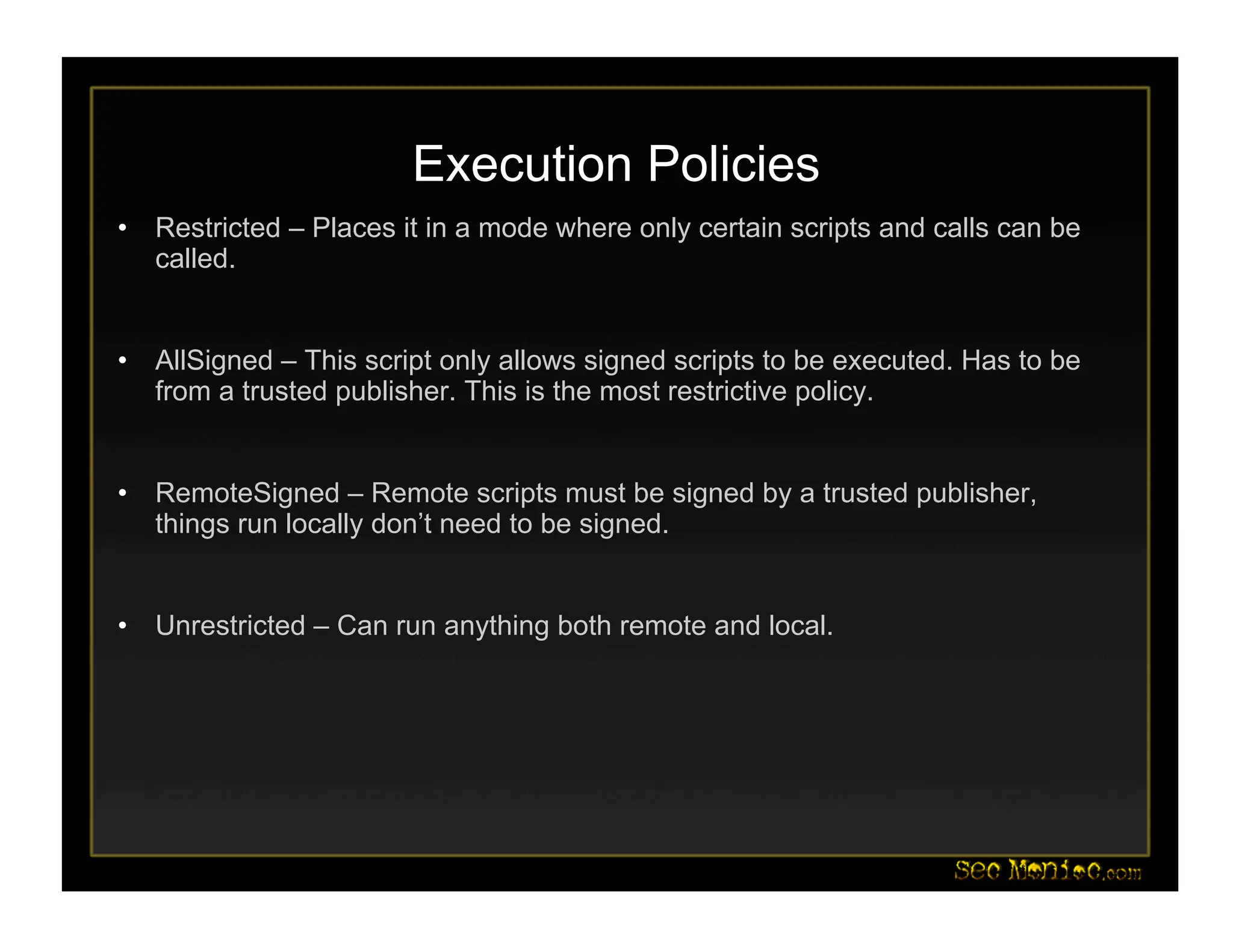
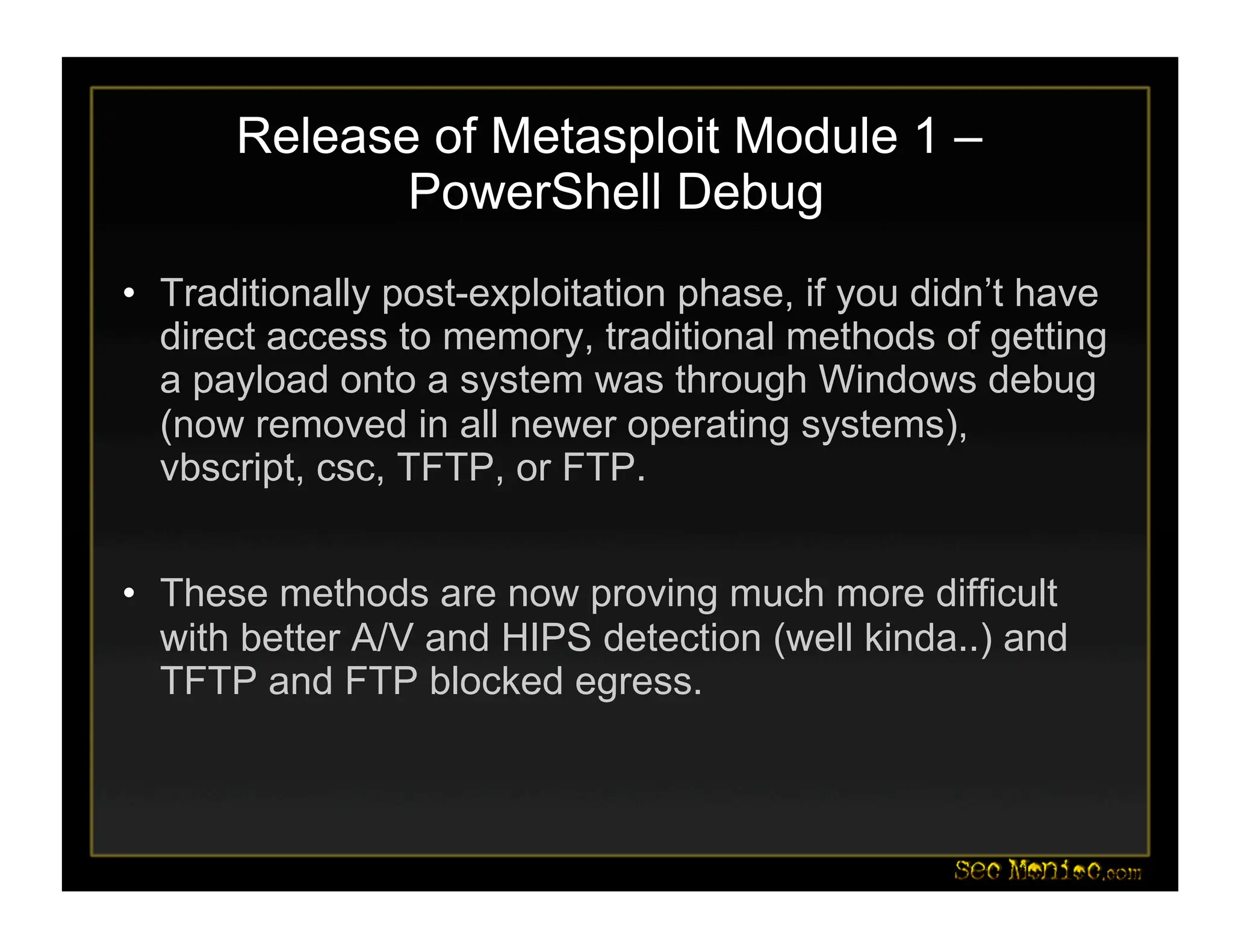
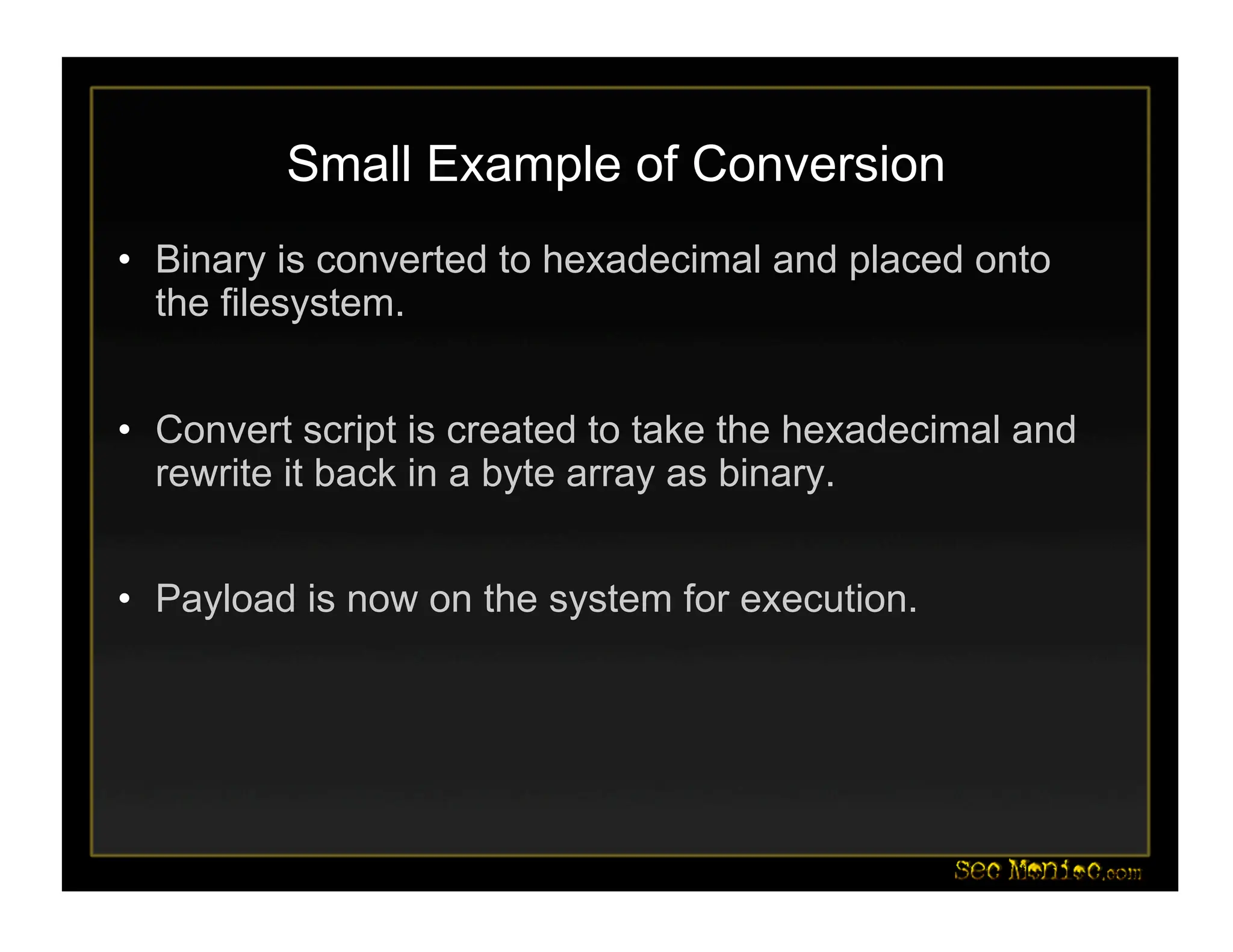
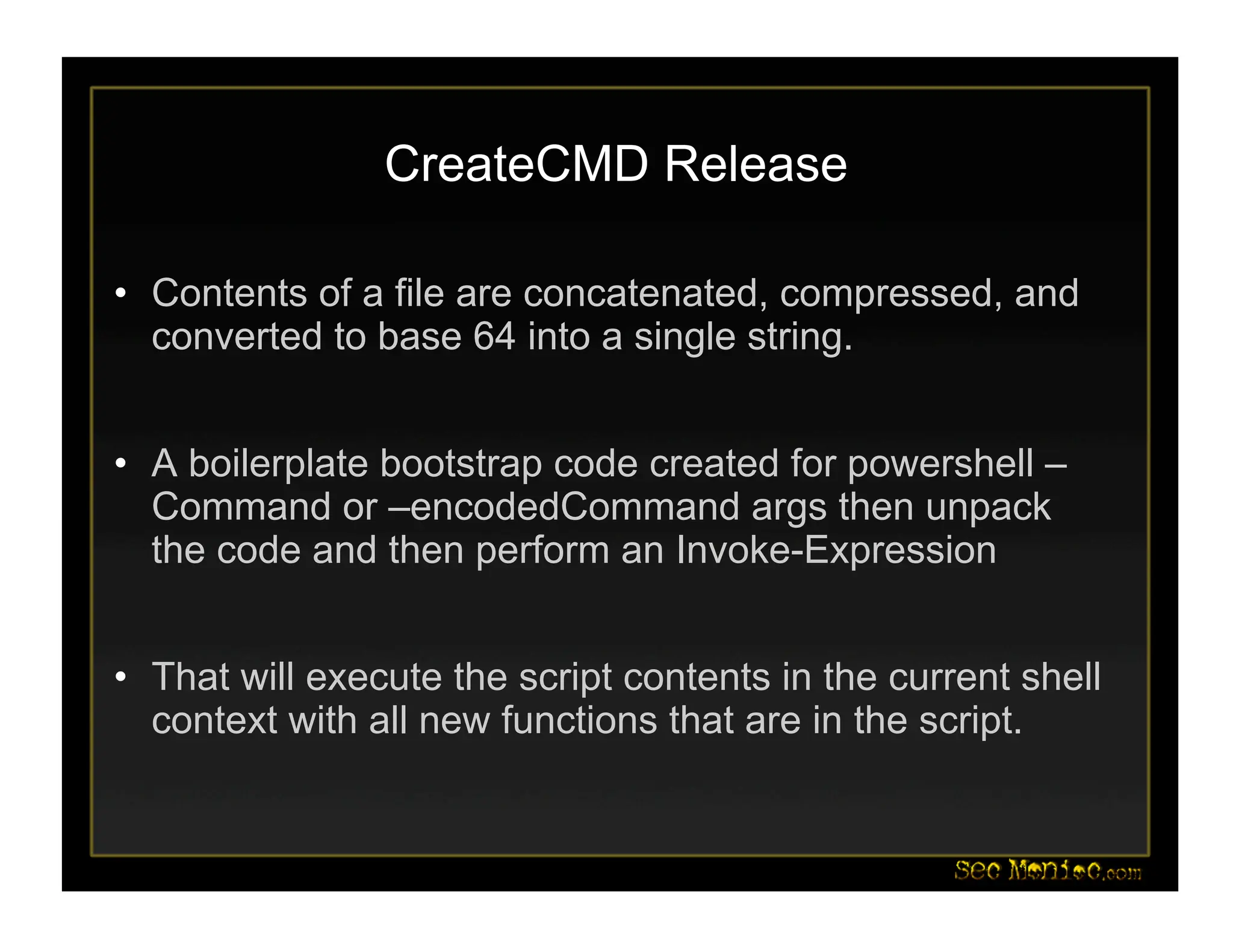
This document introduces PowerShell and its security applications. It summarizes the backgrounds and specializations of Dave Kennedy and Josh Kelley, who will demonstrate PowerShell tools. These include a Metasploit module for PowerShell-based post-exploitation, examples converting binaries to PowerShell, and demos of PowerShell-based password dumping and backdoors. The document also discusses the Social-Engineer Toolkit and updates, including new Java applet and USB attack vectors. Future PowerShell capabilities mentioned include process injection and deploying security baselines.