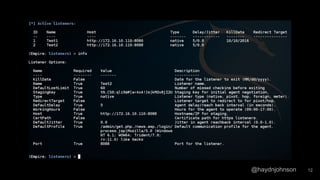
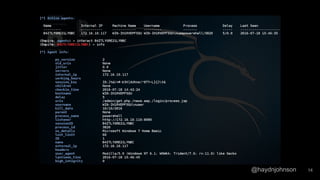
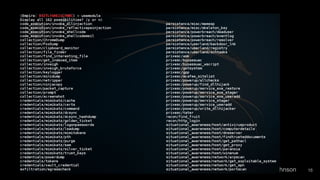
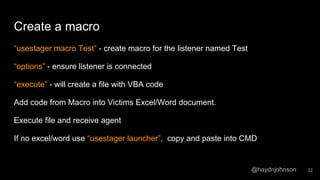
The document discusses the process of using PowerShell Empire for post-exploitation activities after gaining access to a network, covering steps such as identifying the host and user permissions, and using various modules for further exploitation and privilege escalation. It highlights the advantages of PowerShell as a versatile tool and guides on setting up listeners and agents to control compromised machines. Tutorials are linked for further learning on techniques to maintain access and gather information from victims' systems.