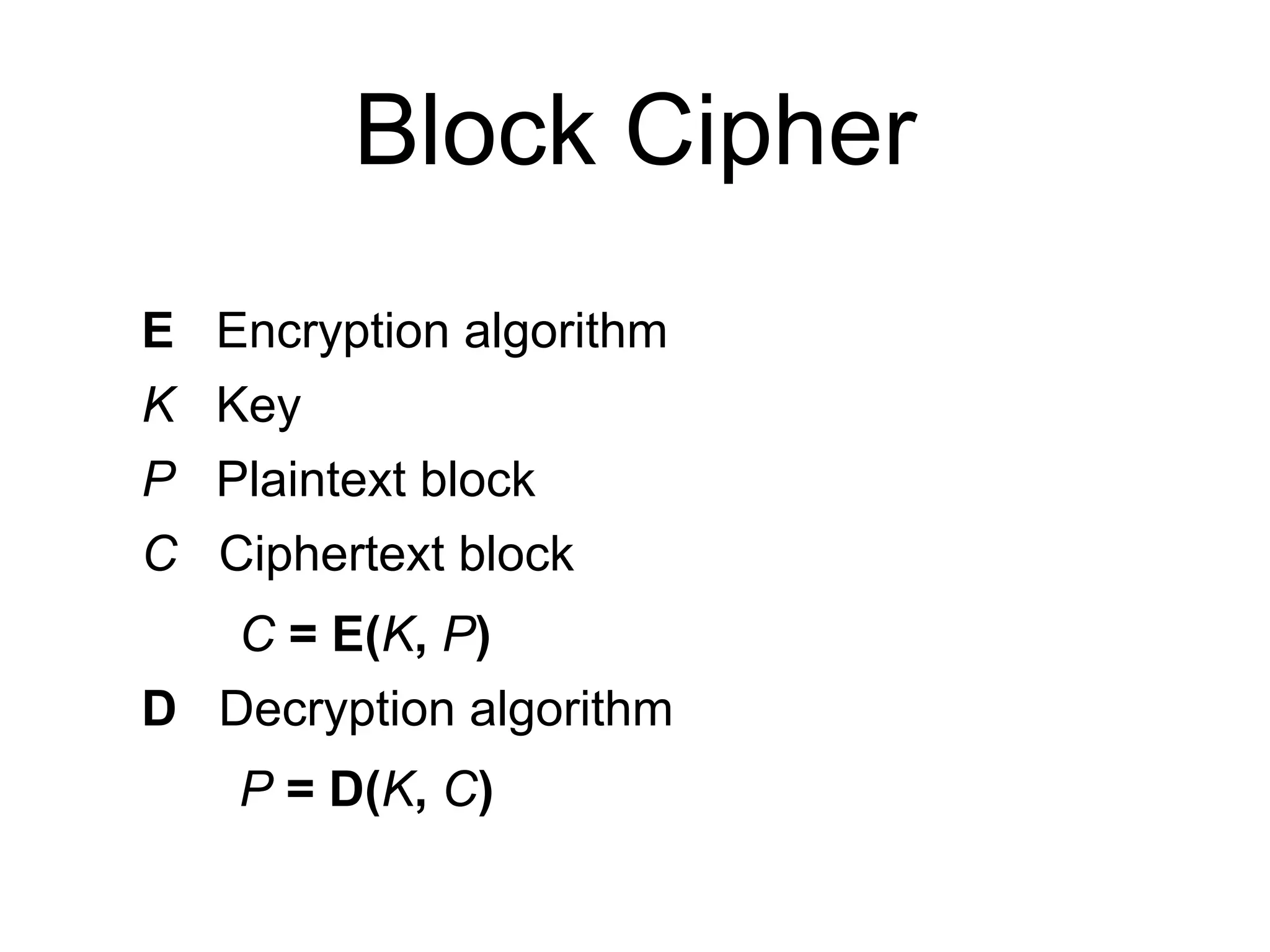
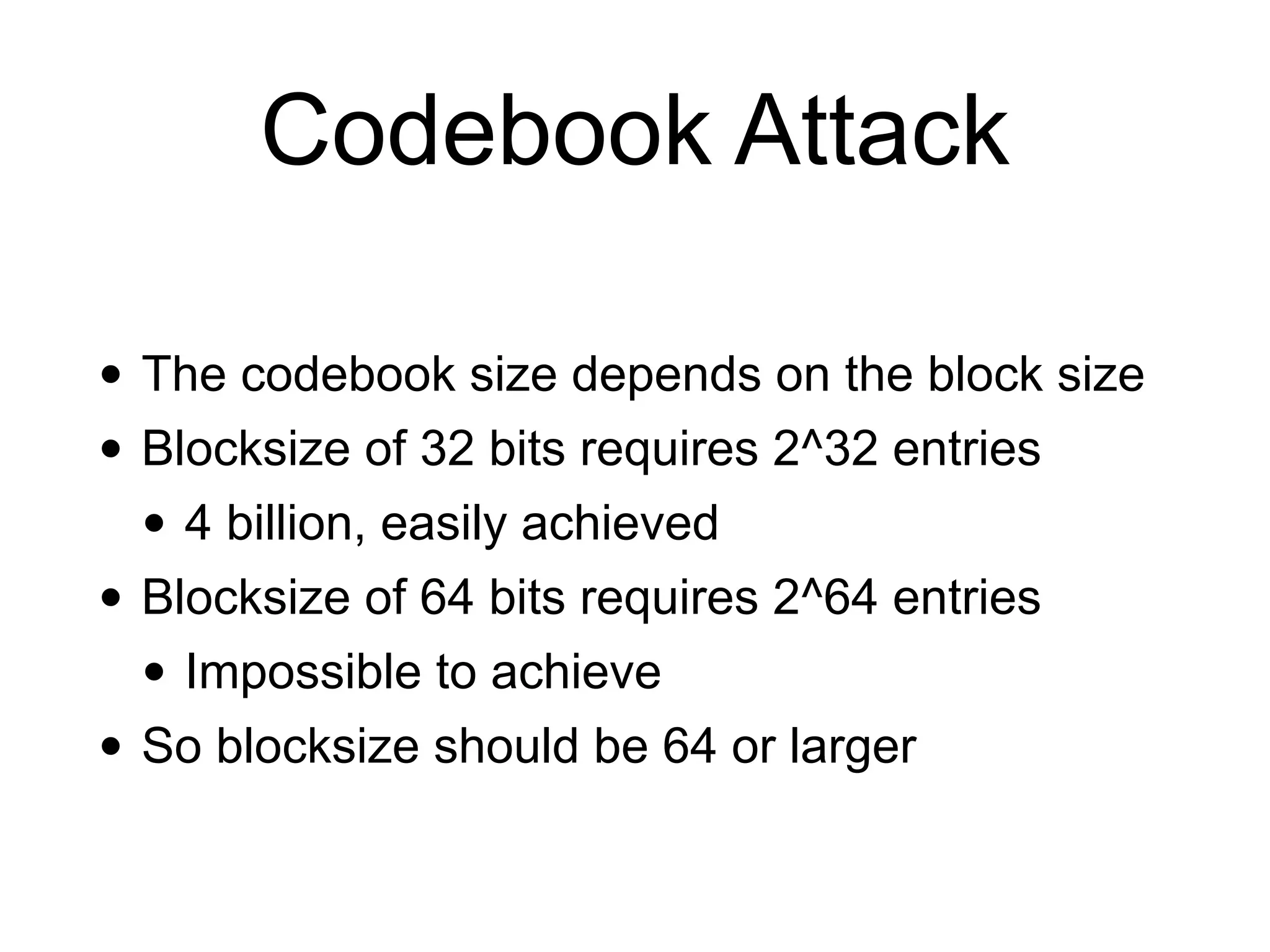
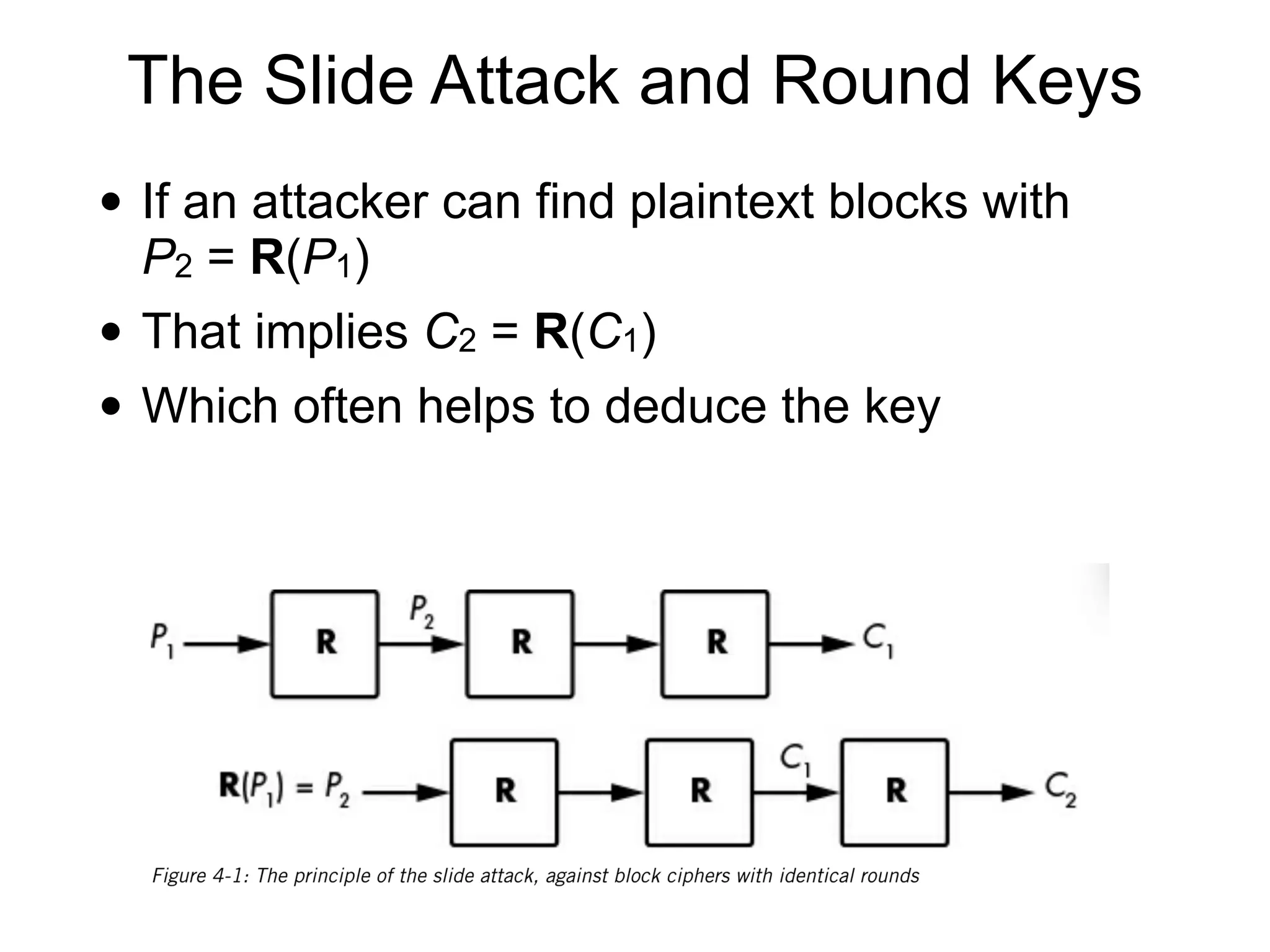
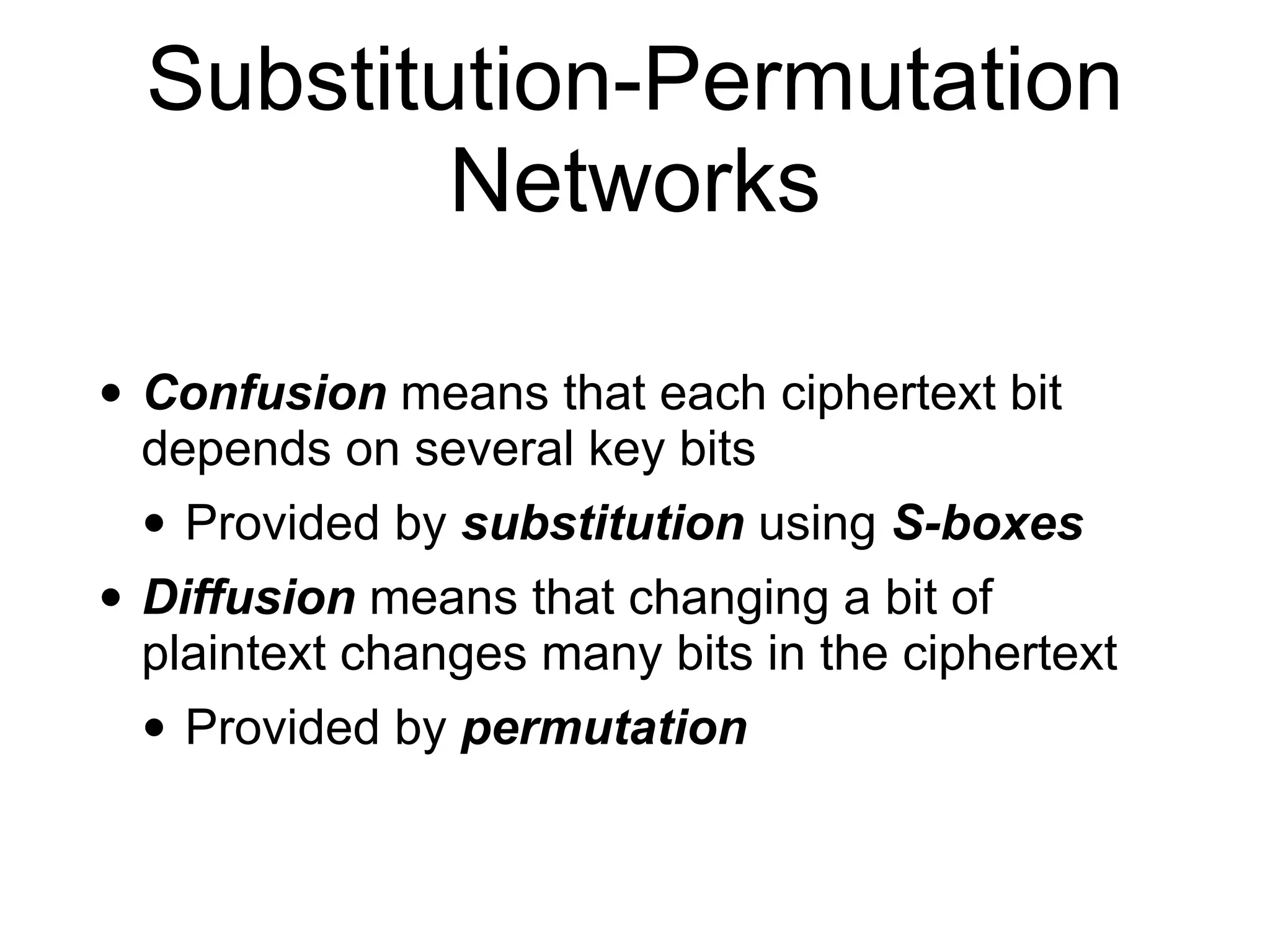
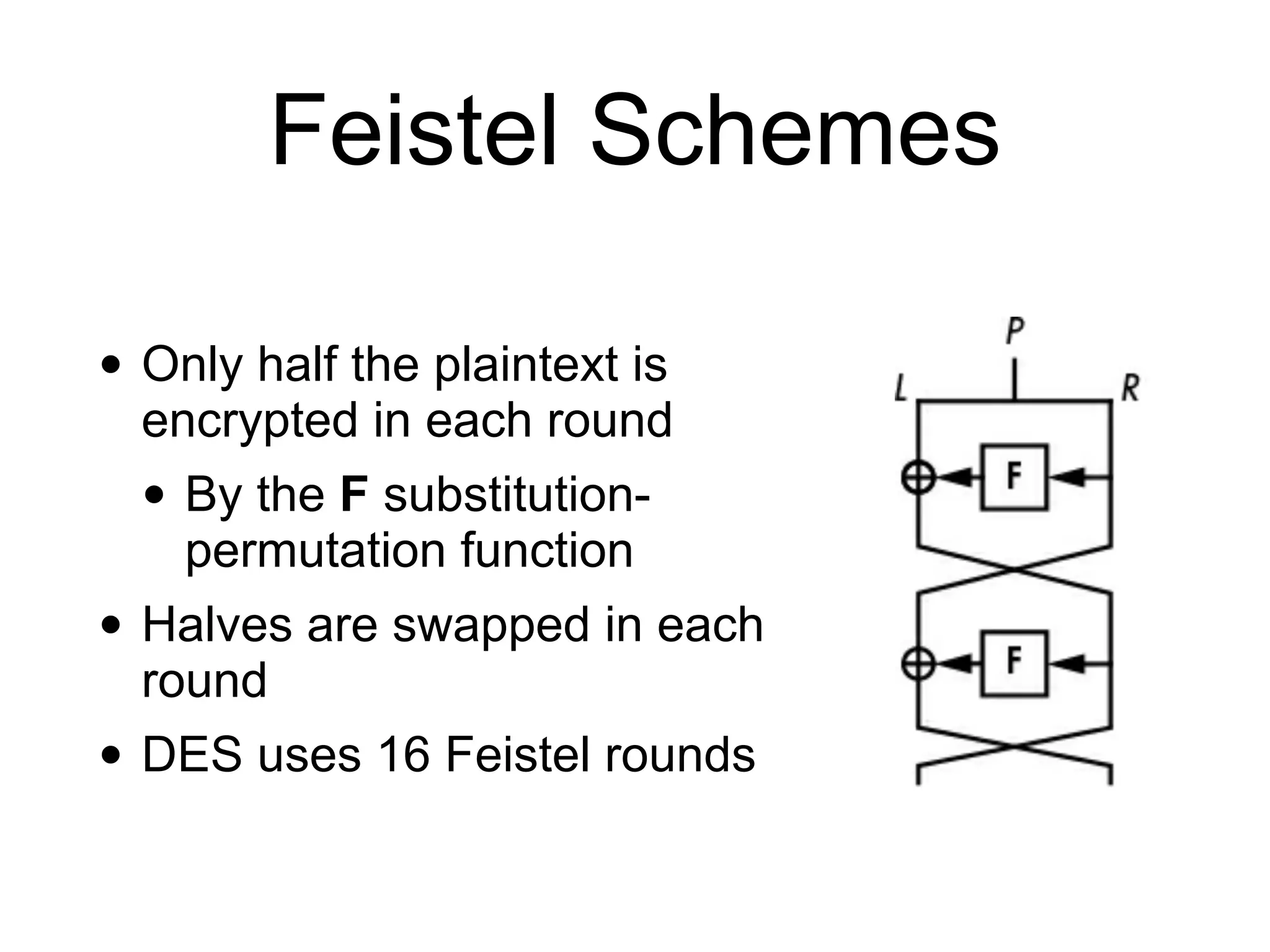
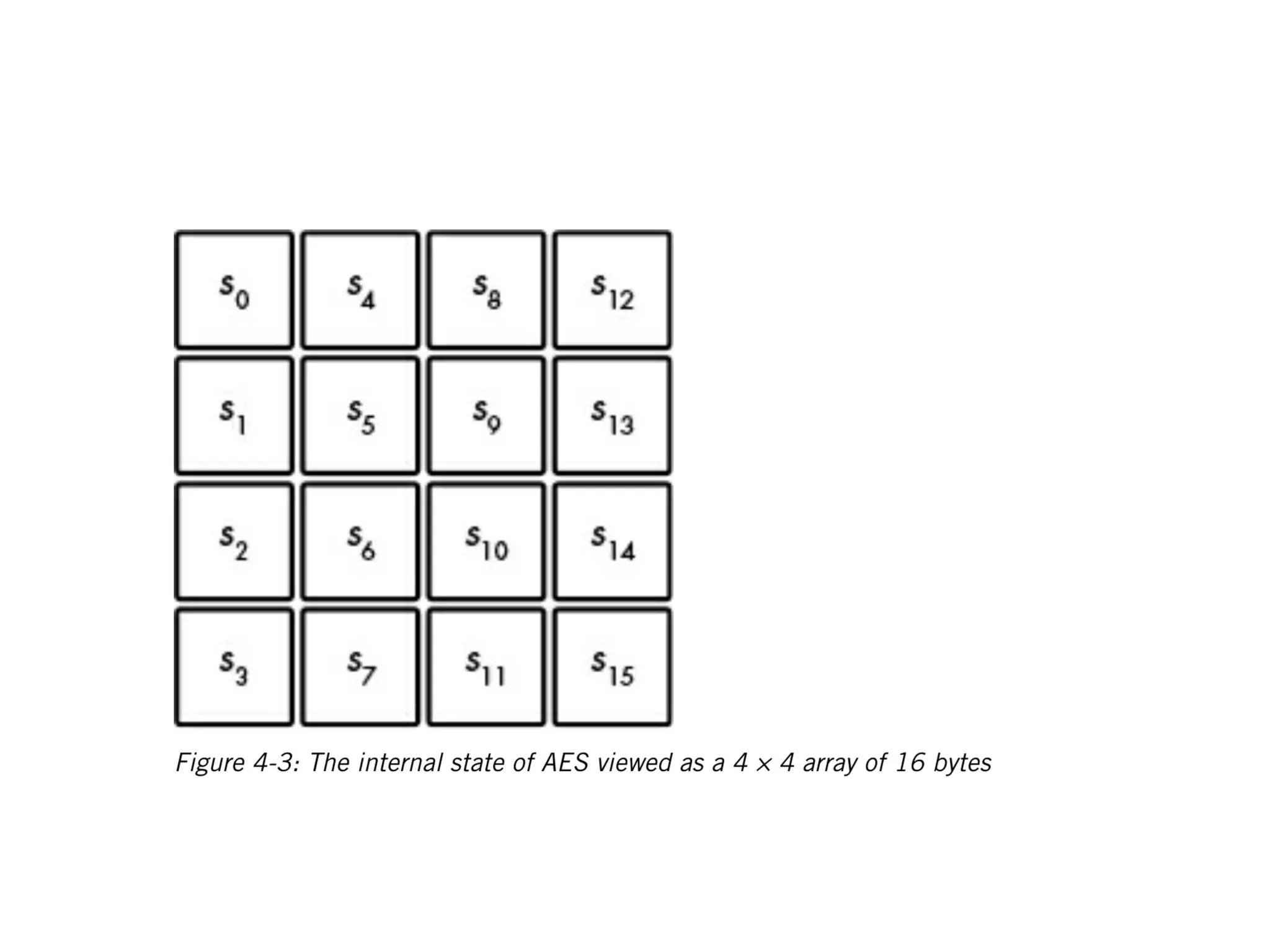
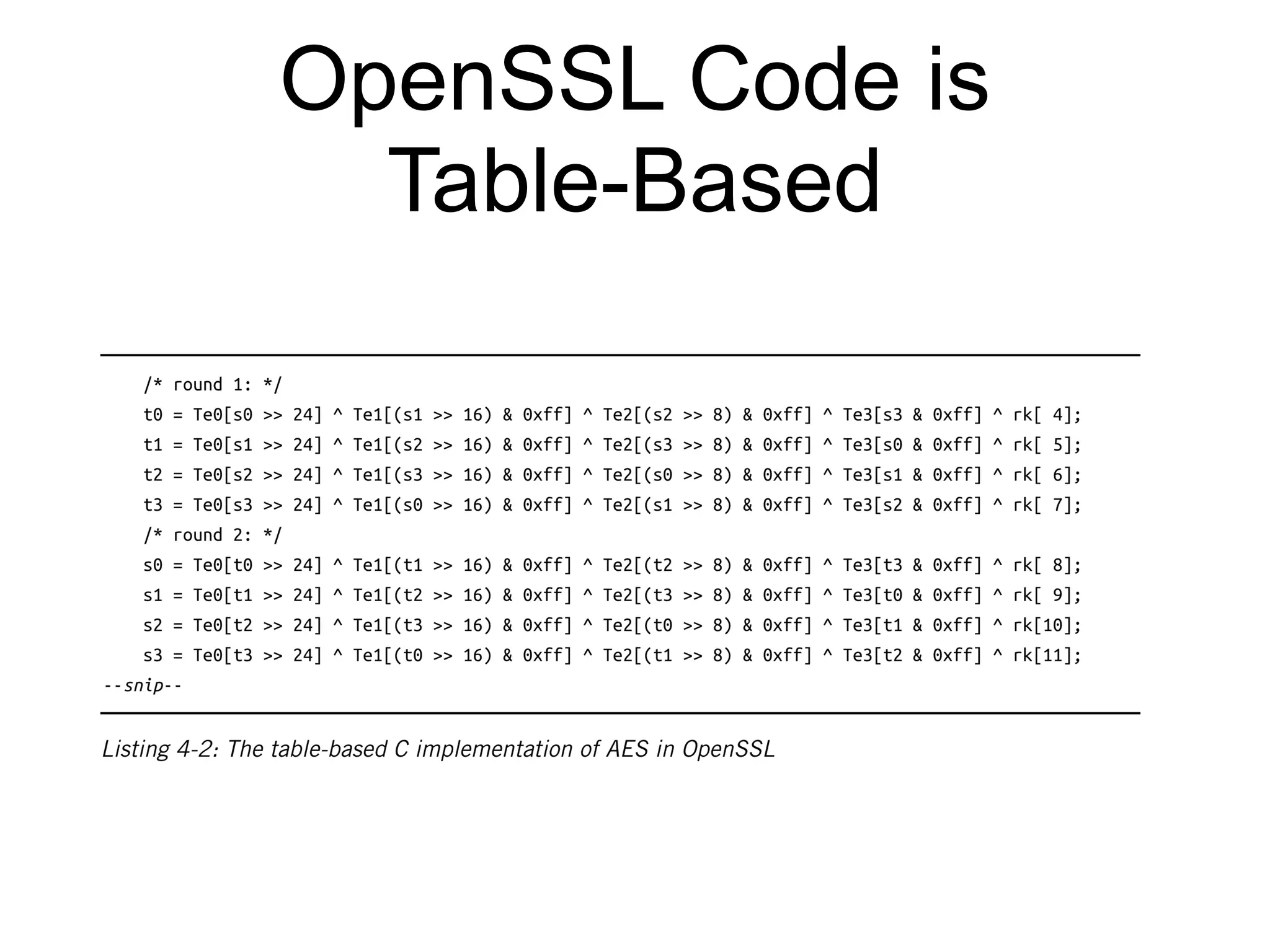
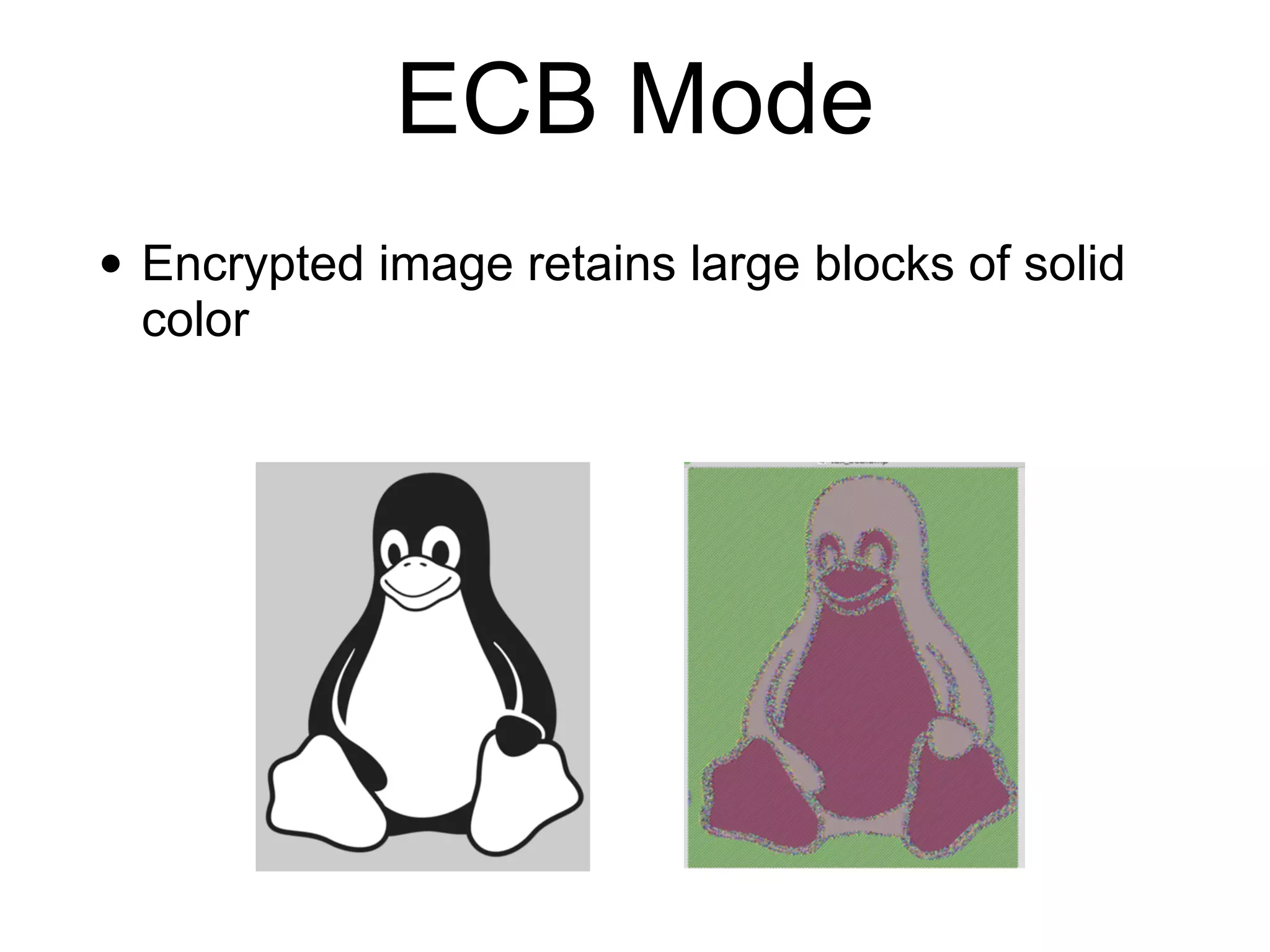
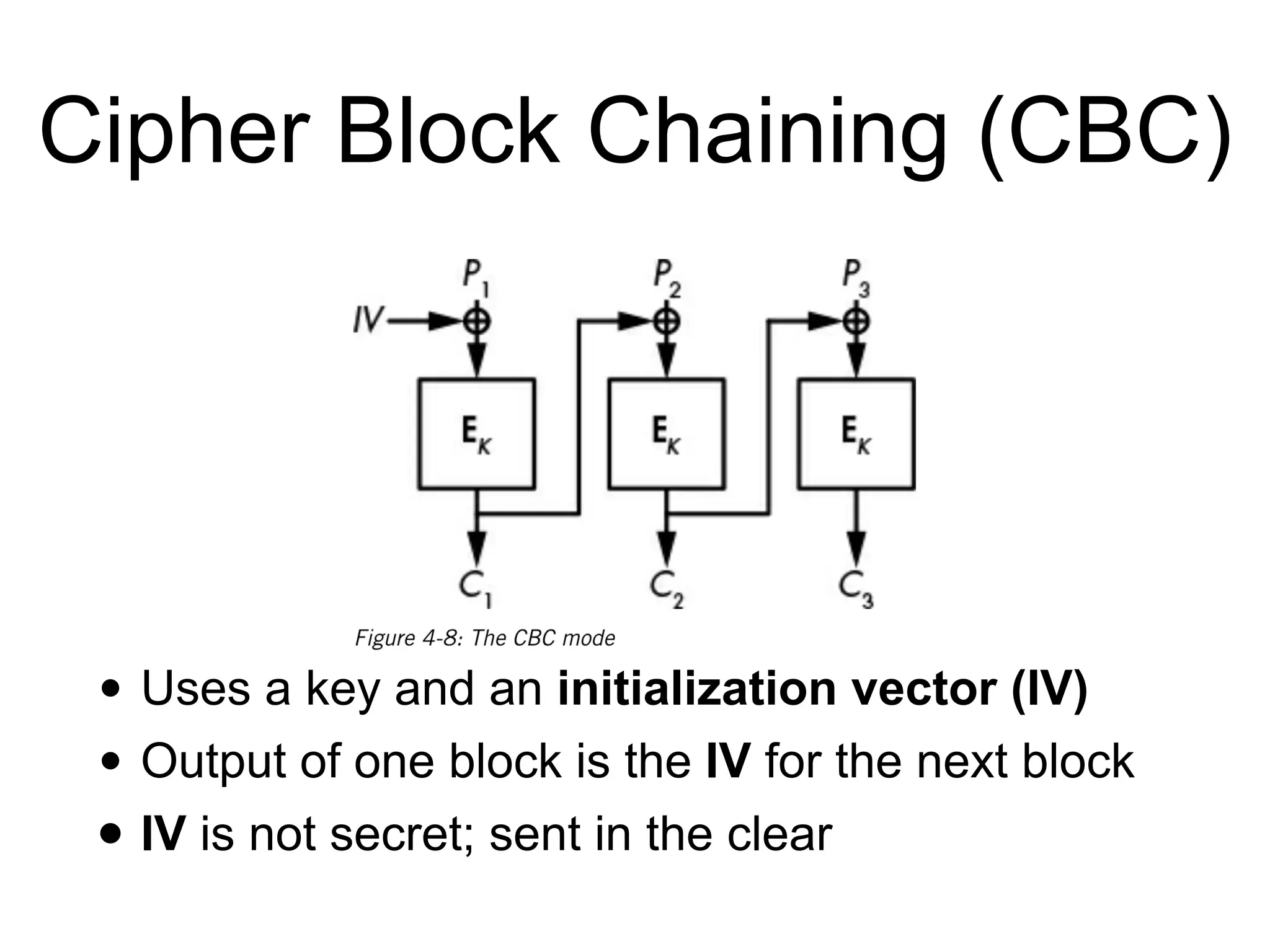
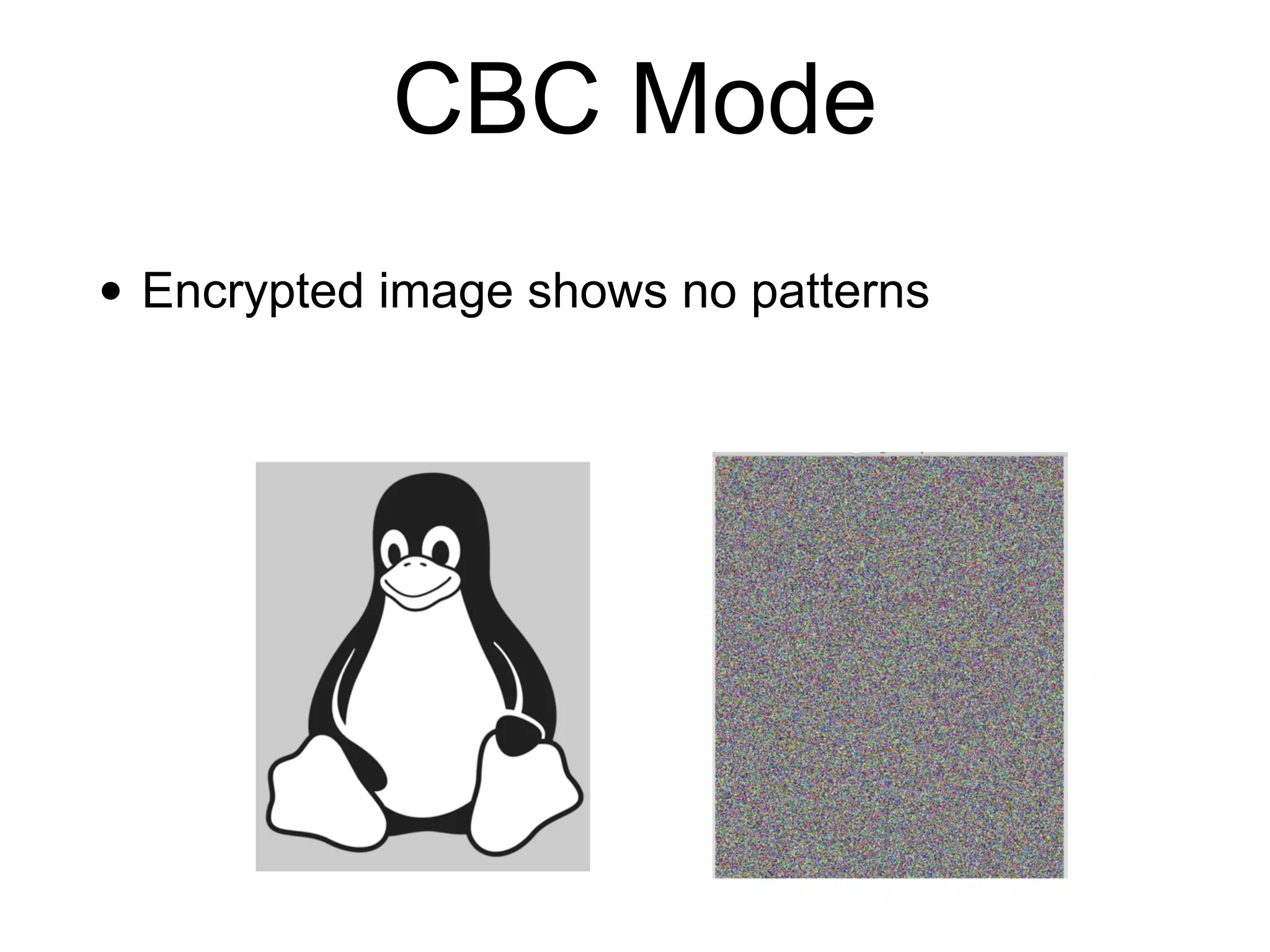
Block ciphers like AES encrypt data in fixed-size blocks and use cryptographic keys and rounds of processing to encrypt the data securely. AES is the current standard, using 128-bit blocks and keys of 128, 192, or 256 bits. Modes of operation like ECB, CBC, CTR are used to handle full messages. ECB is insecure as identical plaintext blocks produce identical ciphertext, while CBC and CTR provide security if nonces and IVs are not reused. Implementation details like padding and side channels must be handled carefully to prevent attacks.












































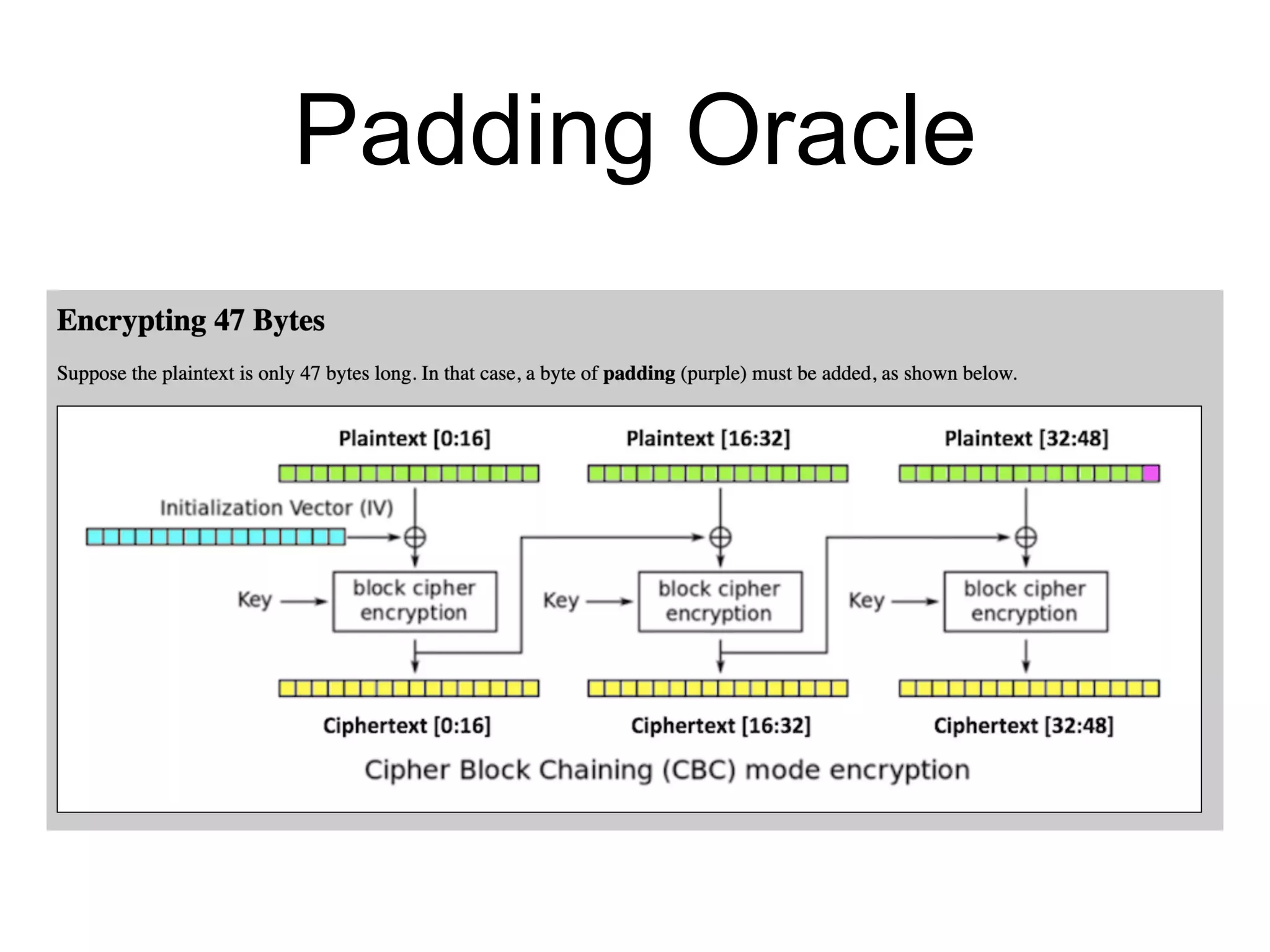




![Padding Oracle
• Once the orange bytes are known
• Attacker can forge plaintext[32:48] to say
anything](https://image.slidesharecdn.com/141-ch4-220914145810-c58bc0e0/75/4-Block-Ciphers-66-2048.jpg)
