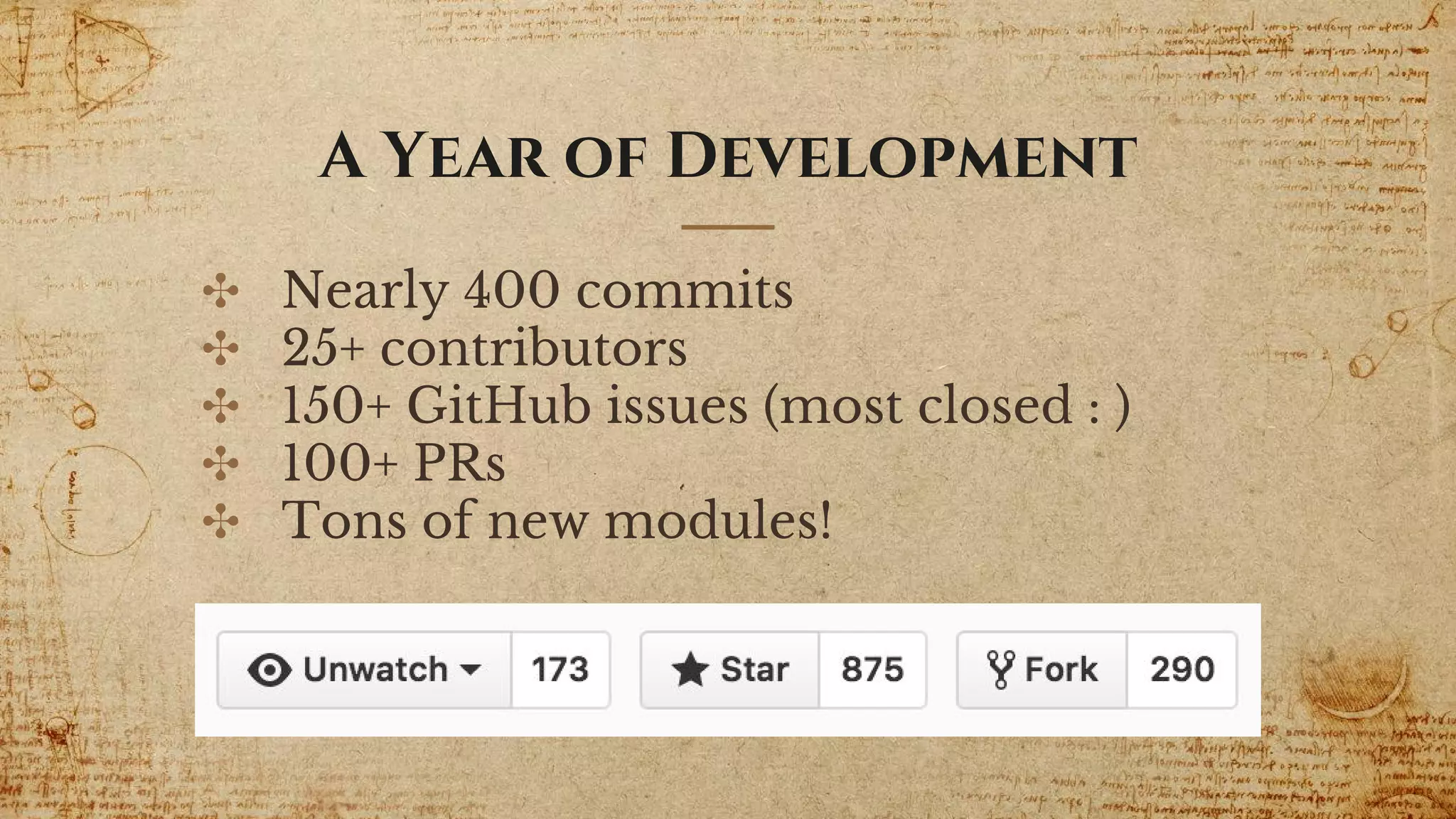
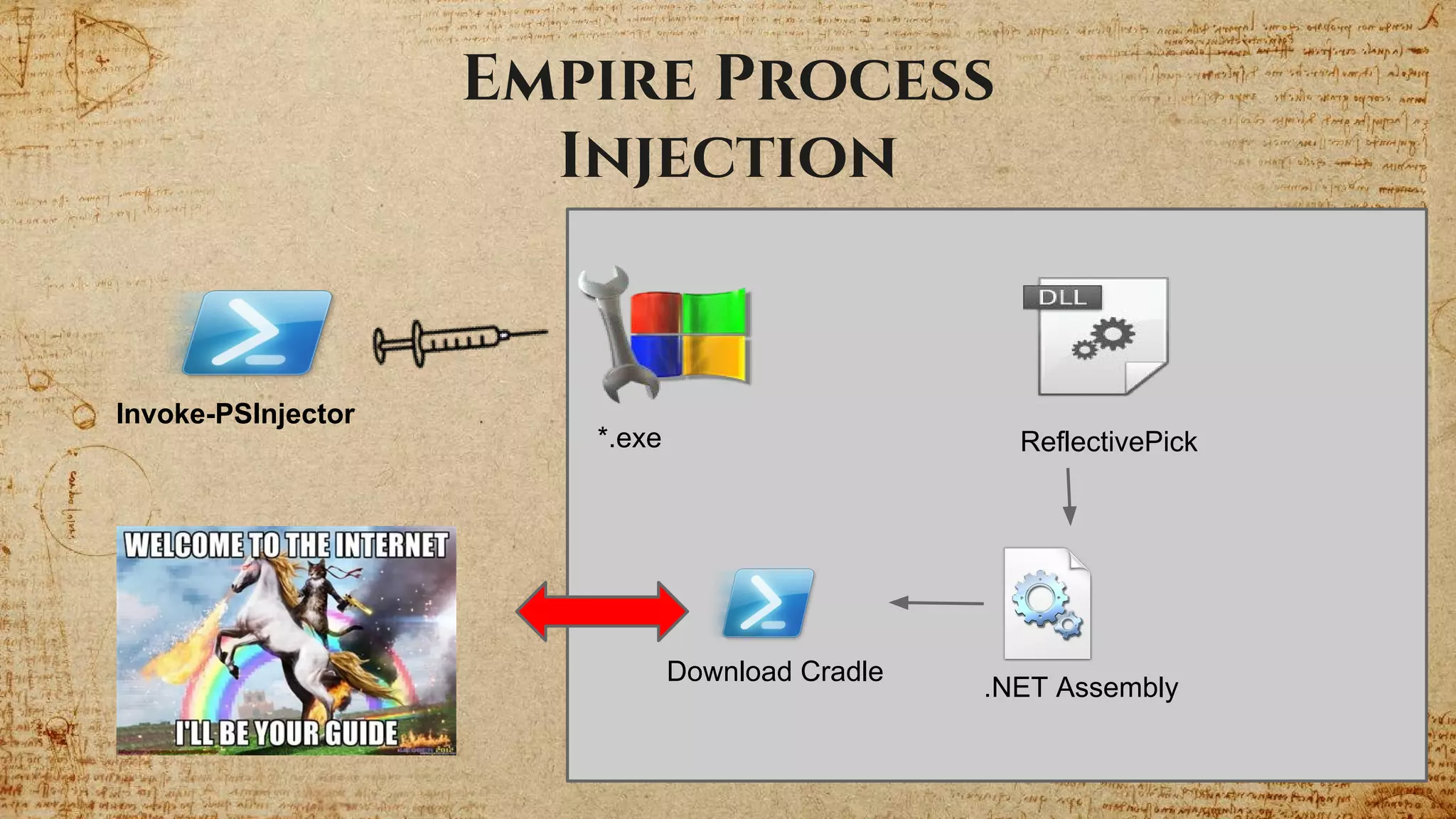
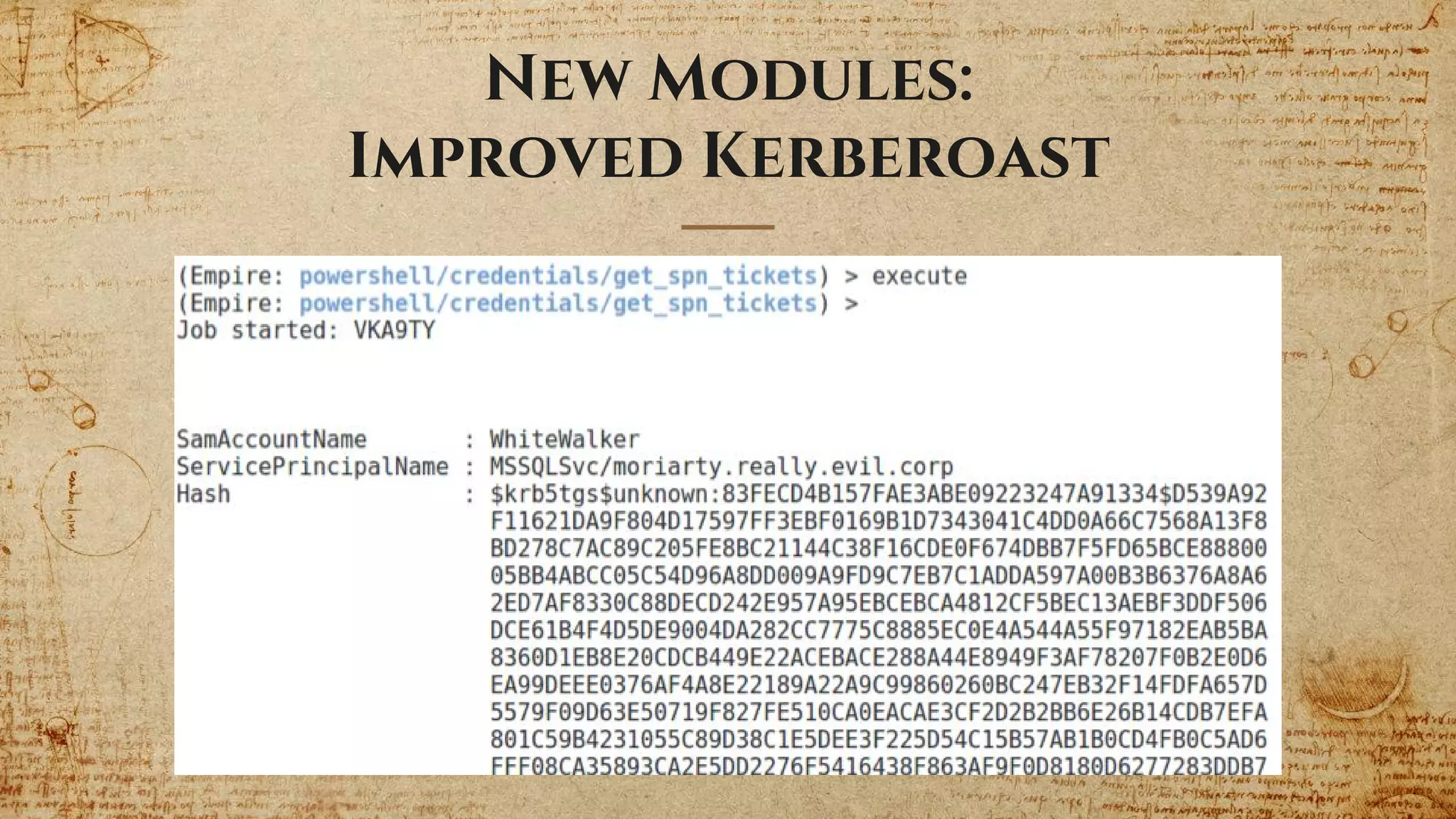
The document provides a comprehensive overview of the Empire 2.0 project, a PowerShell post-exploitation framework developed by a team of contributors. It details the motivations behind its development, new features introduced, and the integration of the Empyre variant with enhancements for modularity and cross-platform compatibility. Additionally, it emphasizes future development plans including new listener modules and improved communication structures.

















![Empire Drawbacks
✣ We’ve never built a RAT before
Mistakes were made ¯_(ツ)_/¯
✣ Only comms methods were HTTP[S]
Modules were expandable, transports
weren’t
✣ Separate projects for Empire/EmPyre
Name/project confusion
Separate codebases ==](https://image.slidesharecdn.com/ayearintheempire-160924020132/75/A-Year-in-the-Empire-20-2048.jpg)













![interact AGENT
Drops you into the
language-appropri
ate agent menu
with the same
options you’re
used to for either
project.
Interface Integration
stagers/*
Now broken out
into OS-applicable
folders
(Windows/OS
X/Linux).
usemodule [tab]
Executed from an
agent, only
tab-completes
language-appropri
ate modules.](https://image.slidesharecdn.com/ayearintheempire-160924020132/75/A-Year-in-the-Empire-36-2048.jpg)




![listeners/http
✣ The original HTTP[S] listener
But now redone with flask!
“Routing packet” is base64’ed and stuffed
into a new cookie value
✣ Generates Python and PowerShell
launchers, staging, and agent code
✣ You can easily modify the cookie
used/transforms on the data itself to
change up indicators!](https://image.slidesharecdn.com/ayearintheempire-160924020132/75/A-Year-in-the-Empire-41-2048.jpg)










