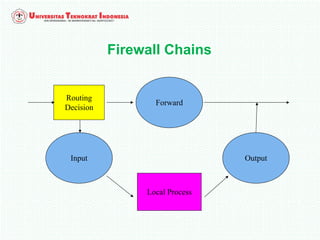
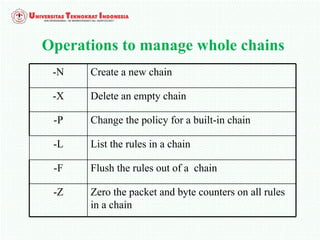
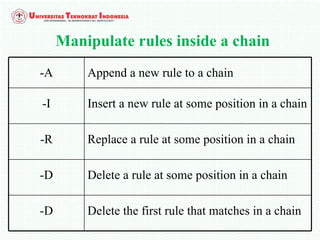
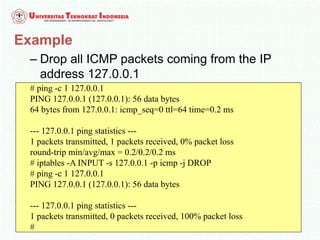
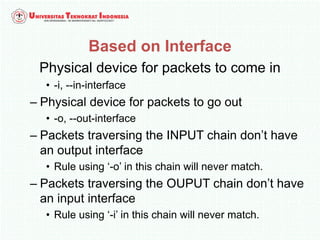
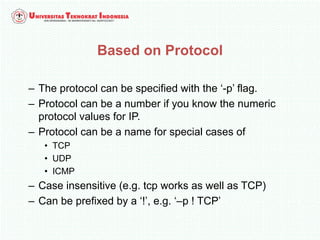
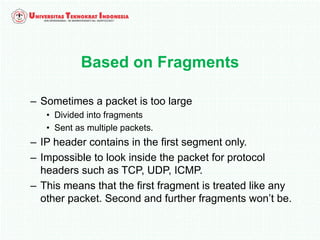
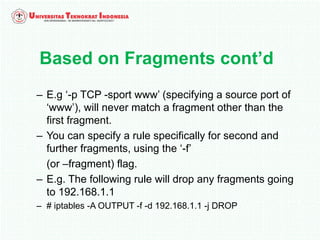
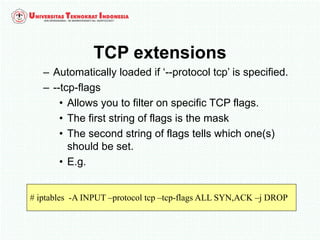
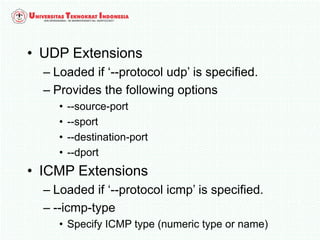
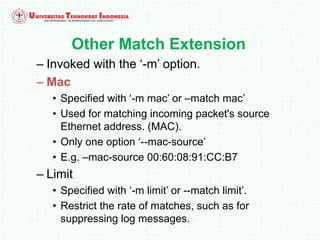
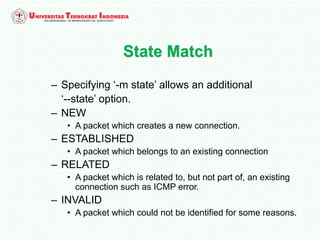
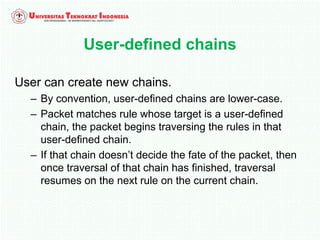
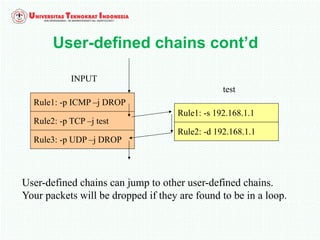
A firewall is software or hardware that controls incoming and outgoing network traffic by analyzing the header information in packets and allowing or blocking them based on predefined rules. There are different types of firewalls including host-based, network-based, and cloud firewalls. Under Linux, iptables provides a firewall framework to define rules for the built-in chains INPUT, OUTPUT, and FORWARD using options like source/destination addresses, protocols, and ports. Rules can match packets and target them to user-defined chains for further processing before accepting or dropping them.