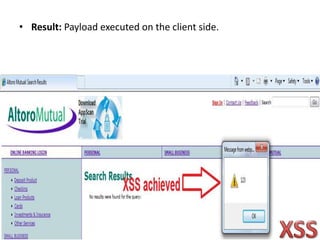
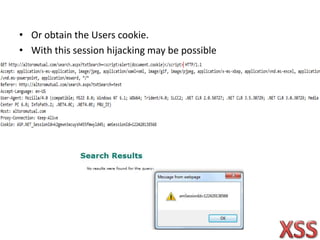
Cross-site scripting (XSS) is one of the most common web application attacks, where malicious scripts are injected into otherwise benign websites. There are three main types of XSS attacks - stored, reflected, and DOM-based. To prevent XSS, developers should sanitize user input by removing hazardous characters, properly escape untrusted output before displaying it, and enforce a specific character encoding.