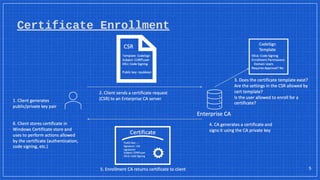
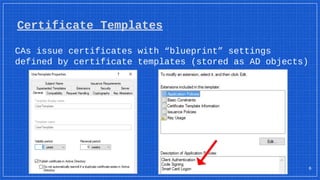
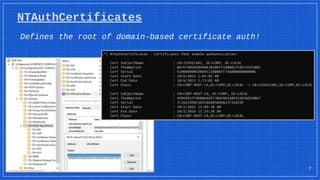
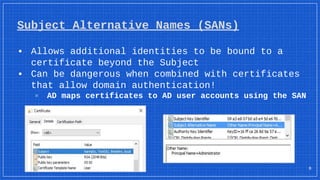
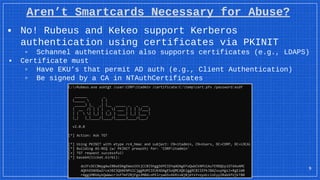
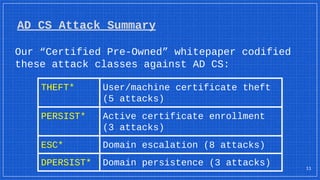
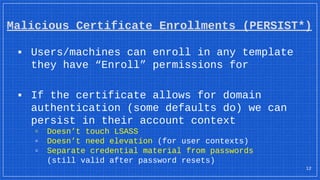
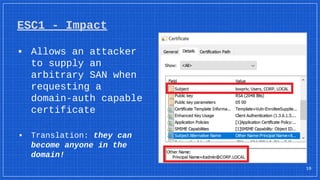
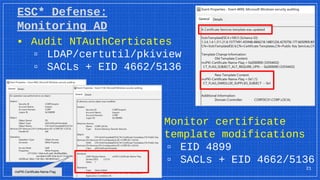
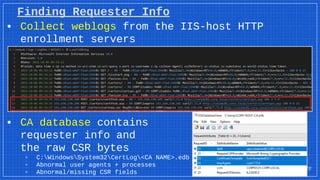
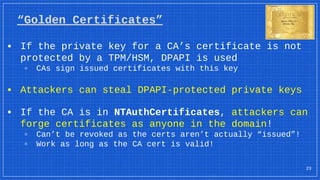
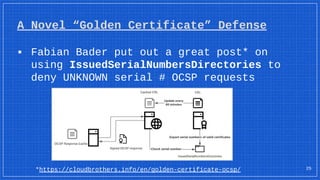
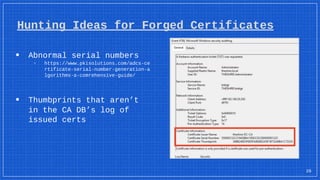
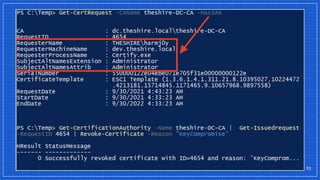
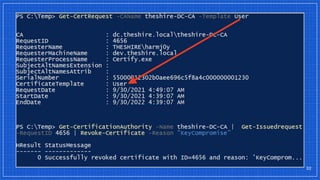
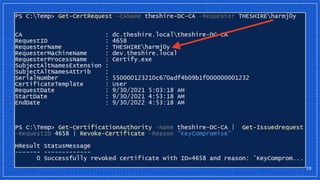
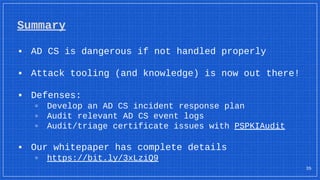
The document discusses the vulnerabilities and defense strategies associated with Active Directory Certificate Services (AD CS), particularly focusing on various attack methods and their impacts. It outlines the importance of properly securing AD CS to prevent unauthorized certificate enrollment and domain escalation, and emphasizes the necessity of monitoring and auditing certificate activities. Recommendations for incident response and key defensive measures are also provided to mitigate risks associated with certificate management.


![THEFT*/PERSIST* Defense: Overview
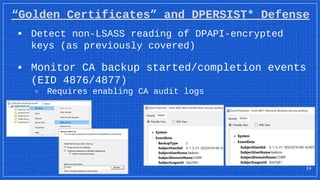
▪ Detect non-LSASS reading of DPAPI-encrypted keys
▫ Monitor file opens/reads of DPAPI files (SACLs*?)
■ (Local)AppData folders:
Microsoft[Crypto | Protect | Vault | Credentials]
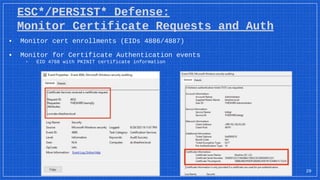
▪ Monitor certificate auth/enrollment events
▫ EIDs 4886/4887, EID 4768 (more on these later)
▪ Monitor for Certificate Authentication events
▫ EID 4768 with PKINIT certificate information
(more on this later)
▪ “Honey Credentials” in certificate form
14
*https://medium.com/@cryps1s/detecting-windows-endpoint-compromise-with-sacls-cd748e10950](https://image.slidesharecdn.com/recertifyingactivedirectory-211110164221/85/ReCertifying-Active-Directory-14-320.jpg)
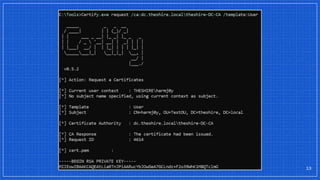
![Requirements:
1. Low-privileged user can enroll in the template
2. No “Issuance Restrictions”
3. [PKINIT] Client Authentication EKU, Smart Card Logon
EKU, Any Purpose EKU, or No EKU
4. The ENROLLEE_SUPPLIES_SUBJECT flag set on the template
▫ Template’s AD object has msPKI-Certificate-Name-Flag set to 1 in its bitmask
ESC1 - ENROLLEE_SUPPLIES_SUBJECT
15](https://image.slidesharecdn.com/recertifyingactivedirectory-211110164221/85/ReCertifying-Active-Directory-15-320.jpg)



![Thanks!
ANY QUESTIONS?
You can find us at:
@harmj0y | @tifkin_
[will | lee] @specterops.io
AD CS Whitepaper: https://bit.ly/3xLziQ9
37](https://image.slidesharecdn.com/recertifyingactivedirectory-211110164221/85/ReCertifying-Active-Directory-37-320.jpg)