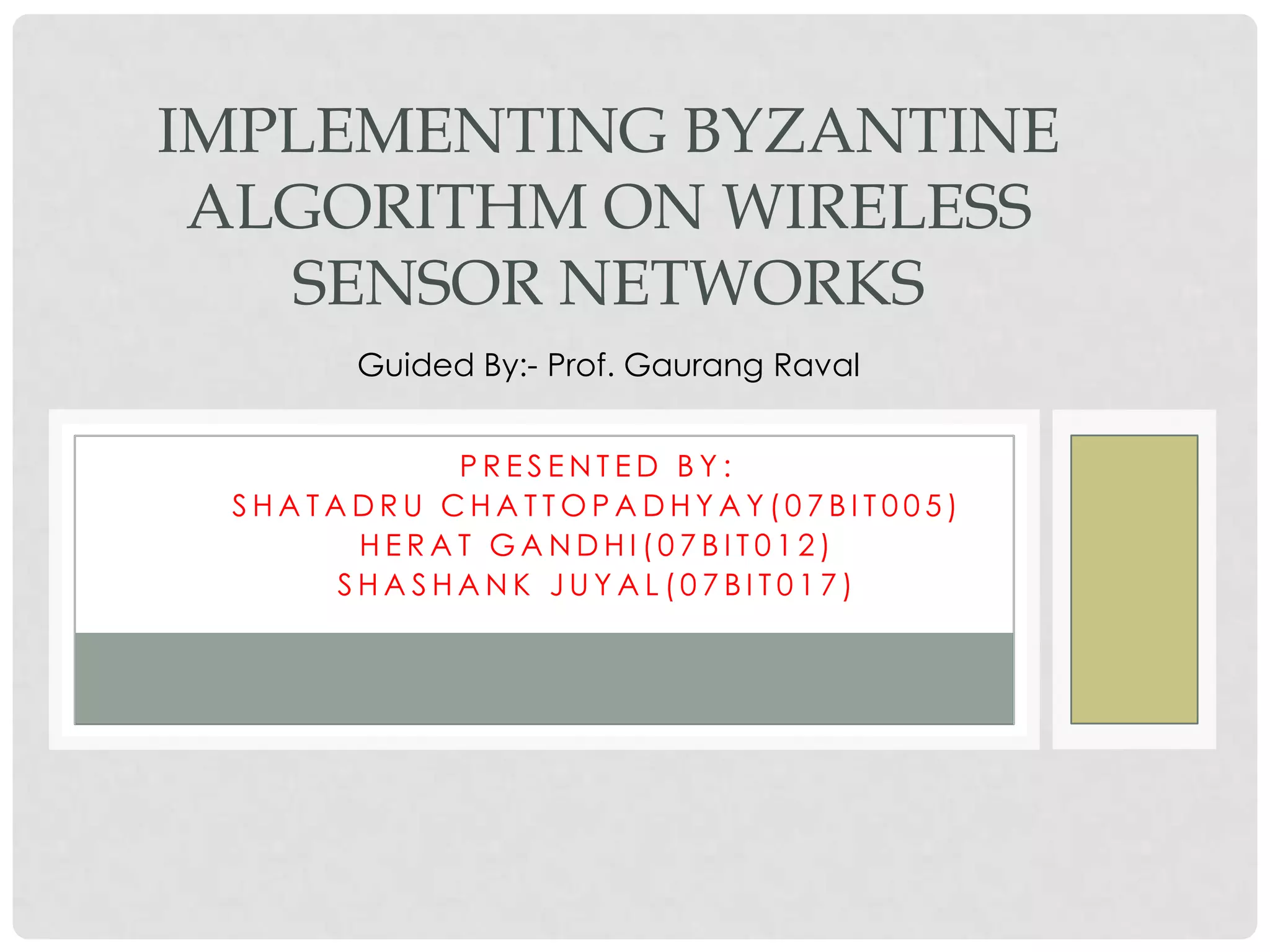
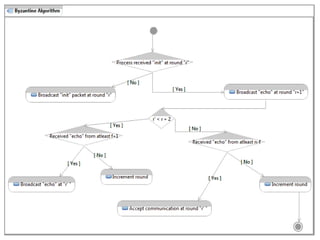
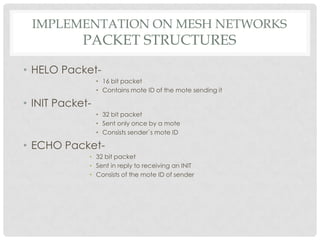
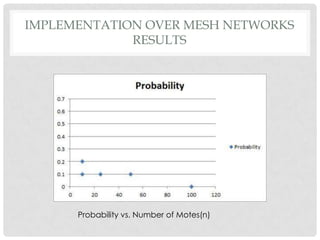
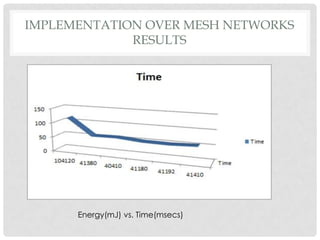
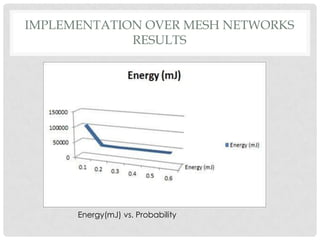
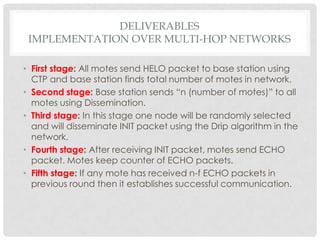
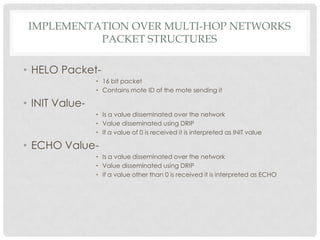
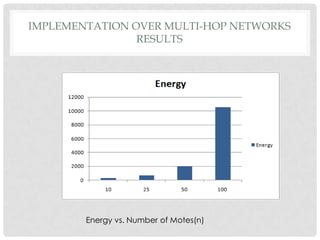
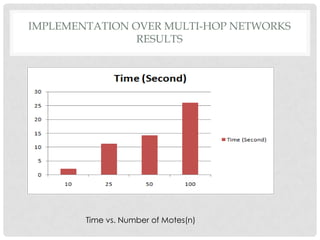
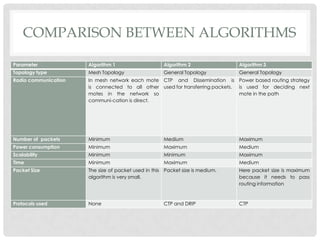
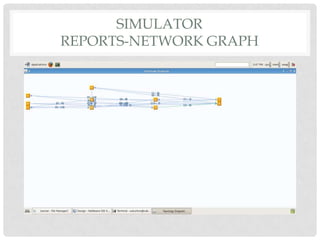
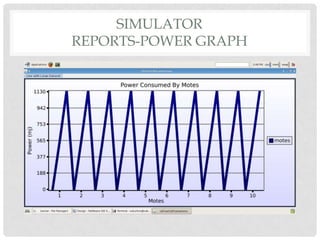
The document discusses the implementation of the Byzantine Fault Tolerant algorithm in wireless sensor networks, detailing the goals, constraints, and procedures for its execution on both mesh and multi-hop network configurations. It covers the technologies used, including simulations and practical demonstrations, as well as comparisons between different algorithms. Future improvements and a cloud computing extension for the simulator are also suggested.