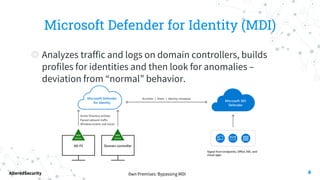
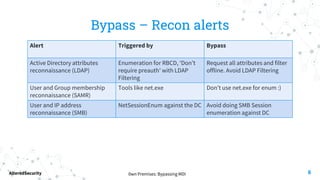
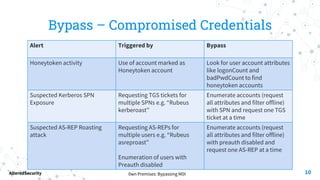
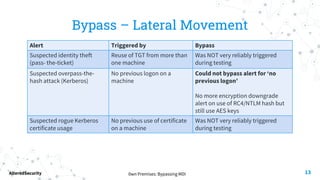
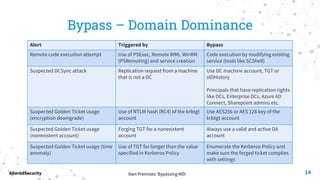
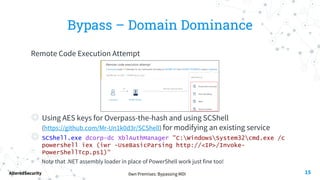
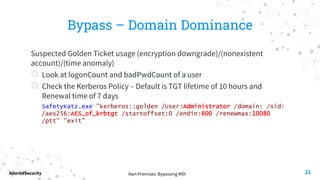
This document discusses bypassing alerts from Microsoft Defender for Identity (MDI). It begins with an introduction to MDI and the types of alerts it generates. It then explores techniques for bypassing alerts during different phases of an attack like reconnaissance, credential compromise, and lateral movement. These include using alternative tools, limiting interactions with domain controllers, and complying with Kerberos policies. The document also notes techniques like silver tickets that are not detected by MDI. It concludes by acknowledging limitations of only testing alerts and not coupled defenses.