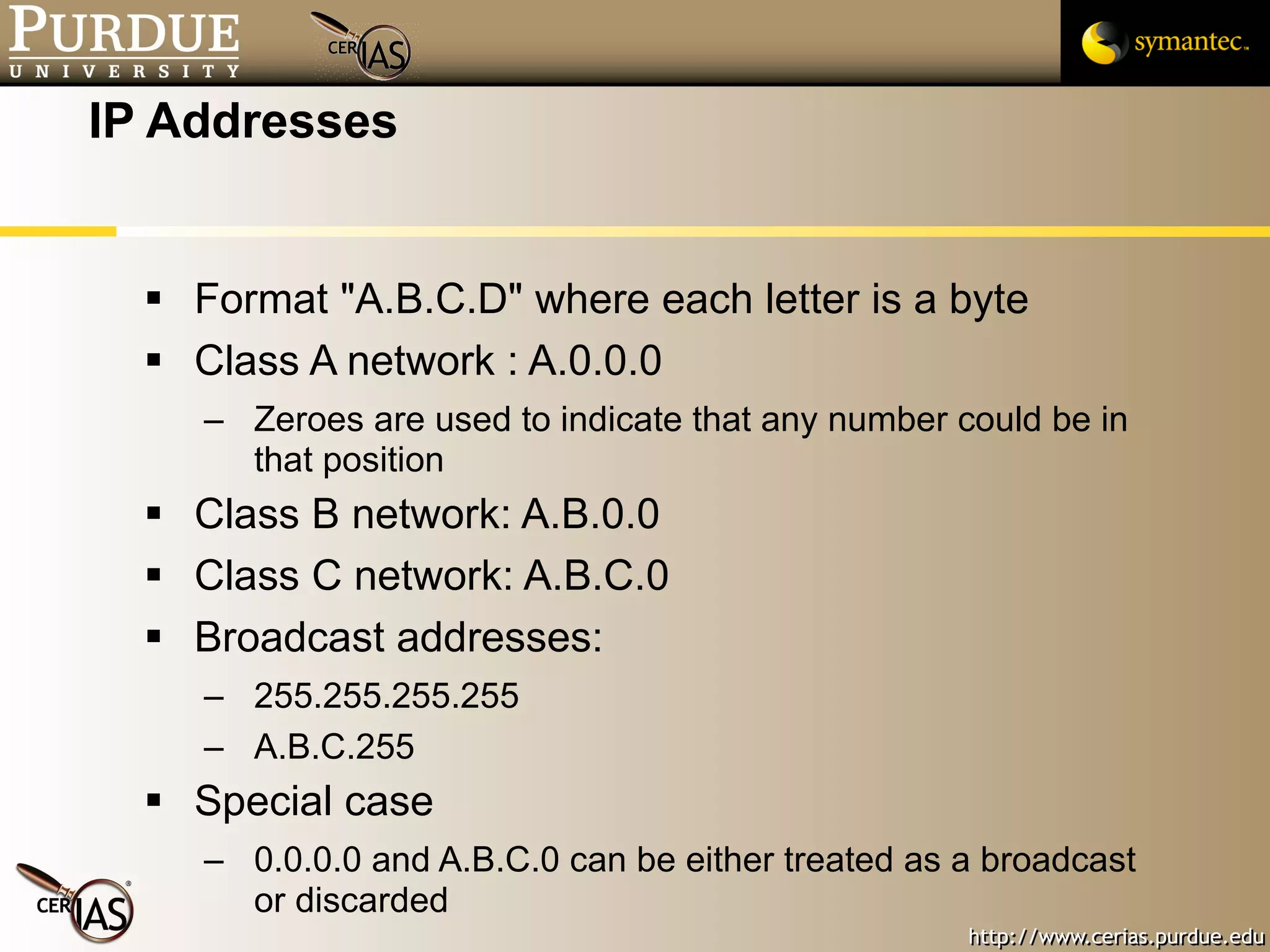
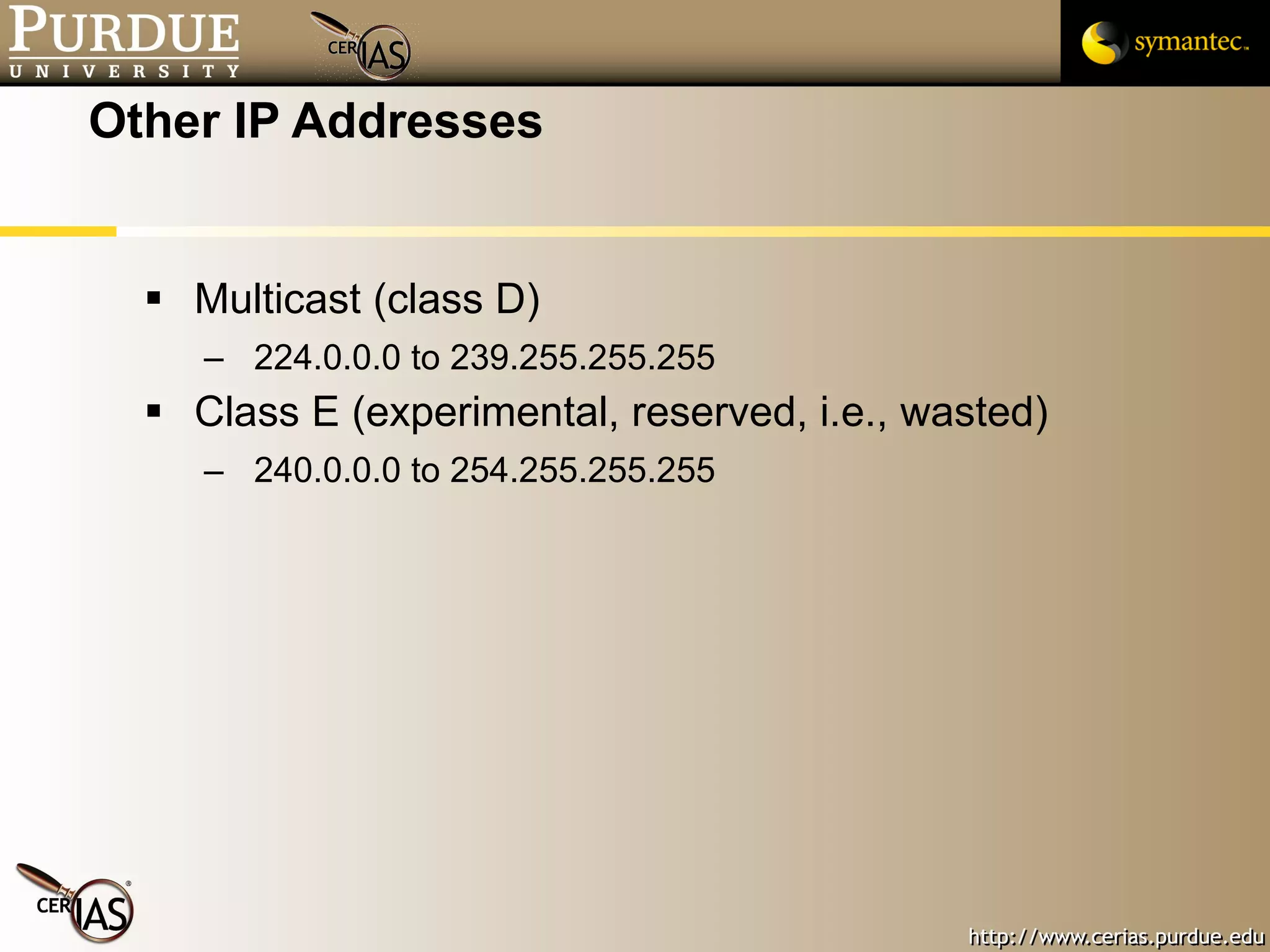
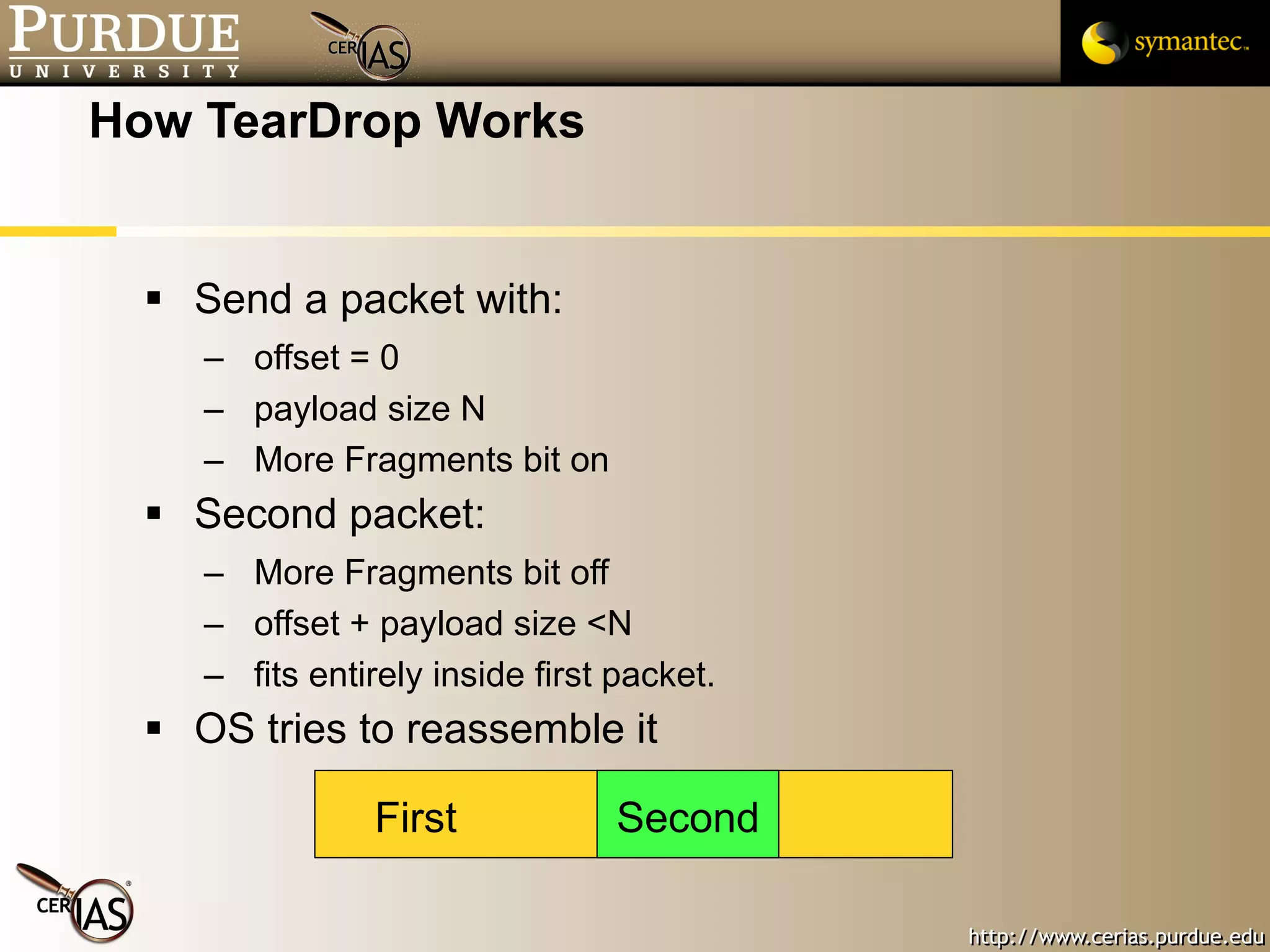
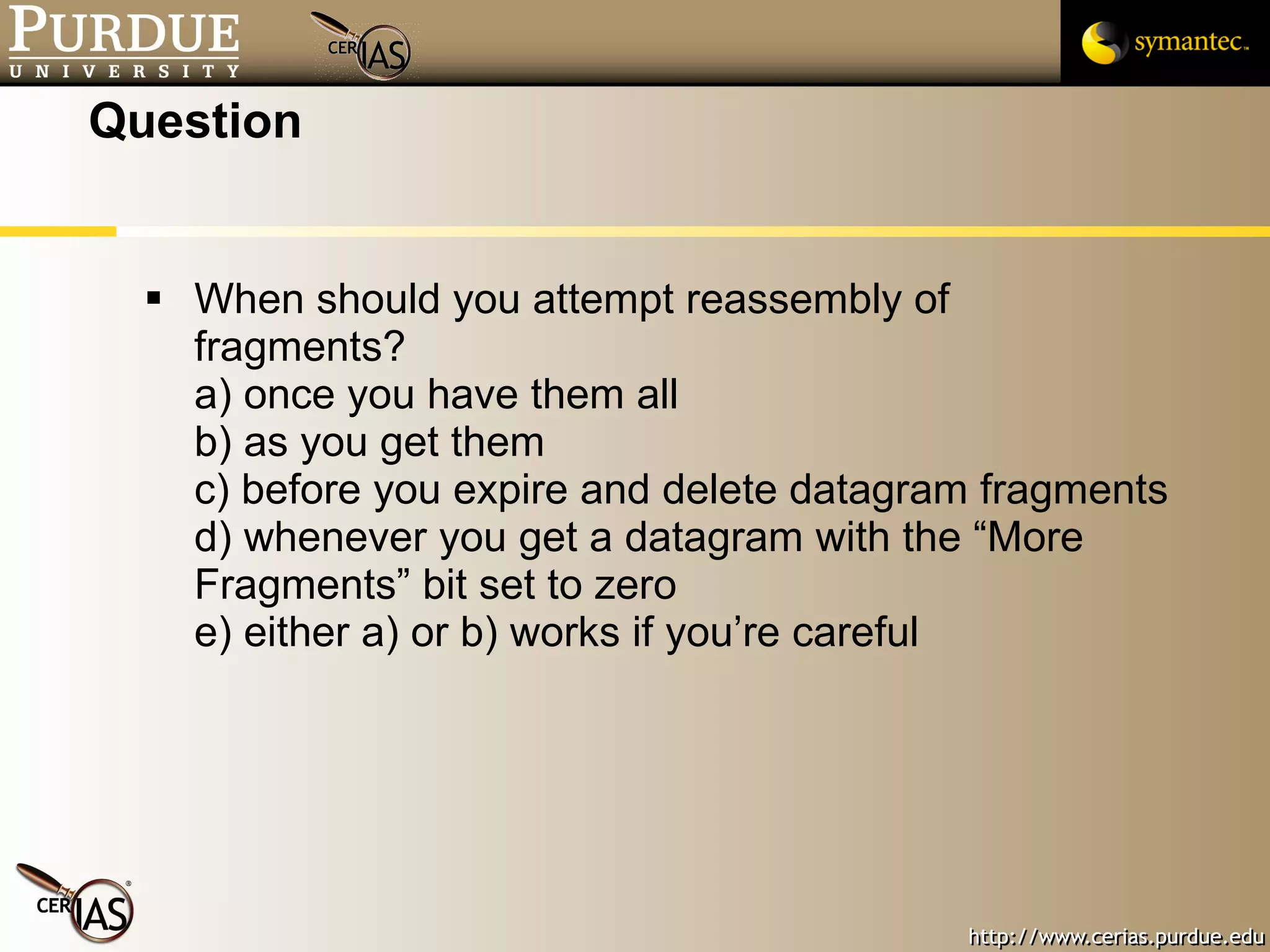
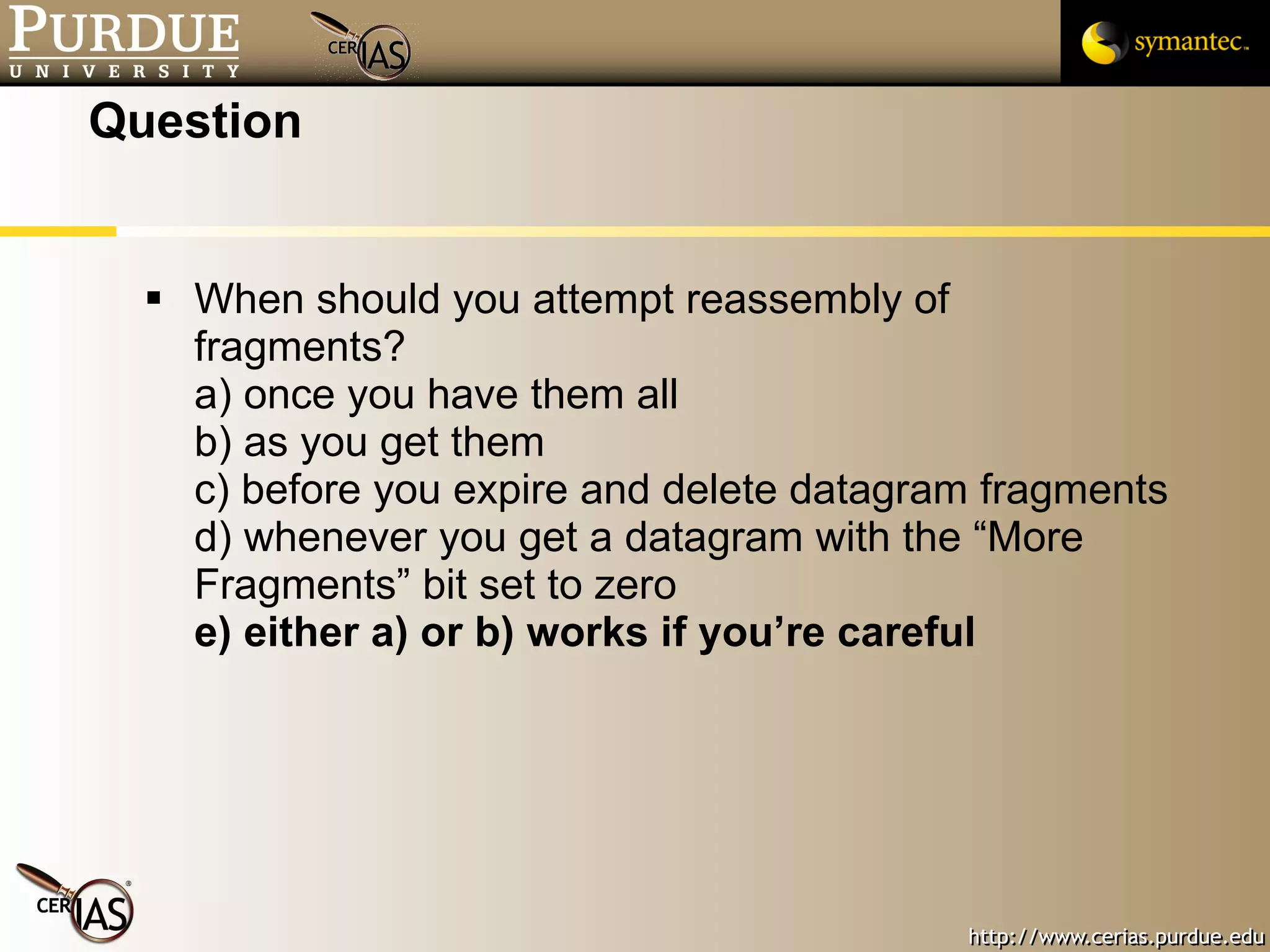
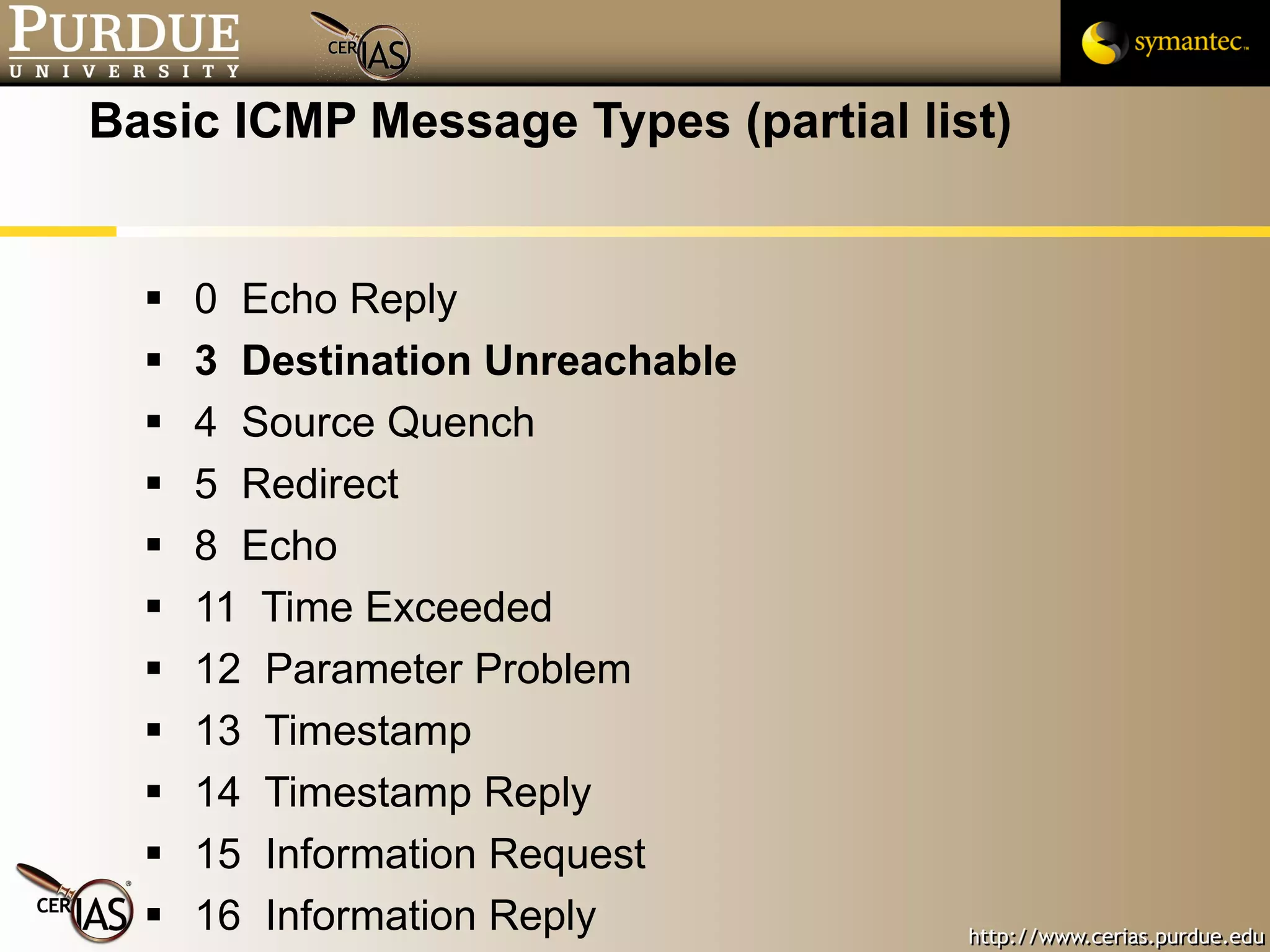
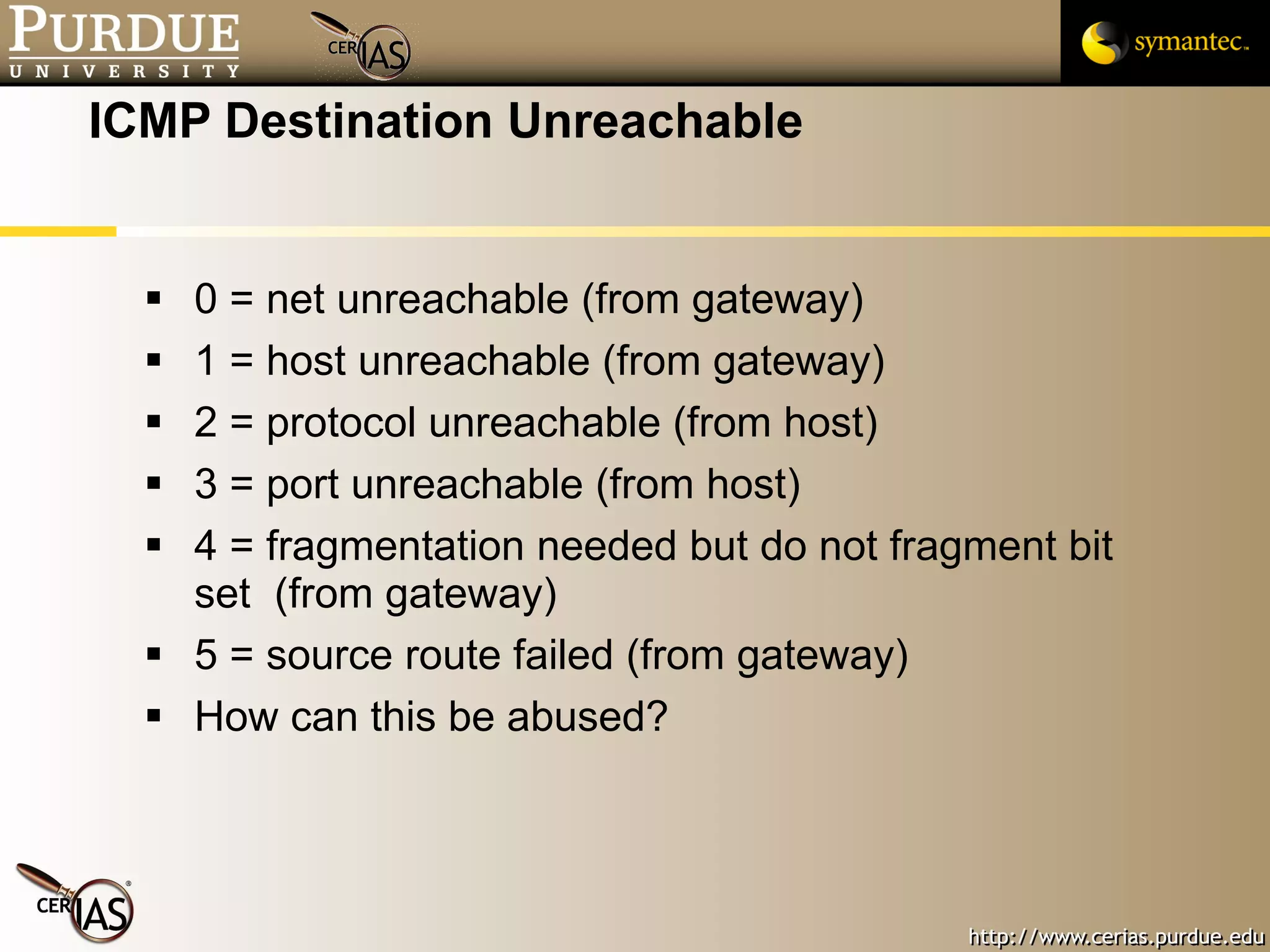
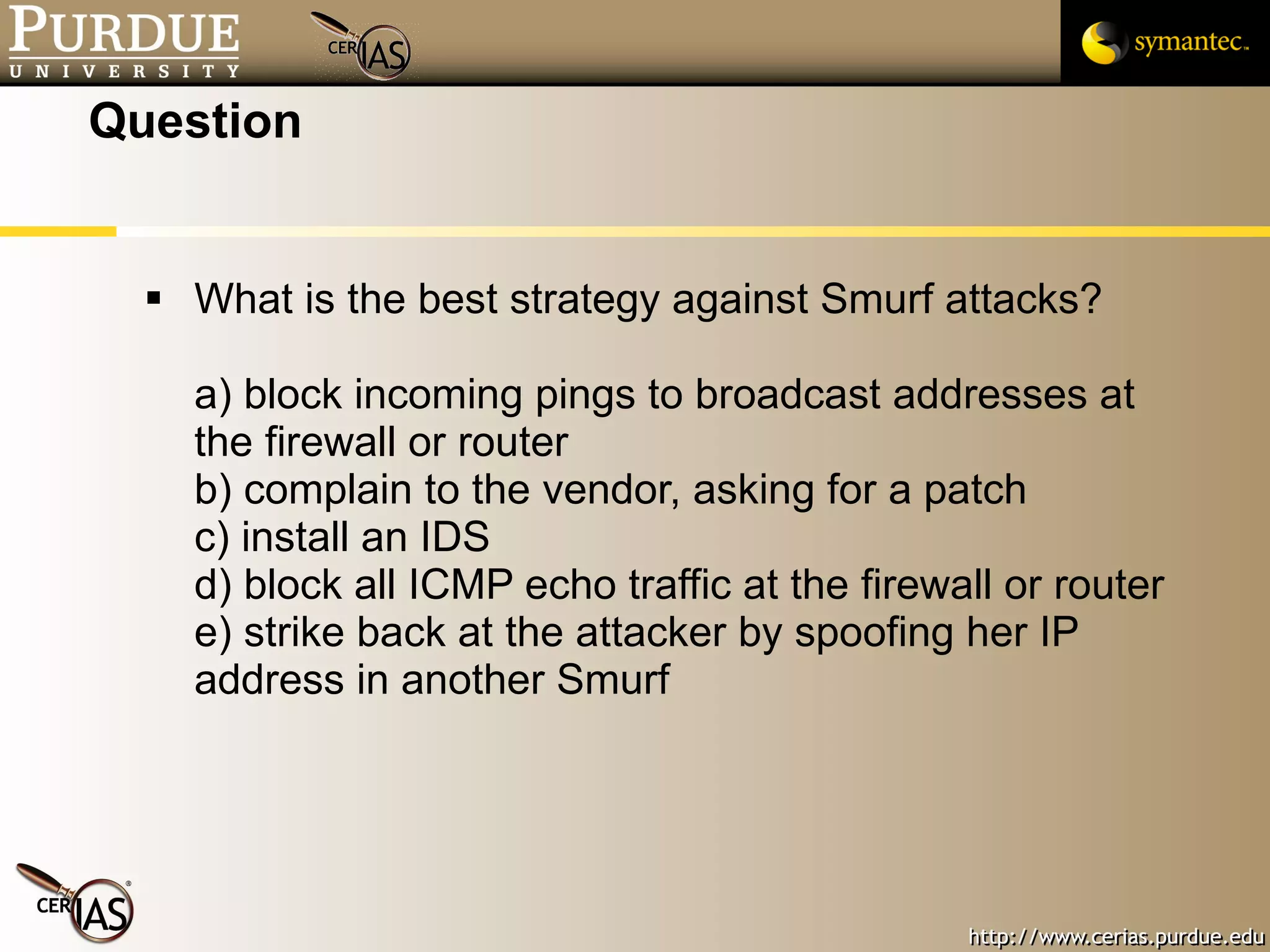
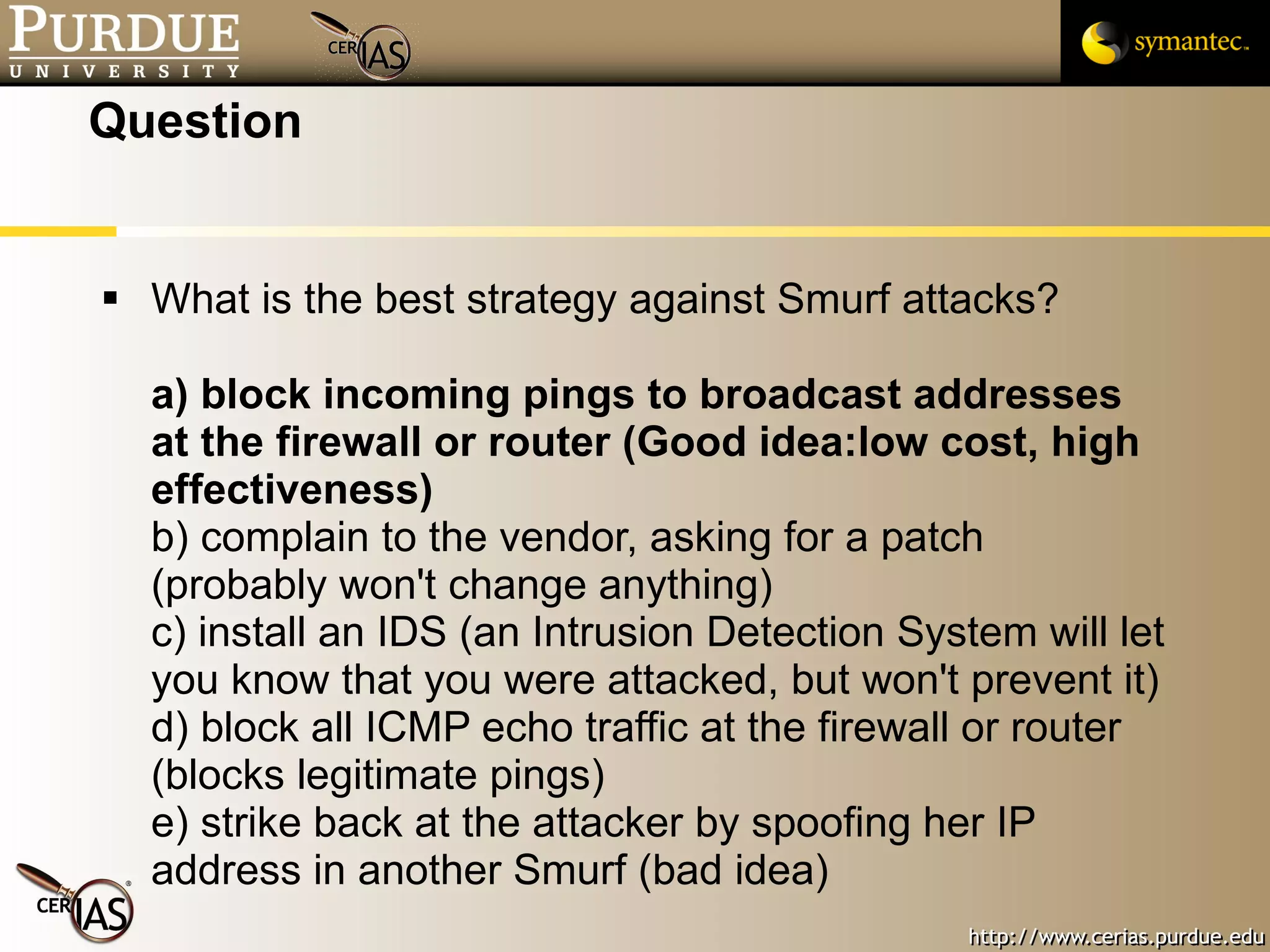
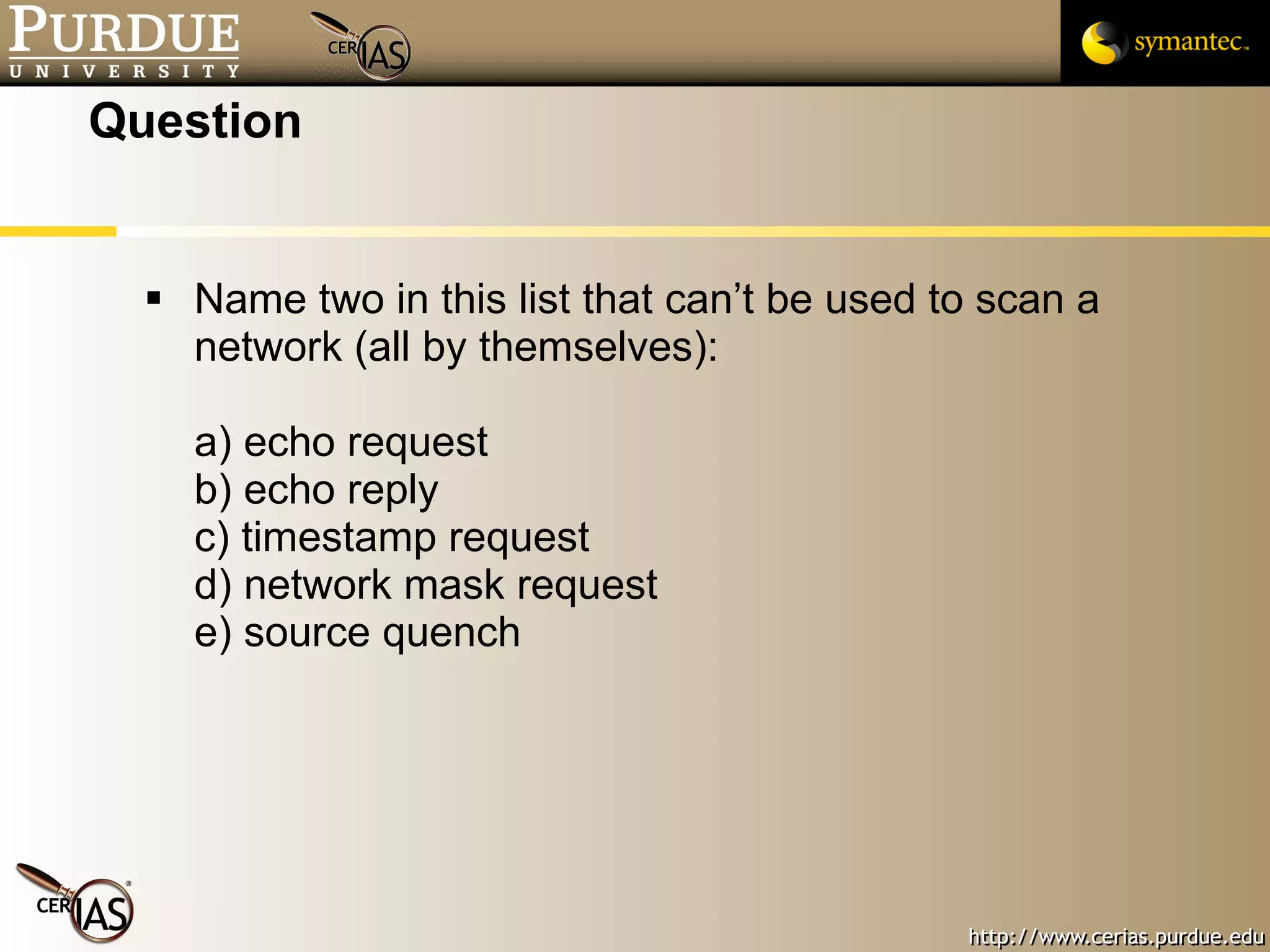
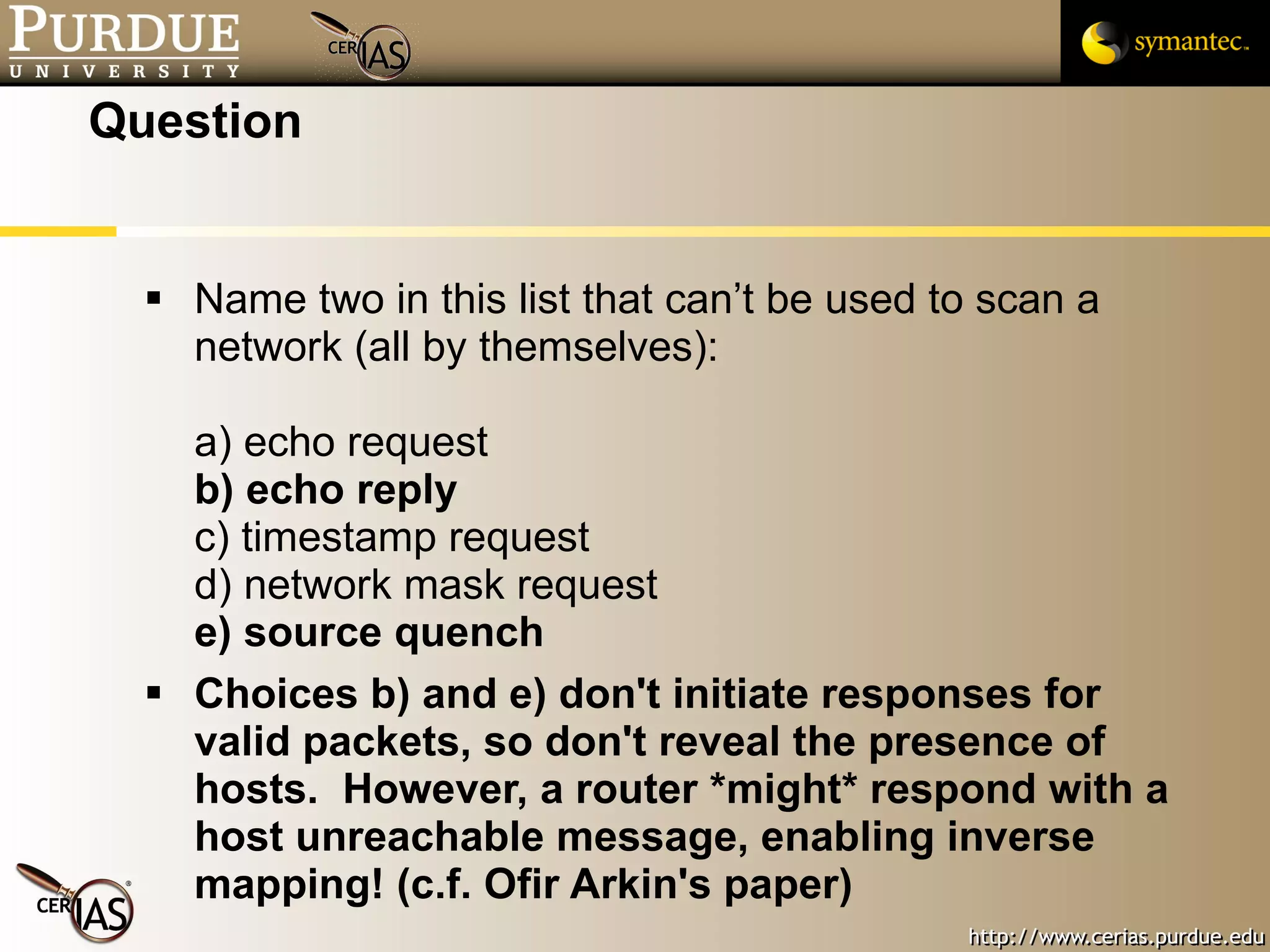
This document provides a summary of key topics in network security including IP addressing, IP spoofing, fragmentation, ICMP messages, and ways these can be abused or pose risks. Specific vulnerabilities discussed include ping flooding using spoofed source addresses for amplification attacks, overlapping IP fragments that can crash systems, and abusing ICMP unreachable messages to poison routing tables or disrupt connectivity. Safe practices like egress filtering and carefully handling fragmented packets are recommended.




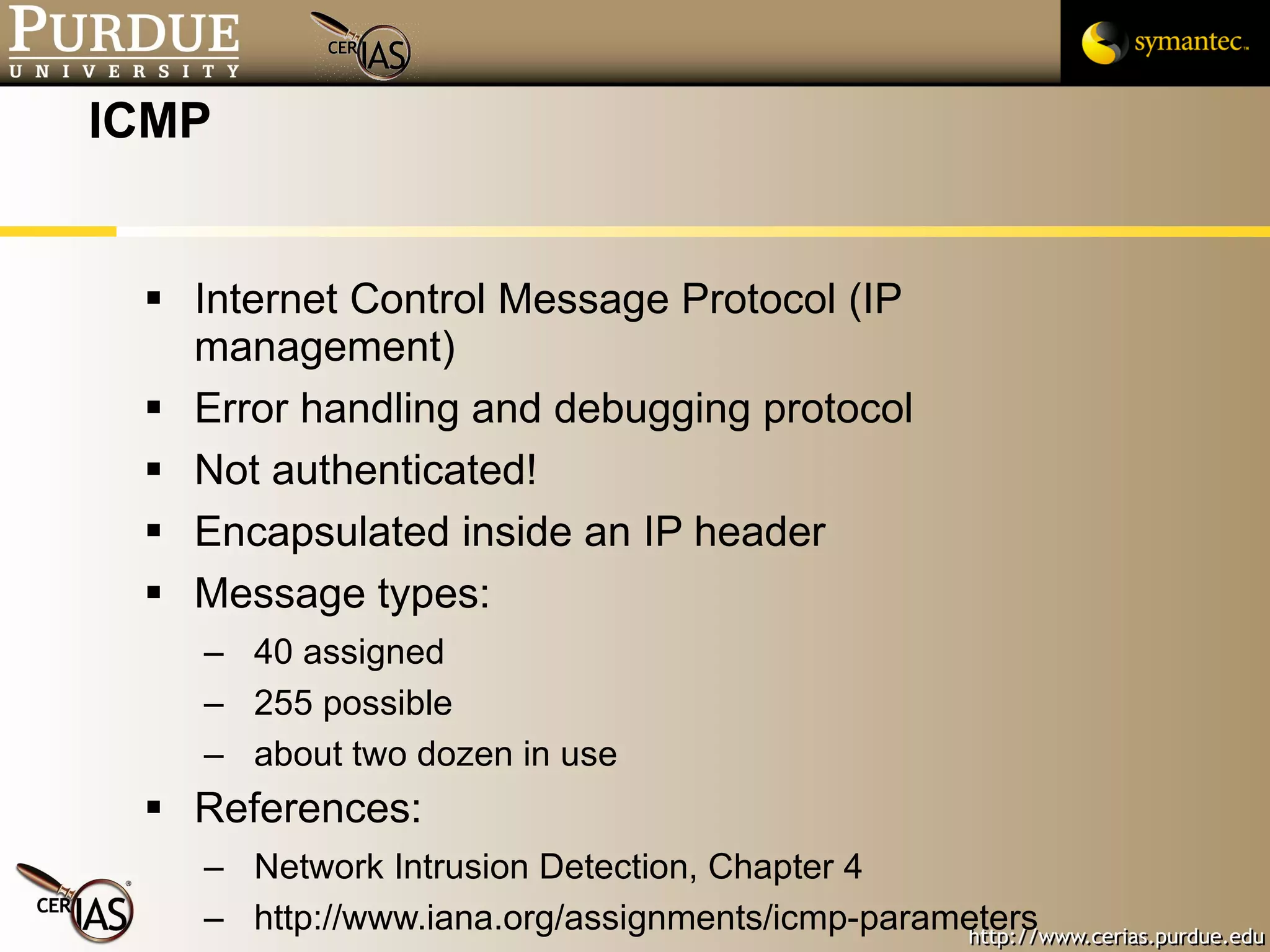
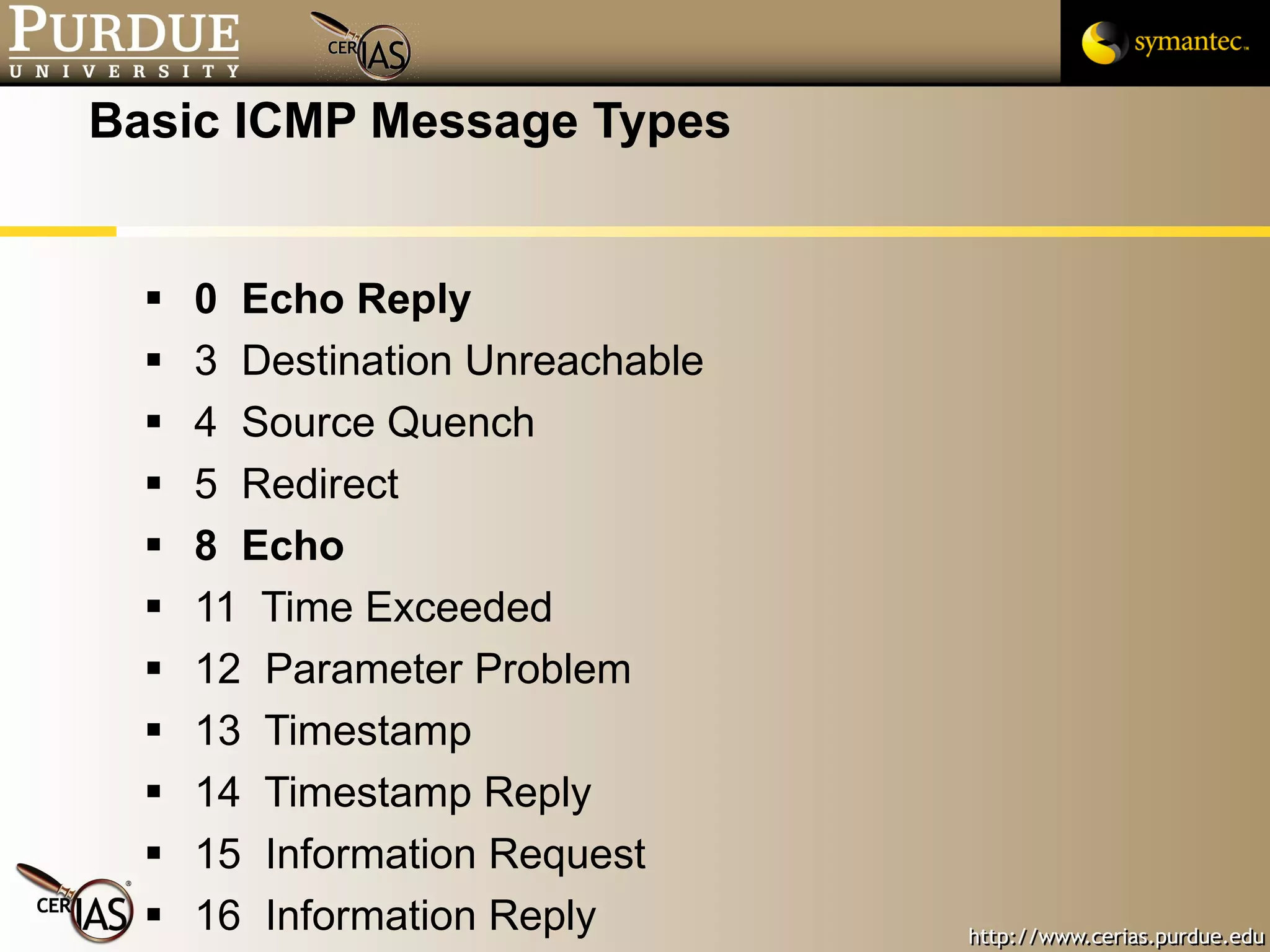
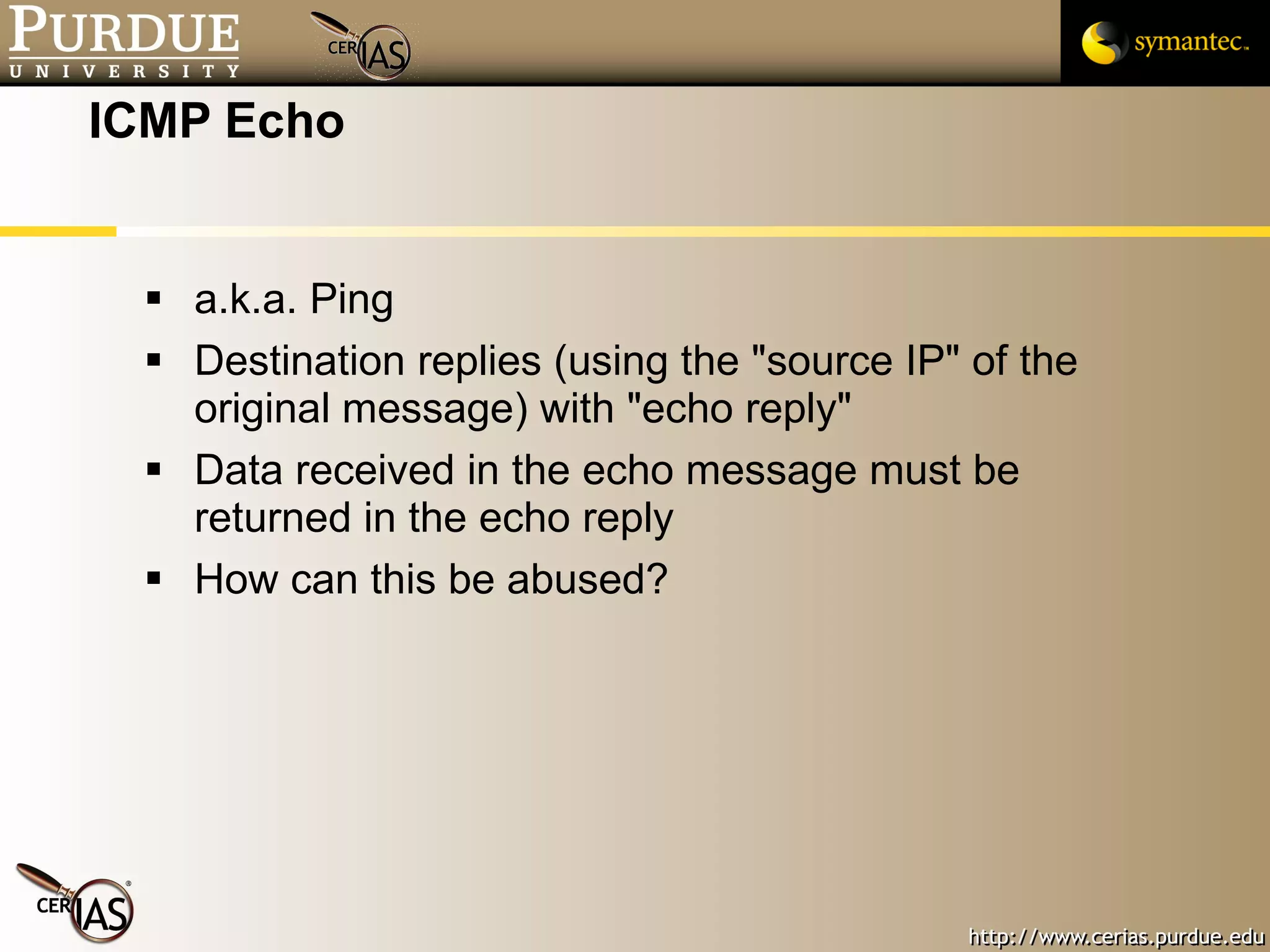





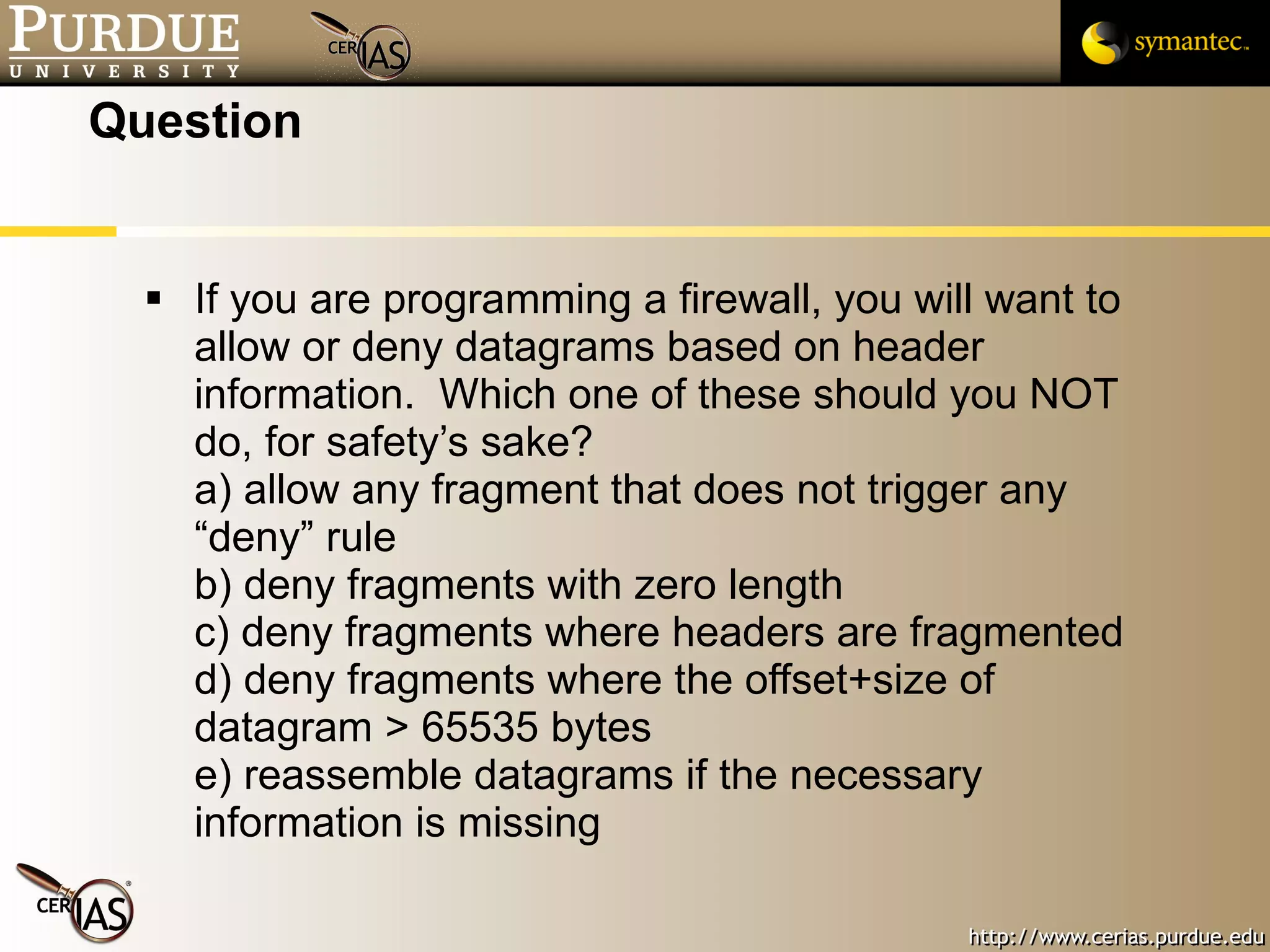
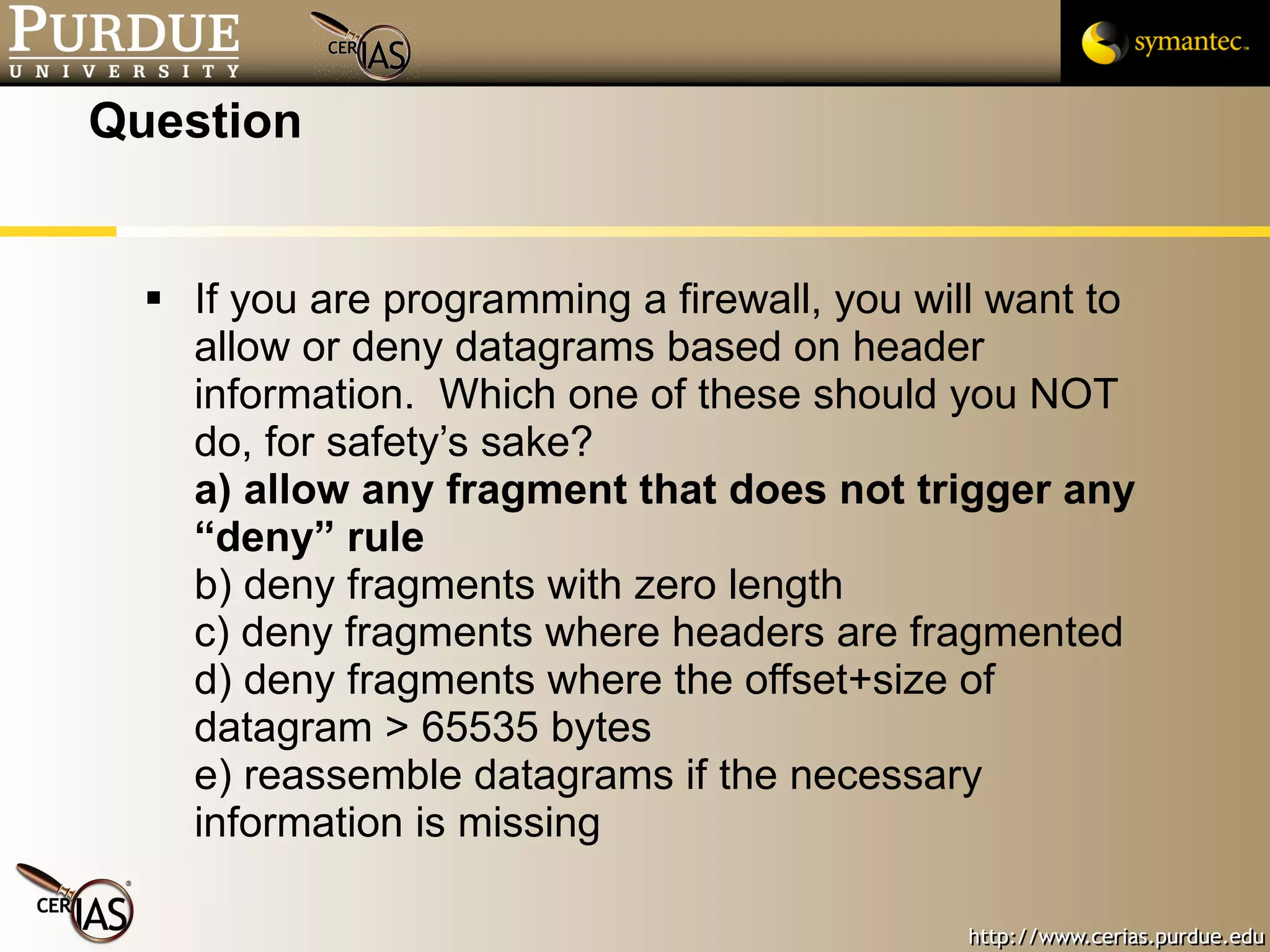
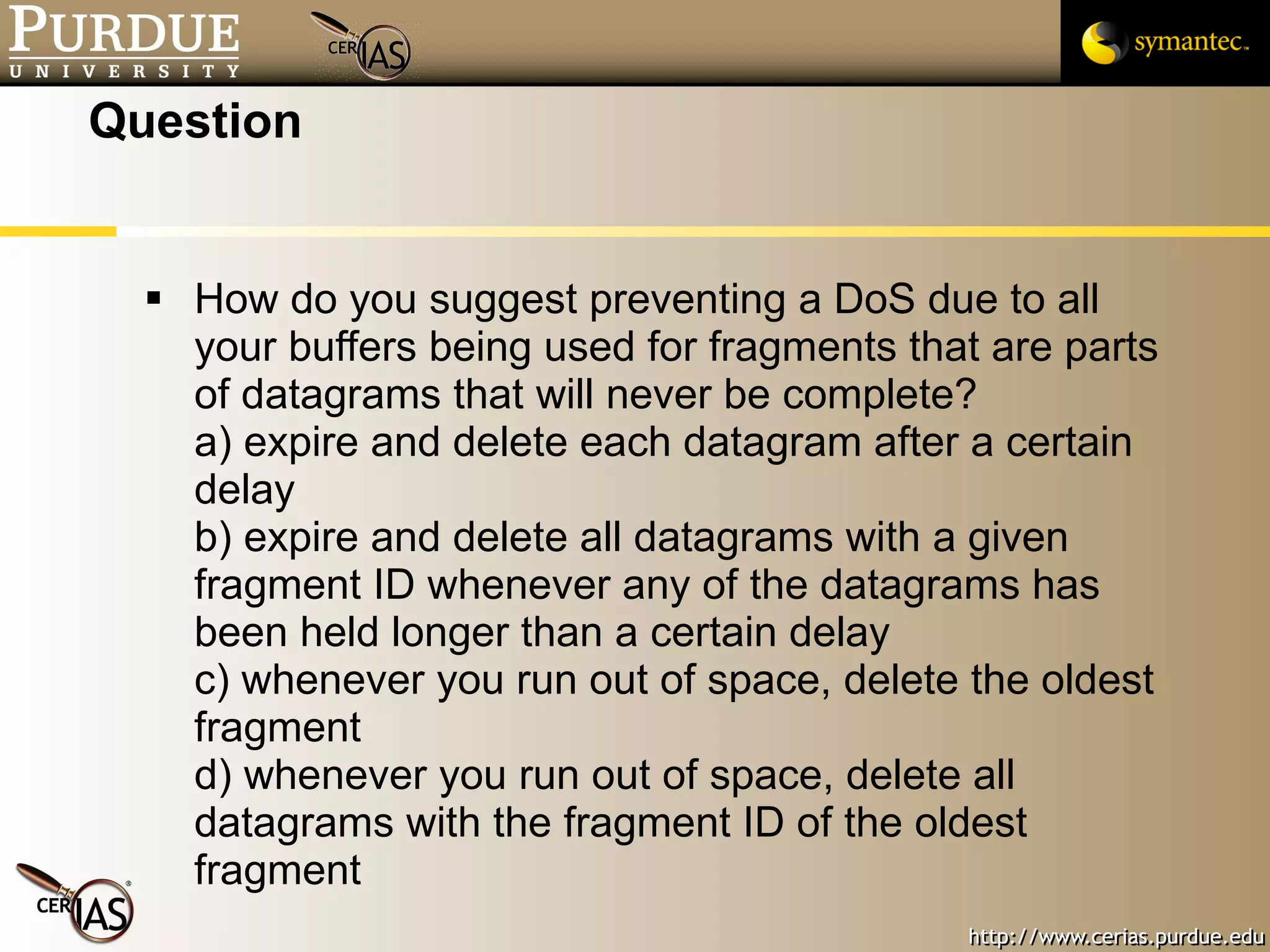
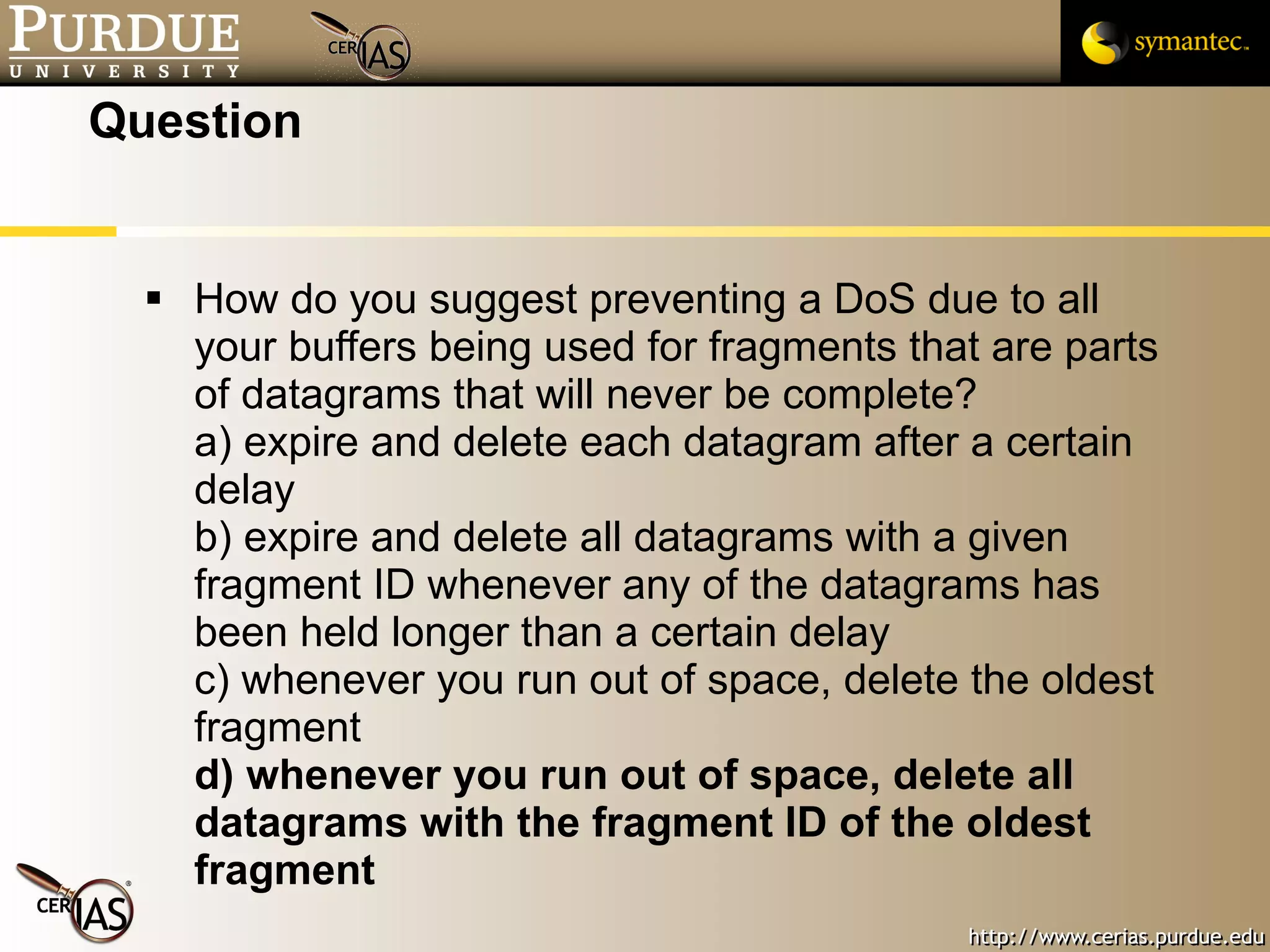


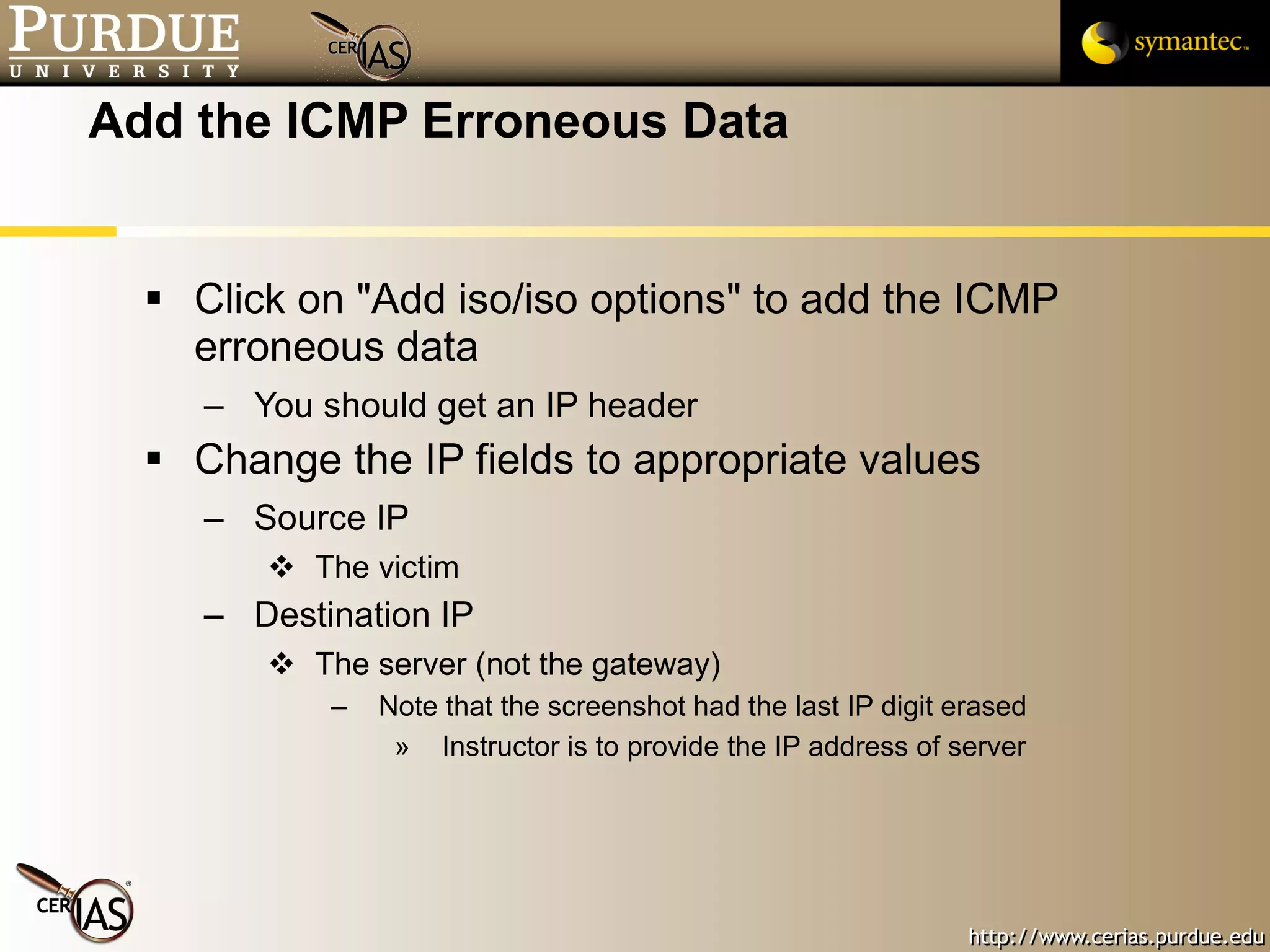
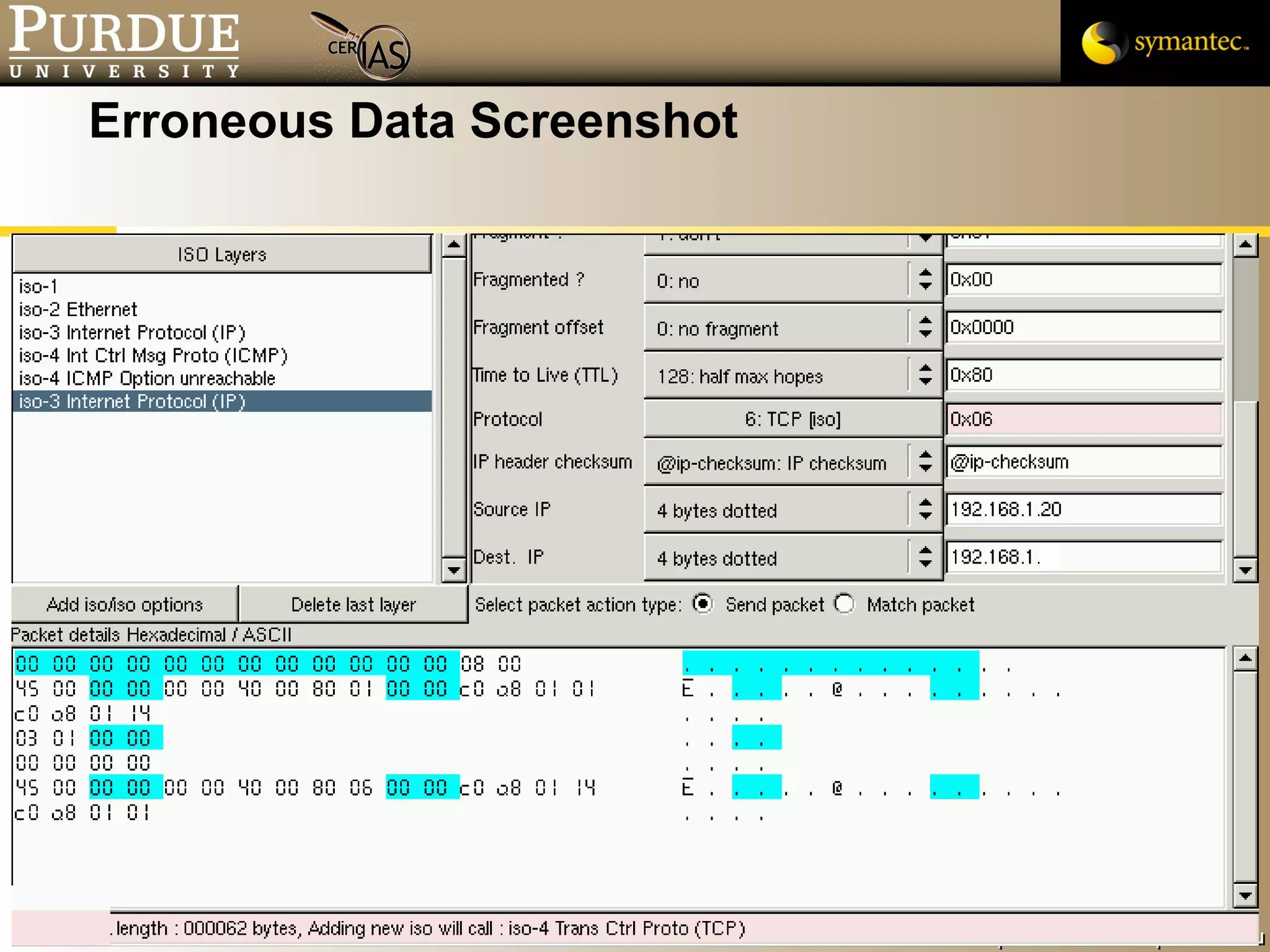
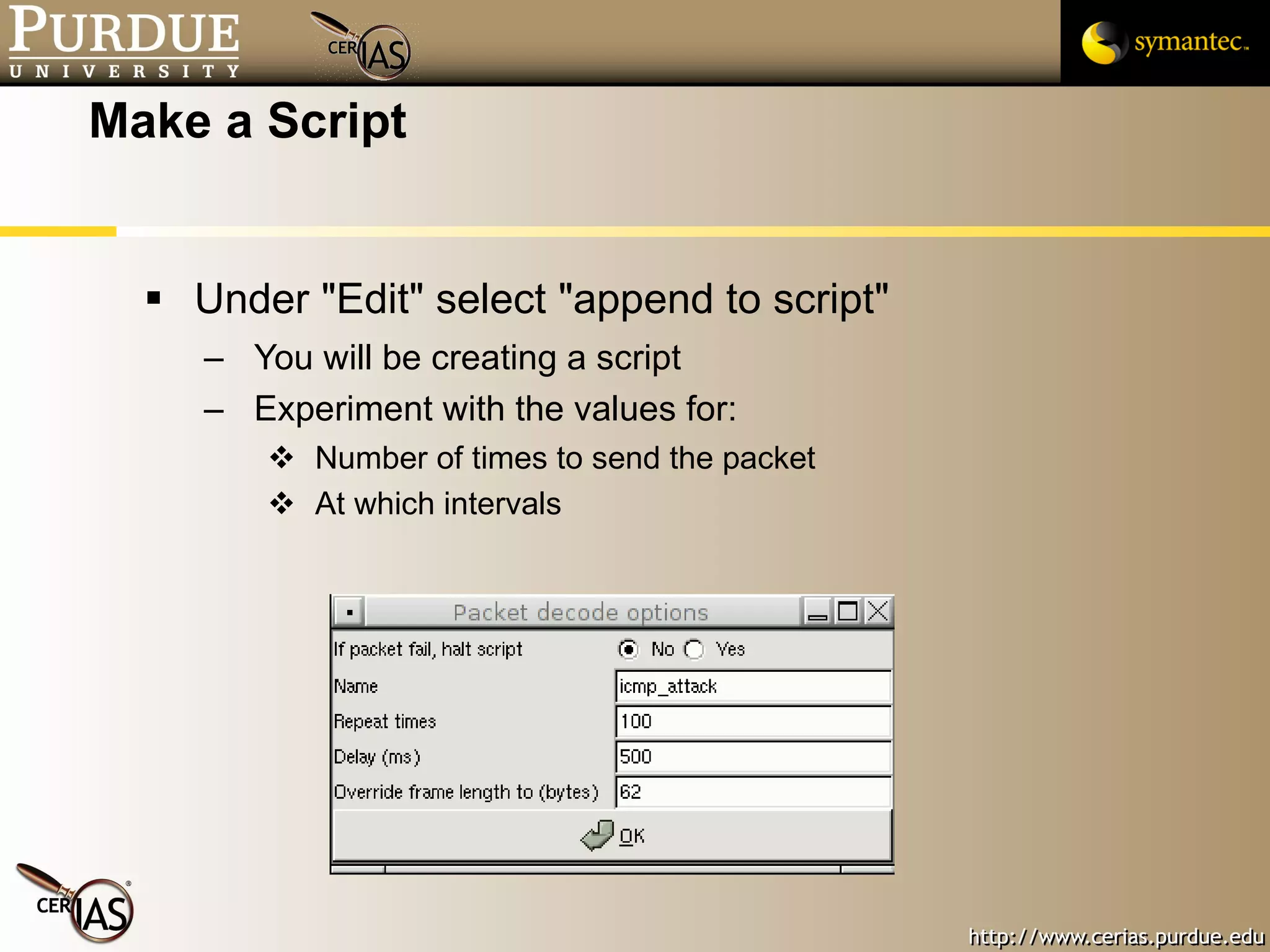
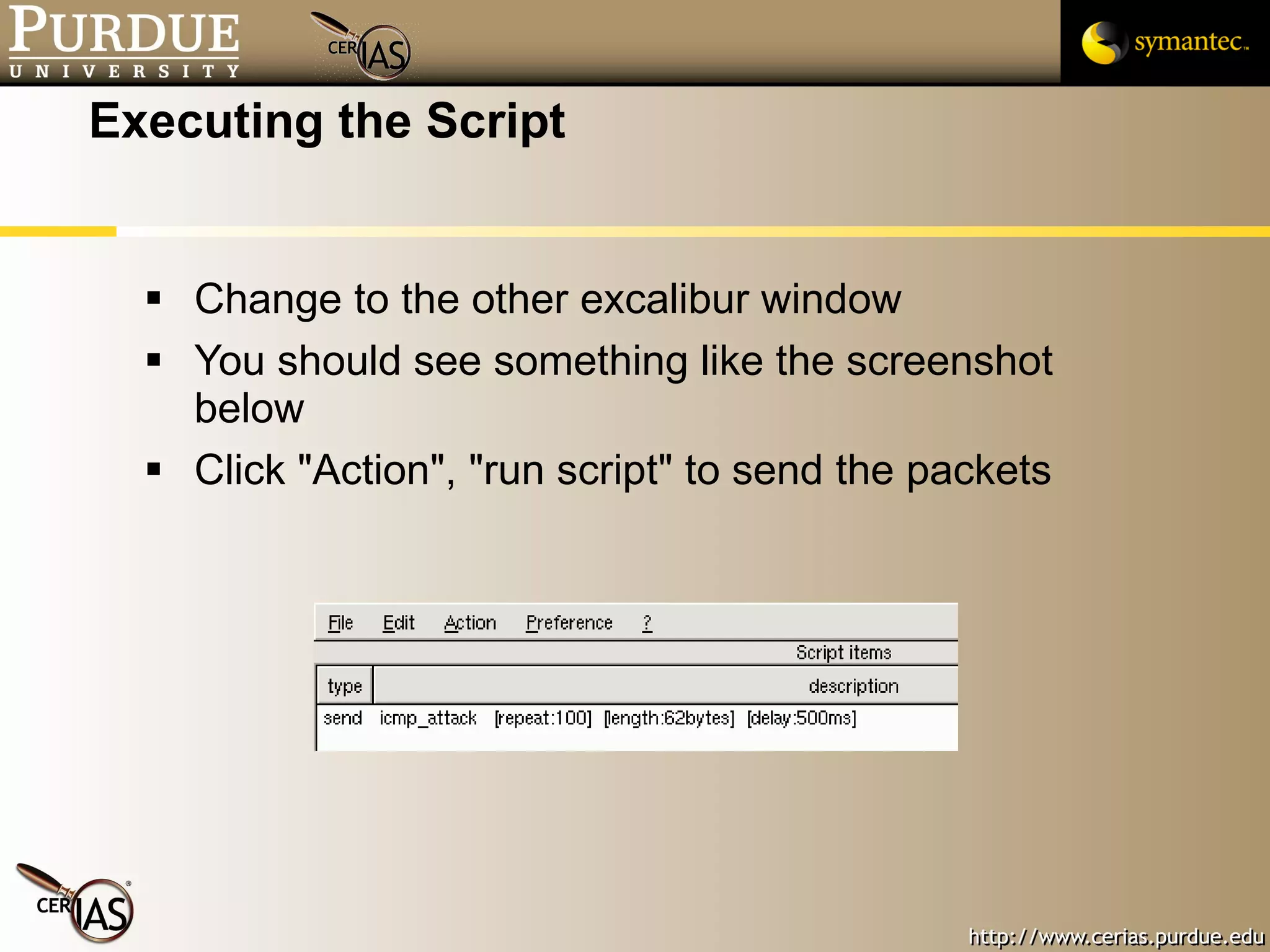
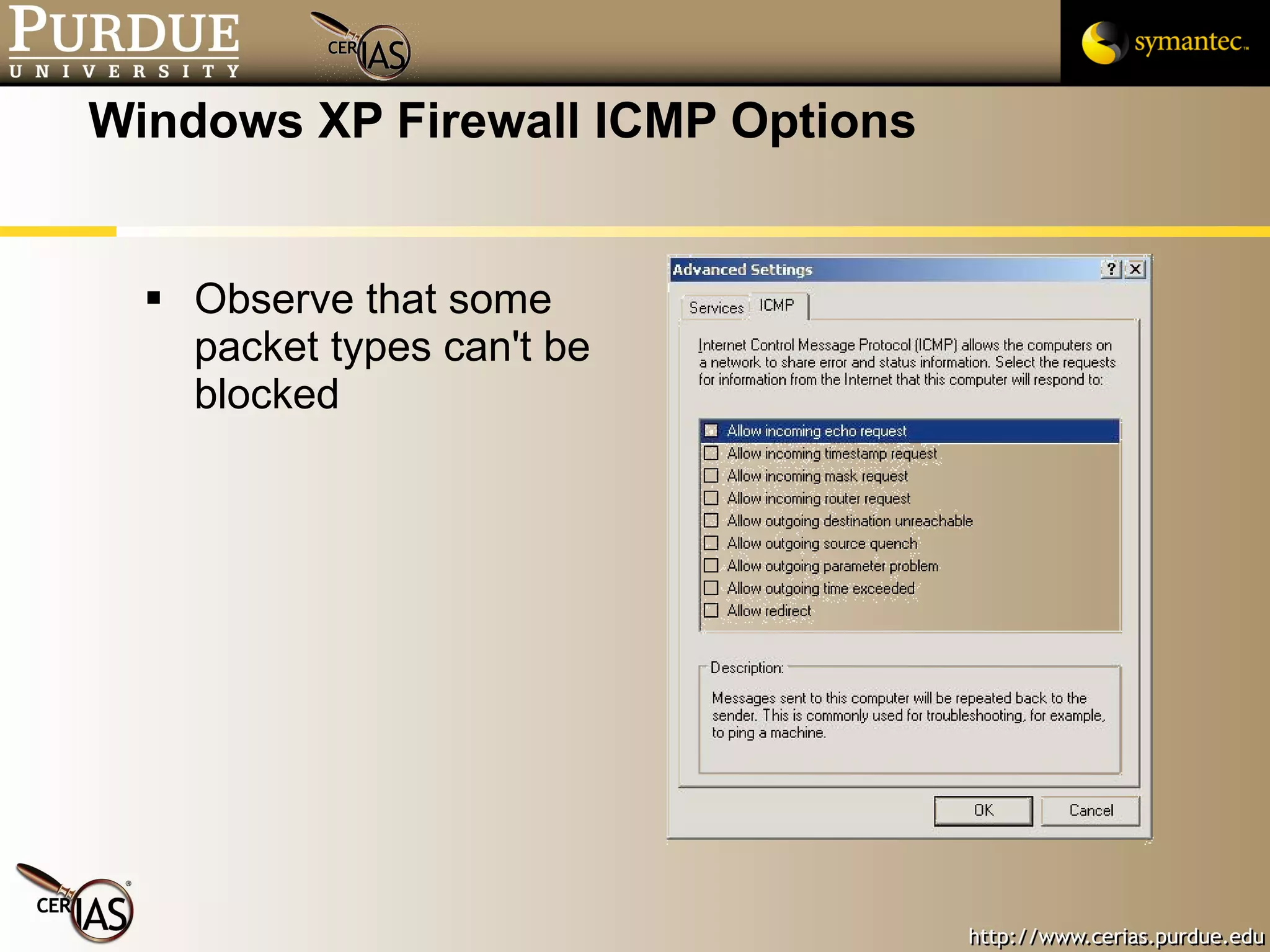
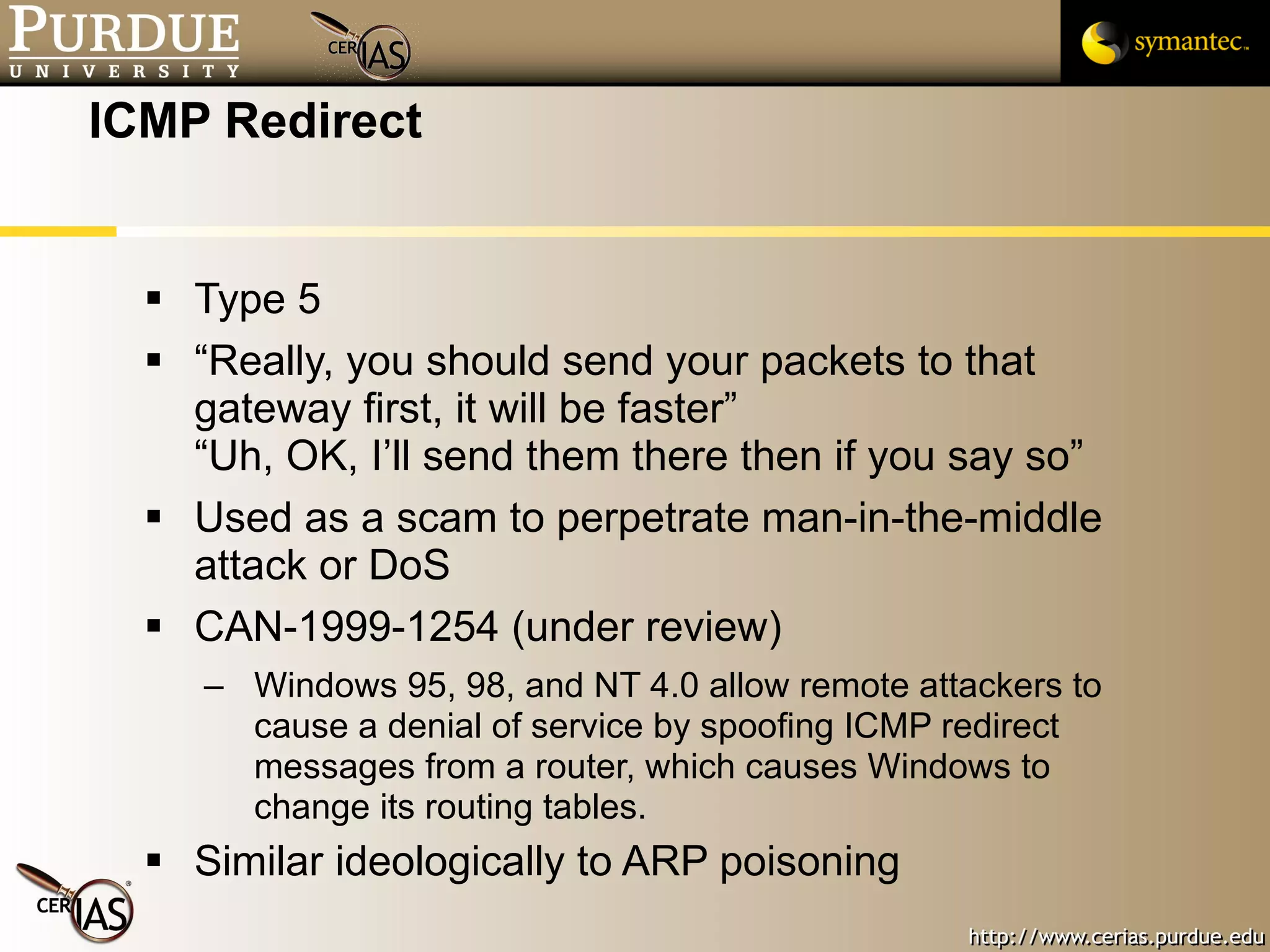
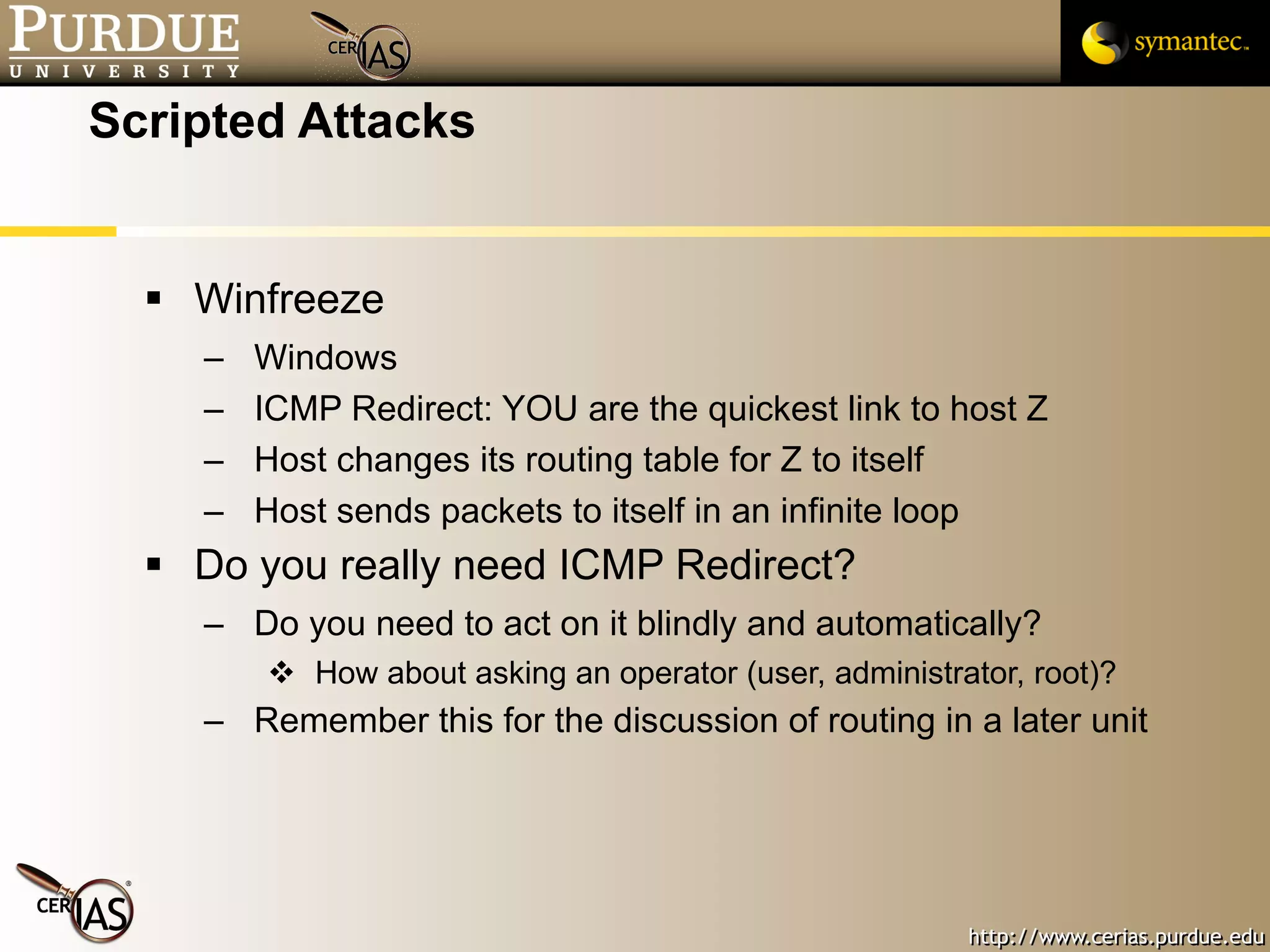
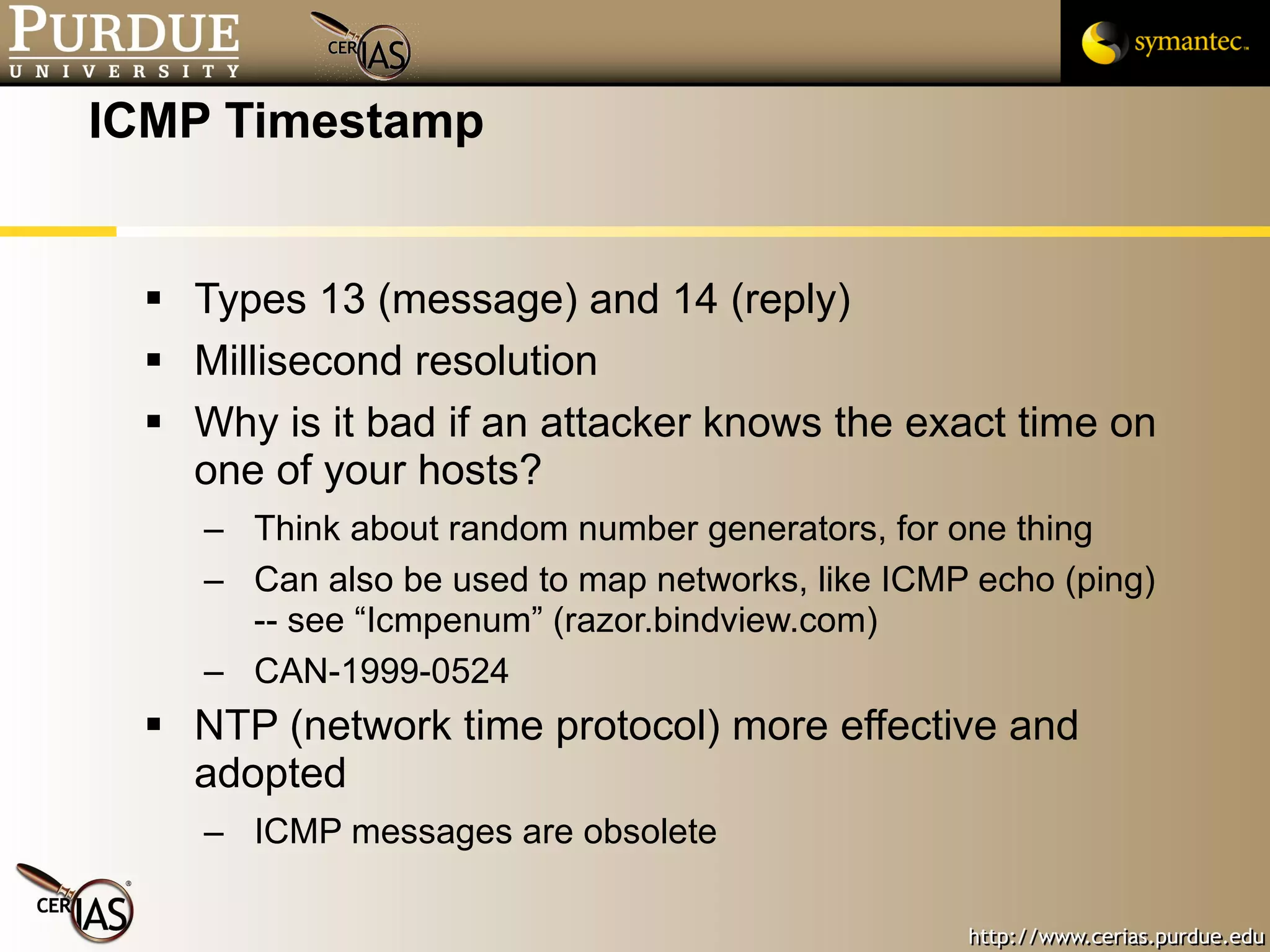
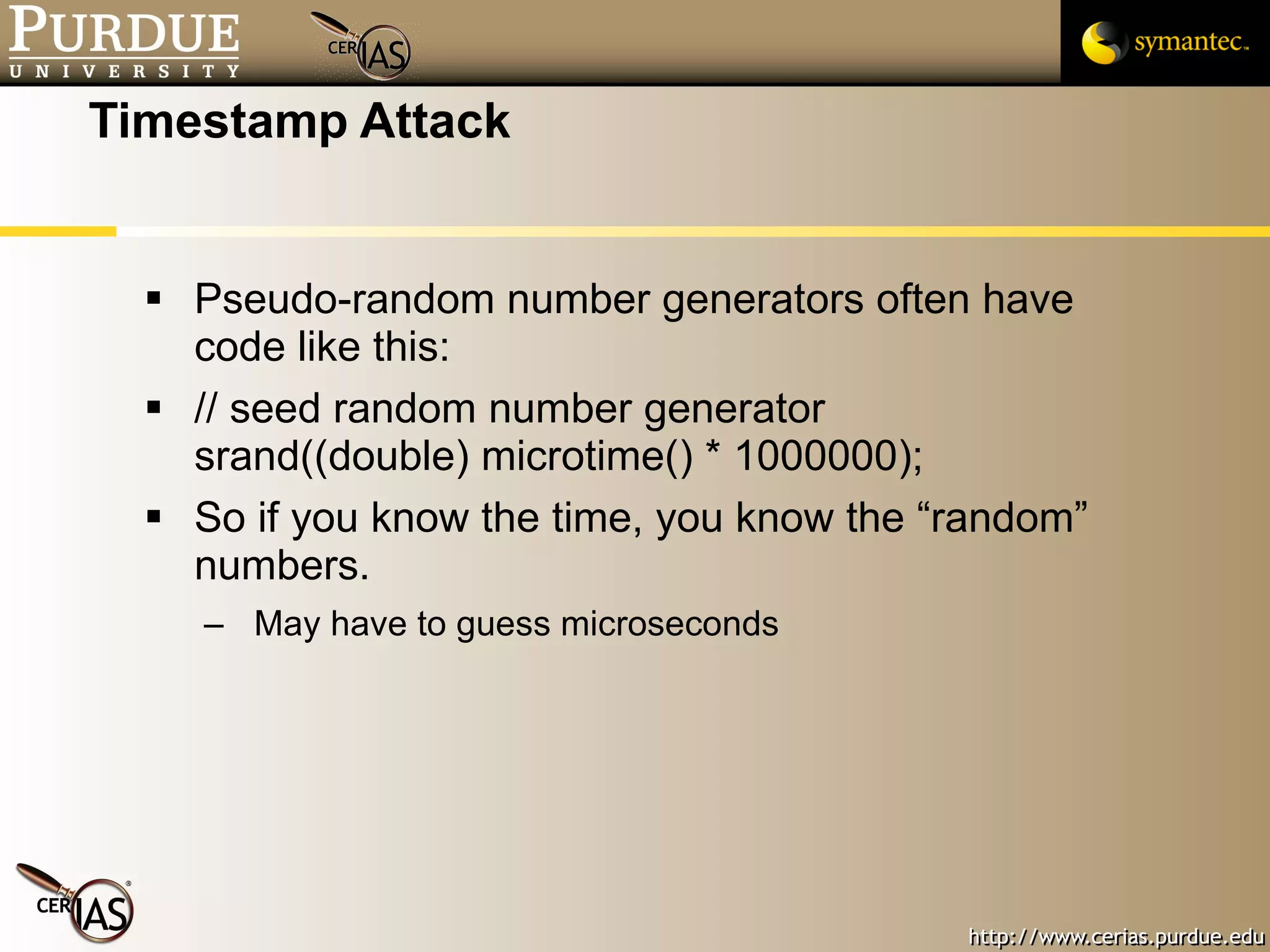


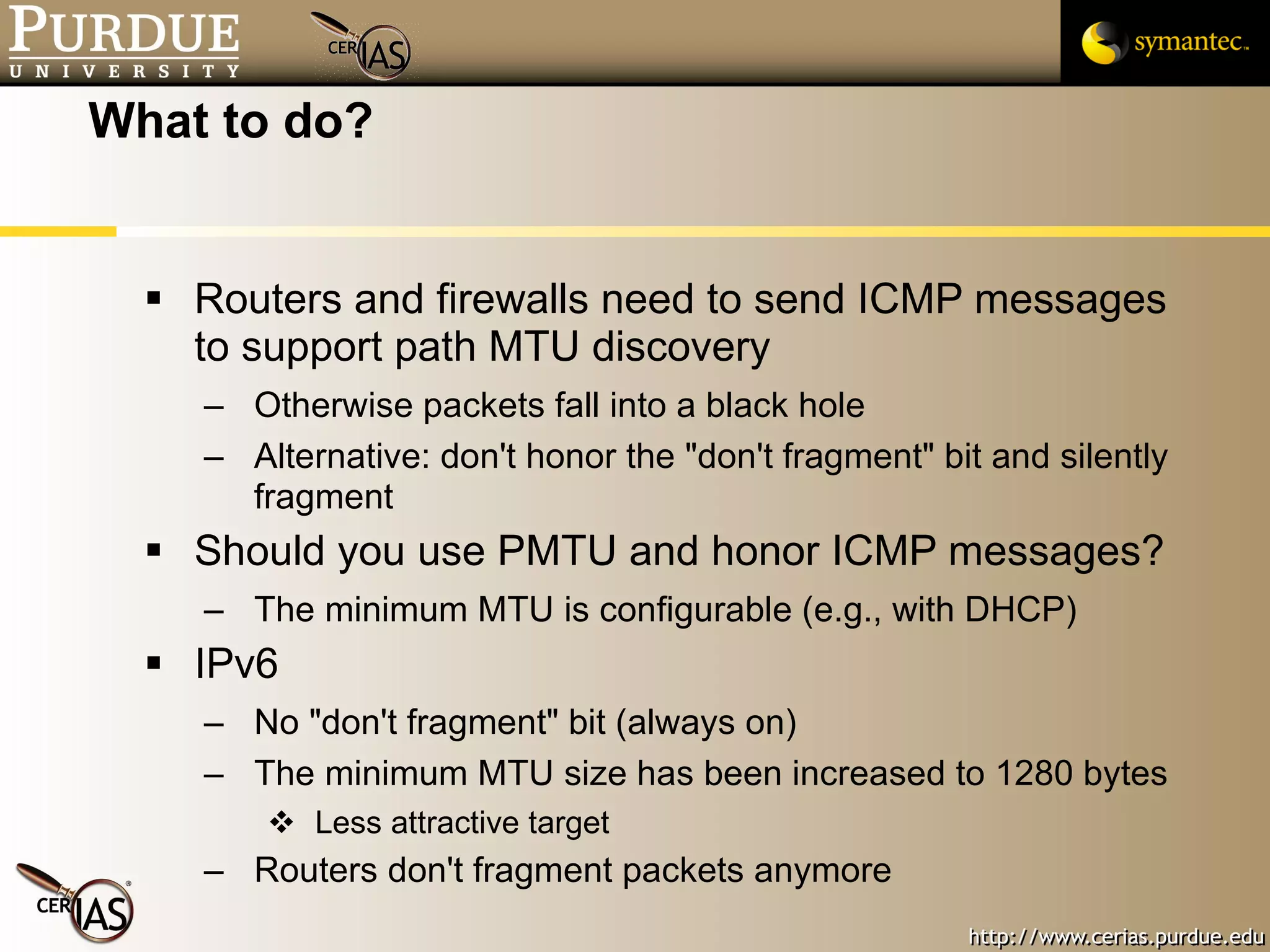
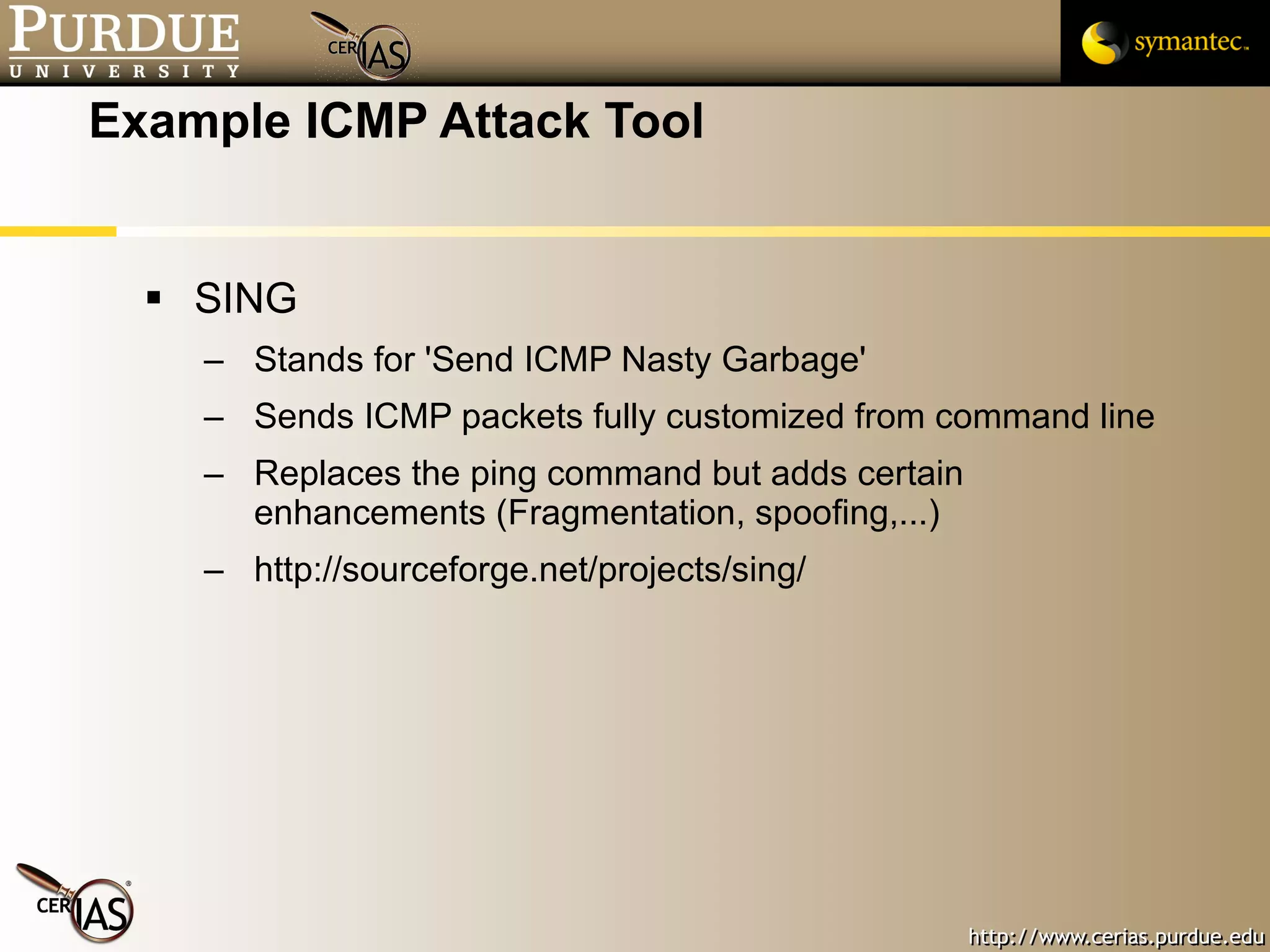
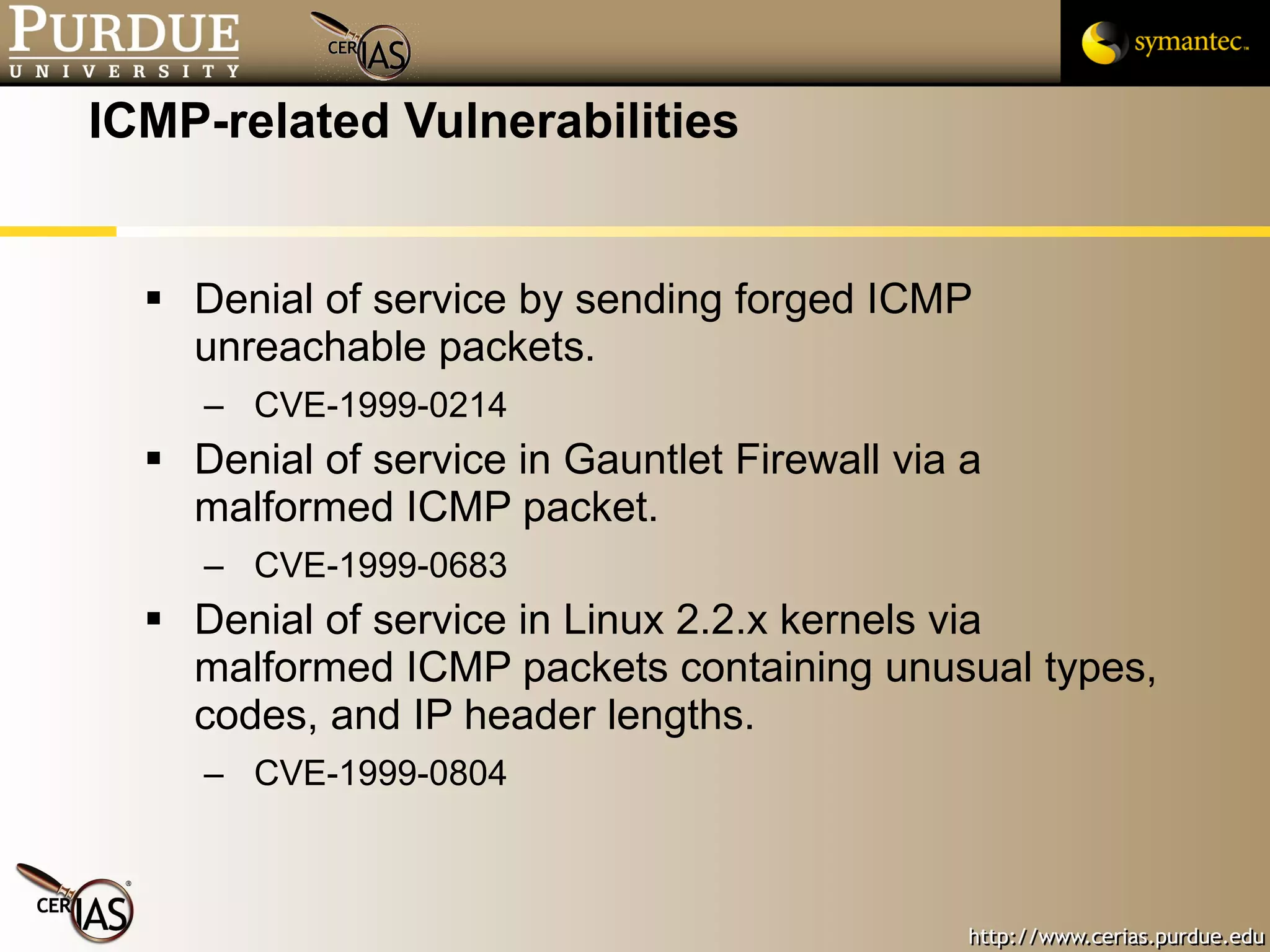
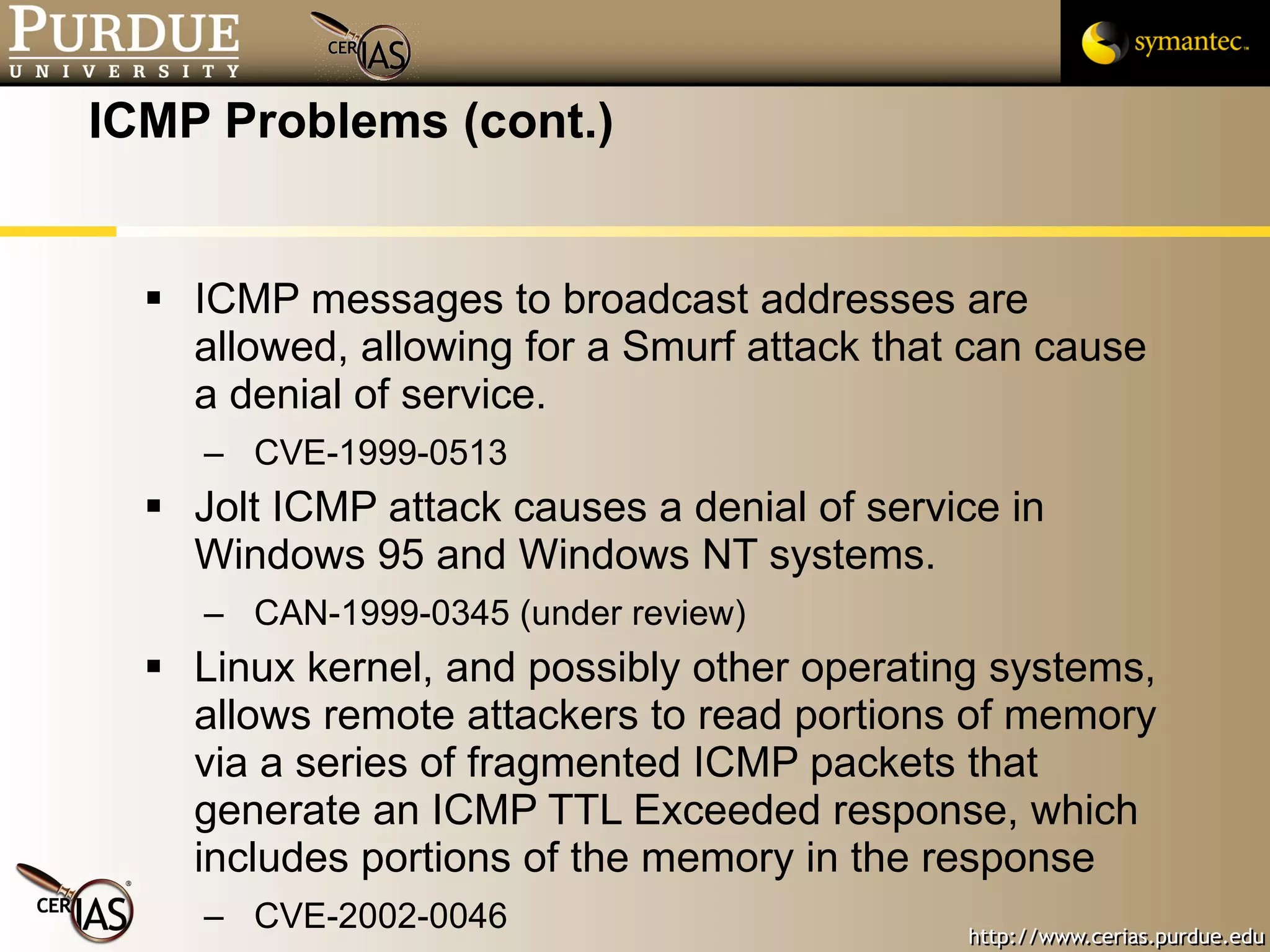

![Pascal Meunier [email_address] Contributors: Jared Robinson, Alan Krassowski, Craig Ozancin, Tim Brown, Wes Higaki, Melissa Dark, Chris Clifton, Gustavo Rodriguez-Rivera](https://image.slidesharecdn.com/3-network-091013224341-phpapp02/75/3-Network-114-2048.jpg)