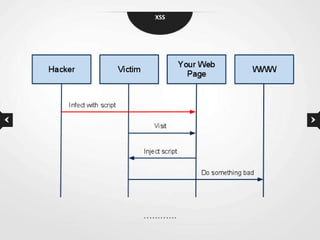
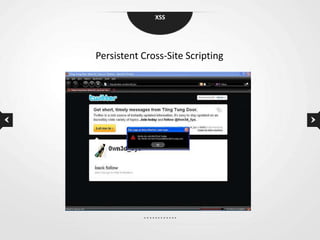
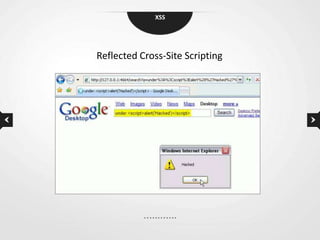
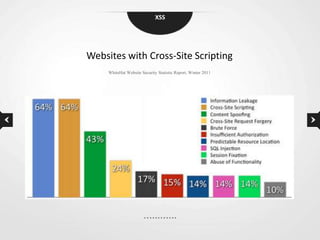
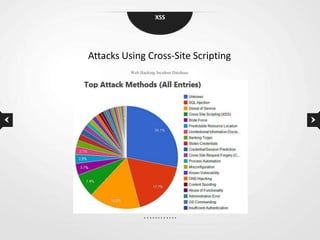
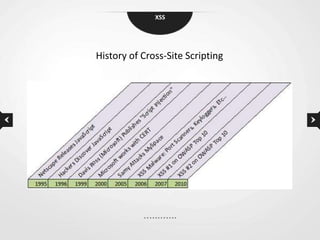
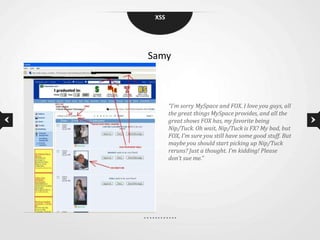
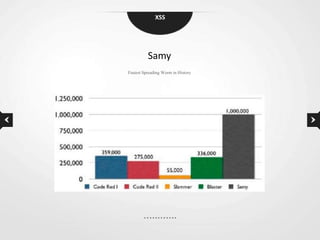
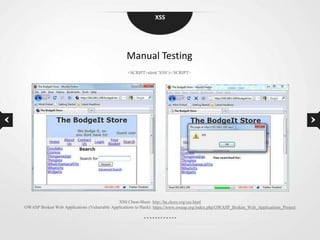
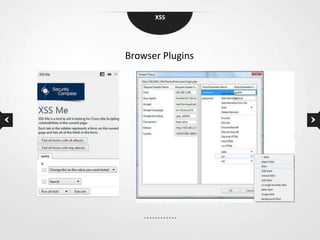
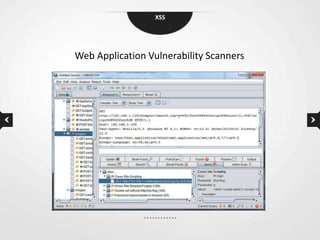
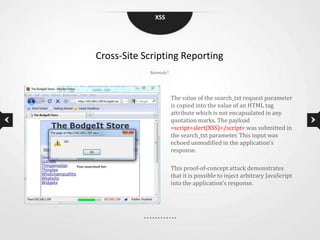
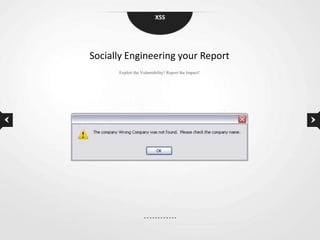
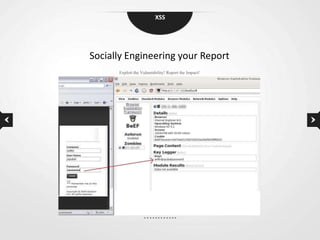
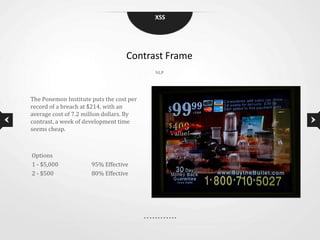
This document discusses cross-site scripting (XSS) vulnerabilities. XSS allows attackers to inject malicious scripts into vulnerable websites that are then executed by users' browsers. The document outlines different types of XSS, provides examples of real-world attacks, and discusses techniques for detecting and preventing XSS like input validation, output encoding, and using security libraries. It also suggests ways to effectively report XSS vulnerabilities to developers, including exploiting the vulnerability to demonstrate impact and using social engineering strategies that appeal to developers' priorities and incentives.