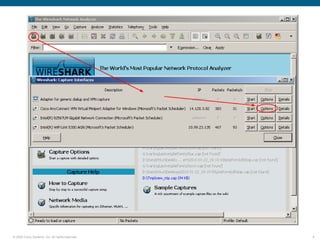
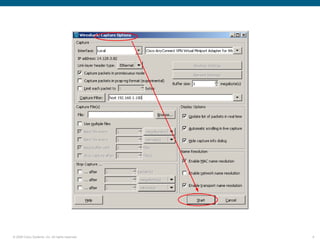
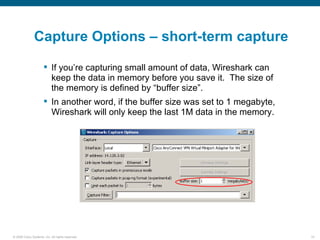
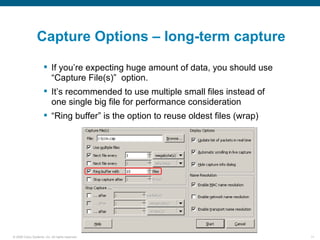
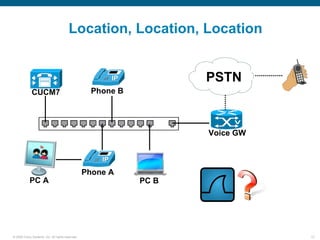
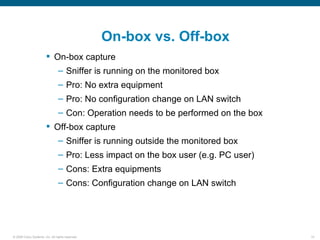
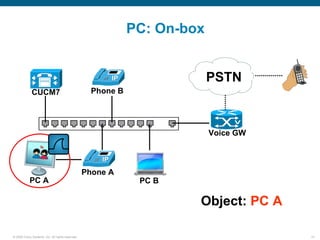
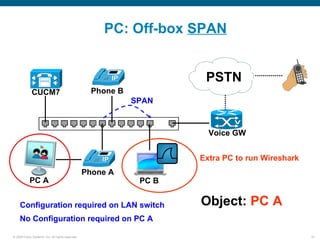
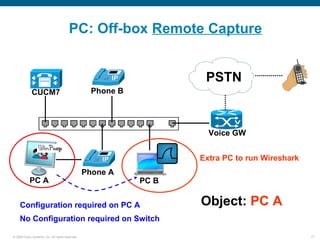
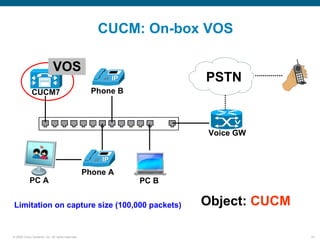
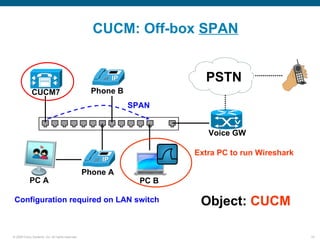
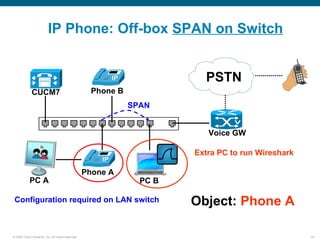
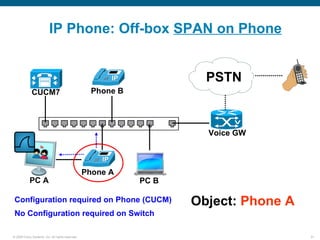
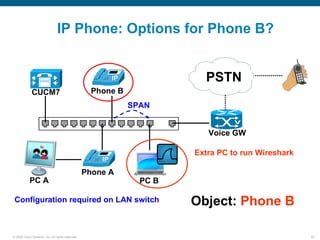
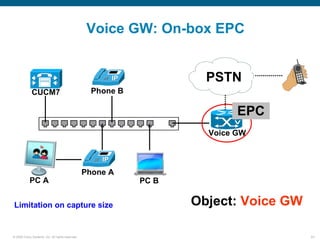
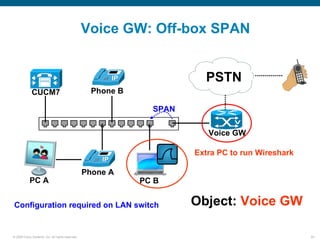
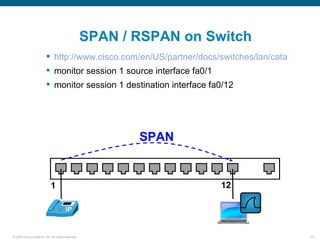
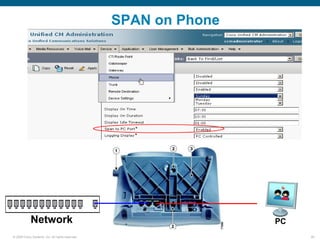
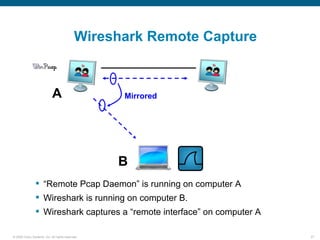
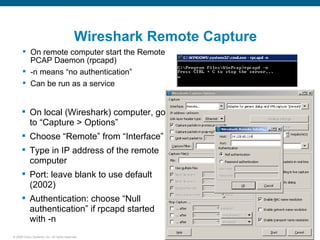
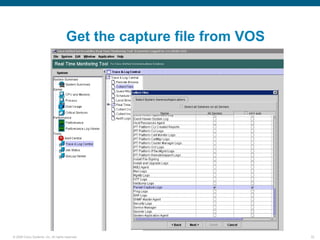
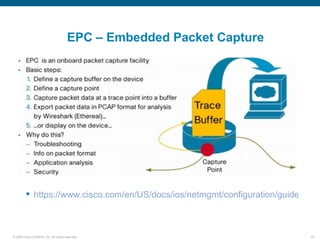
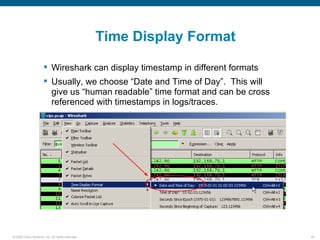
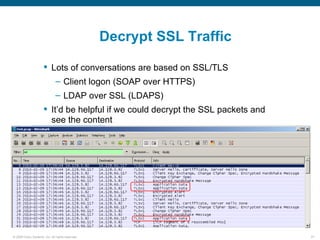
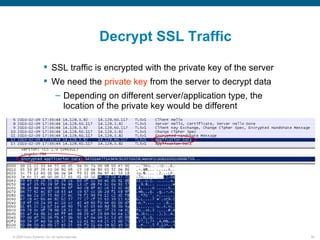
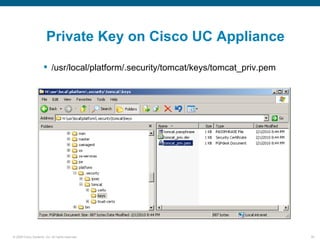
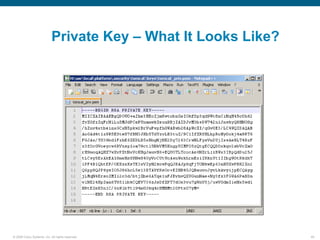
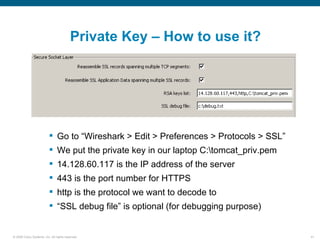
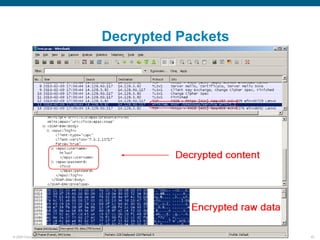
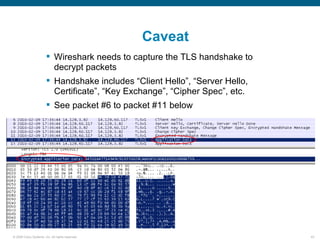
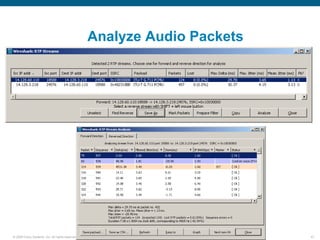
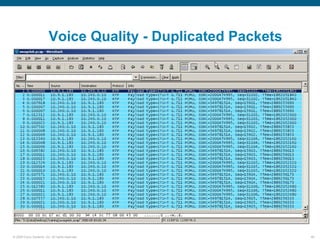
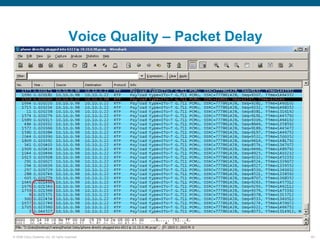
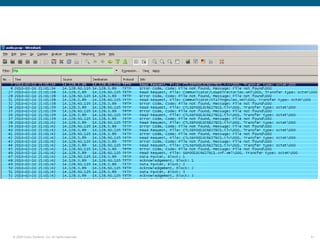
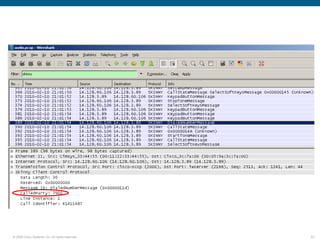
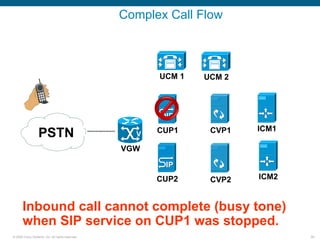
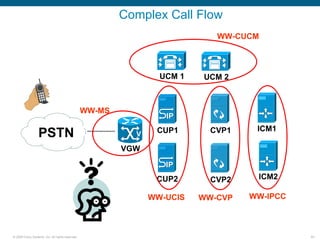
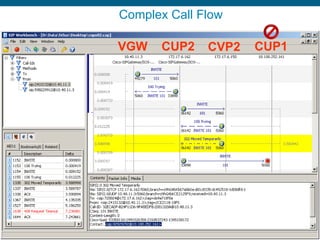
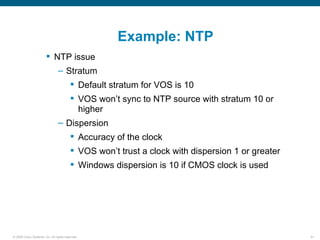
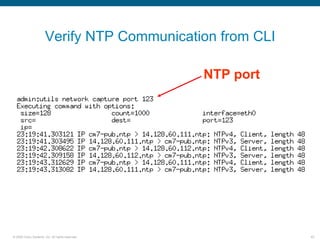
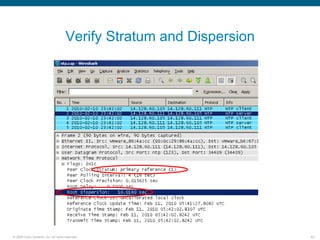
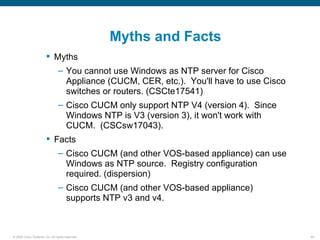
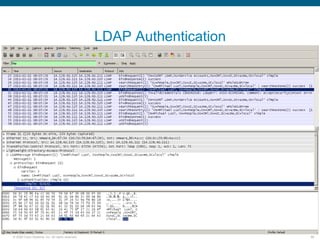
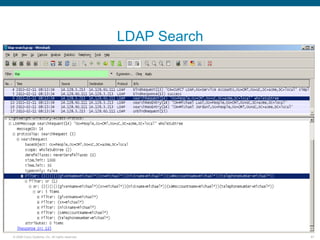
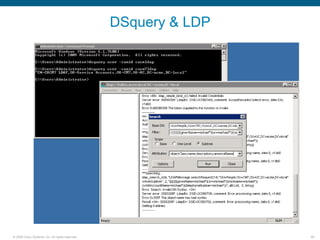
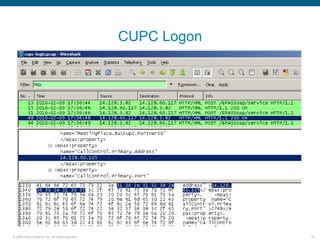
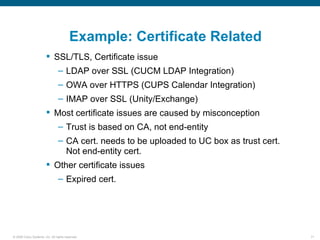
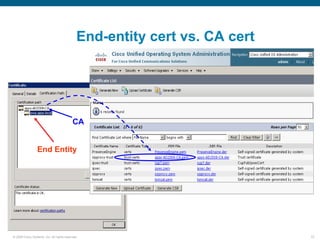
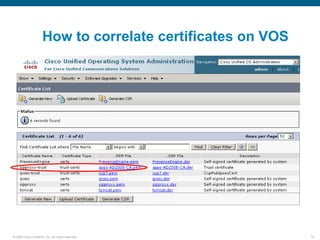
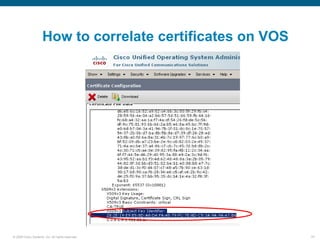
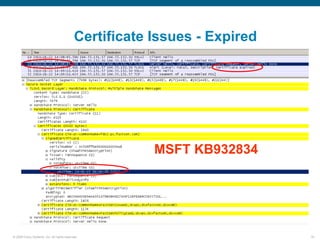
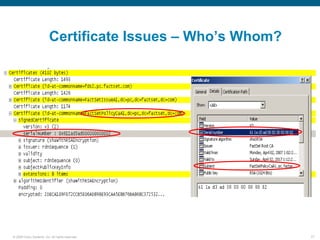
Wireshark is a free and open-source packet analyzer that can be used to capture packets on a network for troubleshooting purposes, with options to filter captures by IP address, port number, or other criteria. Wireshark runs either directly on the device being monitored or by configuring port mirroring on a switch to send traffic to a separate machine running Wireshark. The document discusses different locations and methods for capturing packets both on and off the target device.