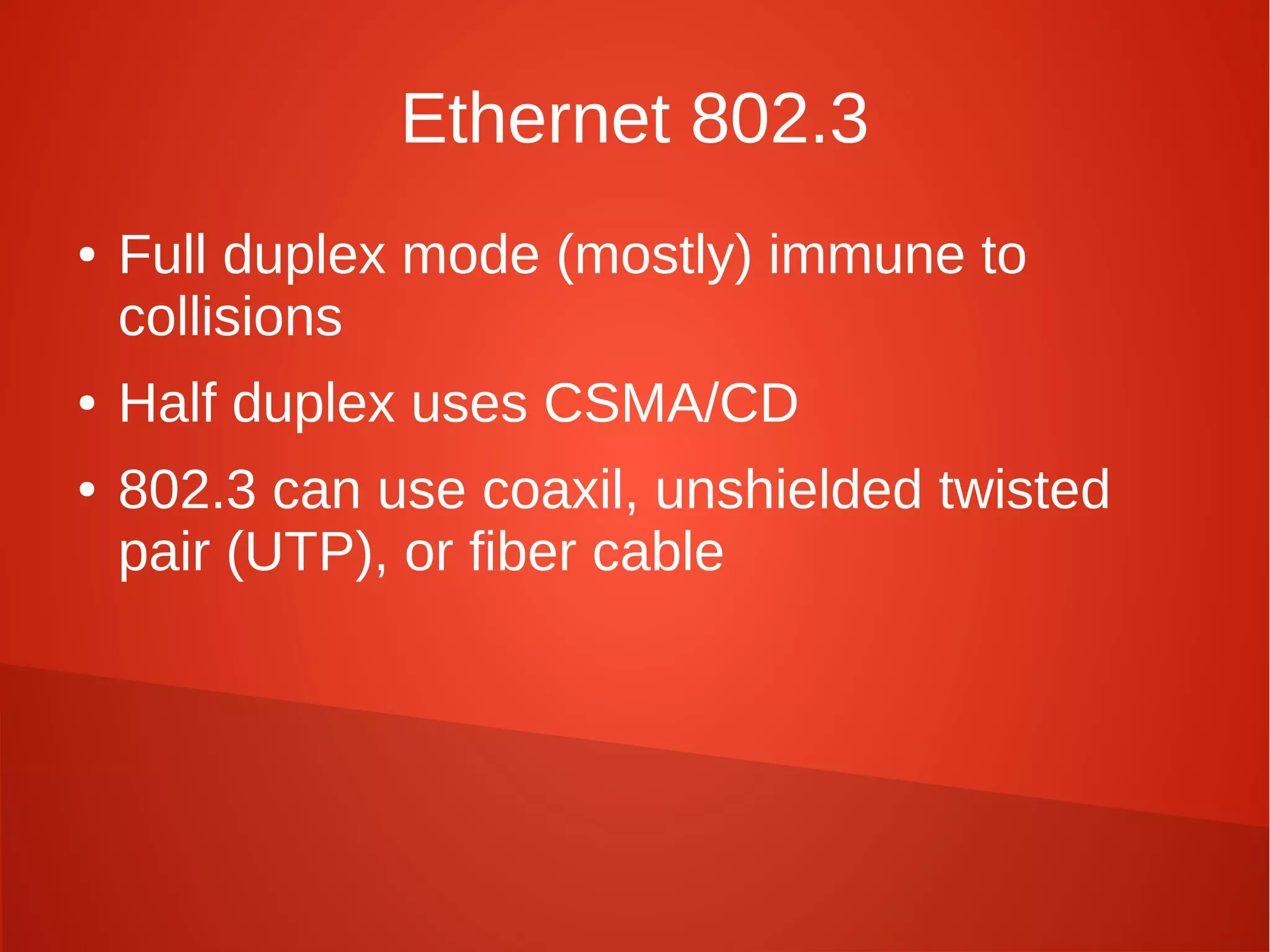
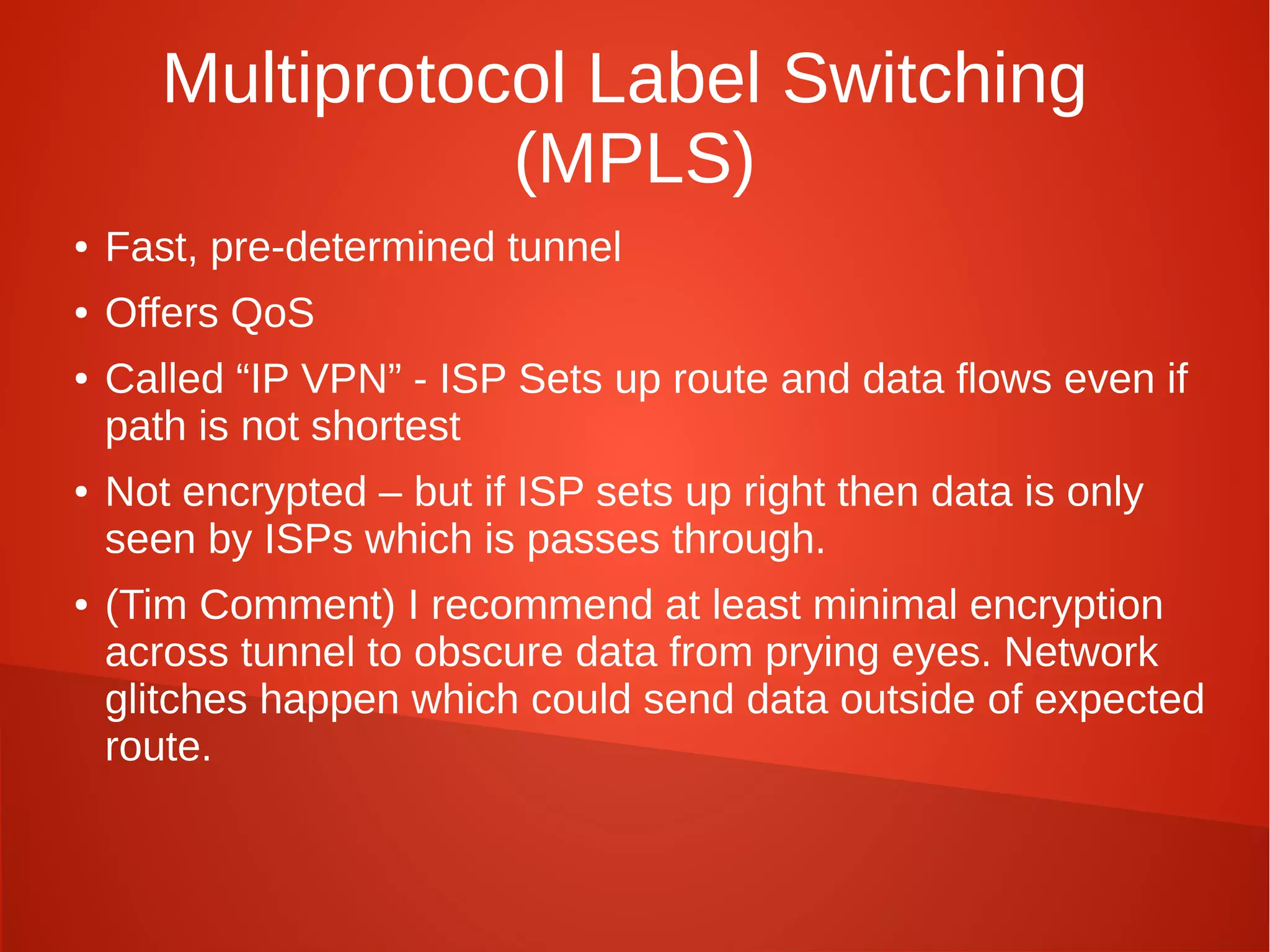
This document provides a summary of network security concepts covered in Week 7 of a CISSP training course. It discusses authentication protocols like RADIUS and SNMP, as well as remote access services such as Telnet and protocols like TCP/IP. It also covers network device types, topologies, and common network attacks such as denial of service, spoofing, and session hijacking. Countermeasures discussed include network segmentation, firewalls, patching, and log monitoring.