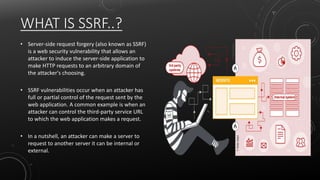
This document provides an overview of server-side request forgery (SSRF) vulnerabilities. It defines SSRF as allowing an attacker to induce a server to make HTTP requests to domains of the attacker's choosing. The document covers the types of SSRF (basic and blind), impact (exposing internal systems or remote code execution), methods for finding SSRF vulnerabilities, exploitation techniques like bypassing filters, and mitigations like using whitelists instead of blacklists. Tools for finding and exploiting SSRF vulnerabilities are also listed.