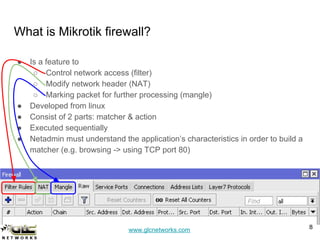
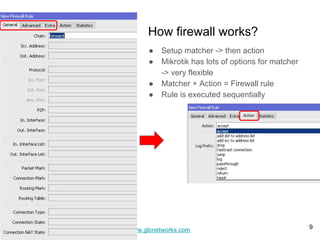
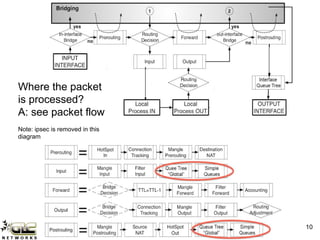
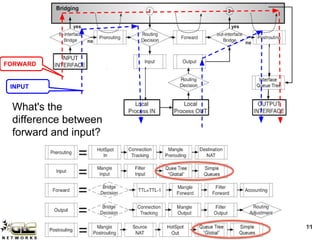
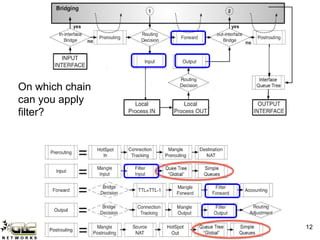
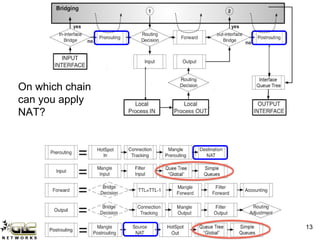
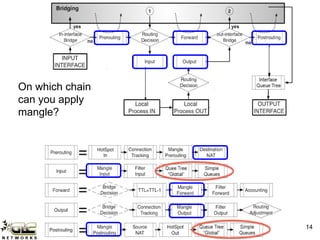
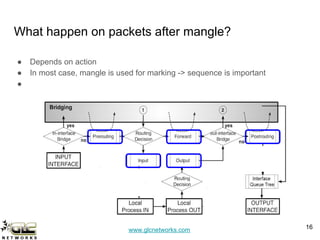
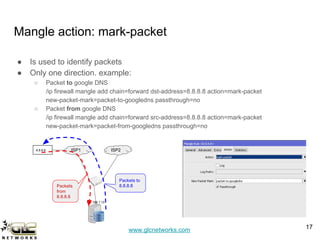
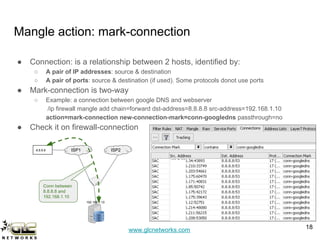
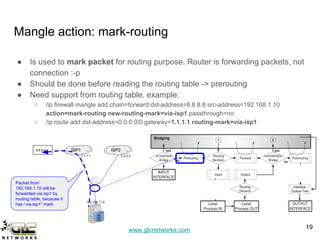
The GLC Networks webinar, led by Achmad Mardiansyah, covers key topics including firewall operations and Mikrotik's mangle features for network control. The presentation aims to educate participants about managing network access, modifying headers, and marking packets for processing. Attendees are encouraged to contribute and share their experiences in a collaborative learning environment.