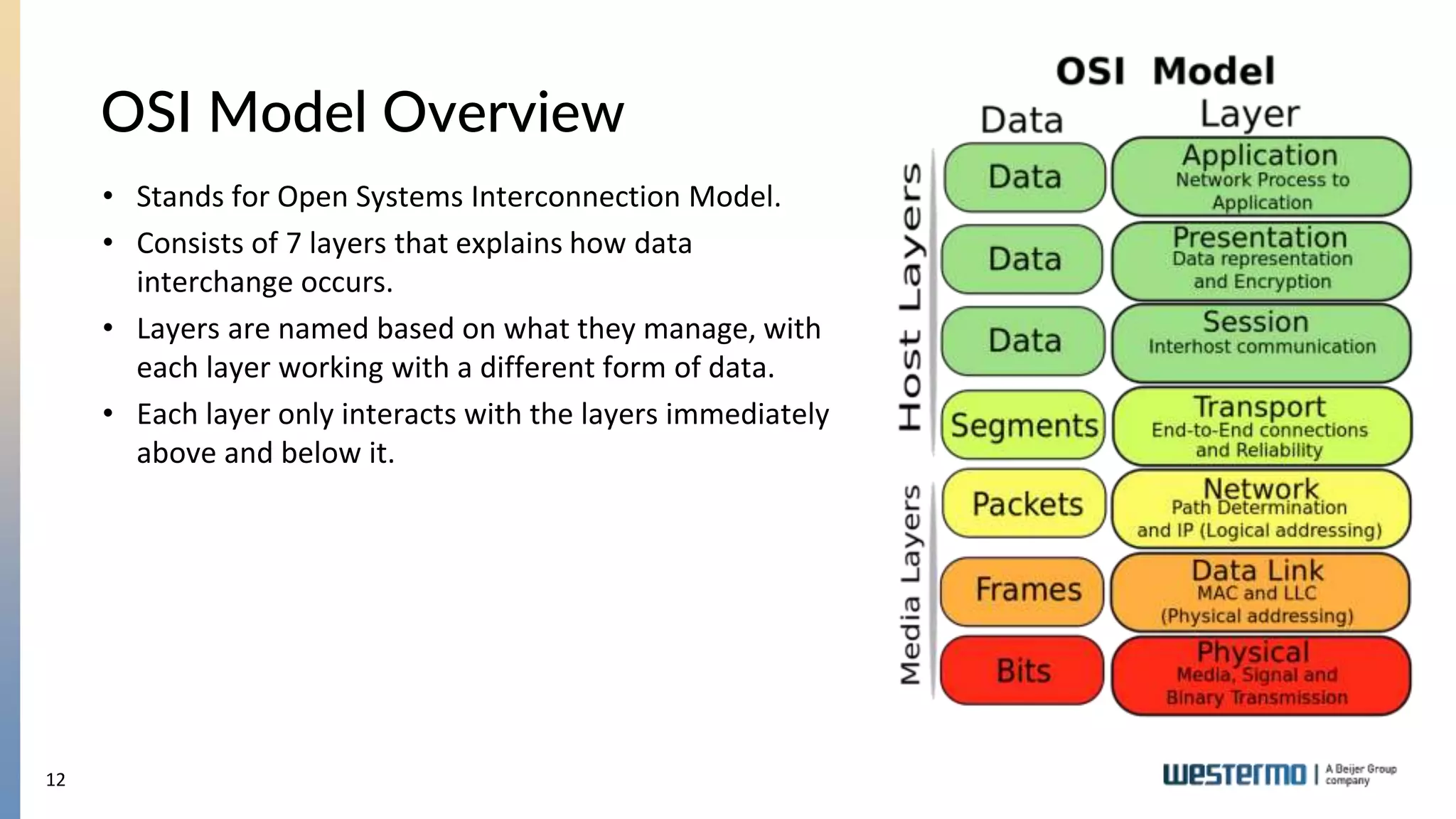
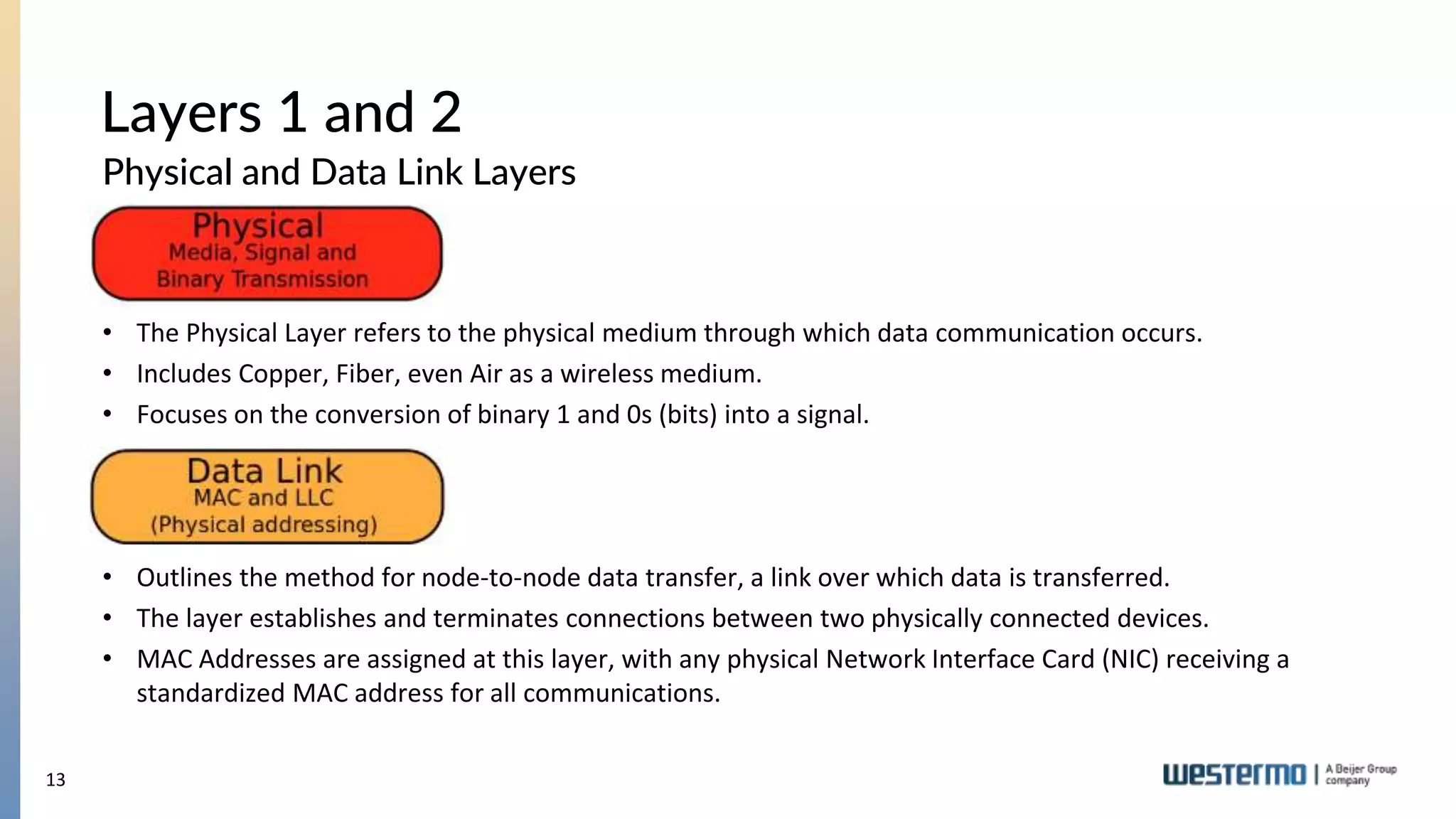
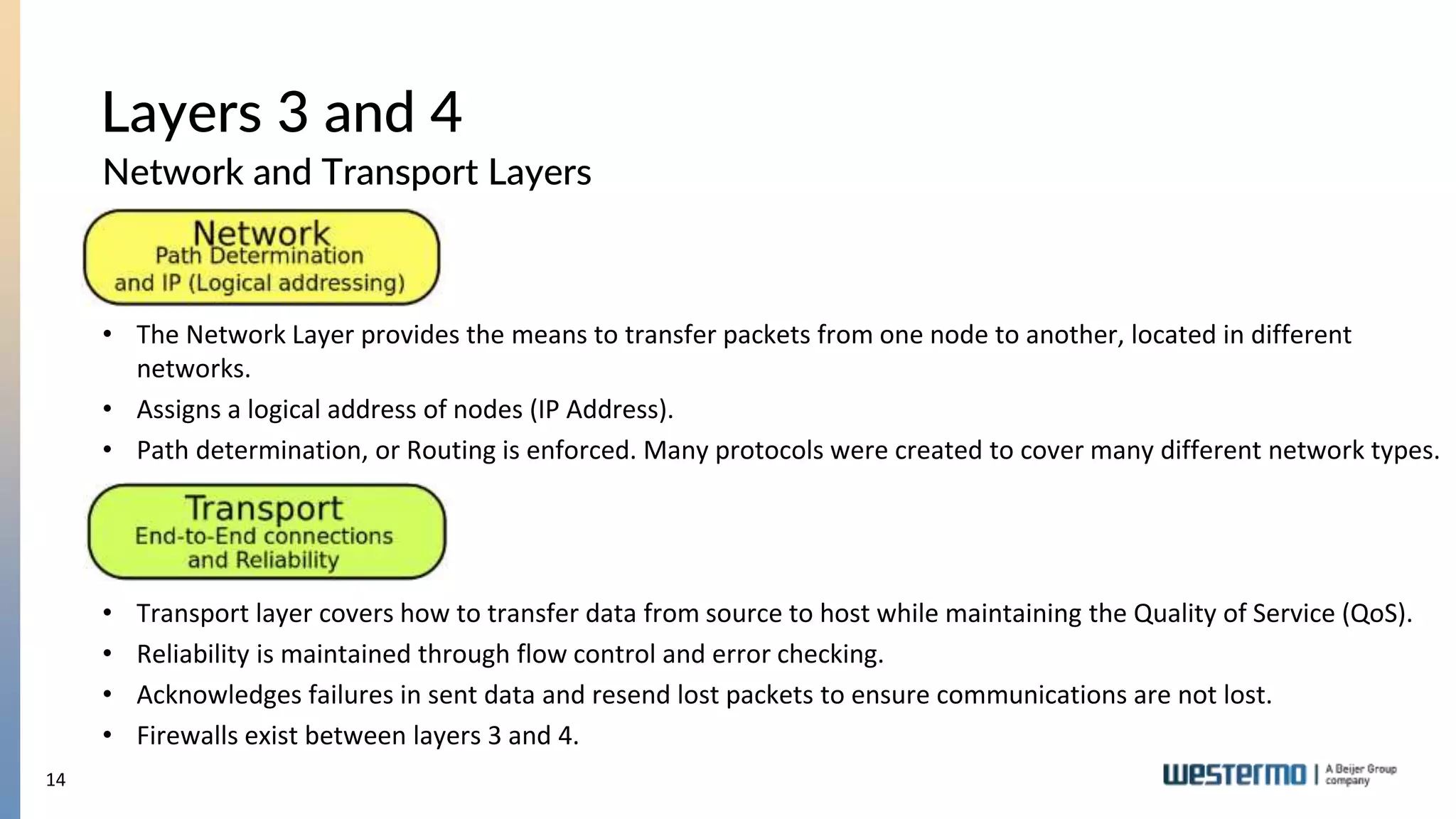
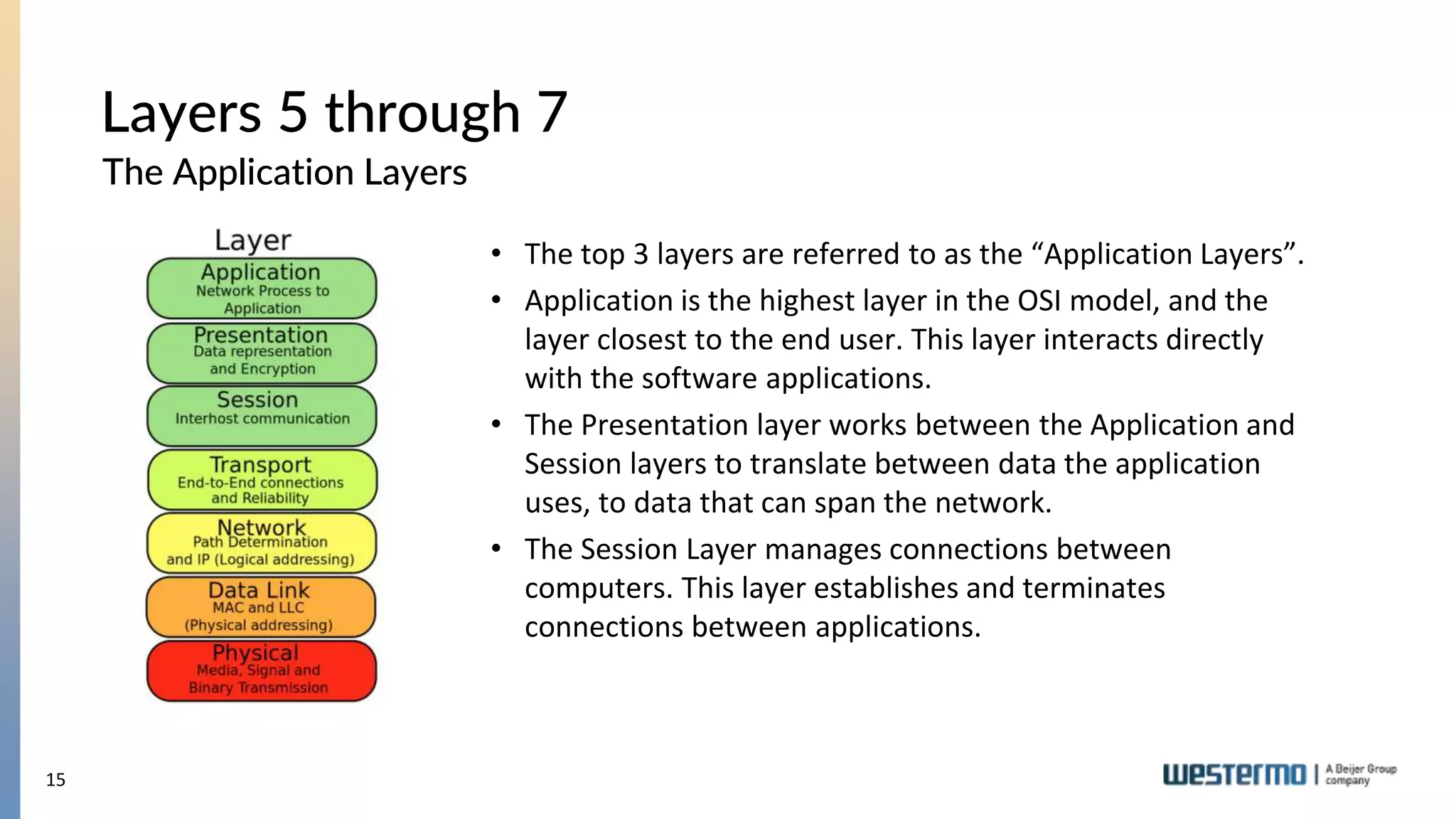
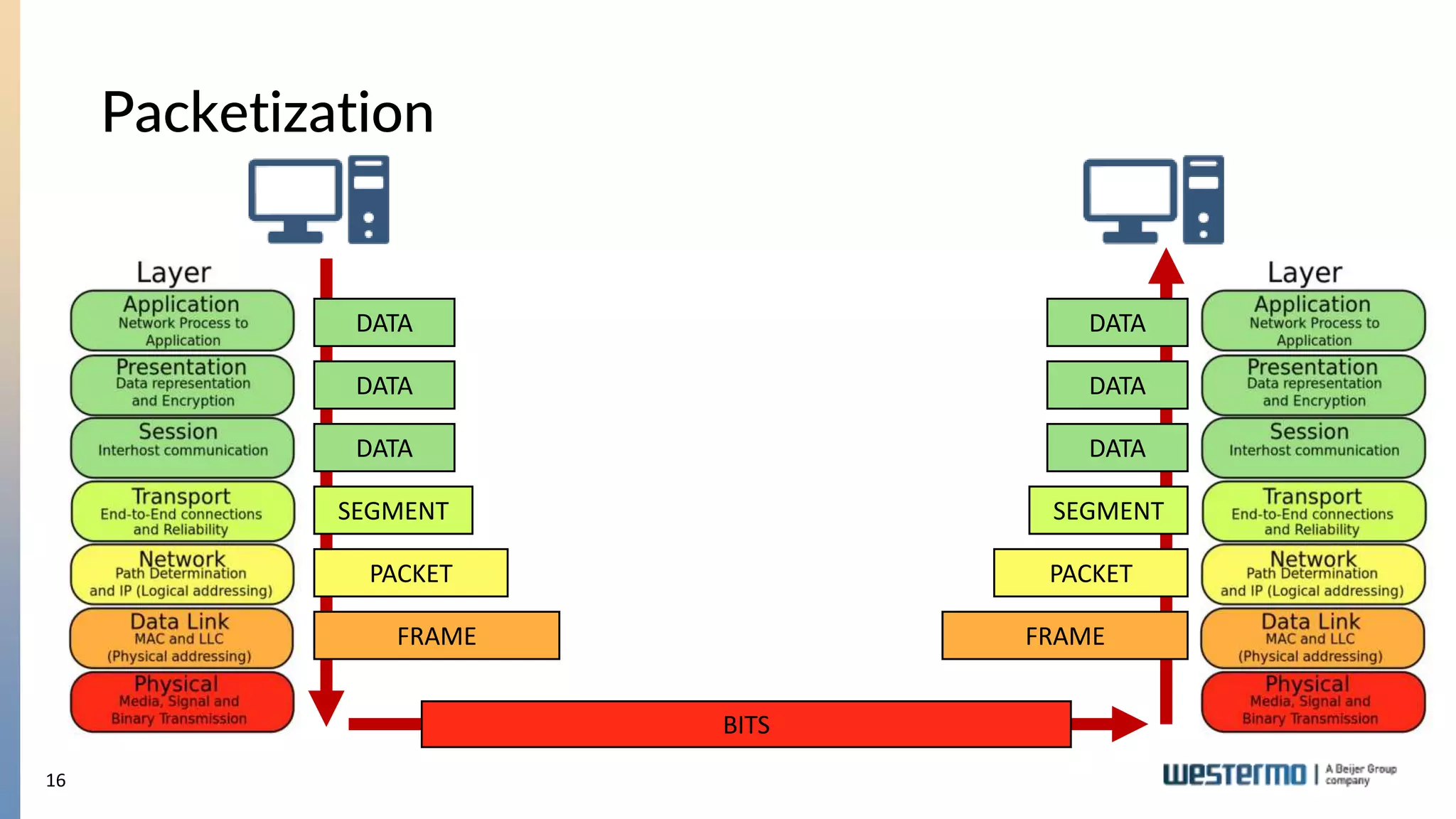
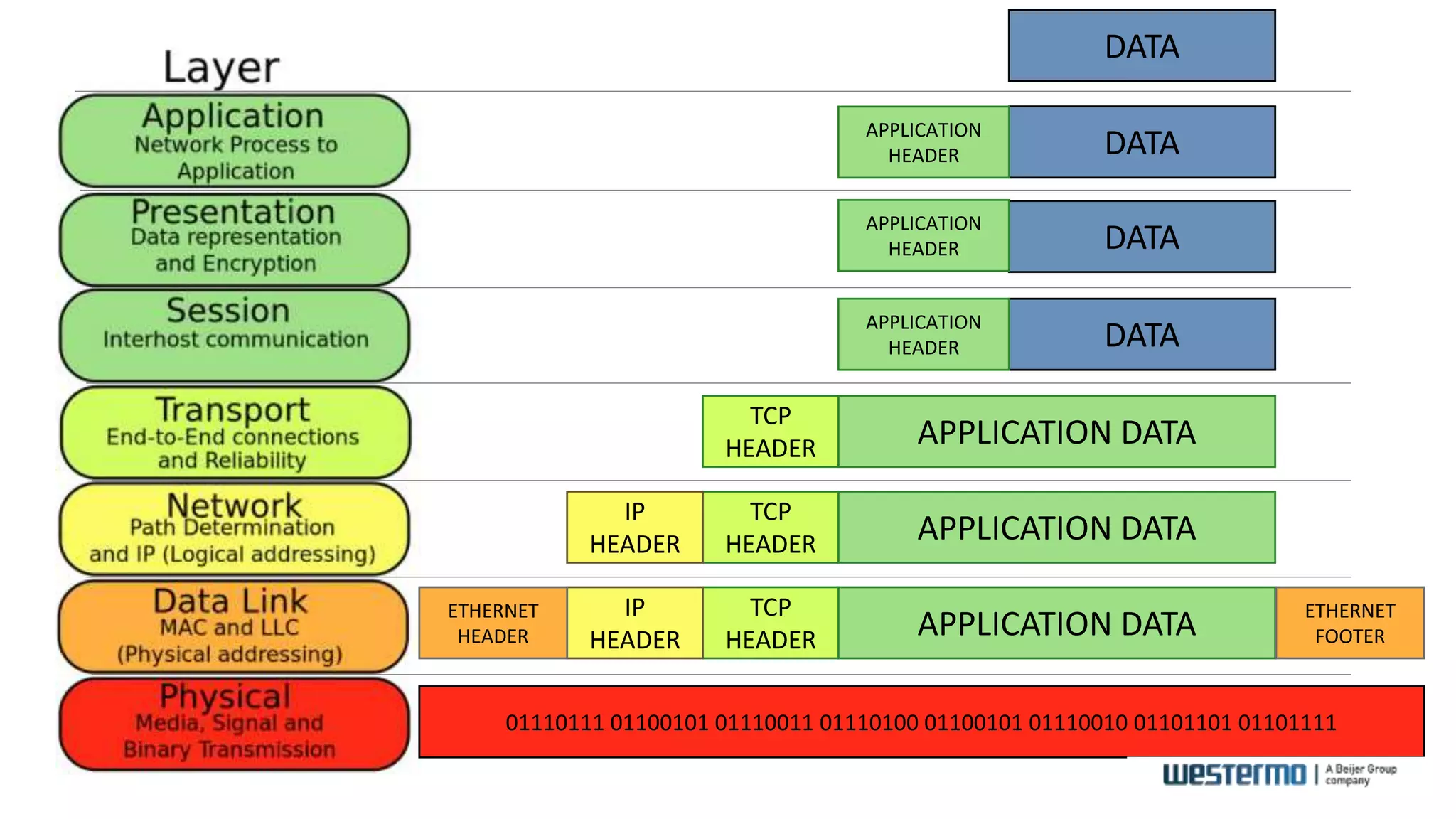
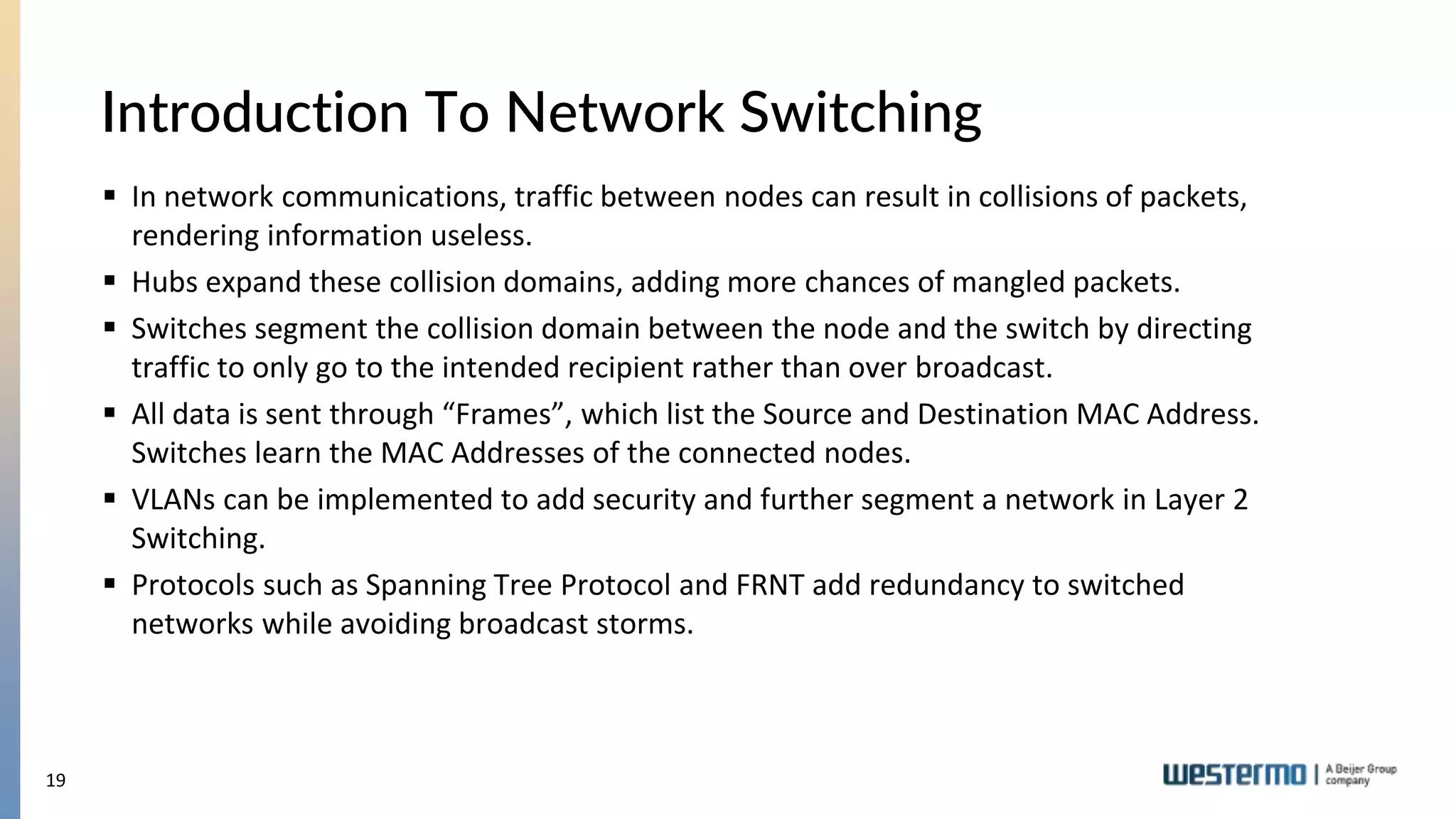
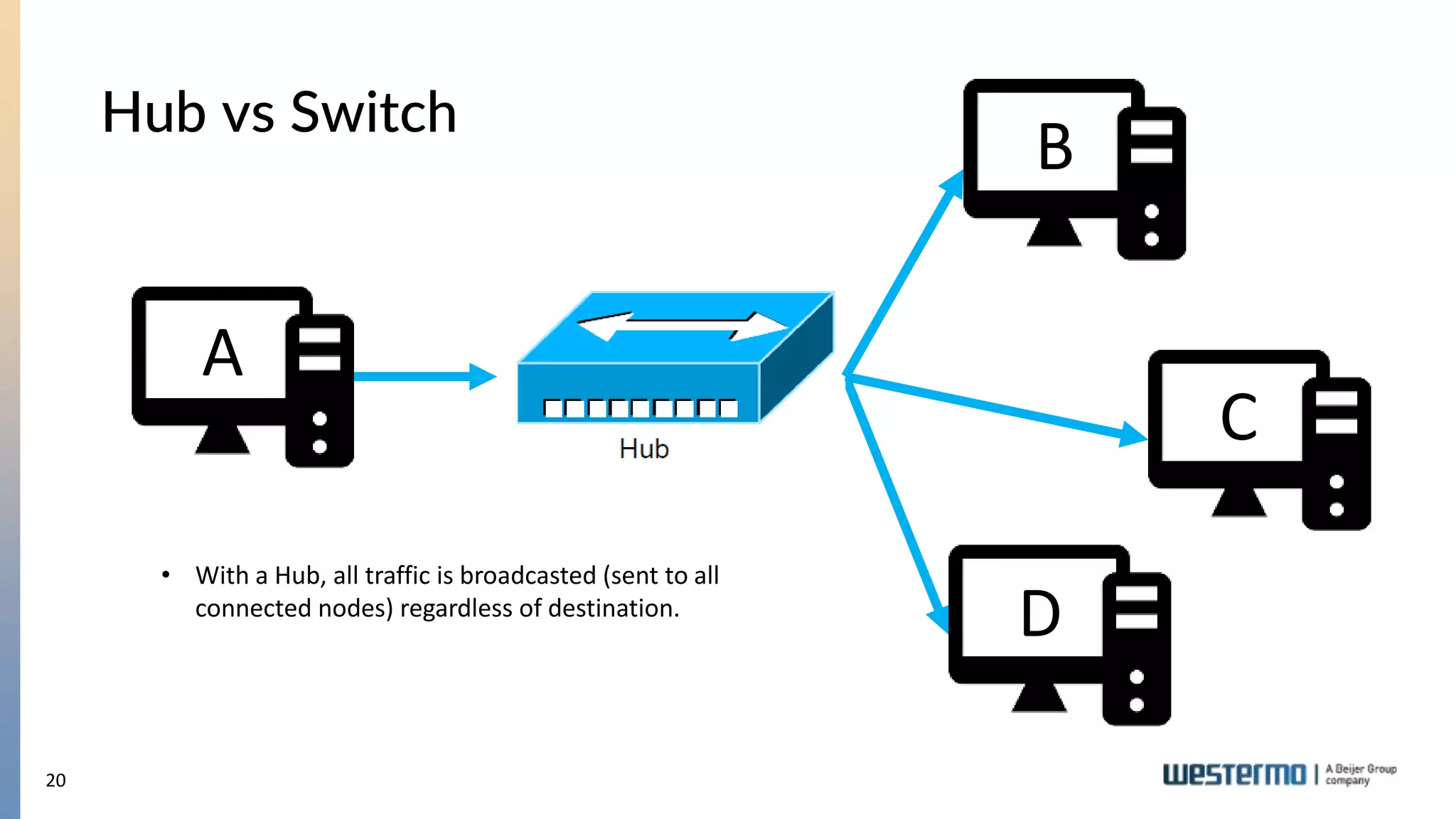
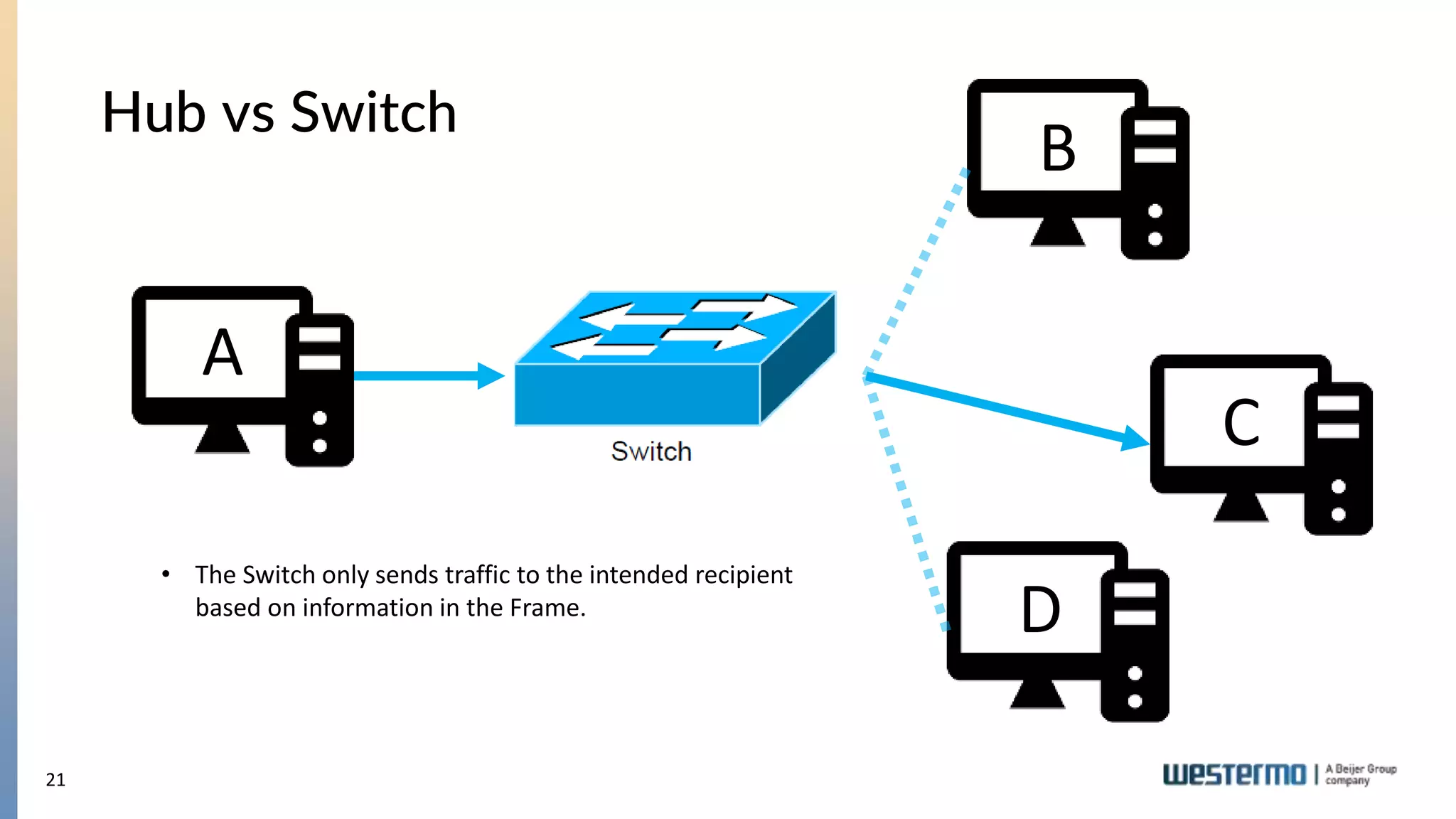
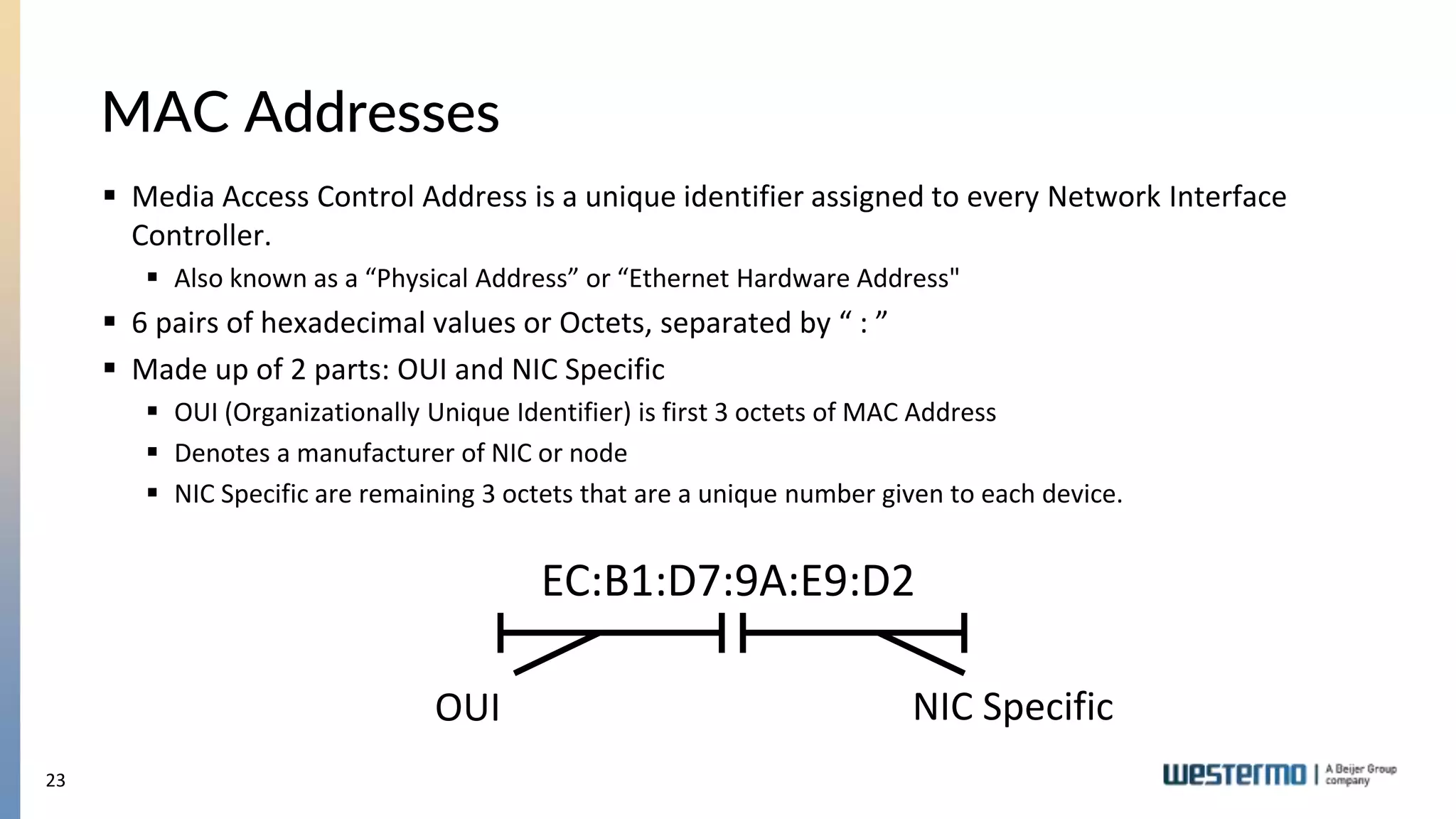
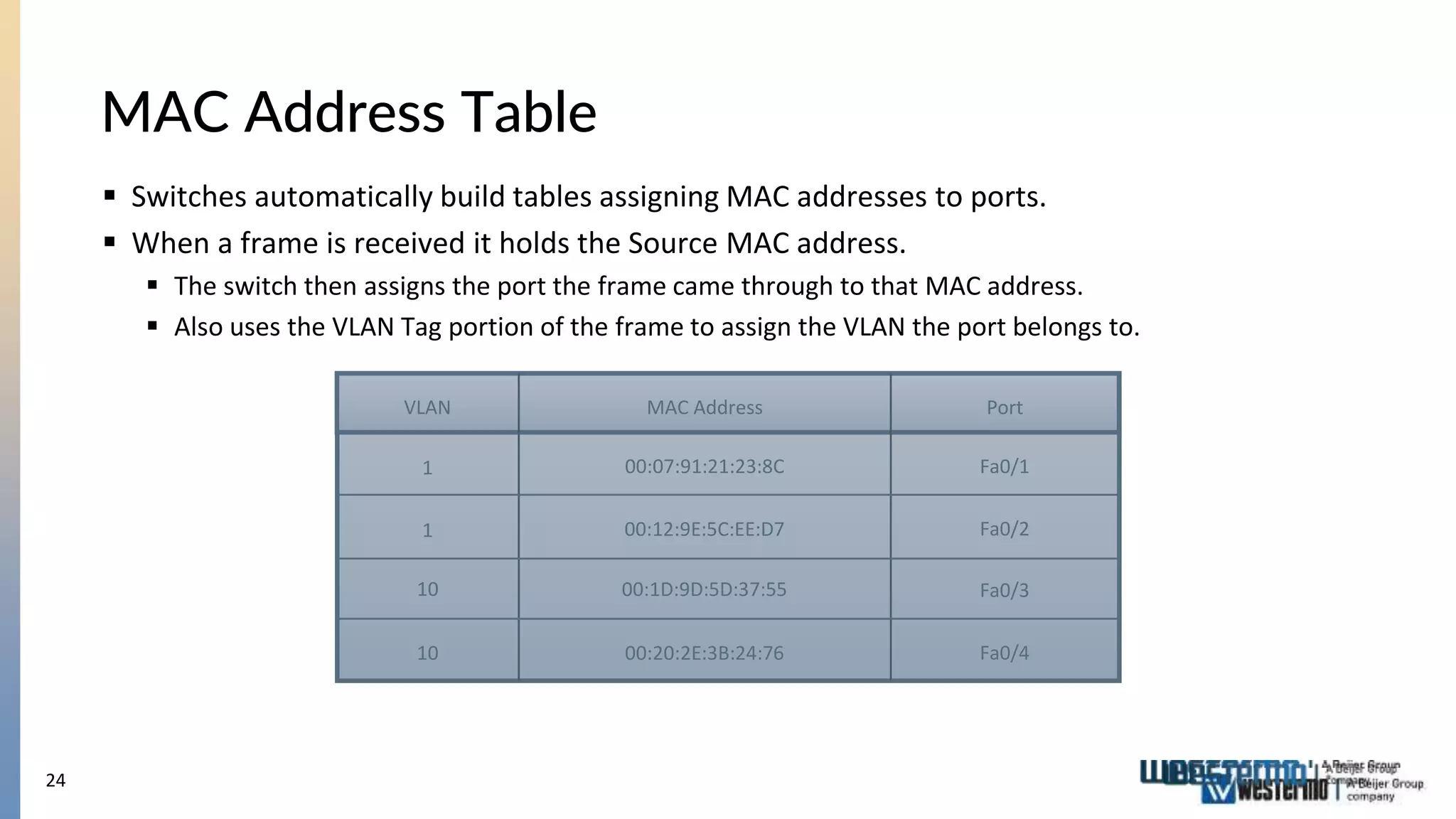
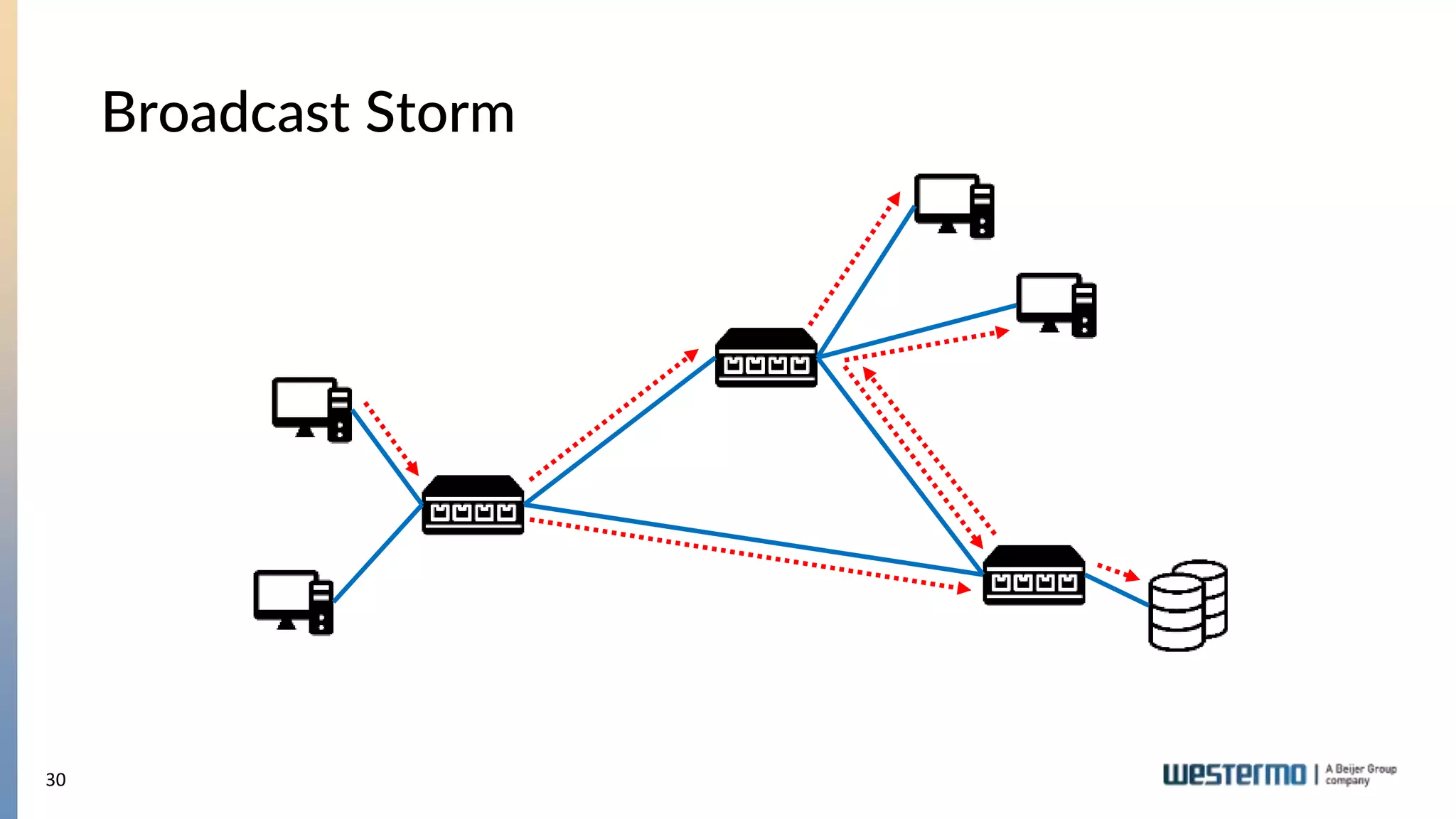
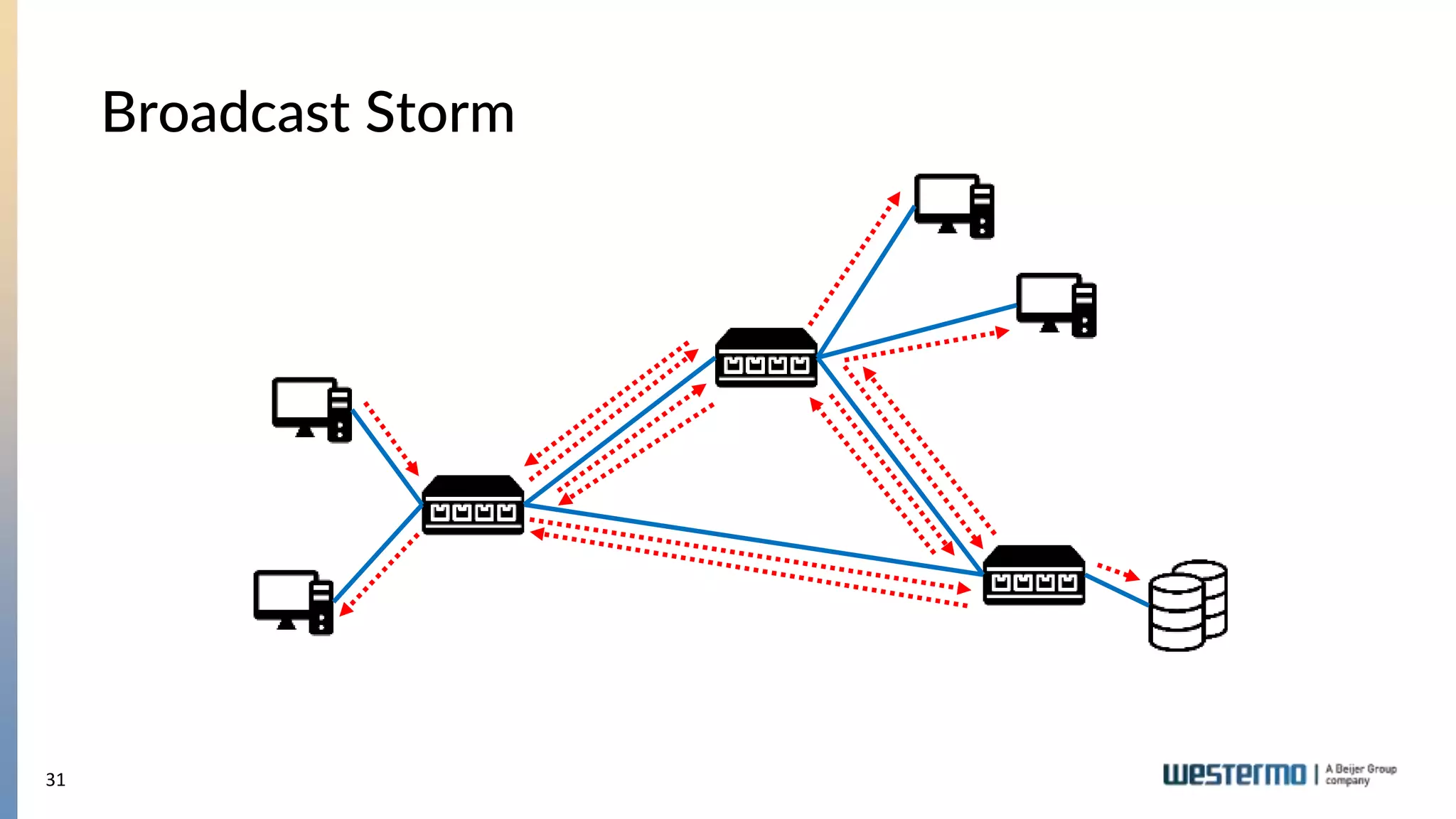
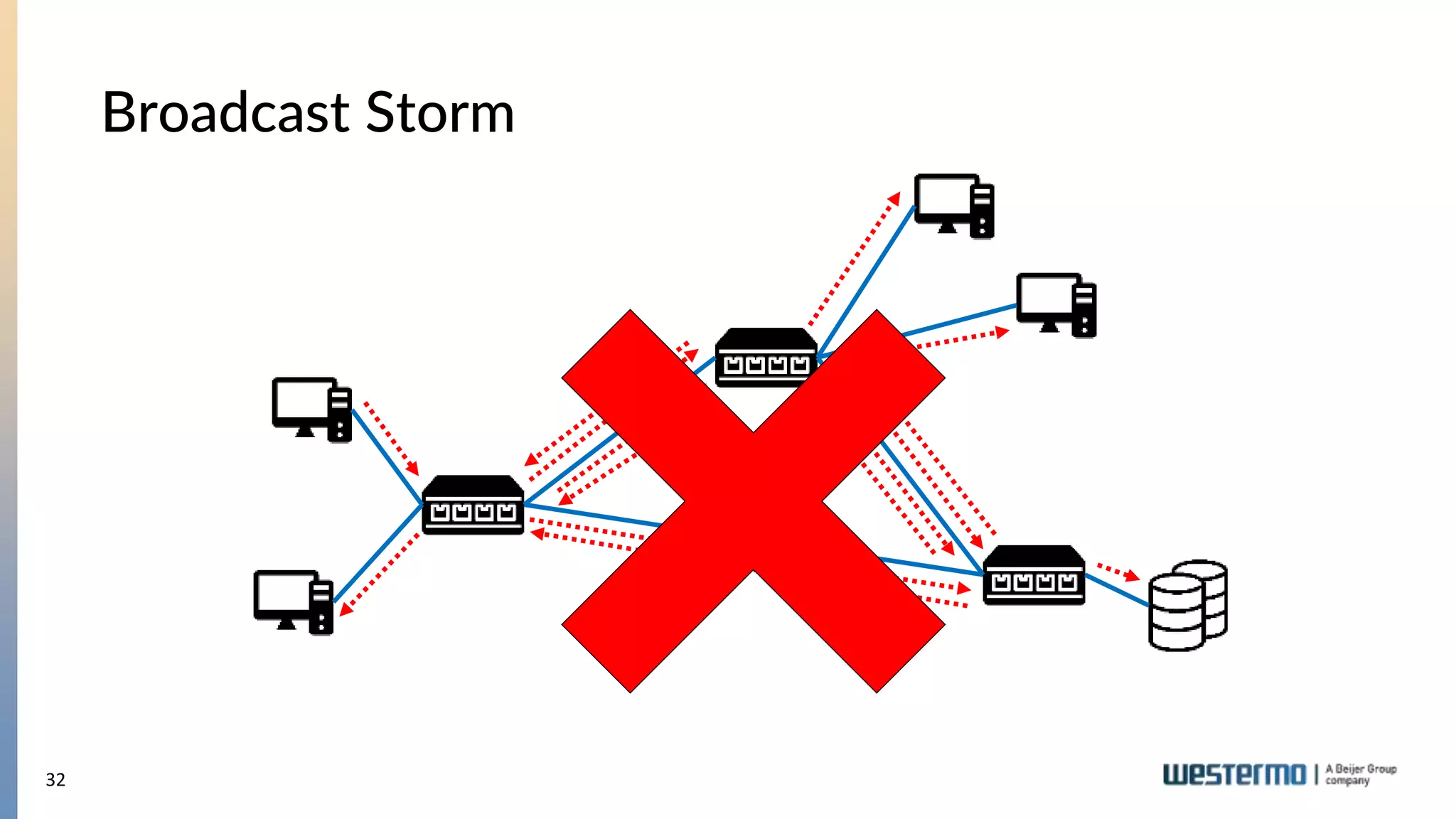
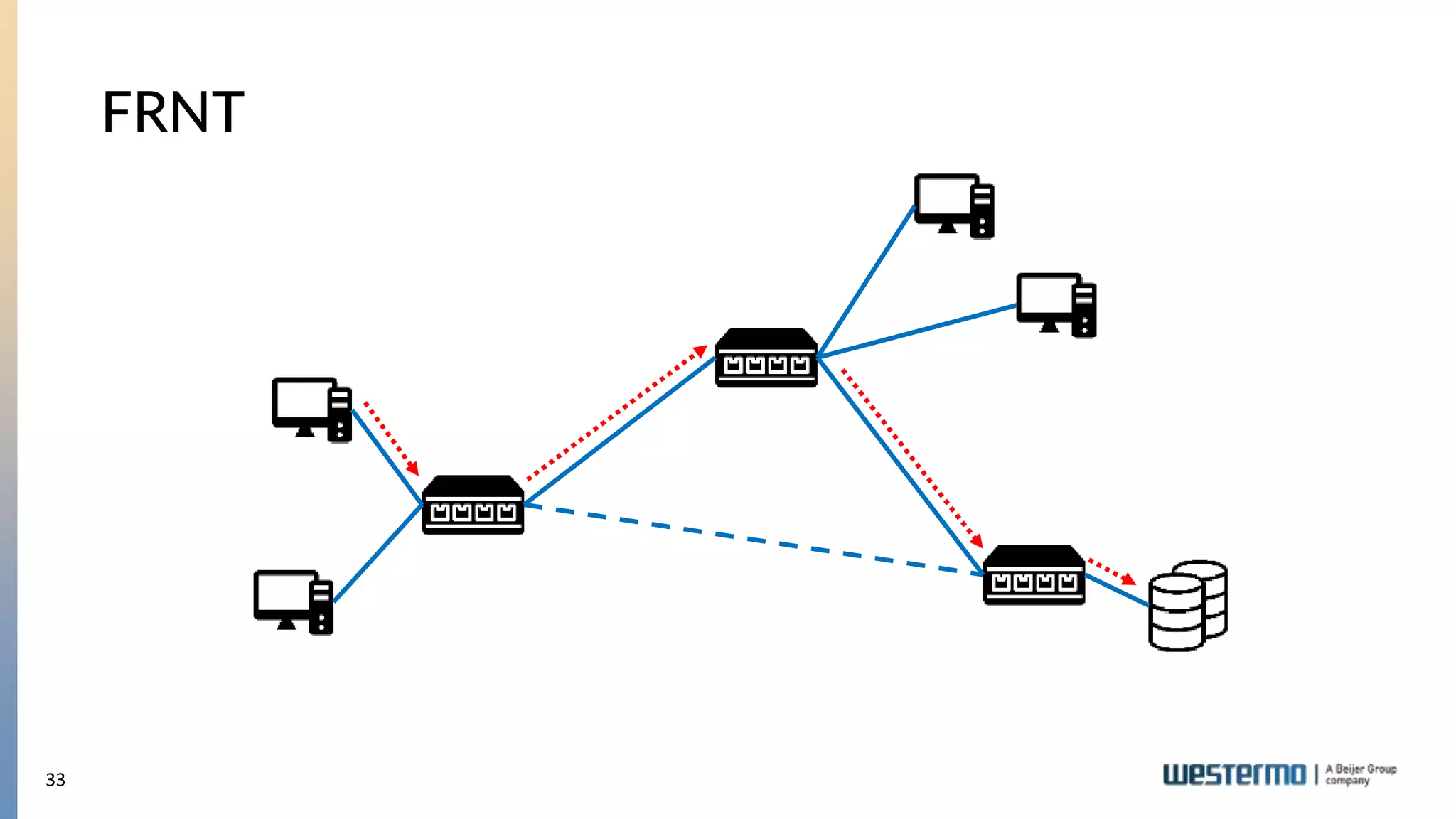
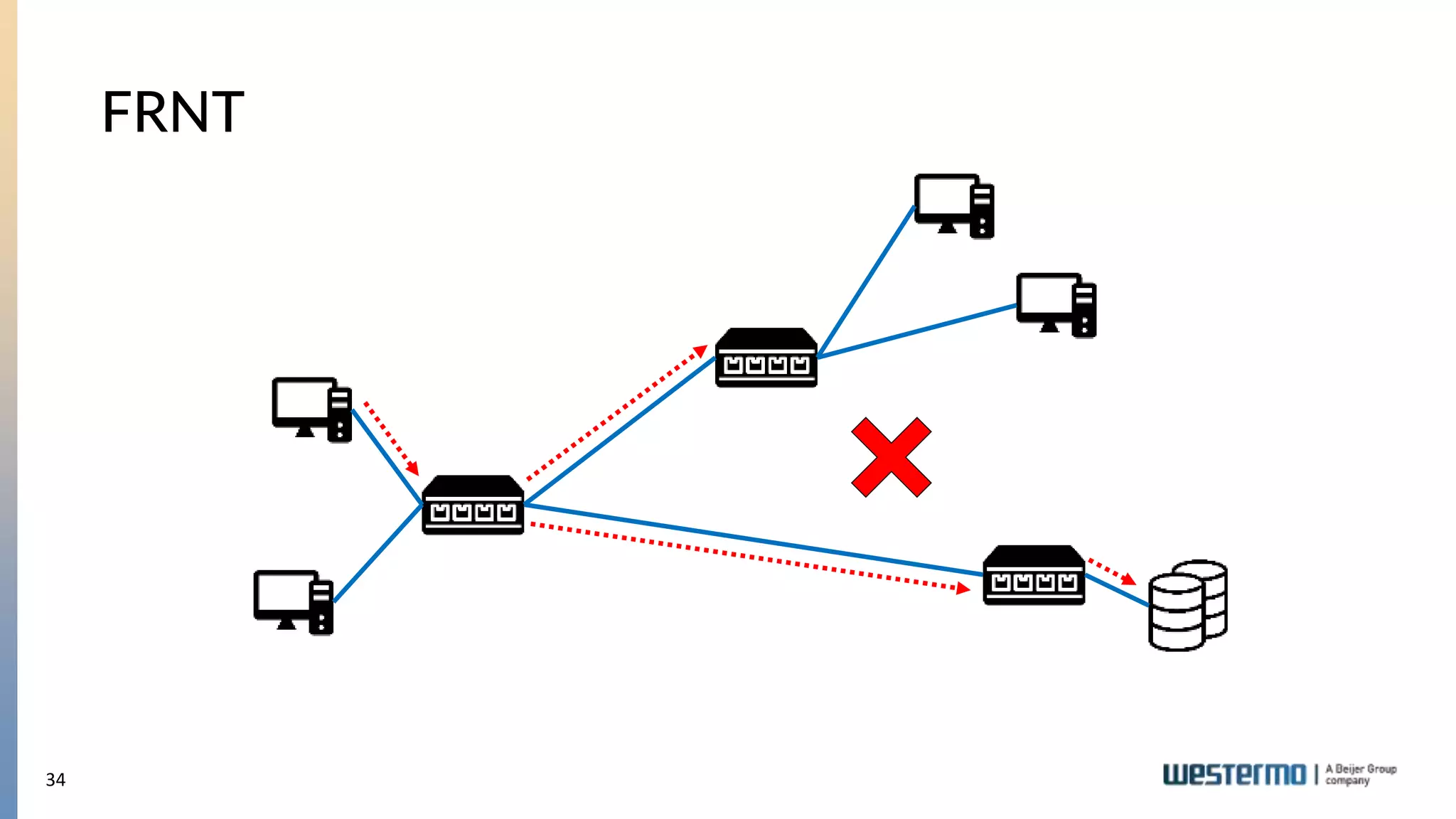
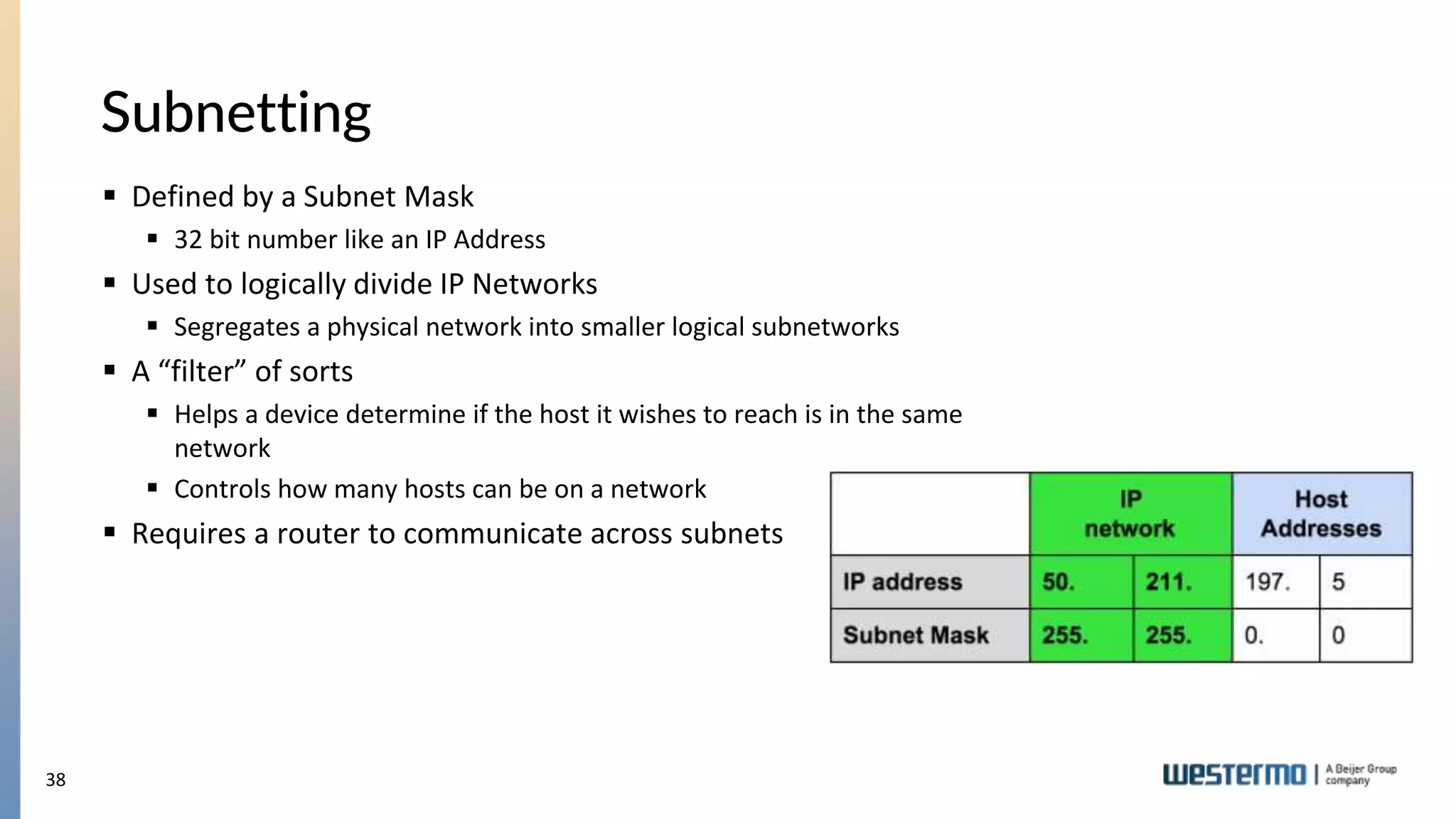
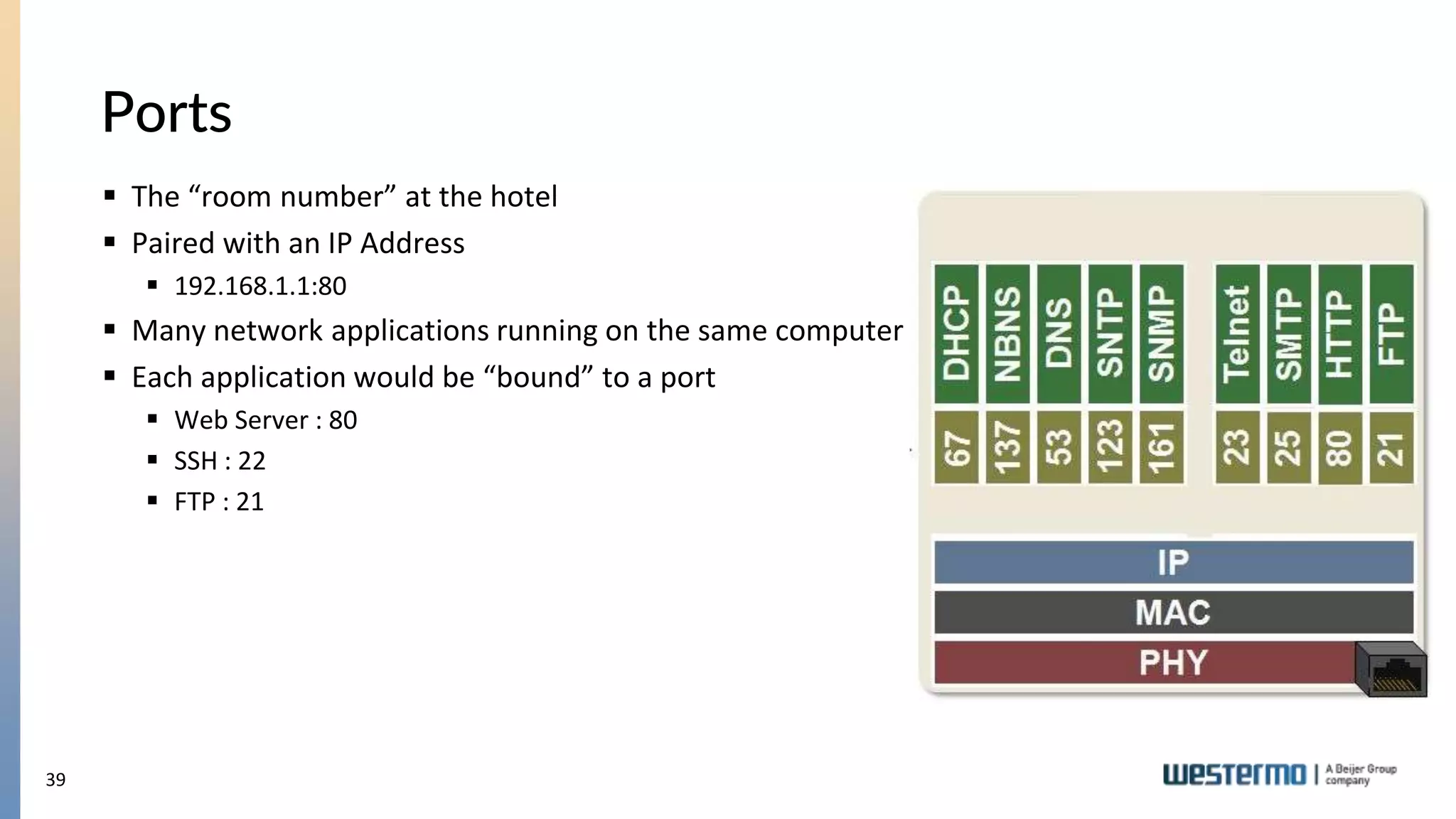
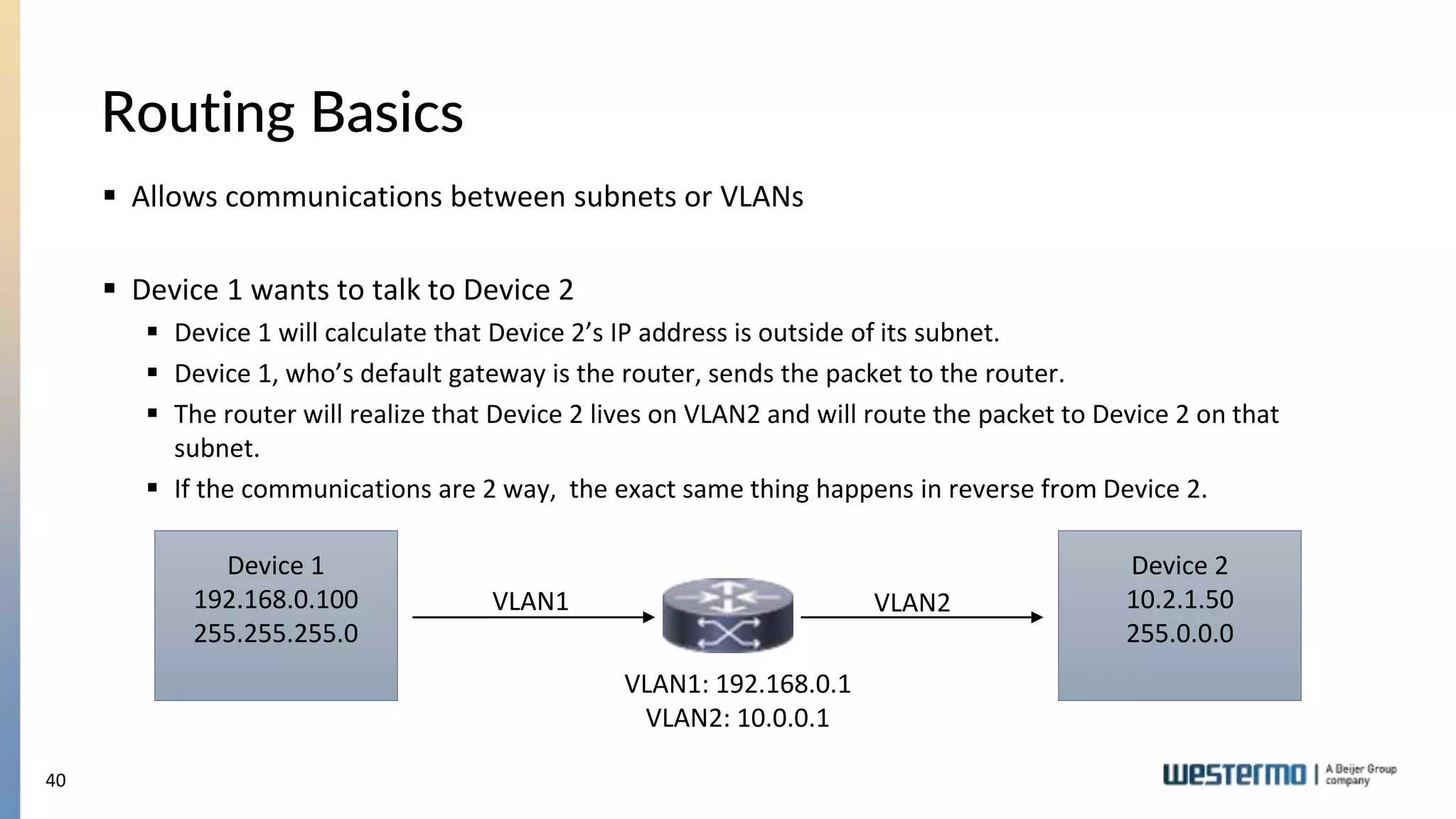
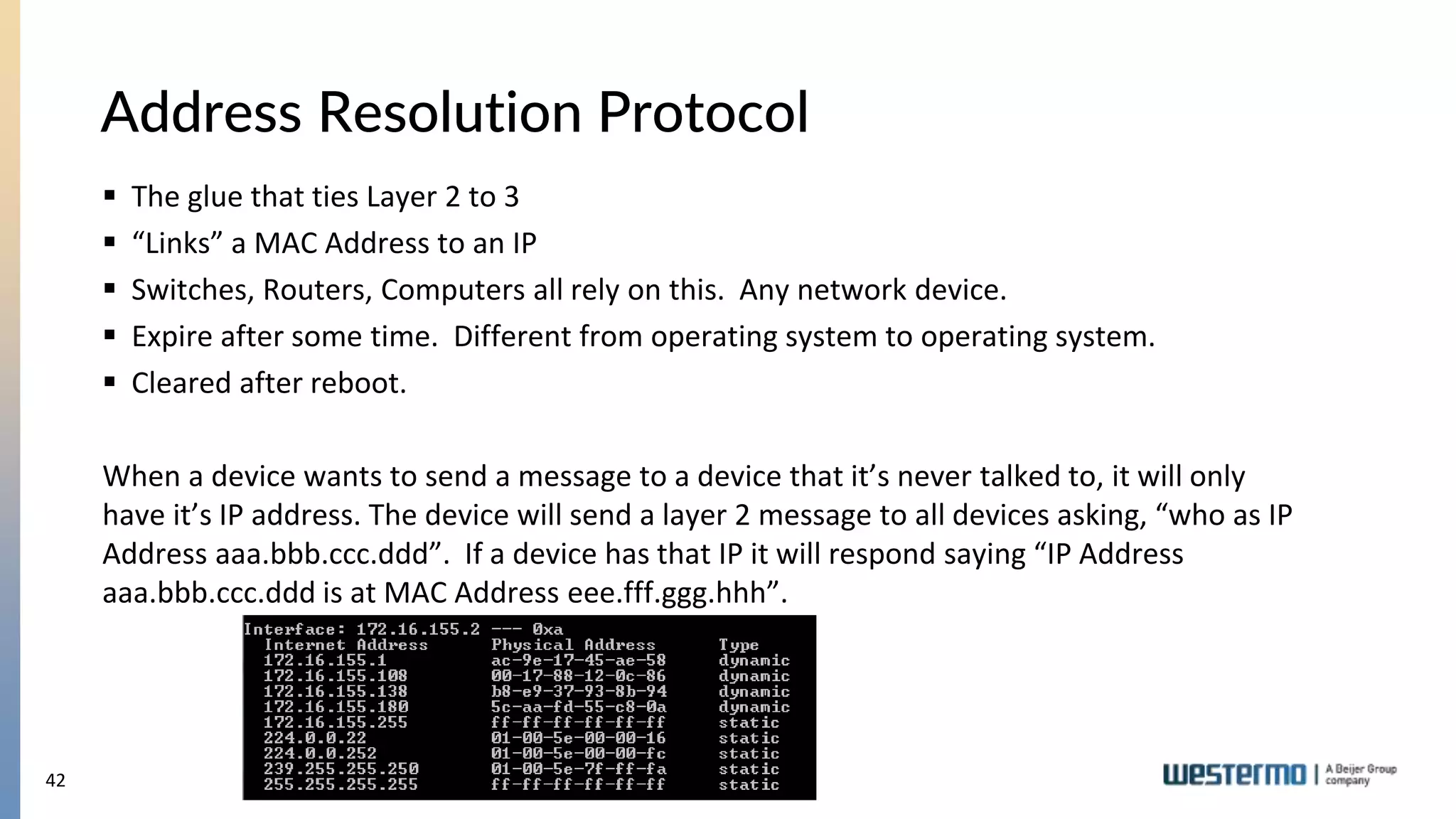
The document provides an overview of Ethernet networking, covering key concepts such as industrial networking, physical layers, data handling, switching, routing, and firewalls. It introduces Westermo, its historical context, and industry presence, and discusses the importance of environmental considerations in industrial settings. Further learning opportunities and training programs offered by Westermo are also presented.